Test1_soln
... a. ULTs are cheaper to create and run than processes. b. Communication overhead between two ULTs is much smaller than between processes. c. ULTs are transparent to Kernel. Ans. (a) ULTs pertain to a single process, and therefore they share the same address space. Consequently, the overhead to create ...
... a. ULTs are cheaper to create and run than processes. b. Communication overhead between two ULTs is much smaller than between processes. c. ULTs are transparent to Kernel. Ans. (a) ULTs pertain to a single process, and therefore they share the same address space. Consequently, the overhead to create ...
Math vs. Malware
... alongside them, without relying on human intervention. That’s where math and machine learning have the advantage. If we can objectively classify ‘good’ files from ‘bad’ based on mathematical risk factors, then we can teach a machine to make the appropriate decisions on these files in real time. A ma ...
... alongside them, without relying on human intervention. That’s where math and machine learning have the advantage. If we can objectively classify ‘good’ files from ‘bad’ based on mathematical risk factors, then we can teach a machine to make the appropriate decisions on these files in real time. A ma ...
1-web
... or the operating system itself. Describe two difficulties that you think could arise with such a scheme. Answer: ...
... or the operating system itself. Describe two difficulties that you think could arise with such a scheme. Answer: ...
How-OS-Works.pdf
... How the Operating System Works, a brief overview, R. Craig Collins, © 2008 When the computer is turned on, the BIOS locates the operating system on the hard drive, and transfers the core parts into memory, RAM. If a command line is used, a file named autoexec.bat is executed, to configure the system ...
... How the Operating System Works, a brief overview, R. Craig Collins, © 2008 When the computer is turned on, the BIOS locates the operating system on the hard drive, and transfers the core parts into memory, RAM. If a command line is used, a file named autoexec.bat is executed, to configure the system ...
Chap 9 - IUP Personal Websites
... The process by which a private IP address in a corporate network is translated into a public address by a router or firewall is called_____________ True or False: Advanced firewalls use stateful packet inspection to improve security. A computer providing public network services that resides inside a ...
... The process by which a private IP address in a corporate network is translated into a public address by a router or firewall is called_____________ True or False: Advanced firewalls use stateful packet inspection to improve security. A computer providing public network services that resides inside a ...
HIPAA Security Standards
... There are several types of firewall techniques: • Packet filter: Looks at each packet entering or leaving the network and accepts or rejects it based on user-defined rules. Packet filtering is fairly effective and transparent to users, but it is difficult to configure. In addition, it is susceptible ...
... There are several types of firewall techniques: • Packet filter: Looks at each packet entering or leaving the network and accepts or rejects it based on user-defined rules. Packet filtering is fairly effective and transparent to users, but it is difficult to configure. In addition, it is susceptible ...
Operating Systems
... It should point out that the operating system handles more than one process at a time. This is called multi-tasking. Therefore, an operating system always needs to frequent update the status of many tasks and their related information. The CPU needs to swap from one process to another. Even when you ...
... It should point out that the operating system handles more than one process at a time. This is called multi-tasking. Therefore, an operating system always needs to frequent update the status of many tasks and their related information. The CPU needs to swap from one process to another. Even when you ...
Computer & Network Technology Advisory Committee Meeting 3/24/2015 Minutes
... i. Discuss revision of Information Systems It was noted by a parent in the group, that the selection of courses in the high school is very broad. Some of the concepts we are looking at in the revised information systems course may be an overlap/rehash of material that they have already had in other ...
... i. Discuss revision of Information Systems It was noted by a parent in the group, that the selection of courses in the high school is very broad. Some of the concepts we are looking at in the revised information systems course may be an overlap/rehash of material that they have already had in other ...
Module 3: Operating
... Most modern computer systems use disks as the principle on-line storage medium, for both programs and data. ...
... Most modern computer systems use disks as the principle on-line storage medium, for both programs and data. ...
OPERATING SYSTEMS 2015-16 1 OPERATING SYSTEM
... Sometimes implemented in kernel, sometimes by systems program Sometimes multiple flavors implemented – shells Primarily fetches a command from user and executes it Sometimes commands built-in, sometimes just names of programs If the latter, adding new features doesn’t require shell modificati ...
... Sometimes implemented in kernel, sometimes by systems program Sometimes multiple flavors implemented – shells Primarily fetches a command from user and executes it Sometimes commands built-in, sometimes just names of programs If the latter, adding new features doesn’t require shell modificati ...
Operating System
... machine but the OS have access to other machines. By this way, file sharing, messaging, etc. became possible. In networks, users are aware of the fact that s/he is working in a network and when information is exchanged. The user explicitly handles the transfer of information. ...
... machine but the OS have access to other machines. By this way, file sharing, messaging, etc. became possible. In networks, users are aware of the fact that s/he is working in a network and when information is exchanged. The user explicitly handles the transfer of information. ...
Solaris Zones: Operating System Support for Server Consolidation Andrew Tucker David Comay
... These efforts differ from virtual machine implementations in that there is only one underlying operating system kernel, which is enhanced to provide increased isolation between groups of processes. The result is the ability to run multiple applications in isolation from each other within a single op ...
... These efforts differ from virtual machine implementations in that there is only one underlying operating system kernel, which is enhanced to provide increased isolation between groups of processes. The result is the ability to run multiple applications in isolation from each other within a single op ...
Unit I Operating Systems in Distributed Environments
... • All the OS was constructed in assembler language, reason why it was totally dependant of the machine. • The OS only can manipulate some peripherals. The batch processing was used to improve the resources use. • In Third Generation (1970’s) OS was more complex because they used concepts such as mul ...
... • All the OS was constructed in assembler language, reason why it was totally dependant of the machine. • The OS only can manipulate some peripherals. The batch processing was used to improve the resources use. • In Third Generation (1970’s) OS was more complex because they used concepts such as mul ...
Slide 2: Operating System Overview
... Operating systems are those programs that interface the machine with the applications programs. The main function of these systems is to dynamically allocate the shared system resources to the executing programs. As such, research in this area is clearly concerned with the management and scheduling ...
... Operating systems are those programs that interface the machine with the applications programs. The main function of these systems is to dynamically allocate the shared system resources to the executing programs. As such, research in this area is clearly concerned with the management and scheduling ...
System - Regis University: Academic Web Server for Faculty
... The basic unit of computer storage is the bit. A bit can contain one of two values, 0 and 1. All other storage in a computer is based on collections of bits. Given enough bits, it is amazing how many things a computer can represent: numbers, letters, images, movies, sounds, documents, and programs, ...
... The basic unit of computer storage is the bit. A bit can contain one of two values, 0 and 1. All other storage in a computer is based on collections of bits. Given enough bits, it is amazing how many things a computer can represent: numbers, letters, images, movies, sounds, documents, and programs, ...
Introduction
... – Hides the messy details which must be performed – Presents user with a virtual machine, easier to use ...
... – Hides the messy details which must be performed – Presents user with a virtual machine, easier to use ...
Operating Systems Review
... A program A command interpreter Interface between user and computer An interactive interface A programming language, a shell program is called a shell script ...
... A program A command interpreter Interface between user and computer An interactive interface A programming language, a shell program is called a shell script ...
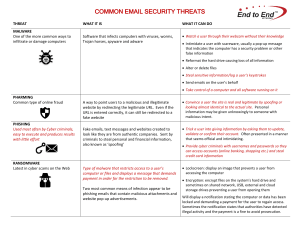
COMMON EMAIL SECURITY THREATS
... Convince a user the site is real and legitimate by spoofing or looking almost identical to the actual site. Personal information may be given unknowingly to someone with malicious intent. ...
... Convince a user the site is real and legitimate by spoofing or looking almost identical to the actual site. Personal information may be given unknowingly to someone with malicious intent. ...
IP security - WordPress.com
... Updating the operating system and application code to the latest version Each OS has its own security but some different steps must be taken to secure OS. ...
... Updating the operating system and application code to the latest version Each OS has its own security but some different steps must be taken to secure OS. ...
Operating systems
... History of operating system A major drawback to using a computer operator as intermediary is that the users have no interaction with their jobs once they are submitted to the operator. New operating systems were developed that allowed a program being executed to carry on a dialogue with the user ...
... History of operating system A major drawback to using a computer operator as intermediary is that the users have no interaction with their jobs once they are submitted to the operator. New operating systems were developed that allowed a program being executed to carry on a dialogue with the user ...
unix intro
... What is an Operating System? • Do we want all programs to have access to all instructions? • The OS is a program that acts as an intermediary between the application programs and the hardware resources – All communication requires hardware resources, thus the OS is also an intermediary between user ...
... What is an Operating System? • Do we want all programs to have access to all instructions? • The OS is a program that acts as an intermediary between the application programs and the hardware resources – All communication requires hardware resources, thus the OS is also an intermediary between user ...
Course Overview, History
... – Does the programmer need to write a single program that performs many independent activities? – Does every program have to be altered for every piece of hardware? – Does a faulty program crash everything? – Does every program have access to all hardware? ...
... – Does the programmer need to write a single program that performs many independent activities? – Does every program have to be altered for every piece of hardware? – Does a faulty program crash everything? – Does every program have access to all hardware? ...
Operating system organization
... organizations Time-sharing system Supports multiple processes Disk files and I/O devices are treated similarly ...
... organizations Time-sharing system Supports multiple processes Disk files and I/O devices are treated similarly ...