WWWTranscribe - A MODULAR TRANSCRIPTION SYSTEM BASED
... In a standard TCP/IP network configuration, WWWTranscribe requires a modern WWW browser, a helper application to output a-law signal files, the scripting environment perl, and TCP/IP access software. Most of the software can be obtained for free or a small shareware fee from Internet software archiv ...
... In a standard TCP/IP network configuration, WWWTranscribe requires a modern WWW browser, a helper application to output a-law signal files, the scripting environment perl, and TCP/IP access software. Most of the software can be obtained for free or a small shareware fee from Internet software archiv ...
第六章文件系统
... file is restored only one time. UNIX files may contain holes. The blocks in between are not part of the file and should not be dumped and not be restored. Special files, named files, and the like should never be ...
... file is restored only one time. UNIX files may contain holes. The blocks in between are not part of the file and should not be dumped and not be restored. Special files, named files, and the like should never be ...
Brocade 2007 - More than Fibre Channel SANs
... the iSNAP 2110 Processor on which it is based. The HBA offloads network processing from a server without modifying applications. Under heavy loads, this increases throughput by three to four times. This solution is for network-intensive applications, such as media streaming and voice over IP. File A ...
... the iSNAP 2110 Processor on which it is based. The HBA offloads network processing from a server without modifying applications. Under heavy loads, this increases throughput by three to four times. This solution is for network-intensive applications, such as media streaming and voice over IP. File A ...
sosftp - SOS
... considered successful if all the files in a group are successfully transferred, in the event of failure in transfer of any one of the files from a group the whole transfer will be “rolled back” and will be considered as unsuccessful. SOSFTP’s test mode provides ease of testing/ checking the entire ...
... considered successful if all the files in a group are successfully transferred, in the event of failure in transfer of any one of the files from a group the whole transfer will be “rolled back” and will be considered as unsuccessful. SOSFTP’s test mode provides ease of testing/ checking the entire ...
the Nilfs version 1: overview
... past, the advantages of LFS were high write performance and faster recovery time. In addition, LFS prevents data write operations from overwriting the disk blocks, thereby minimizing damage to the file data and file system consistency and avoiding a hardware failure. Furthermore, LFS writes data and ...
... past, the advantages of LFS were high write performance and faster recovery time. In addition, LFS prevents data write operations from overwriting the disk blocks, thereby minimizing damage to the file data and file system consistency and avoiding a hardware failure. Furthermore, LFS writes data and ...
A Concept for an Electronic Magazine
... usually defined by the tools available on his local system and often differ from the standards used for publication. The format conversion is made by the management system of the EZine, without bothering the user with it. Ideally, the user should be able to deliver data of any kind of audio and vide ...
... usually defined by the tools available on his local system and often differ from the standards used for publication. The format conversion is made by the management system of the EZine, without bothering the user with it. Ideally, the user should be able to deliver data of any kind of audio and vide ...
FREE Sample Here - We can offer most test bank and
... Chapter 1. Chapter 1 assumes student familiarity with Microsoft Access 2013, and the chapter figures contain screenshots from a database in Microsoft Access. In addition, the Chapter 1 Project Questions require student use of Microsoft Access 2013. ...
... Chapter 1. Chapter 1 assumes student familiarity with Microsoft Access 2013, and the chapter figures contain screenshots from a database in Microsoft Access. In addition, the Chapter 1 Project Questions require student use of Microsoft Access 2013. ...
FREE Sample Here
... Chapter 1. Chapter 1 assumes student familiarity with Microsoft Access 2013, and the chapter figures contain screenshots from a database in Microsoft Access. In addition, the Chapter 1 Project Questions require student use of Microsoft Access 2013. ...
... Chapter 1. Chapter 1 assumes student familiarity with Microsoft Access 2013, and the chapter figures contain screenshots from a database in Microsoft Access. In addition, the Chapter 1 Project Questions require student use of Microsoft Access 2013. ...
Lecture 13
... • What if multiple processes have a given file open? • Should they share one control structure or have one each? • In-memory structures typically contain a cursor pointer – Indicating how far into the file data has been read/written ...
... • What if multiple processes have a given file open? • Should they share one control structure or have one each? • In-memory structures typically contain a cursor pointer – Indicating how far into the file data has been read/written ...
Elixir Repertoire Runtime
... Intialize the ReportEngineFactory by calling init. The interface IReportHost allows you to implement your own class to log messages from the runtime. The BasicReportHost is the default implementation provided. The code example is shown below. ReportEngineFactory.init(new BasicReportHost()); ...
... Intialize the ReportEngineFactory by calling init. The interface IReportHost allows you to implement your own class to log messages from the runtime. The BasicReportHost is the default implementation provided. The code example is shown below. ReportEngineFactory.init(new BasicReportHost()); ...
Operating Systems - Lecture #5: File Management
... there are restrictions on filename with each operating system: MS-DOS - allows names from one to eight alphanumeric ...
... there are restrictions on filename with each operating system: MS-DOS - allows names from one to eight alphanumeric ...
Chapter 21 PowerPoint
... – There is a limited number of signals, and they cannot carry information: only the fact that a signal occurred is available to a process. – The Linux kernel does not use signals to communicate with processes with are running in kernel mode, rather, communication within the kernel is accomplished vi ...
... – There is a limited number of signals, and they cannot carry information: only the fact that a signal occurred is available to a process. – The Linux kernel does not use signals to communicate with processes with are running in kernel mode, rather, communication within the kernel is accomplished vi ...
p1 p2 p3 pn
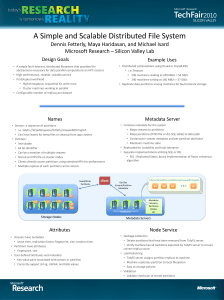
... • 240 machines reading at 240 MB/s = 56 GB/s • 240 machines writing at 160 MB/s = 37 GB/s • Replicate data partitions among machines for fault tolerant storage ...
... • 240 machines reading at 240 MB/s = 56 GB/s • 240 machines writing at 160 MB/s = 37 GB/s • Replicate data partitions among machines for fault tolerant storage ...
Chapter 11 File System Implementation
... • Following a mount request that conforms to its export list, the server returns a file handle —a key for further accesses • File handle –a file-system identifier, and an inode number to identify the mounted directory within the exported file system • The mount operation changes only the user’ s vie ...
... • Following a mount request that conforms to its export list, the server returns a file handle —a key for further accesses • File handle –a file-system identifier, and an inode number to identify the mounted directory within the exported file system • The mount operation changes only the user’ s vie ...
File System - UC Davis Computer Science
... open directory “two”, search for “three”, get loc. of “three” open file “three” (of course, permissions are checked at each step) ...
... open directory “two”, search for “three”, get loc. of “three” open file “three” (of course, permissions are checked at each step) ...
Storing Data: Disks and Files
... • The size in bytes of the memory buffer InnoDB uses to cache data and indexes of its tables. The default value is 128MB (v 5.1-5.6, and in use on topcat). • On a dedicated database server, you may set this to up to 80% of the machine physical memory size. • But of course not larger than the DB data ...
... • The size in bytes of the memory buffer InnoDB uses to cache data and indexes of its tables. The default value is 128MB (v 5.1-5.6, and in use on topcat). • On a dedicated database server, you may set this to up to 80% of the machine physical memory size. • But of course not larger than the DB data ...
Project Description Userspace Deduplication File System using FUSE
... The goal of this project is to build a functioning deduplication file system. We will build our system using the FUSE [2] file system framework within the Linux operating system environment. You will NOT be using xv6 for this project. This will enable us to use it just like any other file system, bu ...
... The goal of this project is to build a functioning deduplication file system. We will build our system using the FUSE [2] file system framework within the Linux operating system environment. You will NOT be using xv6 for this project. This will enable us to use it just like any other file system, bu ...
Query Processing - Department of Computer Science
... Locks The most common way in which access to items is controlled is by “locks.” Lock manager is the part of a DBMS that records, for each item I, whether one or more transactions are reading or writing any part of I. If so, the manager will forbid another transaction from gaining access to I, provi ...
... Locks The most common way in which access to items is controlled is by “locks.” Lock manager is the part of a DBMS that records, for each item I, whether one or more transactions are reading or writing any part of I. If so, the manager will forbid another transaction from gaining access to I, provi ...
Data Management in Geodise
... Our focus is on leveraging existing database tools not commonly used in engineering … …and making them accessible to users of the system. © Geodise Project, University of Southampton, 2003. http://www.geodise.org/ ...
... Our focus is on leveraging existing database tools not commonly used in engineering … …and making them accessible to users of the system. © Geodise Project, University of Southampton, 2003. http://www.geodise.org/ ...
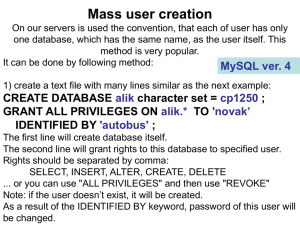
GRANT ALL PRIVILEGES ON alik.* TO `novak`
... This is important to prepare this file in such directory, that the name including path can be easy written (the desktop address is very complicated to be written). Note: in the Windows XP command line prompt, you cannot use the Ctrl+C and Ctrl+V commands. Using Linux and the “putty” program, you can ...
... This is important to prepare this file in such directory, that the name including path can be easy written (the desktop address is very complicated to be written). Note: in the Windows XP command line prompt, you cannot use the Ctrl+C and Ctrl+V commands. Using Linux and the “putty” program, you can ...
TrusTed plaTform module (Tpm) Toshiba securiTy
... The Emergency Recovery Archive File stores all user security keys. This file should be backed up periodically to an external storage device in case the HDD ever becomes inaccessible. The Emergency Recovery Token is a key that is required to access the Emergency Recovery Archive file. This token file ...
... The Emergency Recovery Archive File stores all user security keys. This file should be backed up periodically to an external storage device in case the HDD ever becomes inaccessible. The Emergency Recovery Token is a key that is required to access the Emergency Recovery Archive file. This token file ...
ch14protection
... When file is executed and setuid = on, then user-id is set to owner of the file being executed. When execution completes user-id is reset. Example: set password Must change an entry in “passwd” file Could perform through system call Very limiting, must alter the kernel What if a user wan ...
... When file is executed and setuid = on, then user-id is set to owner of the file being executed. When execution completes user-id is reset. Example: set password Must change an entry in “passwd” file Could perform through system call Very limiting, must alter the kernel What if a user wan ...
Presentation - lsp4you.com
... Information from the file is accessed in order, one record after the other. Compilers, multimedia applications, sound files, etc. are the most common examples of programs using sequential access. In case of a read operation, the record at the location pointed by the file pointer is read and the file ...
... Information from the file is accessed in order, one record after the other. Compilers, multimedia applications, sound files, etc. are the most common examples of programs using sequential access. In case of a read operation, the record at the location pointed by the file pointer is read and the file ...
Return Codes and Associated Messages
... The S1000 (SAS API Error) return code is often accompanied by error messages that are returned by your communications software. The following tables list some of these message texts and provide explanations for them. In addition to these error messages and return codes, some additional information c ...
... The S1000 (SAS API Error) return code is often accompanied by error messages that are returned by your communications software. The following tables list some of these message texts and provide explanations for them. In addition to these error messages and return codes, some additional information c ...