Network Security - School of Computing and Engineering
... intrusive activity prior to exfiltration. – Seemed to be folcused on maintenance of their presence within the network – When detected IS would block the link. – Apparently intruders were able to open up other links undetected to continue their reconaissance. ...
... intrusive activity prior to exfiltration. – Seemed to be folcused on maintenance of their presence within the network – When detected IS would block the link. – Apparently intruders were able to open up other links undetected to continue their reconaissance. ...
Exam 1 Study Guide
... Integrated software applications are single applications that can perform a variety of commonly used tools found in productivity software. Software suites are a group of several software applications that have been bundled together as a package. Software applications that belong to a suite tend to w ...
... Integrated software applications are single applications that can perform a variety of commonly used tools found in productivity software. Software suites are a group of several software applications that have been bundled together as a package. Software applications that belong to a suite tend to w ...
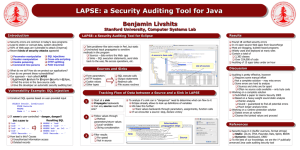
Auditing Java Code in Eclipse - Suif
... WHERE = `bob’ WHERE = `bob’ -- ’ WHERE bob’ or 1=1 -- ’ WHERE bob’; ...
... WHERE = `bob’ WHERE = `bob’ -- ’ WHERE bob’ or 1=1 -- ’ WHERE bob’; ...
Lab_1.pdf
... Introduction to Linux OS What is Linux? Linux is an operating system that was created by Linus Torvalds when he was a student at the University of Helsinki. Torvalds started Linux by writing a Kernel – the heart of the OS -, originally working with Minix, (a small UNIX system) decided to create an o ...
... Introduction to Linux OS What is Linux? Linux is an operating system that was created by Linus Torvalds when he was a student at the University of Helsinki. Torvalds started Linux by writing a Kernel – the heart of the OS -, originally working with Minix, (a small UNIX system) decided to create an o ...
ch11
... File-open count: counter of number of times a file is open – to allow removal of data from open-file table when last processes closes it Disk location of the file: cache of data access information Access rights: per-process access mode information ...
... File-open count: counter of number of times a file is open – to allow removal of data from open-file table when last processes closes it Disk location of the file: cache of data access information Access rights: per-process access mode information ...
Figure 11.01 - 醫學資訊系 鄭仁亮教授
... File-open count: counter of number of times a file is open – to allow removal of data from open-file table when last processes closes it Disk location of the file: cache of data access information Access rights: per-process access mode information ...
... File-open count: counter of number of times a file is open – to allow removal of data from open-file table when last processes closes it Disk location of the file: cache of data access information Access rights: per-process access mode information ...
interrupt
... Process termination requires reclaim of any reusable resources Single-threaded process has one program counter specifying location of next instruction to execute Process executes instructions sequentially, one at a time, until ...
... Process termination requires reclaim of any reusable resources Single-threaded process has one program counter specifying location of next instruction to execute Process executes instructions sequentially, one at a time, until ...
Computer Hardware
... Allocates resources such as memory, CPU time, and I/O devices to programs Protects users and programs from each other and provides for inter-program communication Provides feedback to the system administrators to permit performance optimization of the computer system Chapter 13 Operating Syste ...
... Allocates resources such as memory, CPU time, and I/O devices to programs Protects users and programs from each other and provides for inter-program communication Provides feedback to the system administrators to permit performance optimization of the computer system Chapter 13 Operating Syste ...
Operating System Objectives and Functions
... What is a process? A program in execution An instance of a program running on a computer The entity that can be assigned to and executed on a processor A unit of activity characterized by a single sequential thread of execution, a current state, and an associated set of system resources Difficulties ...
... What is a process? A program in execution An instance of a program running on a computer The entity that can be assigned to and executed on a processor A unit of activity characterized by a single sequential thread of execution, a current state, and an associated set of system resources Difficulties ...
Slide 1
... File System: Inode List • Inodes are used to access disk files. • Inodes maps the disk files • For each file there is an inode entry in the inode list block • Inode list also keeps track of directory structure ...
... File System: Inode List • Inodes are used to access disk files. • Inodes maps the disk files • For each file there is an inode entry in the inode list block • Inode list also keeps track of directory structure ...
kernel-intro
... File System: Inode List • Inodes are used to access disk files. • Inodes maps the disk files • For each file there is an inode entry in the inode list block • Inode list also keeps track of directory structure ...
... File System: Inode List • Inodes are used to access disk files. • Inodes maps the disk files • For each file there is an inode entry in the inode list block • Inode list also keeps track of directory structure ...
ch11.pdf
... The file system design deals with two distinct matters: 1. How should the file system look to the user. 2. Creating data structures and algorithms to map the logical file system onto the physical secondary storage device. ...
... The file system design deals with two distinct matters: 1. How should the file system look to the user. 2. Creating data structures and algorithms to map the logical file system onto the physical secondary storage device. ...
Document
... Exploit additional vulnerabilities to gain additional access and information to use in penetrating further into an organization. The hacker "becomes" a legitimate user (even an administrator). ...
... Exploit additional vulnerabilities to gain additional access and information to use in penetrating further into an organization. The hacker "becomes" a legitimate user (even an administrator). ...
the user program.
... – stored at x0000 through x00FF in memory – called System Control Block in some architectures ...
... – stored at x0000 through x00FF in memory – called System Control Block in some architectures ...
Distributed File Systems
... For each direction, a CPU overhead of running the communication protocol software ...
... For each direction, a CPU overhead of running the communication protocol software ...
networkworld - Sift Security
... B. Investigators determine what workstation made the connection. C. They look for anomalous activity associated with that workstation and find reconnaissance activity. D. They discover malware on the workstation (ws02.siftsec.com) and pivot to find it on a second workstation (ws35.siftsec.com). E. T ...
... B. Investigators determine what workstation made the connection. C. They look for anomalous activity associated with that workstation and find reconnaissance activity. D. They discover malware on the workstation (ws02.siftsec.com) and pivot to find it on a second workstation (ws35.siftsec.com). E. T ...
Intrusion Detection Prevention Systems
... IDPS technologies was the use of protocol analyzers. • Protocol analyzers can natively decode applicationlayer network protocols, like HTTP or FTP. Once the protocols are fully decoded, the IPS analysis engine can evaluate different parts of the protocol for anomalous behavior or exploits against pr ...
... IDPS technologies was the use of protocol analyzers. • Protocol analyzers can natively decode applicationlayer network protocols, like HTTP or FTP. Once the protocols are fully decoded, the IPS analysis engine can evaluate different parts of the protocol for anomalous behavior or exploits against pr ...
introduction
... Sharing: how are resources shared? Naming: how are resources named by users? Protection: how are distrusting parties protected from each other? Security: how to authenticate, authorize and ensure privacy? Performance: why is it so slow? ...
... Sharing: how are resources shared? Naming: how are resources named by users? Protection: how are distrusting parties protected from each other? Security: how to authenticate, authorize and ensure privacy? Performance: why is it so slow? ...
Office Hours: refer to Schedule
... o the danger of races and indeterminacy o the need for synchronization o synchronization tools o POSIX threads, UNIX processes o the danger of deadlock o techniques for dealing with deadlock operating system functions o user management o filesystem management o I/O management o process management o ...
... o the danger of races and indeterminacy o the need for synchronization o synchronization tools o POSIX threads, UNIX processes o the danger of deadlock o techniques for dealing with deadlock operating system functions o user management o filesystem management o I/O management o process management o ...
History of OS - EECG Toronto
... • Multiple users cannot concurrently access the computer • Efficiency • CPU is idle while the computer is doing I/O ...
... • Multiple users cannot concurrently access the computer • Efficiency • CPU is idle while the computer is doing I/O ...
CIS 442_Chapter5_
... • A botnet is a collection of compromised computers (members) that are controlled remotely by their (illegitimate) owner, who is often referred to as a “botherd” or “botherder.” • Each member computer of a botnet is running a bot program and these programs work either separately (stealing personal d ...
... • A botnet is a collection of compromised computers (members) that are controlled remotely by their (illegitimate) owner, who is often referred to as a “botherd” or “botherder.” • Each member computer of a botnet is running a bot program and these programs work either separately (stealing personal d ...
Chapter 2 Operating System Overview
... Each (guest) operating system runs in a virtual machine (VM), and can execute multiple applications Guest operating systems execute as if they were interacting directly with the hardware, but in fact they are interacting with a Virtual Machine Monitor (VMM) which runs directly on the hardware or on ...
... Each (guest) operating system runs in a virtual machine (VM), and can execute multiple applications Guest operating systems execute as if they were interacting directly with the hardware, but in fact they are interacting with a Virtual Machine Monitor (VMM) which runs directly on the hardware or on ...
dsk-01-intro
... Many types of resources - Some (such as CPU cycles, main memory, and file storage) may have special allocation code, others (such as I/O devices) may have general request and release code. ...
... Many types of resources - Some (such as CPU cycles, main memory, and file storage) may have special allocation code, others (such as I/O devices) may have general request and release code. ...