Balloon: A Forward-Secure Append-Only Persistent Authenticated
... to make data processing by service providers transparent to data subjects whose personal data are being processed. Balloon can also be used as part of a secure logging system, similar to the history tree system by Crosby and Wallach [6]. Another closely related application is as an extension to Cert ...
... to make data processing by service providers transparent to data subjects whose personal data are being processed. Balloon can also be used as part of a secure logging system, similar to the history tree system by Crosby and Wallach [6]. Another closely related application is as an extension to Cert ...
Document
... Note that parentheses don’t appear. Expression trees are not ambiguous, as infix expressions are (can be). ...
... Note that parentheses don’t appear. Expression trees are not ambiguous, as infix expressions are (can be). ...
Chapter17
... item at head is already greater than item being inserted, or because list is empty – Insertion is after an existing node in a nonempty list ...
... item at head is already greater than item being inserted, or because list is empty – Insertion is after an existing node in a nonempty list ...
Creating Common Information Structures Using Lists Stored in SAS® DATA Step HASH Objects
... Since we are going to be storing our data in hash tables we have to make our keys, in an individual list, either numeric or character type. All the examples we will cover in this paper will have numeric typed keys. This is primarily because it makes sorting keys straightforward and simplifies the lo ...
... Since we are going to be storing our data in hash tables we have to make our keys, in an individual list, either numeric or character type. All the examples we will cover in this paper will have numeric typed keys. This is primarily because it makes sorting keys straightforward and simplifies the lo ...
Mounds: Array-Based Concurrent Priority Queues
... independently at each level, rather than through a large atomic section. This, in turn, allows the recursive cleaning moundify of one extractMin to run concurrently with another extractMin. The lock-free moundify operation retains the obligation to clear any dirty bit that it sets. However, since th ...
... independently at each level, rather than through a large atomic section. This, in turn, allows the recursive cleaning moundify of one extractMin to run concurrently with another extractMin. The lock-free moundify operation retains the obligation to clear any dirty bit that it sets. However, since th ...
I n - Virginia Tech
... Some Questions to Ask • Are all data inserted into the data structure at the beginning, or are insertions interspersed with other operations? • Can data be deleted? • Are all data processed in some welldefined order, or is random access allowed? ...
... Some Questions to Ask • Are all data inserted into the data structure at the beginning, or are insertions interspersed with other operations? • Can data be deleted? • Are all data processed in some welldefined order, or is random access allowed? ...
Range Majority in Constant Time and Linear Space
... Observation 1 For every query range Q there exists a unique level ` such that Q contains at least one and at most two consecutive blocks in T (`), and, if Q contains two blocks, then the nodes representing these blocks are not siblings in the tree T . Let U be a quadruple consisting of four consecut ...
... Observation 1 For every query range Q there exists a unique level ` such that Q contains at least one and at most two consecutive blocks in T (`), and, if Q contains two blocks, then the nodes representing these blocks are not siblings in the tree T . Let U be a quadruple consisting of four consecut ...
RRRpdfauthor=TTTpdfsubject=YYYpdfkeywords=Clemson
... theoretical efficiency of modern cache-oblivious data structures by using classic data structures such as weight-balanced trees or height balanced trees (e.g. AVL trees). We preserve the original topology and algorithms of the given balanced search tree using a simple post-processing with guaranteed ...
... theoretical efficiency of modern cache-oblivious data structures by using classic data structures such as weight-balanced trees or height balanced trees (e.g. AVL trees). We preserve the original topology and algorithms of the given balanced search tree using a simple post-processing with guaranteed ...
Persistent Data Structures
... the new modification and label it with the time stamp t. To query a specific version of the data structure at a particular time, we then only have to do a single binary search, after which we can access the data structure at that time. This requires O(n) extra space and time for each modification, h ...
... the new modification and label it with the time stamp t. To query a specific version of the data structure at a particular time, we then only have to do a single binary search, after which we can access the data structure at that time. This requires O(n) extra space and time for each modification, h ...
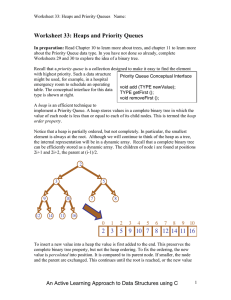
Priority Queues
... Upheap terminates when the key k reaches the root or a node whose parent has a key smaller than or equal to k Since a heap has height O(log n), upheap runs in O(log n) time ...
... Upheap terminates when the key k reaches the root or a node whose parent has a key smaller than or equal to k Since a heap has height O(log n), upheap runs in O(log n) time ...