Smoke and Mirrors: Reflecting Files at a Geographically Remote Location Without Loss of Performance.
... mote distances at the update rates seen within their datacenters. Faced with this apparent impossibility, they literally risk disaster. It is not feasible to simply legislate a solution, because today’s technical options are inadequate. Financial systems are under huge competitive pressure to suppor ...
... mote distances at the update rates seen within their datacenters. Faced with this apparent impossibility, they literally risk disaster. It is not feasible to simply legislate a solution, because today’s technical options are inadequate. Financial systems are under huge competitive pressure to suppor ...
Peer-to-Peer Networks For Content Sharing
... Napster server network. Clients connect automatically to an internally designated "metaserver" that acts as common connection arbiter. This metaserver assigns at random an available, lightly loaded server from one of the clusters. Servers appeared to be clustered about five to a geographical site an ...
... Napster server network. Clients connect automatically to an internally designated "metaserver" that acts as common connection arbiter. This metaserver assigns at random an available, lightly loaded server from one of the clusters. Servers appeared to be clustered about five to a geographical site an ...
AT16827: TCP/IP Server-Client with CycloneTCP
... The server is a program that receives a request, performs the required service and sends back the results in a reply. A server can usually deal with multiple requests from same or different clients at the same time. In real network scenario, the client and server may exist in different networks as s ...
... The server is a program that receives a request, performs the required service and sends back the results in a reply. A server can usually deal with multiple requests from same or different clients at the same time. In real network scenario, the client and server may exist in different networks as s ...
Remote Access Techniques
... A new class of products has emerged—remote node. Whereas remote control establishes a connection between two PCs and usually relies on dial-up connections by modem, remote node relies on a remote access server that is set up and maintained at a central location. Many remote users, all at different l ...
... A new class of products has emerged—remote node. Whereas remote control establishes a connection between two PCs and usually relies on dial-up connections by modem, remote node relies on a remote access server that is set up and maintained at a central location. Many remote users, all at different l ...
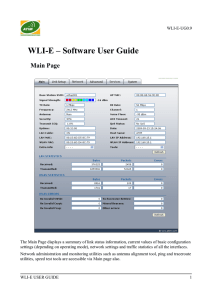
WLI-E – Software User Guide
... transferred between devices through the Ethernet interface either way. Both unicast IP traffic (conversations between two hosts using HTTP, SMTP, SSH and other protocols) and broadcast traffic (while addressing all hosts in a given network range with a single destination IP address) is accounted. As ...
... transferred between devices through the Ethernet interface either way. Both unicast IP traffic (conversations between two hosts using HTTP, SMTP, SSH and other protocols) and broadcast traffic (while addressing all hosts in a given network range with a single destination IP address) is accounted. As ...
Good Control/Good Proxy Server Installation
... operating system, if you are not already running it. Microsoft does not provide an easy path to upgrade the word size. So you need to install the Windows 64-bit OS first and then install the latest Good Control. Do a full backup of your current 32-bit GC installation as a safety measure. ...
... operating system, if you are not already running it. Microsoft does not provide an easy path to upgrade the word size. So you need to install the Windows 64-bit OS first and then install the latest Good Control. Do a full backup of your current 32-bit GC installation as a safety measure. ...
Net-Centric Computing Overview
... Information system (applications). Multiple machines. Over the network. Seamlessly integrated. Using standard data formats. There are some securities. Example, anyone ? ...
... Information system (applications). Multiple machines. Over the network. Seamlessly integrated. Using standard data formats. There are some securities. Example, anyone ? ...
Printopia® Pro - Decisive Tactics
... When a new version of Printopia Pro is available, you will be prompted automatically. You may check for updates manually at any time using the “Check for Updates...” menu item. When an update is available, you’ll see this: ...
... When a new version of Printopia Pro is available, you will be prompted automatically. You may check for updates manually at any time using the “Check for Updates...” menu item. When an update is available, you’ll see this: ...
Development of DNS
... better organizing themselves – instead of single flat file – Organizations are of different sizes – depth should be of different levels ...
... better organizing themselves – instead of single flat file – Organizations are of different sizes – depth should be of different levels ...
VK2-3MPBIR3V9F User manual
... can be monitored on a real-time screen regardless of distances and locations. By using its dedicated program, many users are able to have an access to the Network Camera at once or a single user can monitor various network cameras at the same time. It also enables users to play, store and retrieve a ...
... can be monitored on a real-time screen regardless of distances and locations. By using its dedicated program, many users are able to have an access to the Network Camera at once or a single user can monitor various network cameras at the same time. It also enables users to play, store and retrieve a ...
AirLive WL-5460AP Manual
... Access Control (MAC) address to your router. This procedure will cause the router to appear as a single PC, while allowing online access to multiple computers on your network. ...
... Access Control (MAC) address to your router. This procedure will cause the router to appear as a single PC, while allowing online access to multiple computers on your network. ...
Slides
... mechanism, with one end opened for reading and the other end for writing. pipe() system call is used to create a readwrite pipe that may later be used to communicate with a forked off process. An array of 2 integers as the argument that will be used to save the two file descriptors used to acces ...
... mechanism, with one end opened for reading and the other end for writing. pipe() system call is used to create a readwrite pipe that may later be used to communicate with a forked off process. An array of 2 integers as the argument that will be used to save the two file descriptors used to acces ...
R1.What is the difference between a host and an end system?List
... destination without message segmentation. How long does it take to move the message from the source host to the first packet switch? Keeping in mind that each switch uses store-and-forward packet switching, what is the total time to move the message from source host to destination host? ...
... destination without message segmentation. How long does it take to move the message from the source host to the first packet switch? Keeping in mind that each switch uses store-and-forward packet switching, what is the total time to move the message from source host to destination host? ...
Harden Communications
... spoofed, then there is no way to know if the information is correct, and no way to avoid sending confidential information where it should not go. Integrity ensures that the data has not changed during transport. If integrity is not guaranteed, then an attacker might successfully change data. Encrypt ...
... spoofed, then there is no way to know if the information is correct, and no way to avoid sending confidential information where it should not go. Integrity ensures that the data has not changed during transport. If integrity is not guaranteed, then an attacker might successfully change data. Encrypt ...
NetToolTM - Fluke testery
... Each Fluke Networks product is warranted to be free from defects in material and workmanship under normal use and service. The warranty period is one year and begins on the date of purchase. Parts, accessories, product repairs and services are warranted for 90 days. This warranty extends only to the ...
... Each Fluke Networks product is warranted to be free from defects in material and workmanship under normal use and service. The warranty period is one year and begins on the date of purchase. Parts, accessories, product repairs and services are warranted for 90 days. This warranty extends only to the ...
SIP - OpenLoop.com
... ACK Final response to the INVITE OPTIONS Ask for server capabilities CANCEL Cancels a pending request BYE Terminates a session REGISTER Sends user’s address to server ...
... ACK Final response to the INVITE OPTIONS Ask for server capabilities CANCEL Cancels a pending request BYE Terminates a session REGISTER Sends user’s address to server ...
HERA600 Series User Guide
... Look for a ICCID on the appropriate SIM slot Check that the APN matches the type of SIM inserted, for instance www.eseye.com Look to see what the network name is Check the signal strength. A good signal strength is over -100dB. (Read between -50 and -99dB) 10. Look for a PPP IP. It should be differe ...
... Look for a ICCID on the appropriate SIM slot Check that the APN matches the type of SIM inserted, for instance www.eseye.com Look to see what the network name is Check the signal strength. A good signal strength is over -100dB. (Read between -50 and -99dB) 10. Look for a PPP IP. It should be differe ...
ch08
... Introducing DHCP • DHCP – Service that provides a way for client computer to request IP address assignment – Delivers necessary configuration information to clients – Traces its origins back to an earlier protocol named BOOTP – Servers can manage one or more ranges of IP addresses ...
... Introducing DHCP • DHCP – Service that provides a way for client computer to request IP address assignment – Delivers necessary configuration information to clients – Traces its origins back to an earlier protocol named BOOTP – Servers can manage one or more ranges of IP addresses ...
overview of the project
... The high false alarm rate is the primary drawback of behavior-based techniques because the entire scope of the behavior of an information system may not be covered during the learning phase. Also, behavior can change over time, introducing the need for periodic online retraining of the behavior prof ...
... The high false alarm rate is the primary drawback of behavior-based techniques because the entire scope of the behavior of an information system may not be covered during the learning phase. Also, behavior can change over time, introducing the need for periodic online retraining of the behavior prof ...
Chapter_7_V6.0_HU
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for us ...
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for us ...
point to point and point to multi point calls over IP
... Marker bit. The interpretation of the marker is defined by a profile. It is intented to allow significant events such as frame boundaries to be marked in the packet stream • PT Payload type. Identifies the format of the RTP payload and determines its interoperability by the application. A profile sp ...
... Marker bit. The interpretation of the marker is defined by a profile. It is intented to allow significant events such as frame boundaries to be marked in the packet stream • PT Payload type. Identifies the format of the RTP payload and determines its interoperability by the application. A profile sp ...
PDF file - The Open University of Hong Kong
... As a distance education student, the World Wide Web is an integral part of your life. In courses such as this one, you rely on it to communicate with tutors and fellow students, download study materials, and view online resources. This experience is bound to make you very familiar with the Web from ...
... As a distance education student, the World Wide Web is an integral part of your life. In courses such as this one, you rely on it to communicate with tutors and fellow students, download study materials, and view online resources. This experience is bound to make you very familiar with the Web from ...
PowerPoint
... • Goal: to avoid congestion before it occurs by dropping isolated packets among different streams. Packets are dropped according to the current amount of data into a buffer. If buffer_level < thr1 p(drop) = 0 case 1 thr1 < buffer_level < thr2 0 < p(drop) < 1 case 2 otherwise p(drop) = 1 case 3 • (W) ...
... • Goal: to avoid congestion before it occurs by dropping isolated packets among different streams. Packets are dropped according to the current amount of data into a buffer. If buffer_level < thr1 p(drop) = 0 case 1 thr1 < buffer_level < thr2 0 < p(drop) < 1 case 2 otherwise p(drop) = 1 case 3 • (W) ...
3rd Edition: Chapter 4 - Northwestern Networks Group
... received at router running DHCP server Ethernet demuxed to IP demuxed, UDP demuxed to ...
... received at router running DHCP server Ethernet demuxed to IP demuxed, UDP demuxed to ...
Lag
In online gaming, lag is a noticeable delay between the action of players and the reaction of the server. Although lag may be caused by high latency, it may also occur due to insufficient processing power in the client(Screen-lag). Screen-Lag can also happened in single player games as well.The tolerance for lag depends heavily on the type of game. For instance, a strategy game or a turn-based game with a low pace may have a high threshold or even be mostly unaffected by high delays, whereas a twitch gameplay game such as a first-person shooter with a considerably higher pace may require significantly lower delay to be able to provide satisfying gameplay. But, the specific characteristics of the game matter. For example, fast chess is a turn-based game that is fast action and may not tolerate high lag. And, some twitch games can be designed such that only events that don't impact the outcome of the game introduce lag, allowing for fast local response most of the time.