Document
... For example: home directories would have read/write access for all known users, allowing each to access their own files Would still not have access to the files of others unless that permission would normally exist ...
... For example: home directories would have read/write access for all known users, allowing each to access their own files Would still not have access to the files of others unless that permission would normally exist ...
Android - part IV
... • Are the standard interface that connects data in one process with code running in another process • Applications usually must request specific permissions in their manifest files to access providers • There is no need for a provider if you don't intend to share your data with other applications • ...
... • Are the standard interface that connects data in one process with code running in another process • Applications usually must request specific permissions in their manifest files to access providers • There is no need for a provider if you don't intend to share your data with other applications • ...
Embedding Object Files in an Existing Operating System: A Practical Approach
... OPERATING SYSTEMS In this section, we will explain the typical problems that occur in existing data storage systems and the proposed technique used in order to design our system. 4.1 Typical Problems In general, file system is designed for a specific operating system [5]. File system always consider ...
... OPERATING SYSTEMS In this section, we will explain the typical problems that occur in existing data storage systems and the proposed technique used in order to design our system. 4.1 Typical Problems In general, file system is designed for a specific operating system [5]. File system always consider ...
Read Dirty to Me: SQL Server Isolation Levels
... Repeatable Read ◦ Pessimistic ◦ Rows locked as they are read ◦ Rows remain locked until transaction ...
... Repeatable Read ◦ Pessimistic ◦ Rows locked as they are read ◦ Rows remain locked until transaction ...
Files and File Systems • files: persistent, named data objects – data
... – time of last file access – time of last i-node update, last file update – number of hard links to this file – 12 direct data block pointers – one single, one double, one triple indirect data block pointer ...
... – time of last file access – time of last i-node update, last file update – number of hard links to this file – 12 direct data block pointers – one single, one double, one triple indirect data block pointer ...
Slide 1
... To designate a file’s location, you must first specify the device where the file is stored – The main hard disk usually is referred to as Drive C A disk partition is a section of hard disk drive that is treated as a separate storage unit – Partitions can be assigned drive letters – Partitions ar ...
... To designate a file’s location, you must first specify the device where the file is stored – The main hard disk usually is referred to as Drive C A disk partition is a section of hard disk drive that is treated as a separate storage unit – Partitions can be assigned drive letters – Partitions ar ...
AIX is building momentum as the leading, UNIX operating system for
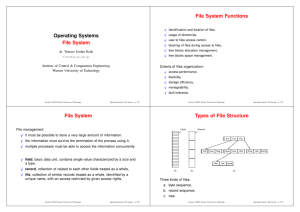
... A file system is a hierarchical structure (file tree) of files and directories. This type of structure resembles an inverted tree with the roots at the top and branches at the bottom. This file tree uses directories to organize data and programs into groups, allowing the management of several direct ...
... A file system is a hierarchical structure (file tree) of files and directories. This type of structure resembles an inverted tree with the roots at the top and branches at the bottom. This file tree uses directories to organize data and programs into groups, allowing the management of several direct ...
Chapter 9: File-System Interface
... Recovery from failure can involve state information about status of each remote request ...
... Recovery from failure can involve state information about status of each remote request ...
Using SAS/ACCESS-OLE DB for Pharmacoeconomic Analysis
... Pharmacoeconomic analyses, such as cost-effectiveness, trend analysis, retrospective database analysis, may occur on an ad hoc or an ongoing basis involving several data sources in disparate file formats. At a Pharmacy Benefit Management company, pharmacy claims number in the millions and are often ...
... Pharmacoeconomic analyses, such as cost-effectiveness, trend analysis, retrospective database analysis, may occur on an ad hoc or an ongoing basis involving several data sources in disparate file formats. At a Pharmacy Benefit Management company, pharmacy claims number in the millions and are often ...
OODB
... Restoration after disk or system failure: Full backup. Using log files. Transaction logs. ...
... Restoration after disk or system failure: Full backup. Using log files. Transaction logs. ...
System software - Barbados SDA Secondary
... it is working properly. It does this by following certain instructions held on a ROM chip known as the BIOS. ...
... it is working properly. It does this by following certain instructions held on a ROM chip known as the BIOS. ...
Experiences with Content Addressable Storage and Virtual Disks Anthony Liguori
... In order to get a better idea of the performance and efficiency implications of using a CAS based image management system, we constructed a prototype by combining the Venti [10] CAS back end with a service-oriented file system to provide an organizational infrastructure and tested it with guest logi ...
... In order to get a better idea of the performance and efficiency implications of using a CAS based image management system, we constructed a prototype by combining the Venti [10] CAS back end with a service-oriented file system to provide an organizational infrastructure and tested it with guest logi ...
dmxcourse
... Script-driven comms for Async & TCP/IP Normally used with standard scripts Can be used for most Internet protocols Can be used to create a server For secure comms use with Stunnel ...
... Script-driven comms for Async & TCP/IP Normally used with standard scripts Can be used for most Internet protocols Can be used to create a server For secure comms use with Stunnel ...
Slides
... network failure, server failure Recovery from failure can involve state information about ...
... network failure, server failure Recovery from failure can involve state information about ...
Application of Bioinformatics
... or IE with “C:\” in the address window. • Change the “ToolsFolder Options” so that the file extensions (.xxx) are revealed. • Edit the downloaded sequence file in MS Word, highlight a section of the sequence with Bold font or color and save as .doc • Open the .doc file in NotePad – observe the inse ...
... or IE with “C:\” in the address window. • Change the “ToolsFolder Options” so that the file extensions (.xxx) are revealed. • Edit the downloaded sequence file in MS Word, highlight a section of the sequence with Bold font or color and save as .doc • Open the .doc file in NotePad – observe the inse ...
... Seek 200 Kbytes and repeat the pattern. This again is a typical application behavior for applications that have data structures contained within a file and is accessing a particular region of the data structure. Most operating systems do not detect this behavior or implement any techniques to enhan ...
Distributed File Systems
... NFS and ONC figured prominently in the network-computing war between Sun Microsystems and Apollo Computer, and later the UNIX wars (ca 1987-1996) between AT&T and Sun on one side, and Digital Equipment, HP, and IBM on the other. During the development of the ONC protocol (called SunRPC at the time), ...
... NFS and ONC figured prominently in the network-computing war between Sun Microsystems and Apollo Computer, and later the UNIX wars (ca 1987-1996) between AT&T and Sun on one side, and Digital Equipment, HP, and IBM on the other. During the development of the ONC protocol (called SunRPC at the time), ...
Document
... • ACID transactions are: – Atomic : Whole transaction or none is done. – Consistent : Database constraints preserved. – Isolated : It appears to the user as if only one process executes at a time. • That is, even though actions of several transactions might be interleaved, the net effect is identica ...
... • ACID transactions are: – Atomic : Whole transaction or none is done. – Consistent : Database constraints preserved. – Isolated : It appears to the user as if only one process executes at a time. • That is, even though actions of several transactions might be interleaved, the net effect is identica ...
Lecture 12
... – Requires extra mechanism to allow revocation – In network environment, need cryptographic methods to prevent forgery CS 111 Summer 2014 ...
... – Requires extra mechanism to allow revocation – In network environment, need cryptographic methods to prevent forgery CS 111 Summer 2014 ...