Curriculum Group Report-F2011
... Course Description Recommendations – This course covers command line, scripting and lowlevel (C language) system interfaces for Unix. It covers basic commands, shell and other scripting languages as appropriate; and low-level POSIX interfaces in C, including file I/O, process control, inter-process ...
... Course Description Recommendations – This course covers command line, scripting and lowlevel (C language) system interfaces for Unix. It covers basic commands, shell and other scripting languages as appropriate; and low-level POSIX interfaces in C, including file I/O, process control, inter-process ...
Slides - Winlab
... The permissions can be modified with chmod The owner (and group) can be modified with chown The permission are read –uuugggwww where u = user, g = group, w = world r = read, w = write, x = execute privileges permissions can be assigned numerically if you assume that each position is a 3 bit number, ...
... The permissions can be modified with chmod The owner (and group) can be modified with chown The permission are read –uuugggwww where u = user, g = group, w = world r = read, w = write, x = execute privileges permissions can be assigned numerically if you assume that each position is a 3 bit number, ...
Lecture 1 Operating System Overview
... and controls managed, then also associated with each process, file ...
... and controls managed, then also associated with each process, file ...
Department of CSE
... 13. What is the main advantage for an OS designer of using virtual machine architecture? 14. Describe the action taken by a kernel to context switch between processes? 15. Describe the difference among short-term, medium-term and long-term scheduling. 16. What are the differences between user level ...
... 13. What is the main advantage for an OS designer of using virtual machine architecture? 14. Describe the action taken by a kernel to context switch between processes? 15. Describe the difference among short-term, medium-term and long-term scheduling. 16. What are the differences between user level ...
Unit 13: IT Essentials II: Network Operating Systems
... (AUP), username and password standards, rules for network access, policy for disposal of materials (data and hardware), virus protection standards, on-line security resources Threats to network security: internal/external security, outside threats, Denial of Service (DoS), Inside threats, on-line se ...
... (AUP), username and password standards, rules for network access, policy for disposal of materials (data and hardware), virus protection standards, on-line security resources Threats to network security: internal/external security, outside threats, Denial of Service (DoS), Inside threats, on-line se ...
Chapter One
... As with software changes, you should provide a way to reverse the hardware upgrade and reinstall the old hardware if necessary Keep the old component safe, as you not only might you need to put it back in the device, but you might also need to refer to it for ...
... As with software changes, you should provide a way to reverse the hardware upgrade and reinstall the old hardware if necessary Keep the old component safe, as you not only might you need to put it back in the device, but you might also need to refer to it for ...
File
... Integration with ReactOS. Virtual frame buffer support. Support for more host operating systems such as FreeBSD. ...
... Integration with ReactOS. Virtual frame buffer support. Support for more host operating systems such as FreeBSD. ...
An Introduction to Linux Operating System
... A wide variety of commercial software is available if not satisfied by the free software Easily upgradeable. Supports multiple processors. True multi-tasking, multi-user OS. An excellent window system called X, the equivalent of Windows but much more flexible. Full source code is provided and free. ...
... A wide variety of commercial software is available if not satisfied by the free software Easily upgradeable. Supports multiple processors. True multi-tasking, multi-user OS. An excellent window system called X, the equivalent of Windows but much more flexible. Full source code is provided and free. ...
Slide 1
... Operating systems that support multithreading have the ability to rotate between multiple threads. If a computer has two or more CPUs, techniques that perform operations simultaneously are possible. Multiprocessing Parallel processing ...
... Operating systems that support multithreading have the ability to rotate between multiple threads. If a computer has two or more CPUs, techniques that perform operations simultaneously are possible. Multiprocessing Parallel processing ...
Chapter 9
... Securing Traffic with IPSec IPSec allows us to protect our network from within IPSec secures the IP protocol IPSec has two principle goals: To protect the contents of IP packets To provide defense against network attacks through packet filtering and the enforcement of trusted communicatio ...
... Securing Traffic with IPSec IPSec allows us to protect our network from within IPSec secures the IP protocol IPSec has two principle goals: To protect the contents of IP packets To provide defense against network attacks through packet filtering and the enforcement of trusted communicatio ...
ISA_673-android_presentation_(3) - eee
... • Project Goals – Track usage by resource and process – Modify resource scheduling to ensure fairness ...
... • Project Goals – Track usage by resource and process – Modify resource scheduling to ensure fairness ...
Safe internet Network Base for schools and business use: Οδηγός
... Where various user profiles are required, the school needs to separate the devices on his network in such a way as to ensure that online communication uses different public IP addresses. Every device on the school’s premises must be connected to the Internet via the IP address with which the corresp ...
... Where various user profiles are required, the school needs to separate the devices on his network in such a way as to ensure that online communication uses different public IP addresses. Every device on the school’s premises must be connected to the Internet via the IP address with which the corresp ...
ships with the operating system
... Protection – any mechanism for controlling access of processes or ...
... Protection – any mechanism for controlling access of processes or ...
Secure your remote access with VASCO and
... while remaining easy-to-use When employees use their PC, they want to read e-mail, use software and documents, access files on the corporate network, work with applications and access websites. With the workforce becoming more mobile, the employees want to do all this anywhere and any time. SSL VPN ...
... while remaining easy-to-use When employees use their PC, they want to read e-mail, use software and documents, access files on the corporate network, work with applications and access websites. With the workforce becoming more mobile, the employees want to do all this anywhere and any time. SSL VPN ...
Syllabus
... - The main aspect of job scheduling is the ability to multiprogram. - Multiprogramming increases CPU utilization by organizing jobs such that the CPU always has on to execute. - The idea: The OS keeps several jobs in memory at a time. This set of jobs is the subset of the jobs kept in the job pool. ...
... - The main aspect of job scheduling is the ability to multiprogram. - Multiprogramming increases CPU utilization by organizing jobs such that the CPU always has on to execute. - The idea: The OS keeps several jobs in memory at a time. This set of jobs is the subset of the jobs kept in the job pool. ...
introduction - Eastern Mediterranean University
... File systems Device drivers System calls Interprocess communication Network protocols ...
... File systems Device drivers System calls Interprocess communication Network protocols ...
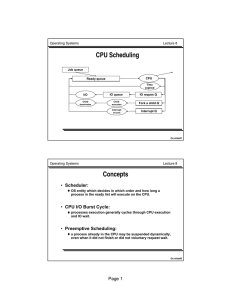
Page 1 • Scheduler: • CPU I/O Burst Cycle: • Preemptive Scheduling:
... • Scheduler: OS entity which decides in which order and how long a process in the ready list will execute on the CPU. ...
... • Scheduler: OS entity which decides in which order and how long a process in the ready list will execute on the CPU. ...
Operating Systems
... between user programs and the hardware of the computer on which they run. The operating system is responsible for allowing resources (such as processors, disks or networks) to be shared, providing common services needed by many different programs (e.g., file service, the ability to start or stop pro ...
... between user programs and the hardware of the computer on which they run. The operating system is responsible for allowing resources (such as processors, disks or networks) to be shared, providing common services needed by many different programs (e.g., file service, the ability to start or stop pro ...
Chapter 1
... Process input to faster device More efficient use of CPU Device Independence - program uses logical devices, not physical devices Overlap of I/O and CPU Processing • specialized card readers and printers • satellite processing - small computer does transfer from/to mag tape or disk ...
... Process input to faster device More efficient use of CPU Device Independence - program uses logical devices, not physical devices Overlap of I/O and CPU Processing • specialized card readers and printers • satellite processing - small computer does transfer from/to mag tape or disk ...
Powerpoint Slides
... Public key encryption scheme can also handle the problem of privacy. Sender uses the receiver’s public key to encode the message. Receiver uses it’s private key to decode the message. Messages can be encoded twice to authenticate the sender and to enforce privacy. First with the sender’s private ...
... Public key encryption scheme can also handle the problem of privacy. Sender uses the receiver’s public key to encode the message. Receiver uses it’s private key to decode the message. Messages can be encoded twice to authenticate the sender and to enforce privacy. First with the sender’s private ...
Overview of OS/2
... protected environment. The model consists of a hierarchy of multitasking objects called sessions, processes, and threads. The session is at the top of the hierarchy, and the thread is at the bottom. The session is the unit of user I/O device sharing. Processes are analogous to programs, and are the ...
... protected environment. The model consists of a hierarchy of multitasking objects called sessions, processes, and threads. The session is at the top of the hierarchy, and the thread is at the bottom. The session is the unit of user I/O device sharing. Processes are analogous to programs, and are the ...
Taxonomy of Computer Security Incidents
... • Incident Timestamp • Source IP, Destination IP, port, and protocol • Operating System, including version, patches, etc. • System Function (e.g., DNS/web server, workstation, etc.) • Antivirus software installed, including version, and latest updates • Location of the system(s) involved in the inci ...
... • Incident Timestamp • Source IP, Destination IP, port, and protocol • Operating System, including version, patches, etc. • System Function (e.g., DNS/web server, workstation, etc.) • Antivirus software installed, including version, and latest updates • Location of the system(s) involved in the inci ...