Network
... Internet Internet Control Message Address Network Protocol (ICMP) Resolution (IP) (ARP) Ethernet, Token Ring, etc. Data Link Twisted Pair, Fiber, Coax, Wireless Physical ...
... Internet Internet Control Message Address Network Protocol (ICMP) Resolution (IP) (ARP) Ethernet, Token Ring, etc. Data Link Twisted Pair, Fiber, Coax, Wireless Physical ...
Final_Presentation1-2
... Received frames are queued in a double buffer Frames must be de-queued in order to be removed from the buffer Incoming frames are dropped if buffer is full ...
... Received frames are queued in a double buffer Frames must be de-queued in order to be removed from the buffer Incoming frames are dropped if buffer is full ...
ppt
... Represented by something over some medium by something Started with terminals connect to computers Communicated by voltages (currents) on wires (teletype) ...
... Represented by something over some medium by something Started with terminals connect to computers Communicated by voltages (currents) on wires (teletype) ...
What is a Network?
... different types of network protocols and standards are required to ensure that your computer (no matter which operating system, network card, or application you are using) can communicate with another computer located on the next desk or halfway around the world. ...
... different types of network protocols and standards are required to ensure that your computer (no matter which operating system, network card, or application you are using) can communicate with another computer located on the next desk or halfway around the world. ...
KIS – Cvičenie #1
... • Divides network into broadcast domains: – A broadcast domain is a logical area in a computer network where any computer connected to the computer network can directly transmit to any other in the domain without having to go through a routing device ...
... • Divides network into broadcast domains: – A broadcast domain is a logical area in a computer network where any computer connected to the computer network can directly transmit to any other in the domain without having to go through a routing device ...
Chapter 15 Local Area Networks
... all devices attached to network connected by layer 2 switches and/or bridges — In large network, broadcast frames can create big overhead — Malfunctioning device can create broadcast storm • Numerous broadcast frames clog network ...
... all devices attached to network connected by layer 2 switches and/or bridges — In large network, broadcast frames can create big overhead — Malfunctioning device can create broadcast storm • Numerous broadcast frames clog network ...
Data Link Layer
... In fact, collisions are a very normal part of Ethernet operation. It’s only when collisions begin to occur frequently that you need to become concerned. ...
... In fact, collisions are a very normal part of Ethernet operation. It’s only when collisions begin to occur frequently that you need to become concerned. ...
Quick-Start Guide
... 3. When prompted for a username and password, type admin for the password only (username is not required). 4. Click Login and enter the username and password provided by your service provider. 5. Click Save. 6. If additional configuration is desired, select Setup to configure DHCP, firewall settings ...
... 3. When prompted for a username and password, type admin for the password only (username is not required). 4. Click Login and enter the username and password provided by your service provider. 5. Click Save. 6. If additional configuration is desired, select Setup to configure DHCP, firewall settings ...
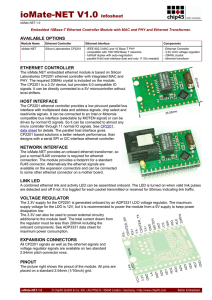
ioMate-NET V1.0 Infosheet
... CHIP45 embedded microcontroller modules (henceforce products) are designed for installation in electrical appliances or as dedicated evaluation boards (i.e.: for use as a test and prototype platform for hardware/software development) in laboratory environments. Caution: CHIP45 products lacking prote ...
... CHIP45 embedded microcontroller modules (henceforce products) are designed for installation in electrical appliances or as dedicated evaluation boards (i.e.: for use as a test and prototype platform for hardware/software development) in laboratory environments. Caution: CHIP45 products lacking prote ...
BEC 8920NE - BEC Technologies
... Check the Ethernet LEDs on the front panel. The LED should be on for a port that has a PC connected. If it is off, check the cables between your router and the PC. Make sure you have uninstalled any software firewall for troubleshooting. Verify that the IP address and the subnet mask are consistent ...
... Check the Ethernet LEDs on the front panel. The LED should be on for a port that has a PC connected. If it is off, check the cables between your router and the PC. Make sure you have uninstalled any software firewall for troubleshooting. Verify that the IP address and the subnet mask are consistent ...
MegaPlug 4P Hub dtsht3.qxd
... End the Ethernet Port Drought Ethernet ports are valuable. They are often the only way to connect computers, printers, and other devices (scanners or networkable hard drives), share Internet connections, or quickly transfer large amounts of data. Unfortunately, many of the components at the heart of ...
... End the Ethernet Port Drought Ethernet ports are valuable. They are often the only way to connect computers, printers, and other devices (scanners or networkable hard drives), share Internet connections, or quickly transfer large amounts of data. Unfortunately, many of the components at the heart of ...
NETWORKING LAB -
... The fundamental difference between a router and a Layer 3 switch is that Layer 3 switches have optimized hardware to pass data as fast as Layer 2 switches, yet they make decisions on how to transmit traffic at Layer 3, just like a router. Within the LAN environment, a Layer 3 switch is usually faste ...
... The fundamental difference between a router and a Layer 3 switch is that Layer 3 switches have optimized hardware to pass data as fast as Layer 2 switches, yet they make decisions on how to transmit traffic at Layer 3, just like a router. Within the LAN environment, a Layer 3 switch is usually faste ...
Investor Presentation
... Access network as cost-effective alternative with full service to TDM access Ethernet services with PWE3 capabilities enable service providers to migrate from TDM networks to a new and richer service portfolio using converged network technology ...
... Access network as cost-effective alternative with full service to TDM access Ethernet services with PWE3 capabilities enable service providers to migrate from TDM networks to a new and richer service portfolio using converged network technology ...
MINI-LINK TN - Relink Networks
... It supports Native Ethernet as well as Native TDM or a mix of them. This allows our customers to start with TDM traffic, add Ethernet when data traffic increases, and move to all Ethernet when required. • Fixed Broadband over Microwave utilizes the integrated solutions for both Carrier and best effo ...
... It supports Native Ethernet as well as Native TDM or a mix of them. This allows our customers to start with TDM traffic, add Ethernet when data traffic increases, and move to all Ethernet when required. • Fixed Broadband over Microwave utilizes the integrated solutions for both Carrier and best effo ...
Network and Communications
... It has its own routing table. It might be simple, like yours, using another default route. At some point, it will reach a router that is running “default-less”, that has loaded the full table of routes for the whole Internet. Networks advertise routes for their own address space to their customers, ...
... It has its own routing table. It might be simple, like yours, using another default route. At some point, it will reach a router that is running “default-less”, that has loaded the full table of routes for the whole Internet. Networks advertise routes for their own address space to their customers, ...
Introduction to Distributed Systems & Networking
... End-to-End Argument • If the network guaranteed packet delivery – one might think that the applications would be simpler • No need to worry about retransmits – But need to check that file was written to the remote disk intact ...
... End-to-End Argument • If the network guaranteed packet delivery – one might think that the applications would be simpler • No need to worry about retransmits – But need to check that file was written to the remote disk intact ...
What is a Network?
... Ethernet running over UTP cables terminated with RJ45 connectors made use of hubs Hubs became the new backbone of many installations As hubs became less expensive, extra hubs were often used a repeaters in more complex networks Hubs are layer one devices (physical/electrical devices) and do not alte ...
... Ethernet running over UTP cables terminated with RJ45 connectors made use of hubs Hubs became the new backbone of many installations As hubs became less expensive, extra hubs were often used a repeaters in more complex networks Hubs are layer one devices (physical/electrical devices) and do not alte ...
What is a Network Protocol?
... using the internet. It is also widely used on many organizational networks due to its flexibility and wide array of functionality provided. Also, it enables computers to exchange data with each other in a meaningful, organized, and efficient way. ...
... using the internet. It is also widely used on many organizational networks due to its flexibility and wide array of functionality provided. Also, it enables computers to exchange data with each other in a meaningful, organized, and efficient way. ...
Link Layer - Instituto Tecnológico de Morelia
... control, etc – extracts datagram, passes to upper layer at receiving side ...
... control, etc – extracts datagram, passes to upper layer at receiving side ...
Networking Concepts An Introduction to
... whether they are being sent over a Cat 5 copper ethernet cable or a fiber optic cable. In addition to the standard source and destination information encoded in the generic packets we discussed earlier, the ethernet frame also contains checksum information, which allows the recipient to determine wh ...
... whether they are being sent over a Cat 5 copper ethernet cable or a fiber optic cable. In addition to the standard source and destination information encoded in the generic packets we discussed earlier, the ethernet frame also contains checksum information, which allows the recipient to determine wh ...
Selling an Idea or a Product
... » It means not only is the system up, but that it is working correctly. » Thus, it includes availability, security and fault-tolerance. Faulttolerance can be: fail-fast, i.e. stop immediately if data starts to corrupt, difficult to achieve). ...
... » It means not only is the system up, but that it is working correctly. » Thus, it includes availability, security and fault-tolerance. Faulttolerance can be: fail-fast, i.e. stop immediately if data starts to corrupt, difficult to achieve). ...