Vulnerabilities - University of Wolverhampton
... passwords from a remote system; assuming the users are mostly English speakers, can attempt to guess the passwords at their leisure, by encrypting each of a list of English words and comparing each encryption against the stored encrypted version of users' passwords. As users often choose easily gues ...
... passwords from a remote system; assuming the users are mostly English speakers, can attempt to guess the passwords at their leisure, by encrypting each of a list of English words and comparing each encryption against the stored encrypted version of users' passwords. As users often choose easily gues ...
Week_Four_Network_MIMIC
... it enters a router and switch interface, it’s source, and destination , IP address, source and destination TCP or UDP port numbers, packet and byte counts. The objective is to document the megabytes per second between pairs of autonomous systems, networks, hosts, and applications. Use the Network Tr ...
... it enters a router and switch interface, it’s source, and destination , IP address, source and destination TCP or UDP port numbers, packet and byte counts. The objective is to document the megabytes per second between pairs of autonomous systems, networks, hosts, and applications. Use the Network Tr ...
downloading
... Consider this example: Two 100 Mbps circuits - 1 km of optic fiber - Via satellite with a distance of 30 km between the base and the satellite ...
... Consider this example: Two 100 Mbps circuits - 1 km of optic fiber - Via satellite with a distance of 30 km between the base and the satellite ...
Unit 8 - WordPress.com
... the client/server model and the master/slave model. In some cases, peer-to-peer communications is implemented by giving each communication node both server and client capabilities. In recent usage, peer-to-peer has come to describe applications in which users can use the Internet to exchange files w ...
... the client/server model and the master/slave model. In some cases, peer-to-peer communications is implemented by giving each communication node both server and client capabilities. In recent usage, peer-to-peer has come to describe applications in which users can use the Internet to exchange files w ...
Introduction and Overview - Assignment #1
... Congestion - It reduces congestion under normal operational conditions as smaller data packets seek out the most efficient route as links become available. Each packet may go a different route; each packet header address tells it where to go and drive the sequence of actions that allows reassembly ...
... Congestion - It reduces congestion under normal operational conditions as smaller data packets seek out the most efficient route as links become available. Each packet may go a different route; each packet header address tells it where to go and drive the sequence of actions that allows reassembly ...
Global-scale service deployment in the XenoServer platform
... overlay so that it is accessible by the MVM at a path chosen according to the new VM’s identifier, and notifies the copy-on-write NFS server. This then exports that locallyaccessible path as / such that it may only be mounted by the user’s virtual machine; the link-local address Xen assigns to each ...
... overlay so that it is accessible by the MVM at a path chosen according to the new VM’s identifier, and notifies the copy-on-write NFS server. This then exports that locallyaccessible path as / such that it may only be mounted by the user’s virtual machine; the link-local address Xen assigns to each ...
Slide 1
... Consider this example: Two 100 Mbps circuits - 1 km of optic fiber - Via satellite with a distance of 30 km between the base and the satellite ...
... Consider this example: Two 100 Mbps circuits - 1 km of optic fiber - Via satellite with a distance of 30 km between the base and the satellite ...
AW36294299
... system in order to minimize the processing overhead required by the receiving system each time it must unload a non-empty buffer. The PUSH + ACK attack is similar to a TCP SYN attack in that its goal is to deplete the resources of the victim system. The attacking agents send TCP packets with the PUS ...
... system in order to minimize the processing overhead required by the receiving system each time it must unload a non-empty buffer. The PUSH + ACK attack is similar to a TCP SYN attack in that its goal is to deplete the resources of the victim system. The attacking agents send TCP packets with the PUS ...
Review For Final - Eastern Illinois University
... 2. Replace hub Y with a switch. Now, what workstations and servers will receive a copy of a packet if the following workstations/servers transmit a message: Workstation 1 sends a message to workstation 3: Workstation 2 sends a message to Server 1: Server 1 sends a message to workstation 3: ...
... 2. Replace hub Y with a switch. Now, what workstations and servers will receive a copy of a packet if the following workstations/servers transmit a message: Workstation 1 sends a message to workstation 3: Workstation 2 sends a message to Server 1: Server 1 sends a message to workstation 3: ...
Review For Final - Eastern Illinois University
... 2. Replace hub Y with a switch. Now, what workstations and servers will receive a copy of a packet if the following workstations/servers transmit a message: Workstation 1 sends a message to workstation 3: Workstation 2 sends a message to Server 1: Server 1 sends a message to workstation 3: ...
... 2. Replace hub Y with a switch. Now, what workstations and servers will receive a copy of a packet if the following workstations/servers transmit a message: Workstation 1 sends a message to workstation 3: Workstation 2 sends a message to Server 1: Server 1 sends a message to workstation 3: ...
Top-Down Network Design
... Authentication, authorization, and auditing Encryption One-time passwords Security protocols – CHAP – RADIUS – IPSec ...
... Authentication, authorization, and auditing Encryption One-time passwords Security protocols – CHAP – RADIUS – IPSec ...
Preventative controls
... • Disasters are different from disruptions since the entire site can be destroyed. • The best solution is to have a completely redundant network that duplicates every network component, but in a different location. • Generally speaking, preventing disasters is difficult. The most fundamental princip ...
... • Disasters are different from disruptions since the entire site can be destroyed. • The best solution is to have a completely redundant network that duplicates every network component, but in a different location. • Generally speaking, preventing disasters is difficult. The most fundamental princip ...
Introducing the - Chicago SQL BI User Group > Home
... modify metadata repository with data such as last populated date • SSIS Package Management and Auditing • Version control is possible (packages are XML files) but cumbersome • Northwestern uses custom auditing solution for packages (ETL Execution Logs, metadata columns to each destination like execu ...
... modify metadata repository with data such as last populated date • SSIS Package Management and Auditing • Version control is possible (packages are XML files) but cumbersome • Northwestern uses custom auditing solution for packages (ETL Execution Logs, metadata columns to each destination like execu ...
Applications and Digital Transmission Fundamentals
... • Web users generate large traffic volumes • Traffic causes congestion & delay • Can improve delay performance and reduce traffic in Internet by moving content to servers closer to the user • Web proxy servers cache web information – Deployed by ISPs – Customer browsers configured to first access IS ...
... • Web users generate large traffic volumes • Traffic causes congestion & delay • Can improve delay performance and reduce traffic in Internet by moving content to servers closer to the user • Web proxy servers cache web information – Deployed by ISPs – Customer browsers configured to first access IS ...
PGTP: Power Aware Game Transport Protocol for Multi
... work on power aware transport protocols for mobile games. As shown in Section III-A, games have unique transport requirements. In the following section we show conventional protocols do not address all these requirements. UDP [8] is the lightest and low latency protocol. Though it is widely used by ...
... work on power aware transport protocols for mobile games. As shown in Section III-A, games have unique transport requirements. In the following section we show conventional protocols do not address all these requirements. UDP [8] is the lightest and low latency protocol. Though it is widely used by ...
ppt - People.cs.uchicago.edu
... a nice GUI. Web browser also responsible for displaying content sent back by server – text, html, images, audio. Broswer must handle server error messages in some elegant way. What errors might be handled by web client itself? ...
... a nice GUI. Web browser also responsible for displaying content sent back by server – text, html, images, audio. Broswer must handle server error messages in some elegant way. What errors might be handled by web client itself? ...
Paper Presentation - Information Services and Technology
... [1]Seyed Fayazbakhsh, Amin Tootoonchian, Yin Lin, Ali Ghodsi, KC Ng, Bruce Maggs, Vyas Sekar, Scott Shenker. Less Pain, Most of the Gain: Incrementally Deployable ICN. in SIGCOMM 2013. ...
... [1]Seyed Fayazbakhsh, Amin Tootoonchian, Yin Lin, Ali Ghodsi, KC Ng, Bruce Maggs, Vyas Sekar, Scott Shenker. Less Pain, Most of the Gain: Incrementally Deployable ICN. in SIGCOMM 2013. ...
CV (Word) - OoCities
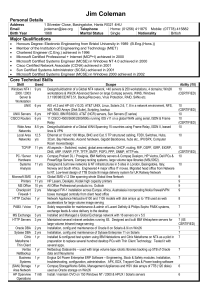
... Server Projects Team Leader. Served on customer site at Eli Lilly & Company based in Basingstoke, Hants. Responsible for a team of 3 Windows 2000 / NT4 server engineers. Managed the CGEY contract with Lilly to build a number of Windows 2000 servers to deliver new Production and QA Siebel 7.5 CRM sys ...
... Server Projects Team Leader. Served on customer site at Eli Lilly & Company based in Basingstoke, Hants. Responsible for a team of 3 Windows 2000 / NT4 server engineers. Managed the CGEY contract with Lilly to build a number of Windows 2000 servers to deliver new Production and QA Siebel 7.5 CRM sys ...
HAM RADIO Mesh Networking 202 SeaPac Northwest
... • Then Connect to IRC Server Address • Wifi to: NW-MESH-AP1-2462 • IRC Server: 44.24.195.1 ...
... • Then Connect to IRC Server Address • Wifi to: NW-MESH-AP1-2462 • IRC Server: 44.24.195.1 ...
NetLord - sigcomm
... − Emulating shuffle-phase of Map-Reduce jobs − Each shuffle: 74 mappers & 74 reducers, one per server − Each mapper transfers 10MB of data to all reducers ...
... − Emulating shuffle-phase of Map-Reduce jobs − Each shuffle: 74 mappers & 74 reducers, one per server − Each mapper transfers 10MB of data to all reducers ...
Servlet
... available that are good for "personal" use or low-volume Web sites. However, with the major exception of Apache, which is free, most commercial-quality Web servers are relatively expensive. ...
... available that are good for "personal" use or low-volume Web sites. However, with the major exception of Apache, which is free, most commercial-quality Web servers are relatively expensive. ...
UNIX Networking
... service request from a client – Client processes started on same system or another system within a network. – Client process sends a request across the network to the server requesting service of some form. 2000 Copyrights, Danielle S. Lahmani ...
... service request from a client – Client processes started on same system or another system within a network. – Client process sends a request across the network to the server requesting service of some form. 2000 Copyrights, Danielle S. Lahmani ...
The network layer
... may pass through several routers in its journey from its source to its destination. Carrying the packet from one node to another (where a node can be a computer or a router) is the responsibility of the data link layer. ...
... may pass through several routers in its journey from its source to its destination. Carrying the packet from one node to another (where a node can be a computer or a router) is the responsibility of the data link layer. ...
Lag
In online gaming, lag is a noticeable delay between the action of players and the reaction of the server. Although lag may be caused by high latency, it may also occur due to insufficient processing power in the client(Screen-lag). Screen-Lag can also happened in single player games as well.The tolerance for lag depends heavily on the type of game. For instance, a strategy game or a turn-based game with a low pace may have a high threshold or even be mostly unaffected by high delays, whereas a twitch gameplay game such as a first-person shooter with a considerably higher pace may require significantly lower delay to be able to provide satisfying gameplay. But, the specific characteristics of the game matter. For example, fast chess is a turn-based game that is fast action and may not tolerate high lag. And, some twitch games can be designed such that only events that don't impact the outcome of the game introduce lag, allowing for fast local response most of the time.