ch_04_ - wathana09
... Each subsystem has access to the other’s information All application programs utilize the same computer file, thereby simplifying operations Fewer backup files for security purposes Relieves some users from data-gathering responsibilities in situations where these users previously gathered t ...
... Each subsystem has access to the other’s information All application programs utilize the same computer file, thereby simplifying operations Fewer backup files for security purposes Relieves some users from data-gathering responsibilities in situations where these users previously gathered t ...
Data Entities
... Each subsystem has access to the other’s information All application programs utilize the same computer file, thereby simplifying operations Fewer backup files for security purposes Relieves some users from data-gathering responsibilities in situations where these users previously gathered their own ...
... Each subsystem has access to the other’s information All application programs utilize the same computer file, thereby simplifying operations Fewer backup files for security purposes Relieves some users from data-gathering responsibilities in situations where these users previously gathered their own ...
Operating Systems and File Management
... 041500 Time Machine is synchronization software used for backup on Macs. 041600 To repopulate a new hard disk from an incremental backup, you have to first restore a full backup. 041700 A boot disk contains a complete copy of your computer’s hard disk as it existed when the computer was new. C ...
... 041500 Time Machine is synchronization software used for backup on Macs. 041600 To repopulate a new hard disk from an incremental backup, you have to first restore a full backup. 041700 A boot disk contains a complete copy of your computer’s hard disk as it existed when the computer was new. C ...
PPT Chapter 13
... • Internal_id is the internal id of returned by the
open call
• Record_id is absent for sequential-access files
– Operation is performed on the next record
...
... • Internal_id is the internal id of
Accounting Information Systems: Essential Concepts
... Each subsystem has access to the other’s information All application programs utilize the same computer file, thereby simplifying operations Fewer backup files for security purposes Relieves some users from data-gathering responsibilities in situations where these users previously gathered t ...
... Each subsystem has access to the other’s information All application programs utilize the same computer file, thereby simplifying operations Fewer backup files for security purposes Relieves some users from data-gathering responsibilities in situations where these users previously gathered t ...
Slide 1
... 041500 Time Machine is synchronization software used for backup on Macs. 041600 To repopulate a new hard disk from an incremental backup, you have to first restore a full backup. 041700 A boot disk contains a complete copy of your computer’s hard disk as it existed when the computer was new. C ...
... 041500 Time Machine is synchronization software used for backup on Macs. 041600 To repopulate a new hard disk from an incremental backup, you have to first restore a full backup. 041700 A boot disk contains a complete copy of your computer’s hard disk as it existed when the computer was new. C ...
File System
... To avoid this constant searching, many operating systems require that an open() system call be made before a file is first used ...
... To avoid this constant searching, many operating systems require that an open() system call be made before a file is first used ...
Overview File Systems and
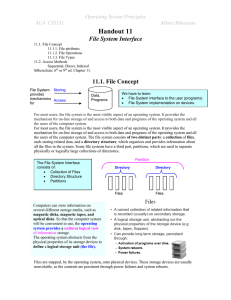
... A directory is a special file which is maintained by the file system, and which contains a list of entries. To a user, an entry appears to be a file and is accessed in terms of its symbolic entry name, which is the user's file name. An entry name need be unique only within the directory in which it ...
... A directory is a special file which is maintained by the file system, and which contains a list of entries. To a user, an entry appears to be a file and is accessed in terms of its symbolic entry name, which is the user's file name. An entry name need be unique only within the directory in which it ...
The SUMERIS Accounting System
... modules providing real-time accounting and business management software. Designed in a multi-threaded client/server architecture, it supports multiple network users and distributed information is made available to all client applications anywhere in a network. Network access to QuantaFlow is totally ...
... modules providing real-time accounting and business management software. Designed in a multi-threaded client/server architecture, it supports multiple network users and distributed information is made available to all client applications anywhere in a network. Network access to QuantaFlow is totally ...
PDF Slides - IIT Guwahati
... • On the other hand, a file or directory may be opened several times by the same process or by different processes, and thus have multiple different file descriptors. • Additionally, files or directories that are not currently open by any process do not have any file descriptors referring to th ...
... • On the other hand, a file or directory may be opened several times by the same process or by different processes, and thus have multiple different file descriptors. • Additionally, files or directories that are not currently open by any process do not have any file descriptors referring to th ...
Windows Vista system integrity technologies
... attempts to open process running as privileged user X for write, to bypass UAP and execute code will full privileges. MIC stops this because desired access is write. Admin (IL=high) runs downloaded program. Process runs as standard (not full) admin (IL=low). MIC prevents processes from write-accessi ...
... attempts to open process running as privileged user X for write, to bypass UAP and execute code will full privileges. MIC stops this because desired access is write. Admin (IL=high) runs downloaded program. Process runs as standard (not full) admin (IL=low). MIC prevents processes from write-accessi ...
Samba - Personal Web Pages
... Use a utility, smbclient (libsmb) installed with Samba to read the shares with a similar interface to a standard command line FTP program ...
... Use a utility, smbclient (libsmb) installed with Samba to read the shares with a similar interface to a standard command line FTP program ...
Music-- Capture it, Organize it and Enjoy it
... M3U but prefers another Microsoft file type, WPL. M3U has a very simple file structure which is just a text list of files. WPL is a little more complex and probably a little more capable and written in HTML. Both work fine and it is impossible to tell which is being used without looking at the file ...
... M3U but prefers another Microsoft file type, WPL. M3U has a very simple file structure which is just a text list of files. WPL is a little more complex and probably a little more capable and written in HTML. Both work fine and it is impossible to tell which is being used without looking at the file ...
H 10.1. File-System Interface
... In Windows the filename is longer. The executable file extensions are the same as in MS-DOS. All the other extensions are handled by appropriate applications or by OS itself. The UNIX system is unable to provide such a feature because it uses a crude magic number stored at the beginning of some file ...
... In Windows the filename is longer. The executable file extensions are the same as in MS-DOS. All the other extensions are handled by appropriate applications or by OS itself. The UNIX system is unable to provide such a feature because it uses a crude magic number stored at the beginning of some file ...
Slide 1
... 041500 Time Machine is synchronization software used for backup on Macs. 041600 To repopulate a new hard disk from an incremental backup, you have to first restore a full backup. 041700 A boot disk contains a complete copy of your computer’s hard disk as it existed when the computer was new. ...
... 041500 Time Machine is synchronization software used for backup on Macs. 041600 To repopulate a new hard disk from an incremental backup, you have to first restore a full backup. 041700 A boot disk contains a complete copy of your computer’s hard disk as it existed when the computer was new. ...
Windows Vista system integrity technologies
... attempts to open process running as privileged user X for write, to bypass UAP and execute code will full privileges. MIC stops this because desired access is write. Admin (IL=high) runs downloaded program. Process runs as standard (not full) admin (IL=low). MIC prevents processes from write-accessi ...
... attempts to open process running as privileged user X for write, to bypass UAP and execute code will full privileges. MIC stops this because desired access is write. Admin (IL=high) runs downloaded program. Process runs as standard (not full) admin (IL=low). MIC prevents processes from write-accessi ...
Slide 1
... A boot disk is a removable storage medium containing the operating system files needed to boot your computer without accessing the hard disk A recovery disk is a bootable CD, DVD, or other media that contains a complete copy of your computer’s hard disk as it existed when the computer was new ...
... A boot disk is a removable storage medium containing the operating system files needed to boot your computer without accessing the hard disk A recovery disk is a bootable CD, DVD, or other media that contains a complete copy of your computer’s hard disk as it existed when the computer was new ...
File Management
... A boot disk is a removable storage medium containing the operating system files needed to boot your computer without accessing the hard disk A recovery disk (sometimes referred to as a recovery CD) is a bootable CD, DVD, or other media that contains a complete copy of your computer’s hard disk a ...
... A boot disk is a removable storage medium containing the operating system files needed to boot your computer without accessing the hard disk A recovery disk (sometimes referred to as a recovery CD) is a bootable CD, DVD, or other media that contains a complete copy of your computer’s hard disk a ...
File Systems
... – an i-number is a unique (within a file system) identifier for a file or directory – given an i-number, the file system can find the data and meta-data for the file • Directories provide a way for applications to group related files • Since directories can be nested, a filesystem’s directories can ...
... – an i-number is a unique (within a file system) identifier for a file or directory – given an i-number, the file system can find the data and meta-data for the file • Directories provide a way for applications to group related files • Since directories can be nested, a filesystem’s directories can ...
Slide 1
... A. Google Chrome is built on the Windows kernel, so it is ideal for netbooks because it has good resistance to malware. B. If you don’t like the user interface for Windows but want to run the vast variety of Windows software, you can install Linux. C. Linux and Mac OS have a reputation for being mor ...
... A. Google Chrome is built on the Windows kernel, so it is ideal for netbooks because it has good resistance to malware. B. If you don’t like the user interface for Windows but want to run the vast variety of Windows software, you can install Linux. C. Linux and Mac OS have a reputation for being mor ...
Document
... For example: home directories would have read/write access for all known users, allowing each to access their own files Would still not have access to the files of others unless that permission would normally exist ...
... For example: home directories would have read/write access for all known users, allowing each to access their own files Would still not have access to the files of others unless that permission would normally exist ...