TPM: A More Trustworthy Solution to Computer Security
... the resources of a computer to be shared among multiple execution environments. At the core of virtualization technology is the VMM which provides the foundation for virtualization management. It was used to consolidate workloads of under-utilized servers to lesser number of machines. It provides is ...
... the resources of a computer to be shared among multiple execution environments. At the core of virtualization technology is the VMM which provides the foundation for virtualization management. It was used to consolidate workloads of under-utilized servers to lesser number of machines. It provides is ...
Device Drivers: Their Function in an Operating System
... between a personal digital assistant and a printer to allow a document to be printed. Jini does not actually download the services themselves. Instead, it downloads an interface through which a device can interact with the services (Cravotta, 2000). I/O drivers with some operating systems, such as L ...
... between a personal digital assistant and a printer to allow a document to be printed. Jini does not actually download the services themselves. Instead, it downloads an interface through which a device can interact with the services (Cravotta, 2000). I/O drivers with some operating systems, such as L ...
Introduction
... Running user commands User types: ‘grep some_word file_name’ Shell parses the command, inserts the strings grep, some_word, file_name into argv and their number to argc Next, the shell uses fork() to create a process (same user ID) Now, it takes the executable name grep and the arguments, a ...
... Running user commands User types: ‘grep some_word file_name’ Shell parses the command, inserts the strings grep, some_word, file_name into argv and their number to argc Next, the shell uses fork() to create a process (same user ID) Now, it takes the executable name grep and the arguments, a ...
GDLS VHMS Approach - SRI International
... • We cannot know a-priori what types of systems/nodes will attach to vulnerable points • Information at all security levels must be protected until nodes are authenticated and authorized ...
... • We cannot know a-priori what types of systems/nodes will attach to vulnerable points • Information at all security levels must be protected until nodes are authenticated and authorized ...
CounterACT: Powerful, Automated Network Protection
... CounterACT: Powerful, Automated Threat Protection against Conficker . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3 How the Conficker Worm Works. . ...
... CounterACT: Powerful, Automated Threat Protection against Conficker . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3 How the Conficker Worm Works. . ...
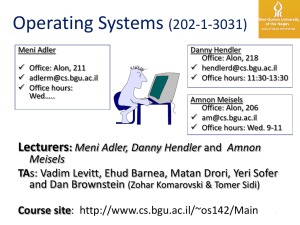
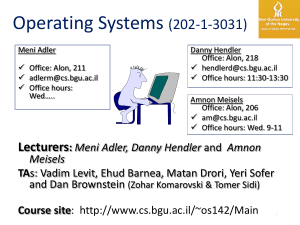
204341 Operating Systems
... Protection and Security Protection – any mechanism for controlling access of processes or users to resources defined by the ...
... Protection and Security Protection – any mechanism for controlling access of processes or users to resources defined by the ...
What is an Operating System?
... Protection and Security Protection – any mechanism for controlling access of processes or ...
... Protection and Security Protection – any mechanism for controlling access of processes or ...
Introduction to Information Security Chapter N
... It does this by understanding how the protocol functions, and opening and closing “doors” in the firewall, based on the information contained in the packet header. In this manner, dynamic packet filters are an intermediate form, between traditional static packet filters and ...
... It does this by understanding how the protocol functions, and opening and closing “doors” in the firewall, based on the information contained in the packet header. In this manner, dynamic packet filters are an intermediate form, between traditional static packet filters and ...
WHAT IS SQL INJECTION? ANATOMY OF A SQL INJECTION
... For example, creating fraudulent records, adding users or promoting users to higher access levels, or deleting data. ...
... For example, creating fraudulent records, adding users or promoting users to higher access levels, or deleting data. ...
Operating Systems, 6th ed. Test Bank Chapter 4 Page 1 of 15
... 5. T / F – In a pure User-Level Thread (ULT) facility, all of the work of thread management is done by the application, but the kernel is aware of the existence of threads. 6. T / F – In the field of distributed operating system design, the One-to-Many (Thread-to-Process) relationship is particularl ...
... 5. T / F – In a pure User-Level Thread (ULT) facility, all of the work of thread management is done by the application, but the kernel is aware of the existence of threads. 6. T / F – In the field of distributed operating system design, the One-to-Many (Thread-to-Process) relationship is particularl ...
Технічний коледж Луцького національного технічного
... changed the spreading of information globally. Internet is worldwide network of connected computers. This network enables you to communicate with the rest of the world in different ways? Has been approximated that the total amount of information globally doubles every 18 months, which indicates that ...
... changed the spreading of information globally. Internet is worldwide network of connected computers. This network enables you to communicate with the rest of the world in different ways? Has been approximated that the total amount of information globally doubles every 18 months, which indicates that ...
CISCO Secure Intrusion Detection System
... platform, a graphical user interface (GUI) displays these alarms in real time, color-coding each alarm based on its severity. This display provides a quick indication that an attack has occurred and how dangerous the attack is. The sensor can also log more detailed alarm information in a local text- ...
... platform, a graphical user interface (GUI) displays these alarms in real time, color-coding each alarm based on its severity. This display provides a quick indication that an attack has occurred and how dangerous the attack is. The sensor can also log more detailed alarm information in a local text- ...
Computer-System Architecture Computer
... Must ensure that a user program could never gain control of the computer in kernel mode. Otherwise, undesirable actions can be done e.g. a user program that, as part of its execution, stores a new address in the interrupt vector. ...
... Must ensure that a user program could never gain control of the computer in kernel mode. Otherwise, undesirable actions can be done e.g. a user program that, as part of its execution, stores a new address in the interrupt vector. ...
Operating Systems, 082
... Running user commands User types: ‘grep some_word file_name’ Shell parses the command, inserts the strings grep, some_word, file_name into argv and their number to argc Next, the shell uses fork() to create a process (same user ID) Now, it takes the executable name grep and the arguments, a ...
... Running user commands User types: ‘grep some_word file_name’ Shell parses the command, inserts the strings grep, some_word, file_name into argv and their number to argc Next, the shell uses fork() to create a process (same user ID) Now, it takes the executable name grep and the arguments, a ...
MYDIGIPASS for Healthcare
... logo are registered or unregistered trademarks of VASCO Data Security, Inc. and/or VASCO Data Security International GmbH in the U.S. and other countries. VASCO Data Security, Inc. and/or VASCO Data Security International GmbH own or are licensed under all title, rights and interest in VASCO Product ...
... logo are registered or unregistered trademarks of VASCO Data Security, Inc. and/or VASCO Data Security International GmbH in the U.S. and other countries. VASCO Data Security, Inc. and/or VASCO Data Security International GmbH own or are licensed under all title, rights and interest in VASCO Product ...
Module 3: Operating
... Systems programs The kernel Consists of everything below the system-call interface ...
... Systems programs The kernel Consists of everything below the system-call interface ...
Windows 2000 System Architecture
... Included to meet US Government requirements Windows 2000 implements POSIX 1003.1 Provides limited set of services • Can’t create threads, windows or use sockets! – Executables linked against POSIX subsystem library (Psxdll.dll) – Commercial Unix-to-Win32 library better approach for porting UNIX appl ...
... Included to meet US Government requirements Windows 2000 implements POSIX 1003.1 Provides limited set of services • Can’t create threads, windows or use sockets! – Executables linked against POSIX subsystem library (Psxdll.dll) – Commercial Unix-to-Win32 library better approach for porting UNIX appl ...
PPT Version
... • Concept of Security Planes could be instrumental for ensuring that essential network activities are protected independently (e.g. compromise of security at the Enduser Security Plane does not affect functions associated with the Management Security Plane). • Concept of Security Planes allows to id ...
... • Concept of Security Planes could be instrumental for ensuring that essential network activities are protected independently (e.g. compromise of security at the Enduser Security Plane does not affect functions associated with the Management Security Plane). • Concept of Security Planes allows to id ...
Discovery 1 Module 2 Course Curriculum Picture Descriptions
... The following is an Interactive Media Activity, which identifies the 3 main download methods for Automatic Updates. The diagram depicts three boxes with the text below: Scenario - A service pack update is required to correct known functionality and security issues within an operating system. Scenari ...
... The following is an Interactive Media Activity, which identifies the 3 main download methods for Automatic Updates. The diagram depicts three boxes with the text below: Scenario - A service pack update is required to correct known functionality and security issues within an operating system. Scenari ...
Distributed systems
... • confidentiality means protection against unauthorized access; • integrity implies protection of data against ...
... • confidentiality means protection against unauthorized access; • integrity implies protection of data against ...
What is an Operating System?
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs Concurrency by multiplexing the CPUs among the processes / ...
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs Concurrency by multiplexing the CPUs among the processes / ...
Processes and threads
... Each instance has resource limitations, security information - rights, capabilities etc. ...
... Each instance has resource limitations, security information - rights, capabilities etc. ...
XML: Part - Houston Community College System
... • It is possible to store public keys by embedding them within digital certificates • This is a form of software-based storage and doesn’t involve any cryptography hardware • Another form of software-based storage involves storing private keys on the user’s local computer ...
... • It is possible to store public keys by embedding them within digital certificates • This is a form of software-based storage and doesn’t involve any cryptography hardware • Another form of software-based storage involves storing private keys on the user’s local computer ...