Nested Parallelism in Transactional Memory Kunal Agrawal Jeremy T. Fineman Jim Sukha
... Since a worker may signal an abort of a transaction running on a (possibly different) worker whose descendants have not yet completed, the XCilk protocol for a transaction abort is more involved than for a commit. Suppose worker i wishes to abort an active transaction X running on a different worker ...
... Since a worker may signal an abort of a transaction running on a (possibly different) worker whose descendants have not yet completed, the XCilk protocol for a transaction abort is more involved than for a commit. Suppose worker i wishes to abort an active transaction X running on a different worker ...
C Data Structures
... For simplicity, we implemented function insert (and other similar functions in this chapter) with a void return type. It’s possible that function malloc will fail to allocate the requested memory. In this case, it would be better for our insert function to return a status that indicates whether the ...
... For simplicity, we implemented function insert (and other similar functions in this chapter) with a void return type. It’s possible that function malloc will fail to allocate the requested memory. In this case, it would be better for our insert function to return a status that indicates whether the ...
Three Problems about Dynamic Convex Hulls
... Next, we turn to another related fundamental problem: dynamic halfplane range reporting. The goal here is to maintain a set S of n points in the plane under insertions and deletions so that we can efficiently report all points inside a query halfplane. We let k denote the number of reported points, ...
... Next, we turn to another related fundamental problem: dynamic halfplane range reporting. The goal here is to maintain a set S of n points in the plane under insertions and deletions so that we can efficiently report all points inside a query halfplane. We let k denote the number of reported points, ...
Stronger Lempel-Ziv Based Compressed Text Indexing | SpringerLink
... – Existential queries: operation exists(P ) tells us whether pattern P occurs in T or not. – Cardinality queries: operation count(P ) counts the number of occurrences of pattern P in T . – Locating queries: operation locate(P ) reports the starting positions of the occ occurrences of pattern P in T ...
... – Existential queries: operation exists(P ) tells us whether pattern P occurs in T or not. – Cardinality queries: operation count(P ) counts the number of occurrences of pattern P in T . – Locating queries: operation locate(P ) reports the starting positions of the occ occurrences of pattern P in T ...
Mining Frequent Closed Rooted Trees
... subtrees. A maximal frequent subtree is a frequent subtree none of whose proper supertrees are frequent. All the labeled frequent tree mining methods proposed in the literature are occurrence based and solve these two problems: – the computation of a tree inclusion relation – the enumeration of all ...
... subtrees. A maximal frequent subtree is a frequent subtree none of whose proper supertrees are frequent. All the labeled frequent tree mining methods proposed in the literature are occurrence based and solve these two problems: – the computation of a tree inclusion relation – the enumeration of all ...
A Fully Retroactive Priority Queues
... each non-leaf node x, we store a single partially retroactive priority queue that tracks all updates to the subtree rooted at x. Before continuing, it is important to note that a fully retroactive priority queue can be built from scratch, given k updates, in O(k log k) time. We see later that this p ...
... each non-leaf node x, we store a single partially retroactive priority queue that tracks all updates to the subtree rooted at x. Before continuing, it is important to note that a fully retroactive priority queue can be built from scratch, given k updates, in O(k log k) time. We see later that this p ...
Data Structures Through C - MLR Institute of Technology
... 5. The record of observations along with the detailed experimental Algorithm of the experiment in the immediate last session should be submitted and certified staff member in-charge 6. Not more than 3 students in a group are permitted to perform the experiment on the set. 7. The group-wise division ...
... 5. The record of observations along with the detailed experimental Algorithm of the experiment in the immediate last session should be submitted and certified staff member in-charge 6. Not more than 3 students in a group are permitted to perform the experiment on the set. 7. The group-wise division ...
External-Memory Algorithms for Processing Line Segments in
... short segments and are not stored in any multi-slab. Instead, they are passed down to lower levels of the tree where they may span recursively defined slabs and be stored. AB and EF are examples of short segments. The portions of long segments that do not completely span slabs are treated as small s ...
... short segments and are not stored in any multi-slab. Instead, they are passed down to lower levels of the tree where they may span recursively defined slabs and be stored. AB and EF are examples of short segments. The portions of long segments that do not completely span slabs are treated as small s ...
TOPICS IN ALGORITHMS
... Finite Capacity Dial-a-Ride Given a collection of objects in a metric space, a specified destination point for each object, and a vehicle with a capacity of at most k objects, the finite capacity dial-a-ride problem is to compute a shortest tour for the vehicle in which all objects can be delivered ...
... Finite Capacity Dial-a-Ride Given a collection of objects in a metric space, a specified destination point for each object, and a vehicle with a capacity of at most k objects, the finite capacity dial-a-ride problem is to compute a shortest tour for the vehicle in which all objects can be delivered ...
estructuras de datos sucintas para recuperación de
... Document listing is probably the most basic document retrieval problem. Given a collection of documents and a query pattern, document listing consists in obtaining all the documents in which the pattern occurs. Note that when the collections contain millions of documents, the output of the query cou ...
... Document listing is probably the most basic document retrieval problem. Given a collection of documents and a query pattern, document listing consists in obtaining all the documents in which the pattern occurs. Note that when the collections contain millions of documents, the output of the query cou ...
Circularly-linked list
... called association lists. There is very little good to be said about this use of linked lists; they are easily outperformed by other data structures such as self-balancing binary search trees even on small data sets (see the discussion in associative array). However, sometimes a linked list is dynam ...
... called association lists. There is very little good to be said about this use of linked lists; they are easily outperformed by other data structures such as self-balancing binary search trees even on small data sets (see the discussion in associative array). However, sometimes a linked list is dynam ...
Data Structures So Far
... The time complexity of an algorithm is the largest time required on any input of size n. (Worst case analysis.) O(n2): For any input size n ≥ n0, the algorithm takes no more than cn2 time on every input. Ω(n2): For any input size n ≥ n0, the algorithm takes at least cn2 time on at least one inpu ...
... The time complexity of an algorithm is the largest time required on any input of size n. (Worst case analysis.) O(n2): For any input size n ≥ n0, the algorithm takes no more than cn2 time on every input. Ω(n2): For any input size n ≥ n0, the algorithm takes at least cn2 time on at least one inpu ...
Pointers and Linked Lists
... the fact that you can draw pictures, like Display 15.1, that represent such structures. We now have pointers inside of structs and have these pointers pointing to structs that contain pointers, and so forth. In such situations the syntax can sometimes get involved, but in all cases the syntax follow ...
... the fact that you can draw pictures, like Display 15.1, that represent such structures. We now have pointers inside of structs and have these pointers pointing to structs that contain pointers, and so forth. In such situations the syntax can sometimes get involved, but in all cases the syntax follow ...
17 - Arizona Computer Science
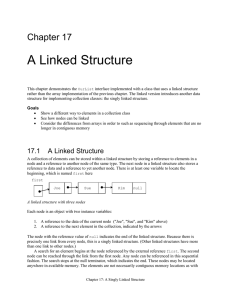
... The Node reference variable named first is not an internal part of the linked structure. The purpose of first is to find the beginning of the list so algorithms can find an insertion point for a new element, for example. In a singly linked structure, the instance variable data of each Node refers to ...
... The Node reference variable named first is not an internal part of the linked structure. The purpose of first is to find the beginning of the list so algorithms can find an insertion point for a new element, for example. In a singly linked structure, the instance variable data of each Node refers to ...
Towards Optimal Range Medians - Department of Computer Science
... We restrict ourselves to the median to simplify notation, but a generalization to arbitrary ranks is straightforward for all our results except the ones in Section 8. RMP naturally fits into a larger group of problems, in which an unsorted array is given, and for a query one wants to compute a certa ...
... We restrict ourselves to the median to simplify notation, but a generalization to arbitrary ranks is straightforward for all our results except the ones in Section 8. RMP naturally fits into a larger group of problems, in which an unsorted array is given, and for a query one wants to compute a certa ...
Chapter 17 - University of Arizona
... The Node reference variable named first is not an internal part of the linked structure. The purpose of first is to find the beginning of the list so algorithms can find an insertion point for a new element, for example. In a singly linked structure, the instance variable data of each Node refers to ...
... The Node reference variable named first is not an internal part of the linked structure. The purpose of first is to find the beginning of the list so algorithms can find an insertion point for a new element, for example. In a singly linked structure, the instance variable data of each Node refers to ...