* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download overview of the project
Asynchronous Transfer Mode wikipedia , lookup
Wireless security wikipedia , lookup
Computer network wikipedia , lookup
Airborne Networking wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Network tap wikipedia , lookup
Internet protocol suite wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Real-Time Messaging Protocol wikipedia , lookup
Deep packet inspection wikipedia , lookup
Distributed firewall wikipedia , lookup
Hypertext Transfer Protocol wikipedia , lookup
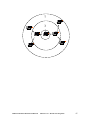
BIDE Behavior Intrusion Detection: Enhanced CS591 Semester Project Dr. Chow FALL 2005 Hakan Evecek Rodolfo Ortiz Magdaleno Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 1 Table of Contents OVERVIEW OF IDS ............................................................................................................. 4 Signature Based IDS ........................................................................................................... 4 Distributed IDS ................................................................................................................... 4 Host-based system .............................................................................................................. 5 Network-based system ........................................................................................................ 5 Strengths and Weaknesses of Host-Based and Network-Based IDS ................................. 6 OVERVIEW OF BEHAVIOR BASED IDS.......................................................................... 8 SNORT – OPEN SOURCE IDS .......................................................................................... 11 Packet decoder .................................................................................................................. 12 Preprocessor ..................................................................................................................... 12 Detection engine ............................................................................................................... 13 Alerting ............................................................................................................................. 13 OVERVIEW OF THE PROJECT ........................................................................................ 14 PROTOCOLS ....................................................................................................................... 18 DNS ...................................................................................................................................... 19 Basic Background ............................................................................................................. 19 How DNS works ............................................................................................................... 19 Why we chose DNS .......................................................................................................... 20 Vulnerabilities .................................................................................................................. 21 ICMP .................................................................................................................................... 22 Basic Background ............................................................................................................. 22 How it works .................................................................................................................... 22 Why we chose ICMP ........................................................................................................ 23 Vulnerabilities .................................................................................................................. 23 HTTP .................................................................................................................................... 24 Basic Background ............................................................................................................. 24 How HTTP works ............................................................................................................. 24 Why we chose HTTP ........................................................................................................ 24 Vulnerabilities .................................................................................................................. 25 HTTPS .................................................................................................................................. 26 Basic Background ............................................................................................................. 26 How HTTPS works .......................................................................................................... 26 Why we chose HTTPS ..................................................................................................... 27 Vulnerabilities .................................................................................................................. 27 TESTBED............................................................................................................................. 28 Analysis Console for Intrusion Databases (ACID) .......................................................... 29 Tools used in the Testbed ................................................................................................. 30 RESULTS OF THE PROJECT ............................................................................................ 32 ICMP ............................................................................................................................ 32 DNS .............................................................................................................................. 34 HTTP vs HTTPS .......................................................................................................... 35 PROPOSED APPROACH ................................................................................................... 38 ICMP ................................................................................................................................ 39 DNS .................................................................................................................................. 40 Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 2 HTTP ................................................................................................................................ 41 HTTPS .............................................................................................................................. 42 SUSPICIOUS PACKETS .................................................................................................... 43 Behavioral signatures ....................................................................................................... 43 Based signatures ............................................................................................................... 43 Inductive signatures .......................................................................................................... 44 FUTURE WORK ................................................................................................................. 46 CONCLUSION .................................................................................................................... 48 APPENDIX .......................................................................................................................... 49 Firewall rules .................................................................................................................... 49 REFERENCES ..................................................................................................................... 50 Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 3 OVERVIEW OF IDS Intrusion detection systems have been studied for over 25 years. Still, they have limitations but have been very useful in detecting attacks. Basically, an IDS is concerned with the detection of hostile actions towards a computer system or network [2]. There are two main techniques to detect intruders: An integrated approach that combines all type of products into a centrally Managed intrusion detection improves network resistance to intrusions and provides greater flexibility. The integrated approach will support an integrated event database and reporting to provide a more flawless approach to network and security management. Anomaly detection (behavior based): based on the normal behavior of the users of the network Signature detection: based on attack patterns registered inside the packets Signature Based IDS Almost all IDS are signature based, also known as knowledge based. Signature based IDS monitor network traffic and analyzes this traffic against specific predefined attacks. When an attack is detected an alarm is generated. This means that any traffic that doesn’t specifically match a signature is considered safe. Signature based IDS obviously require that the signature base be updated regularly to detect new exploits. If legitimate network traffic triggers an alarm this is called a false positive. The amount of false positives generated by signature based IDS can be significantly less than behavior based IDS. Distributed IDS Distributed IDSs collect data from multiple hosts and possibly the network that connects the hosts, aiming at detecting attacks involving multiple hosts. That’s why it is sometimes necessary to perform intrusion detection in large-scale distributed systems in order to ensure the security of all the components involved. In a distributed system, it is also difficult and sometimes impossible to decide whether some events in one place correspond to the attacks without the information from other places [24]. Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 4 On the other hand, the intrusion detection can be performed in two different places: Host based: looks for intruders that may have break into a single computer Network based -NIDS-: analyze the whole network by catching the packets Host-based system With the host-based system, the intrusion detection software resides on a server and monitors the server logs for unauthorized access attempts and abnormal behavior patterns. The security administrator authors the host-based rules that trigger the analysis of the audit and event logs. The host-based system can then evaluate those actions such as user or login activity or user account and application activity. The host-based systems analyze audit and event logs to look for abnormal patterns of local or remote users that may indicate unauthorized attempts to enter the system. For example, some host-based system may issue an alert if a sales clerk attempts to gain access to payroll data. Host-based IDS may also perform statistical analysis on information looking for recognizing the normal behavior. With host-based systems if a host is put on the network without the IDS agent, the host is unprotected. If the host has anyone with admin privileges, the IDS agent will be disabled if appears to get in the way production software. Network-based system The network-based type of IDS resides as an agent on LAN servers in the form of a sensor. A network IDS (NIDS) monitors all traffic on the network segment that it is on. It Filters and analyzes network packets in real time and compares them against a database of known as attack signatures or patterns. The attack signatures are known methods that intruders have employed in the past to penetrate a network. Typically four techniques are used to recognize attack signatures: Pattern or byte-code matching, Threshold crossing, Correlation of lesser events, Statistical anomaly detection. If the packet contents match an attack signature, the IDS takes appropriate steps as enabled by the network security administrator. These steps can take the form of a wide range of responses. They can Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 5 include notifications through Simple Network Management Protocol (SNMP) traps or issuance of alerts to an administrator’s pager, e-mail or phone. Responses can also take of the creation of a log or the recording of a network session; reconfiguration of the firewall to block the source IP of the offending packets, or the execution of a specific program. This signature type of analysis (as opposed to the statistical analysis approach discussed below) has the advantage of producing a low rate of false positive alarms, but is limited by the difficulty recognizing new types of attacks not in its repertoire of attack signatures. Therefore, these type of systems must be updated to remain current. Other can analyze requests for sensitive information or repeated attempts to circumvent security features and take appropriate action if the activities fall outside of predefined thresholds. However, this type of analysis can pose problems and raise the number of false alarms because defining thresholds for a wide range of activities can be difficult and time consuming. A Network-based IDS can work IDS can work with encrypted networks generate so much data it can be very expensive to analyze all the data. Strengths and Weaknesses of Host-Based and Network-Based IDS Host-Based Systems Strengths Monitor both incoming and outgoing traffic on a specific host Systems. Not impacted by network encryption because the files have been unencrypted before entering the log file. This in contrast to network-based systems, which encounter encrypted payloads. Encrypted network files are unencrypted for entry into the log. Provides better application layer protection than a networkbased IDS because it can monitor failed login and application execution attempts. Function well in network-based encrypted Behavior Intrusion Detection: Enhanced Network-Based Systems Operates in real time and employs unobtrusive Passive monitoring techniques. Minimal system resource usage. Typically platform independent because it resides on the network; most are relatively easy to deploy. Because it reads packet headers, Hakan Evecek -- Rodolfo Ortiz Magdaleno 6 environments because by the time the host-based system sees incoming network traffic it has been decrypted. Functions well in switched environments because they can be located on as many hosts as required. Weaknesses Requires up-to-data and installed attack signatures, which can be expensive to update and distribute. Doesnot operates in real time. Only protects a specific computer system. Can put stress on local resources, such as disk storage and memory which a host-based IDS does not, it detection attacks that host-based systems do not. Detect problems before they reach the targeted system. Requires up-to-date and installed attack signatures, which can be pay for upate. Has a tendency to false positive alerts about attacks when using statistical analysis techniques. Many are not integrated into enterprise network management systems, requiring two monitoring stations. It may not be able to with certainly that an attack was successful, unless it has information on the system being attacked. Provides no protection for the network traffic. which means it dose not read the packet headers that the network-based IDS monitors. Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 7 OVERVIEW OF BEHAVIOR BASED IDS Behavior Based Intrusion Detection Systems (BBIDS) can be described as an alarm for strange system behavior [1]. It is based on the idea of an IDS, which uses a set of rules to test network traffic, but it goes further. It operates from a baseline of normal activity [1]. This baseline is obtained from statistics on network behavior, in other words, a ‘profile’ of the network is created. The advantages of behavior based IDS are [4]: They don’t need to know the details of an attack, only the general characteristics They are automatically updated Doesn’t need to know the vulnerabilities of the network And the disadvantages are: May false positives are generated during the sensor training The training must be extensive so that the baseline is accurate In fact, anomaly detection techniques can be divided into[7]: Protocol anomaly: refers to protocol format and protocol behavior (example, unusual TCP usage) Application payload anomaly: there must be a matching between the payload and the application protocol used (example, shellcode in http payload) Statistical anomaly: it’s important to have different measures of the traffic to create a baseline (example, intensity of the monitored traffic) Some examples of anomalies to be detected can be: Traffic to unused ports Set of activities not usually done by the user in a network Non standard service assigned to one standard port (port 80 set for peer sharing) Too much UDP/TCP traffic More bytes coming to a HTTP server than outgoing bytes There is a comprehensive list of violations in [9]. Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 8 Besides, The profile created needs to be robust, sensitive, adaptive and self-learning [7]. The high false alarm rate is the primary drawback of behavior-based techniques because the entire scope of the behavior of an information system may not be covered during the learning phase. Also, behavior can change over time, introducing the need for periodic online retraining of the behavior profile, resulting either in unavailability of the intrusion detection system or in additional false alarms. The information system can undergo attacks at the same time the intrusion detection system is learning the behavior. As a result, the behavior profile contains intrusive behavior, which is not detected as anomalous [23]. When the system administrator activates behavior-based IDS for the first time, it will log network bandwidth usage, processor and memory activity, disk usage, and other system activity over a certain period to create a baseline. After the learning period, activity that doesn’t match the statistics/abnormal system performance, the baselines, will result in an alert. The main advantage of this type of IDS is that it dynamically adapts to new vulnerabilities. Because system behavior can fluctuate for normal reasons, it usually produces a high number of false alarms [28]. The aim for this project is to decrease the number of false alarms by introducing time intervals and get the IDS system create the alarms according to these intervals. Especially with the IDS like SNORT which is open source, the code can be added to analyze the output of the requests. Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 9 Figure Classification of intrusion detection systems [2]. Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 10 SNORT – OPEN SOURCE IDS Snort has evolved from a simple network management tool to a world class enterprise distributed intrusion detection system. Snort can be configured to run in three modes: Sniffer mode, which simply reads the packets off of the network and displays them for you in a continuous stream on the console (screen). Packet Logger mode, which logs the packets to disk. Network Intrusion Detection System (NIDS) mode, the most complex and configurable configuration, which allows Snort to analyze network traffic for matches against a user-defined rule set and performs several actions based upon what it sees. Inline Mode, which obtains packets from iptables instead of from libpcap and then causes iptables to drop or pass packets based on Snort rules that use inline-specific rule types [27]. In sniffer mode, Snort functions by capturing traffic intended for other hosts on the same network. Sniffers take advantage of the shared nature of Ethernet Networks [25]. Ethernet networks are designed to utilize shared communication channels to reduce cost. Because computers share the same network infrastructure, it is possible for one computer to receive traffic that is intended for another. When snort is in sniffer mode, it displays the contents of every packet traversing the wire directly to the monitor. In packet logger mode, Snort grabs packets in a similar sniffing fashion, but logs the gathered data instead of printing it to your screen. Packets can be logged in ASCII text form or in binary tcpdump format. Tcpdump format is best suited for high bandwidth networks where performance could present an issue. NIDS mode is similar to the sniffer mode. It snatches up every packet it encounters, but the key difference is what NIDS mode does with data. The SNORT inspects each packet and determines whether it is benign or malicious in nature. Snort then sends alerts when it finds suspicious looking traffic. Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 11 The basic layout of SNORT is [4]: INTERNET PACKET DECODER PREPROCESSORS DETECTION ENGINE DROP THE PACKET LOGGING AND ALERTING SYSTEM ALERT LOG FILE OUTPUT MODULES Packet decoder It gathers the packet from distinct network interfaces. Preprocessor There can be several preprocessors, and they arrange or modify the packets in order to be sent to the detection engine [3]. Snort has an extensible plug-in architecture that ensures that Snort will remain a proficient intrusion detection system. Snort has a class of plug-ins, known as preprocessors that interact with data before the detection engine processes it. Preprocessors can be broken down into three functional groups: Data Normalization, Protocol Analysis, and NonSignature Matching Detection [25]. Data Normalization: New methods of attacks and IDS are constantly evolving that Snort’s detection engine either does not detect or does not detect efficiently. Preprocessors are added to the Snort architecture to massage or normalize data so that the detection engine can properly interpret them. Protocol Analysis: The detection engine has a short list of protocols that it can interpret. Others, including some protocols that are heavily used over public networks, it cannot be interpret. Abstract Syntax Notation number One (ASN1) protocol can detect protocol abuses like the ones Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 12 with SNMP, LDAP, SSL etc. The capability of detecting misuse of the ASN.1 protocol is necessary to monitor. Non-Signature-Matching Detection: Some types of malicious traffic do not have signatures. This class of preprocessor uses methods other that signature matching to catch suspicious traffic. Harmless ICMP traffic is used to find out the hosts on the network. Detection engine This component uses SNORT rules to match the packets. Alerting Intrusion detection is not an automated process. It requires a human to receive the alerts and react to them in a timely fashion. As expected, getting real time alerts out of Snort [25]. An IDS needs to be able to categorize and prioritize alerts in an organized fashion. Alerting can be done in three ways [25]: No prioritization Hard-Coded prioritization Customizable prioritization The two primary means for alerting are real-time alerting with syslog and swatch and the Analysis Console for Intrusion Databases (ACID). ACID is a web application that reads intrusion data stored in a database and presents it in a browser. In the test results MYSQL is used as a database tool to store the data. ACID presents Snort data in a human friendly format and includes functionality to do complex searches. Complex searches can be created with over 30 different criteria to pinpoint events occurring in a vast sea of intrusion data. Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 13 OVERVIEW OF THE PROJECT Nowadays BBIDS can be attacked and redefined by intruders, it means intruders can train the BBIDS so that it won’t detect an attack. The second problem is that BBIDS generate many false positives during the set up and any time there is a change in the network environment. It is up to the administrator to discard the alerts that are not related to intrusion. It would mean constant training [1] to update the network baseline. The project will consider how to enhance and extend a BBIDS. There are several commercial and open source BIDS (Stealth Watch, RealSecure, Cisco NetRanger, McAfee IntruShield, Shadow[8], SNORT), we will use SNORT, which is a open source Intrusion Detection System. Based on SNORT, several improvements will be proposed. Three protocols will be analyzed: DNS, ICMP and HTTP vs HTTPS. From here, the timing that each protocol generates will be considered: the time it takes to receive an answer must be between a valid range, which we will figure out. The first step is collecting data, and then developing a model to fit the data in. A baseline of what is normal behavior and what is not will be established. For example, in HTTP, there is a three way handshake, which is completed in a certain amount of time. Most of the BBIDS don’t consider this (so SNORT); therefore, if traffic is not close to this timing, it should be put under suspicion. It may be a delay of valid traffic, or worst, it may be someone responding to a computer instead of the original one. A subdomain will be created, with a DNS/HTTP server. The tools to analyze the packets are SNORT and ETHEREAL. These packages show the timing and the content of the packet. Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 14 The first test will consist in sending first ICMP requests and measuring the time it takes to get the ICMP reply, specifically the time B+C (fc4) Firewall Intra1 (XP) DNS Server IDS Inner (FC4) A B ICMP Reply C ICMP Request D The second test will use DNS packets, which are UDP based. The flow will be the following, measuring the time B+C. (fc4) Firewall Intra1 (XP) DNS Server IDS Inner (FC 4) B DNS Reply Behavior Intrusion Detection: Enhanced C A DNS Request D Hakan Evecek -- Rodolfo Ortiz Magdaleno 15 For the HTTP requests, the flow is different. The timing to measure is B+C, D+E and from A to G. B+C is the interval between receiving the SYN packet and receiving the SYN ACK packet. D+E is for measuring the interval between SYN ACK packet and ACK packet. A to G measures the time between the SYN packet and the GET packet. Firewall Intra1 (XP) Web IDS Inner (FC 4) Server A B SYN ACK C SYN D ACK F Behavior Intrusion Detection: Enhanced E G GET Hakan Evecek -- Rodolfo Ortiz Magdaleno 16 HTTPS is similar to HTTP but more steps need to be added. The version is SSL v3. Firewall Intra1 (XP) We b Server IDS Inner (fc4) A B C SYN ACK D ACK F E CLIENT HELLO G CERTIFICATE CLIENT KEY EXCHANGE CERTIFICATE VERIFY CHANGE CIPHER SPEC FINISHED APPLICATION DATA SYN H I J K L N M SERVER HELLO CERTIFICATE SERVER KEY EXCHANGE CERTIFICATE REQUEST SERVER HELLO DONE APPLICATION DATA The timing to be analyzed is: A to M Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 17 PROTOCOLS Starting at top in the figure 1.1, the high-level application layer activity might present a TCP/IP application such as Telnet. Application Transport Internet TCP&UDP IP ICMP Network Interface Figure 1.1 TCP/IP Internet Model [31]. In the Transport layer TCP and UDP protocols provide the end-to end communication between hosts. Beneath that is the Internet layer, which is responsible for getting the datagram from source to destination. The last one is the Network interface layer, which transmits the datagram over the network. In the figure it is shown that ICMP is in the same network layer as IP [31]. ICMP is encapsulated in the IP datagram after the IP header, however it is still considered to be in the same layer as the IP. Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 18 DNS Basic Background DNS is used to retrieve information regarding the domain names. It is mostly used to translate a web address into a numeric IP address. It is based on the UDP protocol when the service is between client and server, and TCP when the transmission is between servers. Basically there is a response and a request, and the query can be recursive or iterative. If the DNS name server doesn’t know the answer to the query, it has to contact a root server. The port used in DNS is 53. Once the response is received, it lasts in memory for a period of time and then is deleted. The packet contains the following fields: Bits 0-15 Bits 16-31 Identification flags number of questions number of answer RRs number of authority RRs number of additional RRs questions answers (RRs) authority (RRs) additional information The resource records can be: Start of Authority (SOA) record Name Server (NS) record Address (A) record Pointer (PTR) record Canonical (CNAME) How DNS works The first concept is zone. It is a group of matches between names and IP addresses. Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 19 The following images where capture with Ethereal when sending a DNS request. DNS request DNS response Why we chose DNS This protocol is critical in Internet, since we don’t type the numerical ip address of a web page, but the name. There have been many attempts to exploit its vulnerabilities, and IDS offers the capability to protect both the clients and servers of intruder’s packets. Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 20 And also what would happen if we type www.google.com and get a personal home page? That is why this protocol is important. Vulnerabilities Cache poisoning consists in responding to DNS server requests on behalf of a real DNS server. This happens when a DNS server doesn’t know an IP address, and has to look for it. It sends a request to other DNS servers but receives an answer from someone pretending to be a DNS server. On the other hand, there can be a man-in-the-middleattack, and an attacker assumes the position of a DNS server. Or the attacker can guess the identifier of the DNS request packet [15] Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 21 ICMP Basic Background The network connecting devices are called Gateways. These gateways communicate between themselves for control purposes via a Gateway to Gateway Protocol (GGP. Occasionally a gateway or destination host will communicate with a source host, for example, to report an error in datagram processing. For such purposes this protocol, the Internet Control Message Protocol (ICMP), is used. ICMP, uses the basic support of IP as if it were a higher level protocol, however, ICMP is actually an integral part of IP, and must be implemented by every IP module [25]. ICMP differs from TCP and UDP in several ways [31]. ICMP has no port numbers like those founding the transport layer protocols. ICMP has to have a differentiation in services as an ICMP message type and code. How it works ICMP messages are sent using the basic IP header. The first octet of the data portion of the datagram is an ICMP type field; the value of this field determines the format of the remaining data. Any field labeled "unused" is reserved for later extensions and must be zero when sent, but receivers should not use these fields (except to include them in the checksum). There is also no client-server concept. When ICMP error messages are delivered, the receiving host might respond internally but might not communicate anything back to the informer like in the TCP communication. There is also no delivery of message guaranteed. ICMP supports broadcast messaging. IP-speaking hosts use ICMP protocol. In other words, ICMP is sued for simple replies and requests in between the hosts. 0 1 2 3 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Type | Code | Checksum | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | unused | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Internet Header + 64 bits of Original Data Datagram | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 22 Why we chose ICMP ICMP is one of the basic and most commonly used protocols especially in the router and gateways. So researching the response times on ICMP will be a valuable data for the SNORT time related behavior based IDS. ICMP is used as a mechanism by routers to inform a sending host of some kind of problem. A router might deliver an ICMP admin prohibited message to a sending host. This means that the sending host attempted to send some kind of traffic that was forbidden. As it can be seen in this scenario, ICMP is one of the highly used protocols in the routers or gateways that attackers might try to access. Vulnerabilities The following are high-level network threats: Information gathering Sniffing Spoofing Session hijacking Denial of service Common information-gathering attacks include: Using Tracert to detect network topology, Using Telnet to open ports for banner grabbing, Using port scans to detect open ports, Using broadcast requests to enumerate hosts on a subnet. ICMP is one of the main protocols used in these tools for attackers to sniff in [30]. Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 23 HTTP Basic Background HTTP is the protocol used to send information in the world wide web. It uses URI and URL for reference. Also, there is a client and a server, which usually uses port 80. HTTP 1.0 has 47 different headers. How HTTP works In order to communicate, there must be a three way handshake between client and server. Then the first HTTP request looks like: GET / HTTP/1.1 Host: www.uccs.edu Accept-Encoding: gzip User-Agent: Firefox/1.0 Then the server responds: HTTP/1.0 200 OK A transmission between client and server captured in Ethereal: Why we chose HTTP After finding out the IP address through the DNS server, the next step is retrieving the web page. Can you imagine if there is a man in the middle attack and we are actually receiving forged packets? We will be receiving fake information, and at the same time we will not notice the attack. Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 24 Vulnerabilities An attacker could respond in behalf of the real web server by acting as a man in the middle. That intruder will see all the information that is sent and received, and may try to interfere in the conversation. Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 25 HTTPS Basic Background HTTPS is a URI scheme equivalent to the http scheme, originally intended to be used with the HTTP protocol, but with added encryption layer. The URI structure is the same, except that URIs begins with "https:" rather than "http:". Instead of using plain text socket communication, the session data is encrypted using either a version of the SSL (Secure Socket Layer) protocol or the TLS (Transport Layer Security) protocol, thus ensuring reasonable protection from eavesdroppers, and man in the middle attacks. The default TCP port of https: is 443 [29]. How HTTPS works To prepare a web-server for accepting https connections the administrator must create a public key certificate for the web-server. These certificates can be created for LINUX based servers with OpenSSL tools (SSL-CA) or in SuSE with the 'gensslcert' command. This certificate must be signed by a certificate authority that you have to pay that it certifies that you are who you claim to be. If you do not want to pay you use a Self-signed certificate and the browser of your client displays (at least once) a security alert that it cannot verify the server's certificate [29]. Another use of Https is client authentication. This applies if someone wants to restrict access to a web-server to only authorized people. For this you have to create user certificates (also public key certificate) that can be loaded into a client browser (e.g. Firefox) to identify the client as authorized to access the server. Usually the webmaster of an organization will create a user certificate (also with sslca) that contains the name and email of an authorized user. On every reconnect the web-server checks the certificate and the user can access the server optionally even without a password [29]. The level of protection depends on the correctness of the implementation by the web browser and the server software and the actual cryptographic algorithms supported. A common misconception among credit card users on the Web is that https: "fully" protects their transaction when submitting a card Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 26 purchase, when in reality card information is only encrypted between their browser and the receiving Web server. Merchant sites are supposed to immediately forward incoming transactions to a financial gateway and retain only a transaction number, but receiving web servers often save card numbers in a database. It is the server and database that is usually attacked and compromised by unauthorized users [29]. Why we chose HTTPS HTTP and HTTPS are one of the most common used protocols. Because of the nature of the internet, it is also most commonly attacked protocols. Measuring the time in these protocols and making this part of the snort time behavior based measurement will cover some of the attacks. Vulnerabilities An attacker could respond in behalf of the real web server by acting as a man in the middle like the HTTP request. That intruder will see all the information that is sent and received, and may try to interfere in the conversation although it will be a secured connection. There is a chance that secure connections can be broken in an attacker can behave as if they are not the intruder. Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 27 TESTBED Our test bed looks like the following: (FC4 ) DNS Server Internet Intranet (10.0.0.0/24) Web Server Intra2(win2003) Firewall Firewall HP5000 SW DLink SW2 DLink SW1 IDS Outer (FC4) DMZ (192.168.0.0/24) IDS Sensor IDS Inner (FC4) IDS Sensor Database Intra1 (XP) The packets for the four protocols will flow as indicated in the image. The inner firewall will collect the data and the timing will be measured. We used five computers with the following characteristics: Pentium III 996 MHz 512 RAM Regarding the operating system, 3 of them were running Fedora Core 4 (Linux 2.6.11-1.1369), a fourth one with Windows XP SP2 and a fifth one running Windows 2003 Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 28 It includes a graphical interface to analyze SNORT packets. Analysis Console for Intrusion Databases (ACID) Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 29 Tools used in the Testbed We also created a set of rules to enhance the security, for example: DMS servers are not allowed to start a conversation Packets that were not requested must not pass through the firewall The firewall should receive the correct source/destination address in each network interface based on the DMZ or LAN IP range All the rules are available in the appendix A The SNORT centralized database in positioned in the inner firewall computer. The firewall that controls the outer part of the network sends all the alert logs to this database. At the same time, we installed ACID. This PHP based program allows us to visualize the information through statistics and graphs. The information consists in alerts generated by both SNORT sensors. The packets were sent using the following programs: Ethereal HttpTrafficGen Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 30 DNS Query Network Traffic Emulator And collected/analyzed using Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 31 RESULTS OF THE PROJECT ICMP First we must say the units are indicated in seconds. Let’s analyze the results by protocol starting with ICMP. The following graph shows that the timing between the REQUEST-REPLY packet converge on an interval, whether the firewall is enabled or not. The blue points represent ICMP timing when the firewall is enabled, and pink points are used when the firewall is disabled. Time (sec) 0.000235 0.000215 0.000195 0.000175 0.000155 0.000135 0.000115 0.000095 0.000075 Packet Sequence Number Before continuing, it is important to remember that in a normal distribution, approximately 99.7% of the population will be in the interval defined by: 3 It works well for the upper bound (using the + sign), but the lower is defined by (using only the - sign): 1 Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 32 Although this is not a normal distribution, neither for ICMP, DNS and HTTP and HTTPs, we still obtain really good results by applying the above formulas. The following table summarizes the data. ICMP Firewall enabled Mean 0.000119 Standard Deviation 0.000023 % inside the above interval 98.64% Firewall disabled 0.000106 0.000011 96.67% By using the interval defined by the formula, we can get the packets that lie outside that interval. Those packets have a timing that is too high or too low. The circles in the graph define the data outside this interval. Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 33 DNS Let’s go on to DNS. Using the same formula, the one that defines approximately 95.5 percent of the packets, we get the following table. DNS Firewall enabled Mean 0.000352 Standard Deviation 0.000038 % inside the above interval 98.64% Firewall disabled 0.000345 0.000023 100.00% The graph is below. Blue is for the firewall and pink is when the firewall is disabled. The circles show approximately which packets lie outside the interval. Time (sec) 0.000735 0.000685 0.000635 0.000585 0.000535 0.000485 0.000435 0.000385 0.000335 0.000285 Behavior Intrusion Detection: Enhanced Packet Sequence Number Hakan Evecek -- Rodolfo Ortiz Magdaleno 34 HTTP vs HTTPS In these two protocols several packet sequences can be measured. The data is shown for the timing between the SYN packet and the GET packet. We also gathered data for the rest of the packet sequence. Using the same interval, the table is: Mean Standard Deviation % inside the above interval Firewall enabled Firewall disabled HTTP HTTPS HTTP HTTPS 0.000582 0.004463 0.000561 0.004320 0.000064 0.001574 0.000033 0.000708 98.48% 98.99% 98.99% 99.49% The information is shown in two graphs. Blue represents HTTP and pink HTTPs. The first graph is based on data using the firewall and the second represents data with a disabled firewall. Time (sec) 0.020000 0.015000 0.010000 0.005000 0.000000 Behavior Intrusion Detection: Enhanced Packet Sequence Number Hakan Evecek -- Rodolfo Ortiz Magdaleno 35 Time (sec) 0.009000 0.008000 0.007000 0.006000 0.005000 0.004000 0.003000 0.002000 0.001000 0.000000 Packet Sequence Number After this, the packets outside the interval need to be classified and put into intervals. That way, we can assign labels to prioritize further analysis of the packets by putting them in different queues. Those queues can be used by SNORT or by the device that forwards the packets. This technique, marking packets and using queues, was used by Angela Cearns [22], who assigned the packets different bandwidth based on its label. The label was defined for each packet based on its protocol. She created two queues, a high priority queue and a low priority queue. Now, how do we assign the packets outside the confidence interval to a queue? First, we must define the number of queues/labels. Right now we are using 3 times the standard deviation for the upper bound, and 1 time the standard deviation for the lower bound For the lower bound, the intervals will be defined between 1 and 2 times the standard deviation. This happens because we have a limit, which is above 0 seconds (the timing will never be 0 seconds). For example, if we are to define 4 intervals for the lower bound, there should be 3 intervals between 1 and 2. The last interval applies to 2 times de standard deviation and up. Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 36 For the upper bound, we can define any number of intervals. Each interval is defined by one time the standard deviation. It means that, starting at 3, we can go to 4, 5, 6, and so on. Each distinct number represents the limit of a interval. If we define 4 intervals, the result will be: Lower bound 1-1.3 1.3-1.6 1.6-2 >2 Behavior Intrusion Detection: Enhanced Upper bound 3-4 4-5 5-6 6-7 Hakan Evecek -- Rodolfo Ortiz Magdaleno 37 PROPOSED APPROACH Using the standard deviation, the intervals will be set. The upper bound starts with 3 and the lower bound starts with 1 time the standard deviation. This difference is because most packets that are far from the mean lie in the upper bound, not in the lower one. After creating the different intervals, they can be assigned to distinct queues. The next step is assign the priorities and label each packet that lies outside the confidence interval. The following graphs explain this idea, they are based on the data obtained when the firewall is enabled. Basically, the confidence interval is defined, and for reference, we define the boundaries for the intervals. Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 38 ICMP Time (sec) 0.000350 0.000300 6 times standard deviation, higher priority 0.000250 0.000200 3 times, lower priority 0.000150 Confidence Interval 0.000100 1 time, lower priority 2 times, higher priority 0.000050 0.000000 Packet Sequence Number Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 39 DNS Time (sec) 0.000700 0.000650 0.000600 6 times the standard deviation, higher priority 0.000550 0.000500 3 times, lower priority 0.000450 Confidence Interval 0.000400 0.000350 1 time, lower priority 0.000300 2 times, higher priority 0.000250 Packet Sequence Number Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 40 HTTP Time (sec) 0.001400 0.001300 0.001200 0.001100 6 times the standard deviation, higher priority 0.001000 0.000900 0.000800 3 times, lower priority 0.000700 Confidence Interval 1 time, lower priority 0.000600 0.000500 0.000400 Behavior Intrusion Detection: Enhanced 2 times, higher priority Packet Sequence Number Hakan Evecek -- Rodolfo Ortiz Magdaleno 41 HTTPS Time (sec) 0.025000 0.020000 0.015000 6 times the standard deviation, higher priority 0.010000 3 times, lower priority Confidence Interval 0.005000 1 time, lower priority 2 times, higher priority 0.000000 Packet Sequence Number Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 42 SUSPICIOUS PACKETS So far, we have defined the suspicious packets. Then we give them a priority by assigning a label. the next step is: how do we know the packet belongs to an attack/intruder? This is a difficult step, where we need to define the behavior (a generic one) for each kind of attack. In [20] the behavior of a worm is defined. The topic is behavioral signatures. Behavioral signatures A packet that is out of the obtained range is not necessarily from an intruder. We need to develop an integral approach to analyze the data. The next topic, behavioral signatures, help to create a more complete approach. Behavioral signatures are valuable because they describe worms without needing to know the specifics of a worm [20]. Two type of signatures may be considered: base signatures and inductive signatures. Base signatures are implemented in a single node based on the traffic that goes in and out that node, while inductive signatures consider a behavior that is captured by several nodes. Based signatures A worm propagates by sending copies of itself from an already infected computer. This can be represented by using two packets, one that infects the local computer and a second one that is sent from the local infected computer attempting to infect other hosts. If the packets were represented in words, they would look like: Packet 1 < A, ?, C, D > Behavior Intrusion Detection: Enhanced -----> Packet 2 < C, ?, E, D > Hakan Evecek -- Rodolfo Ortiz Magdaleno 43 It means already infected computer A sends a packet from an unknown port to computer C and port D. Then computer C gets infected and attempts to send a packet with unknown port number to another computer’s port number D. A:? -> C:D Intra1 (XP) C:? -> E:D Intra2 (XP) If we use this approach to identify a worm, then we need to look for this pattern of information –behavioral signature- in the database. Inductive signatures The idea behind inductive signatures is a descendant relation; it means that when the worm spreads the number of descendant infected host increases. Then, when having a descendant relation, we need to find a branching factor that indicates that a descendant network is growing exponentially. The branching factor higher than 1 indicates this. The branching factor is one way to find that a worm is spreading, other ways are described in [20]. Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 44 7 3 1 Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 45 FUTURE WORK What to do with the packet? How to know if it is from an intruder? It is possible to identify a packet as suspicious, and following the proposed approach, a simple worm can be identified. What other approaches can be followed? What data do we need to store? For the simple case of a worm attack, we need to store IP addresses and ports. What about more complicated worm attacks? Other attacks? How to collect the data towards an automated process? How can SNORT create the intervals automatically? Implement the approach in SNORT’s source code It is possible to modify SNORT so that it can implement the ideas devised in this document. It would be interesting to show how the new module will integrate with SNORT. Analyzing other protocols ICMP, HTTP, HTTP and DNS are only a few protocols that are used in a network. But there are other, like email protocols (SMTP, POP) or ARP. They are also important and need to be secured and overseen. Analyzing other scenarios like an internet server instead of a local server We are very specific on the scenario/testbed we are configuring. But there may be other situations to consider, like the timing from outside the LAN. Probably a worker is connected to the local HTTP server from his house through a VPN. The following image shows this scenario. On the other hand, machines inside the LAN may be trying to access an Internet Web Server, and we want to make sure there is no intruder between client and server. Moreover, the DNS Server may not know have a Resource Record asked by a local machine; so it has to send a Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 46 request to another DNS server. The packets can be spoofed as the DNS server has vulnerabilities, but the Anomaly IDS offers a way to resolve this issue. Analyze wireless communication Since wireless networks are also common, it would be interesting to show how the protocols behave in these networks. The transmission is not through a cable, but the air, so the timing will be different. DNSSecure It provides more security, since it uses encrypted signatures. In fact, the DNS server signs its responses so that the client can validate its authenticity. Every zone has a private key owned by the DNS server. After this, each client needs to decrypt the response using the public key, and recalculates the hash. It would be useful to know the timing of this protocol, although the encryption enhances the security by itself. Behavioral signatures They are defined for worms, but what about other attacks? Is it possible to identify a behavioral signature for those attacks? Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 47 CONCLUSION IDS are an integral part to secure a network. The other components are applying patches, installing a firewall, etc. New techniques and types of attacks can not be prevented by usual tools (antivirus, firewall...), for example, a worm that attack an unknown vulnerability in a commercial database server: but when using a behavior IDS the activity of the network will change and an alarm will be raised. Enhancing Anomaly IDS is important because one goal is to decrease the number of false positives. At the same time, we are looking at the timing variable, which is important but not the only one by far. To implement an integral approach, before raising an alarm Anomaly IDS need to analyze other variables, like performance. Moreover, the proposed intervals work really good in the protocols analyzed. They are not the only protocols (though they are important), so more protocols can be studied and the intervals may or may not apply correctly. It would be interesting to try some attacks. This would enable us to define more accurately the intervals. That means that we know the approximate timing of an attack, and the intervals can fit to that data with more precision. But for now the intervals proposed define a baseline that can be used to prioritize packet analysis and further processing actions. Finally, after looking at the HTTP and HTTPS graphs, we notice they are not completely similar. At the end of HTTPS, there is an increase in the timing (y value). This may be caused by the different amount of information exchanged by each protocol. Therefore, time varies more in HTTPS than HTTP. To conclude, this project was really helpful to find out the timing for different protocols, specially when looking at the graphs. This gives us a better insight to what is happening, and once it is understood, it will be easier to differentiate an attack from a false positive. Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 48 APPENDIX Firewall rules The rules are contained in the attached documents named outfirewall.sh for the outside firewall and infirewall.sh for the inside firewall. Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 49 REFERENCES Testbed images based on Dr. Chow presentations 2005 [1] http://online.securityfocus.com/infocus/1600 [2] http://www.windowsecurity.com/articles/IDS-Part2-Classificationmethods-techniques.html [3] http://cs.uccs.edu/~chow/pub/ids/NISTsp800-31.pdf [4] Intrusion detection with SNORT. Rafeeq Ur Rehman. Prentice Hall 2003 [5] http://www.sans.org/resources/idfaq/behavior_based.php [6]http://www.cs.cmu.edu/afs/cs.cmu.edu/user/maxion/www/pubs/Tan KillourhyMaxion02.pdf [7]http://www.mcafee.com/us/local_content/white_papers/wp_ddt_ano maly.pdf [8] http://www.nswc.navy.mil/ISSEC/CID/ [9]http://luca.ntop.org/ADS.pdf [10] Defending yourself: The role of Intrusion Detection Systems. Jon McHugh, Alan Christie and Julia Allen [11] Network Intrusion Detection. Stephen Northcutt, Judy Novak. New Riders 2003 [12] http://www.scit.wlv.ac.uk/~jphb/comms/dns.html [13]http://eeunix.ee.usm.maine.edu/guides/dns/resource.html [14]http://64.233.167.104/search?q=cache:jgAAT1MhxIEJ:www.auggy. mlnet.com/ibm/3376c45.html+%22domain+name+resolution%22+hea der+port+53&hl=en [15] http://www.sans.org/rr/whitepapers/dns/1054.php [16] http://www.jmarshall.com/easy/http/ [17] http://www.watchfire.com/resources/HTTP-Request-Smuggling.pdf [18] http://www.rhyshaden.com/http.htm [19]http://www.itconnection.ru/support/pdf_repository/introduction_to_ ssl_by_peter_markowsky.pdf [20] A behavioral approach to worm detection. Ellis, Aiken, Atwood, Tenaglia [21] http://www.snort.org/docs/snort-rh7-mysql-ACID-1-5.pdf [22] Design of an Autonomous Anti-DdoS Network (A2D2). Thesis, 2002 [23] Michael Rowton, Introduction to Network Security - Intrusion Detection, http://www.securitydocs.com/library/3009, Dec, 2005 [24] Intrusion Detection in Distributed Systems, Peng Ning, Sushil Jajodia, X. Sean Wang, 2004. [25] Intrusion Detection with Snort, Jack Koziol, 2003. [26] RFC 792 - Internet Control Message Protocol, J. Postel, Sep 1981 http://www.faqs.org/rfcs/rfc792.html [27] Snort documentation, http://www.snort.org/docs Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 50 [28] TechExams.net http://www.techexams.net/technotes/securityplus/ids.shtml#svb [29] http://en.wikipedia.org/wiki/HTTP#Secure_HTTP [30] Microsoft MSDN library Securing Your Network [31] Network Intrusion Detection An Analyst Handbook , Stephen Northcutt, Judy Novak, 2000 Behavior Intrusion Detection: Enhanced Hakan Evecek -- Rodolfo Ortiz Magdaleno 51