teaching portfolio
... I believe that being an educator or a teacher is a blessing from Allah. It is one of the ways to keep our rewards or „pahala‟ continue by sharing knowledge and pass them on and on. As long as the knowledge is being used, one will receive long lasting rewards. And without realizing it; your knowledge ...
... I believe that being an educator or a teacher is a blessing from Allah. It is one of the ways to keep our rewards or „pahala‟ continue by sharing knowledge and pass them on and on. As long as the knowledge is being used, one will receive long lasting rewards. And without realizing it; your knowledge ...
Embedded Operating Systems for Real
... system. Here each task runs until it is finished and only after that next task is started. In shortest job first scheduler each time a running task completes or blocks itself, next task selected is one that will require the least amount of processor time to complete. Round robin is the only scheduli ...
... system. Here each task runs until it is finished and only after that next task is started. In shortest job first scheduler each time a running task completes or blocks itself, next task selected is one that will require the least amount of processor time to complete. Round robin is the only scheduli ...
Presentation Title Size 30PT
... What is this chapter about and why is it important? This chapter discusses operating systems (OS). It covers the functions and terminology of operating systems, specifically Windows 2000, Windows XP, and Windows Vista. Because operating system functionality varies, this chapter explains how to d ...
... What is this chapter about and why is it important? This chapter discusses operating systems (OS). It covers the functions and terminology of operating systems, specifically Windows 2000, Windows XP, and Windows Vista. Because operating system functionality varies, this chapter explains how to d ...
document
... VPN technology also allows a corporation to connect to branch offices or to other companies over a public internetwork (such as the Internet), while maintaining secure communications. The VPN connection across the Internet logically operates as a wide area network (WAN) link between the sites. In bo ...
... VPN technology also allows a corporation to connect to branch offices or to other companies over a public internetwork (such as the Internet), while maintaining secure communications. The VPN connection across the Internet logically operates as a wide area network (WAN) link between the sites. In bo ...
lecture05-chapter03
... parent, to reflect that an additional process now also owns those files. 5. Assign the child process to the Ready to Run state. 6. Returns the ID number of the child to the parent process, and a 0 value to the child process. ...
... parent, to reflect that an additional process now also owns those files. 5. Assign the child process to the Ready to Run state. 6. Returns the ID number of the child to the parent process, and a 0 value to the child process. ...
2005-03-midterm.pdf
... As a virtual machine, an operating system provides an abstraction over the hardware by means of, for example, system calls. In this way, it provides a convenient way to program a machine without the need to know about hardware details. As a resource manager, it allows multiple processes (or users) t ...
... As a virtual machine, an operating system provides an abstraction over the hardware by means of, for example, system calls. In this way, it provides a convenient way to program a machine without the need to know about hardware details. As a resource manager, it allows multiple processes (or users) t ...
Silberschatz, Galvin and Gagne ©2013 Operating System Concepts
... Page fault executes when memory access error ...
... Page fault executes when memory access error ...
Are Virtual-Machine Monitors Microkernels Done Right?
... that combine and colocate significant critical system point out that this liability inversion is in fact an isfunctionality. Such a structure potentially decreases sue in Xen as well. An example for this is actuoverall reliability and poses the risk of a single point ally given in another paper at t ...
... that combine and colocate significant critical system point out that this liability inversion is in fact an isfunctionality. Such a structure potentially decreases sue in Xen as well. An example for this is actuoverall reliability and poses the risk of a single point ally given in another paper at t ...
ppt
... – From user space - interrupt handler performs an asynchronous trap & remote invocation executes – From kernel space – interrupt handler queues the invocation for execution when kernel becomes idle, or when control returns to user space – Has process context so requested operation free to block duri ...
... – From user space - interrupt handler performs an asynchronous trap & remote invocation executes – From kernel space – interrupt handler queues the invocation for execution when kernel becomes idle, or when control returns to user space – Has process context so requested operation free to block duri ...
Chapter 1: Introduction
... The basic unit of computer storage is the bit. A bit can contain one of two values, 0 and 1. All other storage in a computer is based on collections of bits. Given enough bits, it is amazing how many things a computer can represent: numbers, letters, images, movies, sounds, documents, and programs, ...
... The basic unit of computer storage is the bit. A bit can contain one of two values, 0 and 1. All other storage in a computer is based on collections of bits. Given enough bits, it is amazing how many things a computer can represent: numbers, letters, images, movies, sounds, documents, and programs, ...
Silberschatz, Galvin and Gagne ©2009 Operating System Concepts
... Page fault executes when memory access error ...
... Page fault executes when memory access error ...
System Call - Programs in Mathematics and Computer Science
... system itself via resource sharing ...
... system itself via resource sharing ...
cs320ch3powerpoint
... • One aspect of scheduling is system driven, not policy driven: Interrupts force a change in what job is running • Aside from handling interrupts as they occur, it is O/S policy, the scheduling algorithm, that determines what job is scheduled • The O/S maintains data structures, including PCB’s, wh ...
... • One aspect of scheduling is system driven, not policy driven: Interrupts force a change in what job is running • Aside from handling interrupts as they occur, it is O/S policy, the scheduling algorithm, that determines what job is scheduled • The O/S maintains data structures, including PCB’s, wh ...
Isolating Operating System Components with Intel SGX
... functionality by wrapping it in SGX enclaves. • We provide a proof-of-concept implementation of our concept which protects one kernel function, namely full disk encryption, using an Intel SGX enclave in user space. Our implementation is seamlessly integrated by using the Linux Crypto API; the integr ...
... functionality by wrapping it in SGX enclaves. • We provide a proof-of-concept implementation of our concept which protects one kernel function, namely full disk encryption, using an Intel SGX enclave in user space. Our implementation is seamlessly integrated by using the Linux Crypto API; the integr ...
Operating System Theory Guide to Operating Systems
... • Time-sharing systems frequently conduct what are termed batch processes ...
... • Time-sharing systems frequently conduct what are termed batch processes ...
2.01
... Many systems now servers, responding to requests generated by clients Compute-server provides an interface to client to request ...
... Many systems now servers, responding to requests generated by clients Compute-server provides an interface to client to request ...
Chapter 2 – Operating System Overview
... 1) An __________ is a program that controls the execution of application programs and acts as an interface between applications and the computer hardware. Answer: operating system (OS) 2) The portion of the monitor that is always in main memory and available for execution is referred to as the _____ ...
... 1) An __________ is a program that controls the execution of application programs and acts as an interface between applications and the computer hardware. Answer: operating system (OS) 2) The portion of the monitor that is always in main memory and available for execution is referred to as the _____ ...
MIPS Assembler Programming
... (PCBs and Hardware State) When a process is running its Program Counter, stack pointer, registers, etc., are loaded on the CPU (I.e., the processor hardware registers contain the current values) When the OS stops running a process, it saves the current values of those registers into the PCB for that ...
... (PCBs and Hardware State) When a process is running its Program Counter, stack pointer, registers, etc., are loaded on the CPU (I.e., the processor hardware registers contain the current values) When the OS stops running a process, it saves the current values of those registers into the PCB for that ...
Control Panel Security
... company may use the same house key for all enclosures, and can configure the key for specific company needs. Therefore an outsider cannot gain entry to the enclosure with a generic key. If the company wants to limit access further, each enclosure can have its own key. Unique house keys may increase ...
... company may use the same house key for all enclosures, and can configure the key for specific company needs. Therefore an outsider cannot gain entry to the enclosure with a generic key. If the company wants to limit access further, each enclosure can have its own key. Unique house keys may increase ...
Abstract - Chennaisunday.com
... IDAGs. We developed polynomial-time algorithms to construct nodeindependent and link-independent DAGs using all possible edges in the network. The IDAGs approach was evaluated on four real-life network topologies and compared to ITrees and multiple pairs of colored (independent) trees approaches to ...
... IDAGs. We developed polynomial-time algorithms to construct nodeindependent and link-independent DAGs using all possible edges in the network. The IDAGs approach was evaluated on four real-life network topologies and compared to ITrees and multiple pairs of colored (independent) trees approaches to ...
What is an Operating System? - University of Central Florida
... Main memory – only large storage media that the CPU can access directly Secondary storage – extension of main memory that provides large ...
... Main memory – only large storage media that the CPU can access directly Secondary storage – extension of main memory that provides large ...
Security policy design with IPSec
... Network security design can be compared to the design of software, and many of the principles that have been developed and used over the years can be used (Porto and De Geus 2003:1). It is unfortunate that many software products are developed using what might be termed a ‘build and fix’ model. This ...
... Network security design can be compared to the design of software, and many of the principles that have been developed and used over the years can be used (Porto and De Geus 2003:1). It is unfortunate that many software products are developed using what might be termed a ‘build and fix’ model. This ...
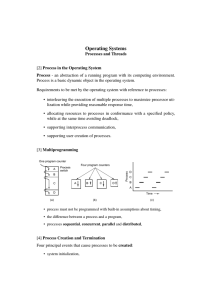
Operating Systems
... [20] Multithreaded Architecture under Solaris OS Solaris makes use of four separate thread-related concepts: • Process - the normal Unix process, • User-level threads - ULTs, implemented through a threads library in the address space of a process, – invisible to the operating system, – interface for ...
... [20] Multithreaded Architecture under Solaris OS Solaris makes use of four separate thread-related concepts: • Process - the normal Unix process, • User-level threads - ULTs, implemented through a threads library in the address space of a process, – invisible to the operating system, – interface for ...
Chapter 1 Slides
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs Concurrency by multiplexing the CPUs among the processes ...
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs Concurrency by multiplexing the CPUs among the processes ...