Ch-11_3431
... Modems split their EPROM in half and duplicate things so there are two copies If one is corrupted, the other is used Can use similar approaches with disks, but is very wasteful of space Can also do limited duplication and avoid overwriting data until the disk is full Complete duplication t ...
... Modems split their EPROM in half and duplicate things so there are two copies If one is corrupted, the other is used Can use similar approaches with disks, but is very wasteful of space Can also do limited duplication and avoid overwriting data until the disk is full Complete duplication t ...
Data Structures in C
... • In addition to these modes a file may be opened either as a binary or text file. • Text files may only contain ASCII data. • Binary files contain images of the data. • Files are opened as text by adding a “t” to the open mode. • Files are opened as binary by adding a “b” to the open mode. ...
... • In addition to these modes a file may be opened either as a binary or text file. • Text files may only contain ASCII data. • Binary files contain images of the data. • Files are opened as text by adding a “t” to the open mode. • Files are opened as binary by adding a “b” to the open mode. ...
Red Hat Linux System Administration I – Concepts
... Searching for RE Patterns in Files using ‘grep’ RE characters for Wildcards RE characters for Modifiers RE characters for Anchors Combining Multiple Regular Expressions In One Request Modifying Streams of Data Using ‘sed’ Searching Multiple Files For The Same RE You Need More? Use Extended Regular E ...
... Searching for RE Patterns in Files using ‘grep’ RE characters for Wildcards RE characters for Modifiers RE characters for Anchors Combining Multiple Regular Expressions In One Request Modifying Streams of Data Using ‘sed’ Searching Multiple Files For The Same RE You Need More? Use Extended Regular E ...
SimpleDB Overview - Massachusetts Institute of Technology
... • Because you haven’t implemented insertTuple, you have no way to create data files ...
... • Because you haven’t implemented insertTuple, you have no way to create data files ...
(DOCX, Unknown)
... FAT – only supports up to 4GB files and its volume tops out at 2TB in size. NTFS – supports up to 16EB (exabytes really bloody big) meaning that uncompressed videos and data can be stored. Back to FAT stuff Files are stored in one or more clusters, these clusters are unlikely to be next to each othe ...
... FAT – only supports up to 4GB files and its volume tops out at 2TB in size. NTFS – supports up to 16EB (exabytes really bloody big) meaning that uncompressed videos and data can be stored. Back to FAT stuff Files are stored in one or more clusters, these clusters are unlikely to be next to each othe ...
Mohammad Husain
... Linux requires 386 architecture to run. Thus, it is compatible with any improved architecture such as 486, Pentium, Pentium Pro, etc There are drivers available for much many types of hardware devices Linux program installation seems to be easier since it only requires a restart when hardware device ...
... Linux requires 386 architecture to run. Thus, it is compatible with any improved architecture such as 486, Pentium, Pentium Pro, etc There are drivers available for much many types of hardware devices Linux program installation seems to be easier since it only requires a restart when hardware device ...
eFS: encrypted File system
... Ensure that private data is not accessed by other users ( may not be malicious). ...
... Ensure that private data is not accessed by other users ( may not be malicious). ...
Operating Systems and File Management Learning Steps LAP CC
... d) An operating system’s 4.___________________________ capability supports a division of labor among all the processing units. e) An operating system might have to deal with a memory, 5.___________________________, a situation caused by an application that requests memory, but never releases it. f) ...
... d) An operating system’s 4.___________________________ capability supports a division of labor among all the processing units. e) An operating system might have to deal with a memory, 5.___________________________, a situation caused by an application that requests memory, but never releases it. f) ...
Mid-term Presentation
... Important to know how our data is being stored. Need to know how your data can be stored efficiently in the cloud i.e. choosing the right kind of storage. ...
... Important to know how our data is being stored. Need to know how your data can be stored efficiently in the cloud i.e. choosing the right kind of storage. ...
Disk Partitioning - Seton Hall University
... predict how much space each partition will need, which may be a difficult task • Logical Volume Management, often used in servers, increases flexibility by allowing data in volumes to expand into separate physical disks • Another option is to resize existing partitions when necessary. ...
... predict how much space each partition will need, which may be a difficult task • Logical Volume Management, often used in servers, increases flexibility by allowing data in volumes to expand into separate physical disks • Another option is to resize existing partitions when necessary. ...
Desktop PC Operating Systems
... A file containing commands to automatically configure a personal computer on start up. ...
... A file containing commands to automatically configure a personal computer on start up. ...
Lab 1 – Using the File System through Windows Explorer
... Copy these two picture files to the folder All Files in the Sun Systems folder. Rename the two picture files to Picture1 and Picture2. Move the two picture files to the folder Sun Systems. Name file attributes that you have used here: ………………………………………… ...
... Copy these two picture files to the folder All Files in the Sun Systems folder. Rename the two picture files to Picture1 and Picture2. Move the two picture files to the folder Sun Systems. Name file attributes that you have used here: ………………………………………… ...
Wannacry Ransomware Alert
... Wannacry encrypts the files on infected Windows systems. This ransomware spreads by using a vulnerability in implementations of Server Message Block (SMB) in Windows systems. This exploit is named as ETERNALBLUE. The ransomware called WannaCrypt or WannaCry encrypts the computer's hard disk drive an ...
... Wannacry encrypts the files on infected Windows systems. This ransomware spreads by using a vulnerability in implementations of Server Message Block (SMB) in Windows systems. This exploit is named as ETERNALBLUE. The ransomware called WannaCrypt or WannaCry encrypts the computer's hard disk drive an ...
Operating Systems
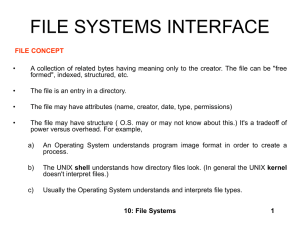
... kept in human-readable form Type: This is needed for the OS in order to decode/process data in the file ...
... kept in human-readable form Type: This is needed for the OS in order to decode/process data in the file ...
Introduction to Linux/Unix
... The prompt is called a shell prompt and waits for user commands User commands consists of three basic parts (in order): command name eg. ls options (modifiers) eg. -la (l= long form, a = all file types) arguments the entity to be acted upon ...
... The prompt is called a shell prompt and waits for user commands User commands consists of three basic parts (in order): command name eg. ls options (modifiers) eg. -la (l= long form, a = all file types) arguments the entity to be acted upon ...
D00_Files
... current Unix-like operating systems (OS) are POSIX compliant (or nearly so): Linux, BSD, Solaris, AIX, IRIX While an understanding of each operating system’s design is necessary to fully utilize its API, most functions work almost identically on any compliant operating system We will develop for ...
... current Unix-like operating systems (OS) are POSIX compliant (or nearly so): Linux, BSD, Solaris, AIX, IRIX While an understanding of each operating system’s design is necessary to fully utilize its API, most functions work almost identically on any compliant operating system We will develop for ...
ECE 175: Computer Programming for Engineering Applications
... Algorithm: Let n be the number tested for primality. If n is not divisible by any number m smaller than d ne then n is a prime. Else n is not a prime. Example: 13 is a prime because no number less than 4 divides it. The rationale behind this simple algorithm is the fact if a number n can be factored ...
... Algorithm: Let n be the number tested for primality. If n is not divisible by any number m smaller than d ne then n is a prime. Else n is not a prime. Example: 13 is a prime because no number less than 4 divides it. The rationale behind this simple algorithm is the fact if a number n can be factored ...
Physical Design
... attributes from one entity into another requires a join that accesses the link file and the associated entity. It may be worth violating 2NF or 3NF rules to duplicate commonly needed attribute values in the link file or even in the "parent" entity. ...
... attributes from one entity into another requires a join that accesses the link file and the associated entity. It may be worth violating 2NF or 3NF rules to duplicate commonly needed attribute values in the link file or even in the "parent" entity. ...
Document
... directory structure for windows operating system by comparing FAT16/FAT32 and NTFS file systems. benefits of each? Why would one file system used over the other? Part3: Write a one-page summary examining the various file systems available to Linux including the directory structure and compare them t ...
... directory structure for windows operating system by comparing FAT16/FAT32 and NTFS file systems. benefits of each? Why would one file system used over the other? Part3: Write a one-page summary examining the various file systems available to Linux including the directory structure and compare them t ...
Computer Forensics Glossary - Information Security and Forensics
... contained on the original physical item. Files are groups of information collectively placed under a name and stored on the computer. Files are organized in various directories and subdirectories. File Allocation Table (FAT). Where the operating system stores information about a disk's structure. Th ...
... contained on the original physical item. Files are groups of information collectively placed under a name and stored on the computer. Files are organized in various directories and subdirectories. File Allocation Table (FAT). Where the operating system stores information about a disk's structure. Th ...
File System Caching Journaling File Systems
... Interoperability with Windows and Mac requires support of different file systems (eg vfat) ⇒ Linux implements common interface for all filesystems Common interface called virtual file system virtual file system maintains inodes for files and directories caches, in particular for directories superblo ...
... Interoperability with Windows and Mac requires support of different file systems (eg vfat) ⇒ Linux implements common interface for all filesystems Common interface called virtual file system virtual file system maintains inodes for files and directories caches, in particular for directories superblo ...
Worksheet 1 - Python intro File
... YouTube and Facebook. A general understanding of its principles is a great start to becoming a web & app developer. Write in this box your definition of a computer program ...
... YouTube and Facebook. A general understanding of its principles is a great start to becoming a web & app developer. Write in this box your definition of a computer program ...
File - CSUS
... Computers Manage Data To understand Window’s use of files and folders, you need to know just a small bit about how a computer stores information. Computers store data which are pieces of information. A computer’s file system is its method of organizing the data stored on its Secondary or Mass storag ...
... Computers Manage Data To understand Window’s use of files and folders, you need to know just a small bit about how a computer stores information. Computers store data which are pieces of information. A computer’s file system is its method of organizing the data stored on its Secondary or Mass storag ...
Computer file

A computer file is a resource for storing information, which is available to a computer program and is usually based on some kind of durable storage. A file is ""durable"" in the sense that it remains available for other programs to use after the program that created it has finished executing. Computer files can be considered as the modern counterpart of paper documents which traditionally are kept in office and library files, and this is the source of the term.