Computer Security and Penetration Testing Chapter 16 Windows
... to access resources on another domain, without being authenticated by it ...
... to access resources on another domain, without being authenticated by it ...
03-os-design
... UNIX was conventionally a monolithic design. Linux started as a monolithic kernel but with the increasing use of modules, the kernel can be made smaller and less monolithic ...
... UNIX was conventionally a monolithic design. Linux started as a monolithic kernel but with the increasing use of modules, the kernel can be made smaller and less monolithic ...
Computers: Tools for an Information Age
... Runs on just about every type of system Run on most main frame, supercomputers, Sun workstations, PC ...
... Runs on just about every type of system Run on most main frame, supercomputers, Sun workstations, PC ...
Chapter 02: Operating System Overview
... – Secondary storage devices – Transfer of blocks of data ...
... – Secondary storage devices – Transfer of blocks of data ...
SRA Customized Web Portal | Secure Remote Access | SonicWALL
... The personalized portal serves two purposes; first, it displays only those assets that each user is authorized to access based on corporate policy, and second, it provides an easy to use interface to make the end-user experience simple and straightforward. ...
... The personalized portal serves two purposes; first, it displays only those assets that each user is authorized to access based on corporate policy, and second, it provides an easy to use interface to make the end-user experience simple and straightforward. ...
computer security - GH Raisoni Polytechnic, Nagpur
... Authorization is the process of giving someone permission to do or have something. In multi-user computer systems, a system administrator defines for the system which users are allowed access to the system and what privileges of use (such as access to which file directories, hours of access, amoun ...
... Authorization is the process of giving someone permission to do or have something. In multi-user computer systems, a system administrator defines for the system which users are allowed access to the system and what privileges of use (such as access to which file directories, hours of access, amoun ...
Slides - Bilkent University Computer Engineering Department
... – Huge range, including denial-of-service, worms, viruses, identity theft, theft of service Systems generally first distinguish among users, to determine who can do what – User identities (user IDs, security IDs) include name and associated number, one per user – User ID then associated with all fil ...
... – Huge range, including denial-of-service, worms, viruses, identity theft, theft of service Systems generally first distinguish among users, to determine who can do what – User identities (user IDs, security IDs) include name and associated number, one per user – User ID then associated with all fil ...
history
... – hardware relocation base and limit registers » read/write/execute protected access ...
... – hardware relocation base and limit registers » read/write/execute protected access ...
Chapter 1: Introduction
... – Huge range, including denial-of-service, worms, viruses, identity theft, theft of service Systems generally first distinguish among users, to determine who can do what – User identities (user IDs, security IDs) include name and associated number, one per user – User ID then associated with all fil ...
... – Huge range, including denial-of-service, worms, viruses, identity theft, theft of service Systems generally first distinguish among users, to determine who can do what – User identities (user IDs, security IDs) include name and associated number, one per user – User ID then associated with all fil ...
Internal Networks and Physical Attacks
... including the remote access server. An IDS attack signature or policy consists of any pattern that constitutes exploiting a known security defect or executing a corporate security violation. These patterns are then monitored within the network data or on a host. The level of sophistication of attack ...
... including the remote access server. An IDS attack signature or policy consists of any pattern that constitutes exploiting a known security defect or executing a corporate security violation. These patterns are then monitored within the network data or on a host. The level of sophistication of attack ...
Operating Systems 2230 Lecture 1: Introduction to Operating Systems
... Traditionally, we would summarize an operating system’s goals as making “the system” convenient to use and scheduling its resources efficiently and fairly. In addition it must support hardware and software not yet developed. Operating System 6= User/Computer Interface An operating system is often si ...
... Traditionally, we would summarize an operating system’s goals as making “the system” convenient to use and scheduling its resources efficiently and fairly. In addition it must support hardware and software not yet developed. Operating System 6= User/Computer Interface An operating system is often si ...
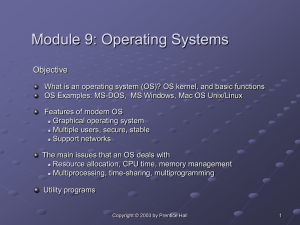
1. Introduction about operating system. 2. What is 32 bit
... Q. What is the difference between 32-bit and 64-bit versions of operating system? Ans: The terms 32-bit and 64-bit refer to the way a computer's processor (also called a CPU), handles information. The 64-bit version of Windows handles large amounts of random access memory (RAM) more effectively than ...
... Q. What is the difference between 32-bit and 64-bit versions of operating system? Ans: The terms 32-bit and 64-bit refer to the way a computer's processor (also called a CPU), handles information. The 64-bit version of Windows handles large amounts of random access memory (RAM) more effectively than ...
Booting process is in progress
... Q. What is the difference between 32-bit and 64-bit versions of operating system? Ans: The terms 32-bit and 64-bit refer to the way a computer's processor (also called a CPU), handles information. The 64-bit version of Windows handles large amounts of random access memory (RAM) more effectively than ...
... Q. What is the difference between 32-bit and 64-bit versions of operating system? Ans: The terms 32-bit and 64-bit refer to the way a computer's processor (also called a CPU), handles information. The 64-bit version of Windows handles large amounts of random access memory (RAM) more effectively than ...
CS 519 -- Operating Systems -
... Internal names: i-node in UNIX - an index into an array of file descriptors/headers for a volume Directory: translation from external to internal name May have more than one external name for a single internal name ...
... Internal names: i-node in UNIX - an index into an array of file descriptors/headers for a volume Directory: translation from external to internal name May have more than one external name for a single internal name ...
Operating Systems
... memory divided by the page size - Page frame = size of memory/page size • How many bits does the system use to maintain the displacement = as much as page size • Ex: contains 128MB of main memory and has a page size of 8KB ...
... memory divided by the page size - Page frame = size of memory/page size • How many bits does the system use to maintain the displacement = as much as page size • Ex: contains 128MB of main memory and has a page size of 8KB ...
The Macintosh File System (continued)
... Designing a Directory Structure (continued) • Consider directories for the following: – Operating system files – Software applications – Work files, such as word processing, graphics, spreadsheets, and database files – Public files that you share over the network – Utilities files – Temporary files ...
... Designing a Directory Structure (continued) • Consider directories for the following: – Operating system files – Software applications – Work files, such as word processing, graphics, spreadsheets, and database files – Public files that you share over the network – Utilities files – Temporary files ...
PPT
... Operating System Concepts, 7th Edition, by Silberschatz, Galvin, and Gagne, John Wiley & Sons, ...
... Operating System Concepts, 7th Edition, by Silberschatz, Galvin, and Gagne, John Wiley & Sons, ...
CPS 210 Course Intro - Duke Computer Science
... The OS and User Applications The OS defines a framework for users and their programs to coexist, cooperate, and work together safely, supporting: • concurrent execution/interaction of multiple user programs • shared implementations of commonly needed facilities “The system is all the code you didn’ ...
... The OS and User Applications The OS defines a framework for users and their programs to coexist, cooperate, and work together safely, supporting: • concurrent execution/interaction of multiple user programs • shared implementations of commonly needed facilities “The system is all the code you didn’ ...
Chapter 1
... and programs, and its data are lost when power is lost, the computer system must provide secondary storage to back up main memory. Secondary storage consists of tapes, disks, and other media designed to hold information that will eventually be accessed in primary storage. Storage is ordinarily divid ...
... and programs, and its data are lost when power is lost, the computer system must provide secondary storage to back up main memory. Secondary storage consists of tapes, disks, and other media designed to hold information that will eventually be accessed in primary storage. Storage is ordinarily divid ...
Web Application Security Vulnerabilities Yen
... web applications allow administrators to access the site using a web interface. If these administrative functions are not very carefully protected, an attacker can gain full access to all aspects of a site. ...
... web applications allow administrators to access the site using a web interface. If these administrative functions are not very carefully protected, an attacker can gain full access to all aspects of a site. ...
Firewalls
... network layer firewall is the router. • Filters out traffic based on source and destination IP addresses and ports. • Usually fast and operate transparently to the user. ...
... network layer firewall is the router. • Filters out traffic based on source and destination IP addresses and ports. • Usually fast and operate transparently to the user. ...