Chapter 18 Binary I/O
... BufferedInputStream/BufferedOutputStream does not contain new methods. All the methods BufferedInputStream/BufferedOutputStream are inherited from the InputStream/OutputStream classes. Liang, Introduction to Java Programming, Sixth Edition, (c) 2005 Pearson Education, Inc. All rights reserved. 0-13- ...
... BufferedInputStream/BufferedOutputStream does not contain new methods. All the methods BufferedInputStream/BufferedOutputStream are inherited from the InputStream/OutputStream classes. Liang, Introduction to Java Programming, Sixth Edition, (c) 2005 Pearson Education, Inc. All rights reserved. 0-13- ...
Quick UNIX Tutorial
... the user’s username and password, creates a shell process. • The shell process displays a prompt on the screen and waits. • When the user enters a command, the shell examines it, interprets it and either executes it or calls another program to do so. • After the command is executed, the shell displa ...
... the user’s username and password, creates a shell process. • The shell process displays a prompt on the screen and waits. • When the user enters a command, the shell examines it, interprets it and either executes it or calls another program to do so. • After the command is executed, the shell displa ...
Brocade 2007 - More than Fibre Channel SANs
... the iSNAP 2110 Processor on which it is based. The HBA offloads network processing from a server without modifying applications. Under heavy loads, this increases throughput by three to four times. This solution is for network-intensive applications, such as media streaming and voice over IP. File A ...
... the iSNAP 2110 Processor on which it is based. The HBA offloads network processing from a server without modifying applications. Under heavy loads, this increases throughput by three to four times. This solution is for network-intensive applications, such as media streaming and voice over IP. File A ...
A Handy New SAS® Tool for Comparing Dynamic Datasets
... small datasets with few variables but is nearly impossible for large datasets with thousands of records and many variables. This paper presents a new tool that provides an efficient way to detect differences in two dynamic data sets captured at different points in time. ...
... small datasets with few variables but is nearly impossible for large datasets with thousands of records and many variables. This paper presents a new tool that provides an efficient way to detect differences in two dynamic data sets captured at different points in time. ...
0 - For link to GMS6014, click here
... “formatdb –i dbs\Dm.P –p T” -- format the dataset for the program. 4. Compose the query sequence save as “3TNF.txt” in the “blast\query\” folder. 5. Initiated the search by typing “blastall –p blastp –d dbs\Dm.P –i query\4_MMD2.fasta –o out\Mdm2_DmP.html –T T” ...
... “formatdb –i dbs\Dm.P –p T” -- format the dataset for the program. 4. Compose the query sequence save as “3TNF.txt” in the “blast\query\” folder. 5. Initiated the search by typing “blastall –p blastp –d dbs\Dm.P –i query\4_MMD2.fasta –o out\Mdm2_DmP.html –T T” ...
the Nilfs version 1: overview
... is written to the page cache, and the page cache is written to the disk later. The indirect blocks of the file also use page cache, because they need to determine whether the block exists on page cache or not, for all file read and write operations. This must be done efficiently to maintain read/wri ...
... is written to the page cache, and the page cache is written to the disk later. The indirect blocks of the file also use page cache, because they need to determine whether the block exists on page cache or not, for all file read and write operations. This must be done efficiently to maintain read/wri ...
File Systems_PPT_ch04
... • Initially implemented in MS-DOS and supported by all versions of Windows and most other OSs. ...
... • Initially implemented in MS-DOS and supported by all versions of Windows and most other OSs. ...
Elixir Repertoire Runtime
... process, the amount of report that can renders concurrently is dependent on the system resources. The report rendering threads and number in queue is in turned controlled by the licensing. It will not exceed this amount. The default runtime license sets the number of threads to one. Please contact E ...
... process, the amount of report that can renders concurrently is dependent on the system resources. The report rendering threads and number in queue is in turned controlled by the licensing. It will not exceed this amount. The default runtime license sets the number of threads to one. Please contact E ...
Standard Operating and Maintenance Procedures
... • Example: If Microsoft Word 2007 and 2010 are being used, create Word2007 and Word2010 subdirectories under the Program Files directory Guide to Operating Systems, 4th ed. ...
... • Example: If Microsoft Word 2007 and 2010 are being used, create Word2007 and Word2010 subdirectories under the Program Files directory Guide to Operating Systems, 4th ed. ...
Brief Introduction of Bioinformatics
... A relative path name is one that doesn't start with /; in that case, the directory tree is traversed starting from a given point, which changes depending on context, called the current directory. In every directory, there are two special directories called . and .., which refer respectively to the d ...
... A relative path name is one that doesn't start with /; in that case, the directory tree is traversed starting from a given point, which changes depending on context, called the current directory. In every directory, there are two special directories called . and .., which refer respectively to the d ...
Document
... The UNIX filesystem is heirarchical (resembling a tree structure). The tree is anchored at a place called the root, designated by a slash "/". Every item in the UNIX filesystem tree is either a file, or a directory. A directory is like a file folder. A directory can contain files, and other director ...
... The UNIX filesystem is heirarchical (resembling a tree structure). The tree is anchored at a place called the root, designated by a slash "/". Every item in the UNIX filesystem tree is either a file, or a directory. A directory is like a file folder. A directory can contain files, and other director ...
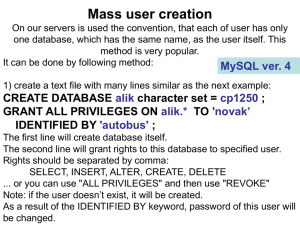
GRANT ALL PRIVILEGES ON alik.* TO `novak`
... mysql> source c:\any_name.txt This is important to prepare this file in such directory, that the name including path can be easy written (the desktop address is very complicated to be written). Note: in the Windows XP command line prompt, you cannot use the Ctrl+C and Ctrl+V commands. Using Linux an ...
... mysql> source c:\any_name.txt This is important to prepare this file in such directory, that the name including path can be easy written (the desktop address is very complicated to be written). Note: in the Windows XP command line prompt, you cannot use the Ctrl+C and Ctrl+V commands. Using Linux an ...
Raw Format - Sam Bowne
... I am finding contradictory claims about this—wait until we have a real example for clarity Compressing Disk Images Lossless compression might compress a disk image by 50% or more But files that are already compressed, like ZIP files, won’t compress much more Error in textbook: JPEGs use lossy co ...
... I am finding contradictory claims about this—wait until we have a real example for clarity Compressing Disk Images Lossless compression might compress a disk image by 50% or more But files that are already compressed, like ZIP files, won’t compress much more Error in textbook: JPEGs use lossy co ...
Defeating Encrypted and Deniable File Systems
... rations, a typical configuration might be as follows: Alice creates a regular (non-deniable) encrypted file system on her laptop, protected by some password she knows. Inside that encrypted file system, she has the option to also create a deniable file system, protected by a second password. TrueCry ...
... rations, a typical configuration might be as follows: Alice creates a regular (non-deniable) encrypted file system on her laptop, protected by some password she knows. Inside that encrypted file system, she has the option to also create a deniable file system, protected by a second password. TrueCry ...
WinFS
... Changes made by WinFS Apps are reflected in the file system WinFS App does not need to know whether this is a file-backed Item Serialization format for non-WinFS Stores ...
... Changes made by WinFS Apps are reflected in the file system WinFS App does not need to know whether this is a file-backed Item Serialization format for non-WinFS Stores ...
Defeating Encrypted and Deniable File Systems
... rations, a typical configuration might be as follows: Alice creates a regular (non-deniable) encrypted file system on her laptop, protected by some password she knows. Inside that encrypted file system, she has the option to also create a deniable file system, protected by a second password. TrueCry ...
... rations, a typical configuration might be as follows: Alice creates a regular (non-deniable) encrypted file system on her laptop, protected by some password she knows. Inside that encrypted file system, she has the option to also create a deniable file system, protected by a second password. TrueCry ...
sosftp - SOS
... A jump host is located in the DMZ, therefore it can access servers at customer sites via the internet. Local servers quite often are excluded from internet access for security concerns. Jump hosts are used in order to store files temporarily and to forward them to the final destination which is ...
... A jump host is located in the DMZ, therefore it can access servers at customer sites via the internet. Local servers quite often are excluded from internet access for security concerns. Jump hosts are used in order to store files temporarily and to forward them to the final destination which is ...
Lecture 13
... • There is an on-disk structure pointing to disk blocks (and holding other information) • When file is opened, an in-memory structure is created • Not an exact copy of the disk version – The disk version points to disk blocks – The in-memory version points to RAM pages • Or indicates that the block ...
... • There is an on-disk structure pointing to disk blocks (and holding other information) • When file is opened, an in-memory structure is created • Not an exact copy of the disk version – The disk version points to disk blocks – The in-memory version points to RAM pages • Or indicates that the block ...
Chapter 11 File System Implementation
... FAT FAT32, NTFS… –Duplication of code is minimized for different file ...
... FAT FAT32, NTFS… –Duplication of code is minimized for different file ...
File System - UC Davis Computer Science
... Directory internals • A directory is typically just a file that happens to contain special metadata directory = list of (name of file, file attributes) attributes include such things as: o size, protection, location on disk, creation time, access time, … ...
... Directory internals • A directory is typically just a file that happens to contain special metadata directory = list of (name of file, file attributes) attributes include such things as: o size, protection, location on disk, creation time, access time, … ...
File System - WordPress.com
... Stands for automatically executed batch file, the file that DOS automatically executes when a computer boots up. This is a convenient place to put commands you always want to execute at the beginning of a computing session. For example, you can set system parameters such as the date and time, and in ...
... Stands for automatically executed batch file, the file that DOS automatically executes when a computer boots up. This is a convenient place to put commands you always want to execute at the beginning of a computing session. For example, you can set system parameters such as the date and time, and in ...
Computer file

A computer file is a resource for storing information, which is available to a computer program and is usually based on some kind of durable storage. A file is ""durable"" in the sense that it remains available for other programs to use after the program that created it has finished executing. Computer files can be considered as the modern counterpart of paper documents which traditionally are kept in office and library files, and this is the source of the term.