Congestion Control Algorithm - Computer Science and Engineering
... the kernel (i.e., Ethernet driver) must know the hardware address to send the data. ...
... the kernel (i.e., Ethernet driver) must know the hardware address to send the data. ...
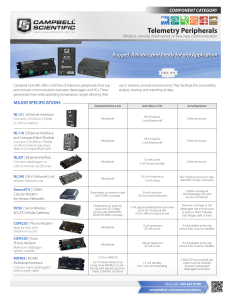
Telemetry Peripherals
... NL116 | Ethernet Interface and CompactFlash Module Connects CR1000 or CR3000 to LAN or Internet and stores data on a CompactFlash card ...
... NL116 | Ethernet Interface and CompactFlash Module Connects CR1000 or CR3000 to LAN or Internet and stores data on a CompactFlash card ...
Medium Access Control (MAC)
... A 6-byte destination address, which specifies either a single recipient node (unicast mode), a group of recipient nodes (multicast mode), or the set of all recipient nodes (broadcast mode). A 6-byte source address, which is set to the sender's globally unique node address. This may be used by the ne ...
... A 6-byte destination address, which specifies either a single recipient node (unicast mode), a group of recipient nodes (multicast mode), or the set of all recipient nodes (broadcast mode). A 6-byte source address, which is set to the sender's globally unique node address. This may be used by the ne ...
ppt - NOISE
... • Reliable Delivery: Guarantee to deliver the frame to the other end of the link without error. • Flow Control: The link layer can provide mechanisms to avoid overflowing the buffer • Error Correction: Determining where errors have occurred and then correcting those errors. ...
... • Reliable Delivery: Guarantee to deliver the frame to the other end of the link without error. • Flow Control: The link layer can provide mechanisms to avoid overflowing the buffer • Error Correction: Determining where errors have occurred and then correcting those errors. ...
20070717-verrant
... Single RSVP signaling session (main session) for end-to-end circuit. Subnet path is created via a separate RSVP-UNI session (subnet session), similar to using SNMP/CLI to create VLAN on an Ethernet switch. The simplest case: one VLSR covers the whole UNI subnet. VLSR is both the source and destinati ...
... Single RSVP signaling session (main session) for end-to-end circuit. Subnet path is created via a separate RSVP-UNI session (subnet session), similar to using SNMP/CLI to create VLAN on an Ethernet switch. The simplest case: one VLSR covers the whole UNI subnet. VLSR is both the source and destinati ...
The Network Layer in the Internet
... The IP addresses cannot be used for sending packets because the data link layer hardware does not understand Internet addresses. Most hosts are attached to a LAN by an interface board that only understands LAN addresses. For example, every Ethernet board is equipped with 48-bit Ethernet address. Man ...
... The IP addresses cannot be used for sending packets because the data link layer hardware does not understand Internet addresses. Most hosts are attached to a LAN by an interface board that only understands LAN addresses. For example, every Ethernet board is equipped with 48-bit Ethernet address. Man ...
Review Questions 1 File
... 8. Briefly compare hierarchy and random access networks in term of the band usage and reliability of transmission 9. Ethernet has not been a popular network for industrial use because of its probabilistic nature. Describe why there is now a strong drive for its use in industry. 10. Explain the basic ...
... 8. Briefly compare hierarchy and random access networks in term of the band usage and reliability of transmission 9. Ethernet has not been a popular network for industrial use because of its probabilistic nature. Describe why there is now a strong drive for its use in industry. 10. Explain the basic ...
SLIP&PPP - W3Professors
... starts the communication, the connection goes into the establishing state. 3.AUTHENATICATING:-The user sends the authenticate request packet & includes the user name & password. 4.NETWORKING:-The exchange of user control and data packets can started. 5.TERMINATING:-The users sends the terminate the ...
... starts the communication, the connection goes into the establishing state. 3.AUTHENATICATING:-The user sends the authenticate request packet & includes the user name & password. 4.NETWORKING:-The exchange of user control and data packets can started. 5.TERMINATING:-The users sends the terminate the ...
PowerPoint - ECSE - Rensselaer Polytechnic Institute
... √ ACKs and NAKs are required for providing reliability over an error-free channel √ MAC protocols are needed for point-to-point communications over a direct, unshared physical link between two hosts. √ Stop-and-wait uses a 1-bit sequence number √ Stop-and-wait and window-based protocols use ...
... √ ACKs and NAKs are required for providing reliability over an error-free channel √ MAC protocols are needed for point-to-point communications over a direct, unshared physical link between two hosts. √ Stop-and-wait uses a 1-bit sequence number √ Stop-and-wait and window-based protocols use ...
Introduction - Communications
... • Authentication: Authentication is optional. PPP supports two authentication protocols: Password Authentication Protocol (PAP) and Challenge Handshake Authentication Protocol (CHAP). • Network protocol configuration: PPP has network control protocols (NCPs) for numerous network layer protocols. The ...
... • Authentication: Authentication is optional. PPP supports two authentication protocols: Password Authentication Protocol (PAP) and Challenge Handshake Authentication Protocol (CHAP). • Network protocol configuration: PPP has network control protocols (NCPs) for numerous network layer protocols. The ...
T01
... • Two main elements: Interconnecting media and Network nodes. • Interconnecting media: cable determine the speed at which the data may be transmitted. • Coaxial cable, twisted Pair Cables • Fiber optic cable: it provides very high immunity to pickup and radiation as well as allowing very high data r ...
... • Two main elements: Interconnecting media and Network nodes. • Interconnecting media: cable determine the speed at which the data may be transmitted. • Coaxial cable, twisted Pair Cables • Fiber optic cable: it provides very high immunity to pickup and radiation as well as allowing very high data r ...
PPT
... • Authentication: Authentication is optional. PPP supports two authentication protocols: Password Authentication Protocol (PAP) and Challenge Handshake Authentication Protocol (CHAP). • Network protocol configuration: PPP has network control protocols (NCPs) for numerous network layer protocols. The ...
... • Authentication: Authentication is optional. PPP supports two authentication protocols: Password Authentication Protocol (PAP) and Challenge Handshake Authentication Protocol (CHAP). • Network protocol configuration: PPP has network control protocols (NCPs) for numerous network layer protocols. The ...
Final Presentation - High Speed Digital Systems Laboratory
... Developing a hardware Ethernet packet generator for Ethernet networks benchmarking. Support stand-alone operation with several user configurations. Implementation of the system on Altera PCI-E Development kit board with Stratix II GX FPGA. ...
... Developing a hardware Ethernet packet generator for Ethernet networks benchmarking. Support stand-alone operation with several user configurations. Implementation of the system on Altera PCI-E Development kit board with Stratix II GX FPGA. ...
r01-review
... • Destination responds (only to requester using unicast) with appropriate 48-bit Ethernet address • E.g, “reply 128.2.184.45 is-at 0:d0:bc:f2:18:58” sent to 0:c0:4f:d:ed:c6 ...
... • Destination responds (only to requester using unicast) with appropriate 48-bit Ethernet address • E.g, “reply 128.2.184.45 is-at 0:d0:bc:f2:18:58” sent to 0:c0:4f:d:ed:c6 ...
LURP
... ethernet card doesn’t know which ethernet address to put into the destination So it sends an Address Resolution Protocol (ARP) packet to the broadcast ethernet address asking if anyone knows about mail.cs.byu.edu Everyone else will ignore it, mail.cs.byu.edu should respond with a packet indicating w ...
... ethernet card doesn’t know which ethernet address to put into the destination So it sends an Address Resolution Protocol (ARP) packet to the broadcast ethernet address asking if anyone knows about mail.cs.byu.edu Everyone else will ignore it, mail.cs.byu.edu should respond with a packet indicating w ...
LAN and WAN
... using a line available from a public network such as a telephone network. • These public companies normally provide the service at the physical layer, the user is responsible for the protocol at the data link layer. • At the physical layer, the point-to-point connection between two devices can be ac ...
... using a line available from a public network such as a telephone network. • These public companies normally provide the service at the physical layer, the user is responsible for the protocol at the data link layer. • At the physical layer, the point-to-point connection between two devices can be ac ...
networks - CS-People by full name
... concession: every packet (now called a cell) is of fixed size--53 bytes--with 48 bytes devoted to data and the remainder to addressing and controlling the virtual circuit. By breaking the data into small cells it becomes possible to pack those cells into standardized cell-divided data streams, ``on- ...
... concession: every packet (now called a cell) is of fixed size--53 bytes--with 48 bytes devoted to data and the remainder to addressing and controlling the virtual circuit. By breaking the data into small cells it becomes possible to pack those cells into standardized cell-divided data streams, ``on- ...
Wireless Broadband Router
... Even Easier to Use In an effort to make the Wireless Broadband Router as uncomplicated as possible to deploy and use, the graphical user interface was redesigned from the ground up. Now, it’s a snap to check the status of the network or the broadband connection’s IP address. Nearly all other configu ...
... Even Easier to Use In an effort to make the Wireless Broadband Router as uncomplicated as possible to deploy and use, the graphical user interface was redesigned from the ground up. Now, it’s a snap to check the status of the network or the broadband connection’s IP address. Nearly all other configu ...
MI424WR Verizon FiOS Router Datasheet
... The First “Smart Home Gateway” Verizon’s next generation FiOS Router sets a new industry benchmark for performance. As a result, service providers can increase service speeds up to 1 Gbps (when equipped with Gigabit Ethernet interface) to meet the needs of an increasingly sophisticated consumer mark ...
... The First “Smart Home Gateway” Verizon’s next generation FiOS Router sets a new industry benchmark for performance. As a result, service providers can increase service speeds up to 1 Gbps (when equipped with Gigabit Ethernet interface) to meet the needs of an increasingly sophisticated consumer mark ...
r01
... • Destination responds (only to requester using unicast) with appropriate 48-bit Ethernet address • E.g, “reply 128.2.184.45 is-at 0:d0:bc:f2:18:58” sent to 0:c0:4f:d:ed:c6 ...
... • Destination responds (only to requester using unicast) with appropriate 48-bit Ethernet address • E.g, “reply 128.2.184.45 is-at 0:d0:bc:f2:18:58” sent to 0:c0:4f:d:ed:c6 ...
Document
... These protocols are very rigidly defined, and for good reason. Network cards must know how to talk to other network cards in order to exchange information Operating systems must know how to talk to network cards in order to send and receive data on the network Application programs must know how to t ...
... These protocols are very rigidly defined, and for good reason. Network cards must know how to talk to other network cards in order to exchange information Operating systems must know how to talk to network cards in order to send and receive data on the network Application programs must know how to t ...
Actiontec MI424WR Revision E Wireless Broadband Router
... improvement over the 32-bit devices sold today. The router’s latest MIPS core offers further performance improvement and additional instructions for networking applications reducing the number of cycles needed for even greater CPU efficiency. Additionally, the router features hardware-level Quality ...
... improvement over the 32-bit devices sold today. The router’s latest MIPS core offers further performance improvement and additional instructions for networking applications reducing the number of cycles needed for even greater CPU efficiency. Additionally, the router features hardware-level Quality ...