* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Vulnerabilities - University of Wolverhampton
Piggybacking (Internet access) wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Computer security wikipedia , lookup
Computer network wikipedia , lookup
Extensible Authentication Protocol wikipedia , lookup
Network tap wikipedia , lookup
Deep packet inspection wikipedia , lookup
Airborne Networking wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Distributed firewall wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Wireless security wikipedia , lookup
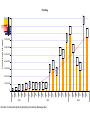
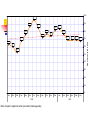
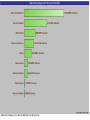
Vulnerabilities Internet attack patterns Typically 1. 2. 3. 4. 5. 6. A weakness is discovered (usually a software bug) Many sites are attacked Short term patch is created Full repairs to software or protocols are issued Majority of web sites etc implement repairs Unrepaired sites end up blacklisted - poses a problem as it then advertises the sites with weaknesses – hence more attacks happen Denial Of Service attacks or SYN flooding In TCP handshaking the sequence is as follows Client S y n Server SYN Time SYN + ACK ACK Client and server can now send service specific data Perils of half-open connections If after the server has send its SYN + ACK response the client does not send a ACK response - half-open connection But the server has built in its system memory a data structure describing all pending connections. Will time out eventually Attacker carries on creating these may cause memory overflow and server to crash or at least not able to accept any new connections until table emptied out IP spoofing location of attacking system is obscured because source addresses in the SYN packets are often implausible. When the packet arrives at the victim server system, there is no way to determine its true source. SYN flooding remedies Non yet with the current IP protocol technology. However, proper router configuration can reduce the likelihood that a site will be the source of one of these attacks. Currently, the best method is to install a filtering router that restricts the input to your external interface (known as an input filter) by not allowing a packet through if it has a source address from your internal network. would prevent outside attackers from sending you packets pretending to be from your internal network. also prevents packets originating within your network from pretending to be from outside your network. RFC 2267 Should also filter outgoing packets that have a source address different from your internal network to prevent a source IP spoofing attack from originating from your site. These filters will not stop all TCP SYN attacks, since outside attackers can spoof packets from any outside network, and internal attackers can still send attacks spoofing internal addresses. IP spoofing – changing source IP address Stealth scan method of spoofing Before an attacker will attack a specific server they will in most cases want to scan the system in order to find out as much as possible about the system. this scan could alert fire-walls, IDS systems and their administrators of a forthcoming attack, and could point the administrator to the originator of a following (basic) DDOS attack. By hiding the actual scan in a large amount of spoofed scanning datagrams from a wide range of IP addresses, the attacker will be able to hide the real scan from the administrators. Intrusion Detection Systems DoS In order to detect and stop hack attacks many companies now implement so IDS. -when combined with fire-walls that support them will in the ideal case stop a hack that is in progress ones specific or generic hacking fingerprints are detected. Downside of IDS systems is that they have to do a wide range of CPU intensive and state-full protocol analysis. Can make Datagrams to use a maximum amount of IDS resources (state objects and cpu) per byte of datagram. By using again a large amount of spoofed IP addresses, and by again using this to create as much as possible state objects on the IDS system, combined with large strains on the IDS to do the full set of protocol analysis it will in many cases be possible to heighten the time taken with IDS detection to such an extend that the full attack can be implemented before the IDS has been able to detect it. Anti spoofing techniques Border router filter rules Simple principle - Don't let anything out with a source IP address not belonging to the ISP rfc2827 Don't let anything in with a source IP address belonging to the ISP The first one is basically the most important, also used to fight DoS attacks, AS for my ISP 171.85.0.0 AS of neighbouring ISP 204.12.15.0 DOS - Smurfing Simple concept – send forged ICMP echo request packets to IP broadcast addresses of an unsuspecting network. All hosts on that network send a ICMP reply to the spoofed IP address of the victim When (potentially) all the machines on a network respond to this ICMP echo request, the result can be severe network congestion or even breakdown. Attacker Sends Broadcast packet to unsuspecting network All hosts send replies to spoofed IP address of victim Router Ping (broadcast address) Victim Attackers have developed automated tools (botnets etc) that enable them to send these attacks to multiple intermediaries at the same time, causing all of the intermediaries to direct their responses to the same victim. Attackers have also developed tools to look for network routers that do not filter broadcast traffic and networks where multiple hosts respond. These networks can the subsequently be used as intermediaries in attacks. Dictionary Attack – cracking of authentication passwords Authentication passwords are stored in a file in both UNIX and Windows – but are usually encrypted with an algorithm that is non reversible (MD5 etc) Passwords are stored in password file encrypted using a one way algorithm (MD5 etc), user enters password which is encrypted and the encrypted version is compared with the stored version With a brute force attack, where all possibilities are searched through exhaustively, a dictionary attack only tries possibilities which are most likely to succeed derived from a list of words in a dictionary. Weakness with passwords Usually word from native language Common list of words typically used Dictionary attacks may be applied in two main situations: in cryptanalysis, in trying to determine the decryption key for a given piece of ciphertext; in computer security, in trying to circumvent an authentication mechanism for accessing a computer system by guessing passwords. An attacker may be able to obtain a copy of the list of encrypted passwords from a remote system; assuming the users are mostly English speakers, can attempt to guess the passwords at their leisure, by encrypting each of a list of English words and comparing each encryption against the stored encrypted version of users' passwords. As users often choose easily guessed passwords, this has historically succeeded about 4 times out of 10 when a reasonably large list is used. Dictionaries for most human languages (even those no longer used) are easily accessible on the Internet, meaning even the use of foreign words is practically useless in preventing dictionary attacks. One way encryption of password Stored in Password table Client Alix.Bergeret ADSNUYTGHLKLLL Password encrypted by the client using same algorithm then passed over network If Hash values are equal then client is authenticated username Encrypted password Alix.Bergeret ADSNUYTGHLKLLL Matthew.Green NJKFFDSHPTTDRD Ian.Coulson VFGMNBDEQQASU Brendan.Riordan VHGUIOUIYEDRDT Chris.Dennett CXZAASWEWEDFD Andy.Sloane MLOPIUYTRFFGHJ Mary.Garvey MNJTYUUIFVCXFG Brian.Penfold REDERFGGGHYTR Password authentication server Combating dictionary attacks An attacker can by encrypting and storing a list of encrypted dictionary words, sorted by the encrypted 'value'. requires a large amount of storage and often a considerable amount of preparation time, but makes the actual attack almost instantaneous. particularly effective when a large number of passwords are to be cracked at once. Attacker simply takes a list of commonly used passwords and passes them all thought the same algorithm Then sorts them alphabetically username Encrypted password Word Hashed word Alix.Bergeret ADSNUYTGHLKLLL cricket ABVGTHYULPMMN Matthew.Green NJKFFDSHPTTDRD football ADSNUYTGHLKLLL england CFTGERHTYUUUU Ian.Coulson VFGMNBDEQQASU sister QRTSNDCNCNNNN Brendan.Riordan VHGUIOUIYEDRDT christopher RTSGHWEREEEDM Chris.Dennett CXZAASWEWEDFD charlie STTHHHHHERERE louise NMZOAOWJBHEEU Andy.Sloane MLOPIUYTRFFGHJ Mary.Garvey MNJTYUUIFVCXFG Brian.Penfold REDERFGGGHYTR Crackers sorted list of hashed words Easy to determine Alix.Begeret password by comparing hash values Password list A SALT is a value used to modify a hash of a password. Unfortunately, obtaining the password file revealed hash values which then could be compared to hash values (the Hash algorithm are public) for popular passwords, thus revealing the password itself. To avoid this, a salt value is hashed along with password, thus changing the hash value and making a known-hash attack difficult. Salt value is a random characters (or more often the username) which can be stored – even if attacker can see salt value means they have to add salt value to every dictionary value – has it and do a comparison against that one entry in the password file Add a salt value Username Password before any encryption Alix.Bergeret Football Password is given a salt value -Username and password added together Alix.Bergeret + Football = Alix.BergeretFootball Then encrypted Alix.BergeretFootball -> FFFGHTYPOIYT As Alix.BergeretFootball is not a word you would find in a common list of words then attacker will not find the encrypted version in his list – makes it impossible to crack attack can be greatly reduced by limiting the number of authentication attempts that can be performed each minute, and even blocking further attempts after a threshold of failed authentication attempts is reached. There are downloadable tools for password cracking RIP attacks Routing Information Protocol (RIP) Routing attacks is often seen in routers which implemented the original RIP. RIP is used to distribute routing information within networks, such as shortest-paths, and advertising routes out from the local network. original version of RIP has no built in authentication, and the information provided in a RIP packet is often used without verifying it. Attacker could forge a RIP packet, claiming his host "X" has the fastest path out of the network. All packets sent out from that network would then be routed through X, where they could be modified or examined. An attacker could also use RIP to effectively impersonate any host, by causing all traffic sent to that host to be sent to the attacker's machine instead. The version 2 of RIP was enhanced with a simple password authentication algorithm, which makes RIP attack harder to happen. IPsec VPN provides a way to keep routing information encrypted among the routers implemented the IPsec VPN. Packet Sniffing NIC cards normally only process packets (MAC) addressed to your PC Software/hardware is easily available to do this Can turn it promiscuous so that it processes all packets passing your portion of the network Means the contents off all packets can be seen – FTP, Telnet, POP3 all send passwords in clear text. Many more implications Should not be a problem in a switched environment as only packets destined for your PC will be on your segment, but …. Packet Sniffing MAC Flooding is an ARP Cache Poisoning technique aimed at network switches. When certain switches are overloaded they often drop into a "hub" mode. In "hub" mode, the switch is too busy to enforce its port security features and just broadcasts all network traffic to every computer in your network. By flooding a switch's ARP table with many spoofed ARP replies, a hacker can overload many vendor's switches and then packet sniff your network while the switch is in "hub" mode. 264,354 247,027 205,953 215,643 259,014 337,050 123,044 4,000,000 5,000,000 3,455,079 7,000,000 7,427,545 7,724,659 6,739,929 8,000,000 5,231,375 4,522,495 4,838,962 9,000,000 2,800,649 2,098,012 6,000,000 9,139,704 10,000,000 n Ju 2005 ay M r Ap ar M b Fe n Ja ec D ct ov N O p Se g Au Number of intercepted phishing attempts (provided by MessageLabs) l 2004 3,015,685 2,493,734 3,000,000 Ju n Ju ay M r Ap ar M b Fe n Ja ec D ov N 2003 69,982 43,222 p Se ct 279 1,000,000 O g Au 0 14 Phishing Emails Intercepted Phishing 2,000,000 100% 94.51% 90% 86.29% 84.25% 81.41% 83.11% 76.76% 76.02% 80% 76.30% 73.77% 72.14% 68.81% 67.61% 68.76% 68.72% 67.25% 70% 59.90% 60% 52.82% 50% 40% 30% 20% 10% 0% Jan Feb Mar Apr May Jun Jul Aug 2004 Ratio of spam to legitimate email (provided by MessageLabs) Sep Oct Nov Dec Jan Feb Mar Apr 2005 May Jun Spam Percentage in Mail 63.01% 1 in 0 1 in 10.37 1 in 10.42 1 in 10.41 1 in 13.75 1 in 14.53 1 in 19.26 1 in 20.69 1 in 20 1 in 28.16 1 in 32.24 1 in 32.16 1 in 33.54 1 in 34.90 1 in 43.37 1 in 46.12 1 in 44.32 1 in 42.78 1 in 40 1 in 60 1 in 80 1 in 100 1 in 120 1 in 129.42 1 in 140 Jan Feb Mar Apr May Jun Jul Aug Sep Oct Nov 2004 Ratio of virus-laden email to legitimate email (provided by MessageLabs) Dec Jan Feb Mar Apr 2005 May Jun Virus Ratio in Mail 1 in 51.75 700,000 612,408 600,000 500,000 Number Stopped 400,000 300,000 275,339 200,000 100,000 3,386 Timeline Number of intercepted directed phishing attempts (provided by MessageLabs) n Ju 2005 -100,000 ay M 2,962 r Ap n Ja 10,903 ar M 56 b Fe 0 Attacks by industry (provided by IBM Security Monitoring) Attacks by category (provided by IBM Security Monitoring)