Abstract View of System Components
... – Conflicts with time-sharing systems, not supported by general-purpose operating systems. Soft real-time system. No deadline support – Limited utility in industrial control or robotics – Useful in applications (multimedia, virtual reality) requiring advanced operating-system features. ...
... – Conflicts with time-sharing systems, not supported by general-purpose operating systems. Soft real-time system. No deadline support – Limited utility in industrial control or robotics – Useful in applications (multimedia, virtual reality) requiring advanced operating-system features. ...
ppt
... no guarantee of integrity or confidentiality. ROM (read-only memory): provides integrity but not confidentiality; ROM may store (part of) the O/S. EPROM (erasable & programmable read-only memory): could store parts of the O/S or cryptographic keys; technologically more sophisticated attacks threaten ...
... no guarantee of integrity or confidentiality. ROM (read-only memory): provides integrity but not confidentiality; ROM may store (part of) the O/S. EPROM (erasable & programmable read-only memory): could store parts of the O/S or cryptographic keys; technologically more sophisticated attacks threaten ...
Minimalizace kybernetických rizik s platformou PikeOS
... The protection mechanism should grant access based on more than one piece of information (e.g., two keys are needed to open a vault-lock or defence in the depth). ...
... The protection mechanism should grant access based on more than one piece of information (e.g., two keys are needed to open a vault-lock or defence in the depth). ...
Final bits of OS - Department of Computer Science
... • The common version of the syslog protocol was originally developed on the University of California Berkeley Software Distribution (BSD) UNIX/TCP/IP system implementations • Messages in the BSD syslog format consist of: – PRI - facilities / severity code – header – timestamp and hostname/IP address ...
... • The common version of the syslog protocol was originally developed on the University of California Berkeley Software Distribution (BSD) UNIX/TCP/IP system implementations • Messages in the BSD syslog format consist of: – PRI - facilities / severity code – header – timestamp and hostname/IP address ...
OnLinePrivacy - Cal State LA
... her/him change the guest privileges to administrative privileges. ...
... her/him change the guest privileges to administrative privileges. ...
security threats: a guide for small and medium
... software. Employees and end-users within an organization may unknowingly introduce malware on the network when they run malicious executable code (EXE files). Sometimes they might receive an email with an attached worm or download spyware when visiting a malicious website. Alternatively, to get work ...
... software. Employees and end-users within an organization may unknowingly introduce malware on the network when they run malicious executable code (EXE files). Sometimes they might receive an email with an attached worm or download spyware when visiting a malicious website. Alternatively, to get work ...
The Mach System
... - A microkernel is physically divided into separate modules. It may consist of 1 or more layers – but only logically. - A layered kernel is physically divided into layers, but logically – it might consist of one or more modules. - A microkernel may be (and often is) logically single layered because ...
... - A microkernel is physically divided into separate modules. It may consist of 1 or more layers – but only logically. - A layered kernel is physically divided into layers, but logically – it might consist of one or more modules. - A microkernel may be (and often is) logically single layered because ...
Information Security
... Keeps track of “state”, blocks traffic that is not in its table of established connections Slower at screening traffic than packet filter, but more secure ...
... Keeps track of “state”, blocks traffic that is not in its table of established connections Slower at screening traffic than packet filter, but more secure ...
Introduction CS 239 Security for Networks and System
... – With relatively few modifications • To review, three subjects • Owner, group, other • and three modes – Read, write, execute – Sometimes these have special meanings CS 236 Online ...
... – With relatively few modifications • To review, three subjects • Owner, group, other • and three modes – Read, write, execute – Sometimes these have special meanings CS 236 Online ...
1.01
... and update pointer Read – read file contents at pointer location, update pointer Reposition within file (seek) – change pointer location Delete – free space and remove entry from directory ...
... and update pointer Read – read file contents at pointer location, update pointer Reposition within file (seek) – change pointer location Delete – free space and remove entry from directory ...
“CHEWBACCA” POS Malware
... Upon execution Chewbacca performs an external IP lookup by doing a GET request to ekiga[.]net, a legitimate service that replies with the IP address the request is sent from. The GET request is constructed with a non-standard User-Agent. Tor v0.2.3.25 is dropped as "tor.exe" to the user's Temp and r ...
... Upon execution Chewbacca performs an external IP lookup by doing a GET request to ekiga[.]net, a legitimate service that replies with the IP address the request is sent from. The GET request is constructed with a non-standard User-Agent. Tor v0.2.3.25 is dropped as "tor.exe" to the user's Temp and r ...
Chapter 5 - High Point University
... Distributed databases are being defined at least 2 ways. One divides a database and distributes its portions throughout a system, without duplicating the data. A network administrator can access any portion from any node (authorization). The second type of distributed database stores the same data a ...
... Distributed databases are being defined at least 2 ways. One divides a database and distributes its portions throughout a system, without duplicating the data. A network administrator can access any portion from any node (authorization). The second type of distributed database stores the same data a ...
What is Batch Processing Operating System?
... contention that can be found in a multiprocessor operating system: Locking system: In order to provide safe access to the resources shared among multiple processors, they need to be protected by locking scheme. The purpose of a locking is to serialize accesses to the protected resource by multiple p ...
... contention that can be found in a multiprocessor operating system: Locking system: In order to provide safe access to the resources shared among multiple processors, they need to be protected by locking scheme. The purpose of a locking is to serialize accesses to the protected resource by multiple p ...
Ceng 334 - Operating Systems
... • The scheduler allocates time based on execution priority, taking into account factors such as whether the thread belongs to a foreground or background process and how long it has been since the thread was last run • Win32 and DOS apps are preemptively multitasked. • Win16 apps are cooperatively mu ...
... • The scheduler allocates time based on execution priority, taking into account factors such as whether the thread belongs to a foreground or background process and how long it has been since the thread was last run • Win32 and DOS apps are preemptively multitasked. • Win16 apps are cooperatively mu ...
Chap 1: Introduction
... Individuals have sole use of computer and do not need advanced CPU utilization of protection features. User convenience and responsiveness not maximizing CPU and peripheral utilization Can adopt some of the technology developed for larger operating system. Not much of utilization Protection, a ...
... Individuals have sole use of computer and do not need advanced CPU utilization of protection features. User convenience and responsiveness not maximizing CPU and peripheral utilization Can adopt some of the technology developed for larger operating system. Not much of utilization Protection, a ...
Slide 1
... 4 File and System Backup A full backup makes a fresh copy of every file in the folders you’ve specified for the backup A differential backup makes a backup of only those files that were added or changed since your last full backup session An incremental backup makes a backup of the files that ...
... 4 File and System Backup A full backup makes a fresh copy of every file in the folders you’ve specified for the backup A differential backup makes a backup of only those files that were added or changed since your last full backup session An incremental backup makes a backup of the files that ...
ISA_673-android_presentation_(1) - eee
... Operating Systems Security Exploring the Android Platform ...
... Operating Systems Security Exploring the Android Platform ...
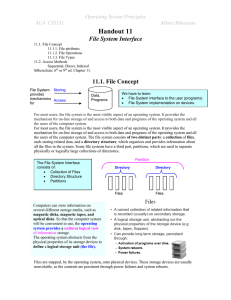
H 10.1. File-System Interface
... an existing file. These primitive operations may then be combined to perform other file operations. Most of the file operations mentioned involve searching the directory for the entry associated with the named file. To avoid this constant searching, many systems require that an open system call be u ...
... an existing file. These primitive operations may then be combined to perform other file operations. Most of the file operations mentioned involve searching the directory for the entry associated with the named file. To avoid this constant searching, many systems require that an open system call be u ...
Norman Matloff, Unix Processes
... A process is an instance of running a program. If, for example, three people are running the same program simultaneously, there are three processes there, not just one. In fact, we might have more than one process running even with only person executing the program, because (you will see later) the ...
... A process is an instance of running a program. If, for example, three people are running the same program simultaneously, there are three processes there, not just one. In fact, we might have more than one process running even with only person executing the program, because (you will see later) the ...
Lecture_1 - bridges to computing
... For Macintosh computers, Mac OS X, Linux, BSD, and some Windows variants are commonly used. Cellphones and other portable devices usually have their own custom build Operating Systems (Apple) but other portable OS are coming online (Android). ...
... For Macintosh computers, Mac OS X, Linux, BSD, and some Windows variants are commonly used. Cellphones and other portable devices usually have their own custom build Operating Systems (Apple) but other portable OS are coming online (Android). ...
ch06
... detection-specific audit records - IDS specific • additional overhead but specific to IDS task • often log individual elementary actions • e.g. may contain fields for: subject, action, object, ...
... detection-specific audit records - IDS specific • additional overhead but specific to IDS task • often log individual elementary actions • e.g. may contain fields for: subject, action, object, ...
Information Security - National University of Sciences and
... someone else to access/take control of your system • Facilitates hacking of system • Hacking: To enter somebody system/account in an illegal way ...
... someone else to access/take control of your system • Facilitates hacking of system • Hacking: To enter somebody system/account in an illegal way ...
Computer Software - :: Naresuan University
... as operating systems for network and Web servers? • Which application software packages are the most important for a business end user to know how to use? ...
... as operating systems for network and Web servers? • Which application software packages are the most important for a business end user to know how to use? ...
OS_Intro - SIUE Computer Science
... (3) OS is the government in your computer (the agent that allocate resources) OS provides “resource management” in your computer ...
... (3) OS is the government in your computer (the agent that allocate resources) OS provides “resource management” in your computer ...
Chapter 8 Operating Systems and Utility Programs
... Used by power users because of its flexibility and power ...
... Used by power users because of its flexibility and power ...