Overview - Seattle University
... – Group identifier (group ID) allows set of users to be defined and controls managed, then also associated with each process, file – Privilege escalation allows user to change to effective ID with more rights ...
... – Group identifier (group ID) allows set of users to be defined and controls managed, then also associated with each process, file – Privilege escalation allows user to change to effective ID with more rights ...
Security+ Guide to Network Security Fundamentals
... Firewall system examines each packet that enters it and allows through only those packets that match a predefined set of rules Can be configured to screen information based on many data fields: ...
... Firewall system examines each packet that enters it and allows through only those packets that match a predefined set of rules Can be configured to screen information based on many data fields: ...
Shim
... complexity which makes compromise inevitable. There are many solutions that have been proposed for enhancing security in these systems such as microkernel and virtual machine monitors (VMM). These solutions provide CPU and memory isolation, but applications still rely on operating system (OS) servic ...
... complexity which makes compromise inevitable. There are many solutions that have been proposed for enhancing security in these systems such as microkernel and virtual machine monitors (VMM). These solutions provide CPU and memory isolation, but applications still rely on operating system (OS) servic ...
Chapter 6 Introduction to Network Operating Systems
... whether it is configured as a workstation or a server. • Text editors are essential for performing any type of maintenance tasks that a user or an administrator may need to do. • Some examples of text editors available in Linux are vi, jed, pico, or Emacs. ...
... whether it is configured as a workstation or a server. • Text editors are essential for performing any type of maintenance tasks that a user or an administrator may need to do. • Some examples of text editors available in Linux are vi, jed, pico, or Emacs. ...
overhead - the denning institute
... Allocation of Resources. Many resources such as CPU cycles, disk sectors, main-memory page frames, local-network packet slots, and shared files can be used by only one task at a time. To prevent conflicts and deadlocks, operating systems implement schedulers for these resources. The time spent runn ...
... Allocation of Resources. Many resources such as CPU cycles, disk sectors, main-memory page frames, local-network packet slots, and shared files can be used by only one task at a time. To prevent conflicts and deadlocks, operating systems implement schedulers for these resources. The time spent runn ...
Operating System Security (II)
... USTC-21000201-OPERATING SYSTEMS; FALL 2014; INSTRUCTOR: CHI ZHANG ...
... USTC-21000201-OPERATING SYSTEMS; FALL 2014; INSTRUCTOR: CHI ZHANG ...
Architecting High-Security Systems for Multilateral
... high-security multilevel workstation which is able to concurrently handle multiple, strictly separated sessions. In fact it enables the user to securely access multiple, differently classified networks from within a single system. Nonetheless, the separation of those networks is maintained at all ti ...
... high-security multilevel workstation which is able to concurrently handle multiple, strictly separated sessions. In fact it enables the user to securely access multiple, differently classified networks from within a single system. Nonetheless, the separation of those networks is maintained at all ti ...
lec01
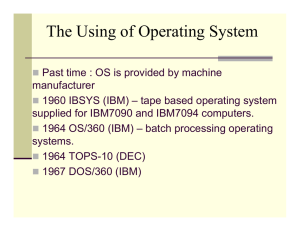
... Approached Bill Gates to see if he can build one Gates approached Seattle computer products, bought 86DOS and created MS-DOS Goal: finish quickly and run existing CP/M software OS becomes subroutine library and command executive ...
... Approached Bill Gates to see if he can build one Gates approached Seattle computer products, bought 86DOS and created MS-DOS Goal: finish quickly and run existing CP/M software OS becomes subroutine library and command executive ...
here - Online Journal of Space Communication
... • Multilevel security - encrypted data transfer with distributed administration • Assures access due to multi-tier priority scheme and automatic queue management • Packetization and data scheduling provides flexibility and efficiency in intermixing and transferring all types of files (data, software ...
... • Multilevel security - encrypted data transfer with distributed administration • Assures access due to multi-tier priority scheme and automatic queue management • Packetization and data scheduling provides flexibility and efficiency in intermixing and transferring all types of files (data, software ...
Introduction - UW Courses Web Server
... Each user has at least one separate program in memory. A program in execution is referred to as a process. Process switch occur so frequently that the users can interact with each program while it is running. File system allows users to access data and program interactively. CSS430 Introduction ...
... Each user has at least one separate program in memory. A program in execution is referred to as a process. Process switch occur so frequently that the users can interact with each program while it is running. File system allows users to access data and program interactively. CSS430 Introduction ...
BAB 8 SISTEM PENGOPERASIAN
... The act of managing computer memory. The management of main memory is critical to the computer system. Virtual memory systems separate the memory addresses used by a process from actual physical addresses, allowing separation of processes and increasing the effectively available amount of RAM ...
... The act of managing computer memory. The management of main memory is critical to the computer system. Virtual memory systems separate the memory addresses used by a process from actual physical addresses, allowing separation of processes and increasing the effectively available amount of RAM ...
NT Security Overview
... • Windows NT has gone through many updates, the latest version, 4.0, was released in 1996. • Windows NT, under the ownership of a single company, Microsoft, does not suffer the same level of security issues as operation systems such as UNIX • Although Windows NT has better security than most operati ...
... • Windows NT has gone through many updates, the latest version, 4.0, was released in 1996. • Windows NT, under the ownership of a single company, Microsoft, does not suffer the same level of security issues as operation systems such as UNIX • Although Windows NT has better security than most operati ...
Operating Systems I Introduction to Operating Systems MCT260-Operating Systems I
... • There are many types of computers intended for various purposes. Therefore, they operate in different ways. • The operating system dictates what the computer can do and how the computer does it. MCT260-Operating Systems I ...
... • There are many types of computers intended for various purposes. Therefore, they operate in different ways. • The operating system dictates what the computer can do and how the computer does it. MCT260-Operating Systems I ...
Introduction - University of Pennsylvania
... OS read routine examines the parameters, checks for errors (e.g. file must be open), consults its file table, and determines the disk address from where data is to be retrieved then it sets up registers to initiate transfer by the disk controller ...
... OS read routine examines the parameters, checks for errors (e.g. file must be open), consults its file table, and determines the disk address from where data is to be retrieved then it sets up registers to initiate transfer by the disk controller ...
why uclinux? - Wireless Africa
... based on microprocessors lacking MMU could not take advantage of Linux uCliknux was started by Arcturus networks in 1997 Implements Linux on MMU-less processors Publicly released back into open source as alternative OS for the Palm Pilot in February 1998 Ported to ARM, MIPS, SPARC, Hitachi SH, Motor ...
... based on microprocessors lacking MMU could not take advantage of Linux uCliknux was started by Arcturus networks in 1997 Implements Linux on MMU-less processors Publicly released back into open source as alternative OS for the Palm Pilot in February 1998 Ported to ARM, MIPS, SPARC, Hitachi SH, Motor ...
Chapter 4 (b) - Jhasudan.com.np
... high-level language program, in which case the calls normally resemble predefined function or subroutine calls. ◦ System calls can be roughly grouped into five major categories : process control, file manipulation, device manipulation, information maintenance, and communications. © Oxford University ...
... high-level language program, in which case the calls normally resemble predefined function or subroutine calls. ◦ System calls can be roughly grouped into five major categories : process control, file manipulation, device manipulation, information maintenance, and communications. © Oxford University ...
Windows NT Operating System
... • Windows NT servers are called protected subsystem because each one resides in a separate process whose memory is protected from other processes by the NT executive’s virtual memory system. They communicate with each other by passing messages. • The NT executive is capable of supporting any number ...
... • Windows NT servers are called protected subsystem because each one resides in a separate process whose memory is protected from other processes by the NT executive’s virtual memory system. They communicate with each other by passing messages. • The NT executive is capable of supporting any number ...
Chapter 10 PowerPoint
... • To mount a volume, the OS must be given the device name and the mount point (the location within the file structure where the new file system will be attached). • What happens if a file system is mounted over a directory that contains files? • Example: Macintosh searches new devices for file syste ...
... • To mount a volume, the OS must be given the device name and the mount point (the location within the file structure where the new file system will be attached). • What happens if a file system is mounted over a directory that contains files? • Example: Macintosh searches new devices for file syste ...
Router/Switch Security
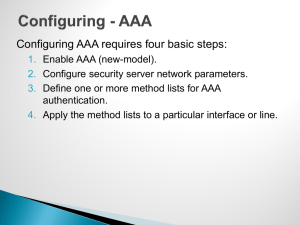
... Community strings should be treated like a password, chose carefully and change at regular ...
... Community strings should be treated like a password, chose carefully and change at regular ...
2.3 Operating System Design and Implementation
... systems implementation language, for implementing operating systems are the same as those accrued when the language is used for application programs: the code can be written faster, is more compact, and is easier to understand and debug. In addition, improvements in compiler technology will improve ...
... systems implementation language, for implementing operating systems are the same as those accrued when the language is used for application programs: the code can be written faster, is more compact, and is easier to understand and debug. In addition, improvements in compiler technology will improve ...
Understanding Internetworking Infrastructure
... users into revealing sensitive information or gaining unauthorized access privileges. Cybercrimes: Illegal activities executed on the Internet. Identify theft: A criminal (the identity thief) poses as someone else. Cyberwar: War in which a country’s information systems could be paralyzed from a mass ...
... users into revealing sensitive information or gaining unauthorized access privileges. Cybercrimes: Illegal activities executed on the Internet. Identify theft: A criminal (the identity thief) poses as someone else. Cyberwar: War in which a country’s information systems could be paralyzed from a mass ...
Processes
... • What is an Operating System? • Various systems and their pros and cons – E.g. multi-tasking vs. Batch ...
... • What is an Operating System? • Various systems and their pros and cons – E.g. multi-tasking vs. Batch ...
Lecture 1 Overview and History
... manipulation and storage devices rather than machines that perform arithmetic operations. Networking becomes very important, and as sharing becomes an important part of the experience so does security. Operating systems become more sophisticated. Start putting back features present in the old ti ...
... manipulation and storage devices rather than machines that perform arithmetic operations. Networking becomes very important, and as sharing becomes an important part of the experience so does security. Operating systems become more sophisticated. Start putting back features present in the old ti ...
Introduction CS 239 Security for Networks and System
... allow sendmail_t etc_aliases_t:file { read write }; allow sendmail_t etc_mail_t:dir { read search add_name remove_name }; allow sendmail_t etc_mail_t:file { create read write unlink }; ...
... allow sendmail_t etc_aliases_t:file { read write }; allow sendmail_t etc_mail_t:dir { read search add_name remove_name }; allow sendmail_t etc_mail_t:file { create read write unlink }; ...
An Overview Of Windows Nt System
... • Layered model is one which divides the O/S into modules and layers them one on top of the other. Each module provides a set of functions that other modules can call. ...
... • Layered model is one which divides the O/S into modules and layers them one on top of the other. Each module provides a set of functions that other modules can call. ...