l4-2 - Heyook Lab
... • Each router advertises its distance vector every 30 seconds (or whenever its routing table changes) to all of its neighbors • RIP always uses 1 as link metric • Maximum hop count is 15, with “16” equal to “” • Routes are timeout (set to 16) after 3 minutes if they are not ...
... • Each router advertises its distance vector every 30 seconds (or whenever its routing table changes) to all of its neighbors • RIP always uses 1 as link metric • Maximum hop count is 15, with “16” equal to “” • Routes are timeout (set to 16) after 3 minutes if they are not ...
PPT
... We need to understand fundamental performance limits for any protocol stack of the ad hoc networks we need. ...
... We need to understand fundamental performance limits for any protocol stack of the ad hoc networks we need. ...
ex2-10-o-can
... • Bandwidth Requirements: • The flooding of link-state packets can adversely affect the available bandwidth on a network. • This should only occur during initial startup of routers, but it can also be an issue on unstable networks. CCNA2-39 ...
... • Bandwidth Requirements: • The flooding of link-state packets can adversely affect the available bandwidth on a network. • This should only occur during initial startup of routers, but it can also be an issue on unstable networks. CCNA2-39 ...
Expl_Rtr_chapter_10_Link_State
... • Bandwidth Requirements: • The flooding of link-state packets can adversely affect the available bandwidth on a network. • This should only occur during initial startup of routers, but it can also be an issue on unstable networks. CCNA2-39 ...
... • Bandwidth Requirements: • The flooding of link-state packets can adversely affect the available bandwidth on a network. • This should only occur during initial startup of routers, but it can also be an issue on unstable networks. CCNA2-39 ...
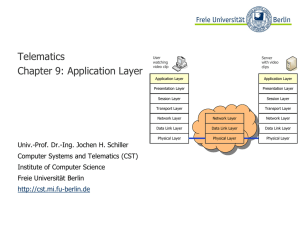
Application Layer - Freie Universität Berlin
... ● File Transfer Protocol (FTP) ● World Wide Web ● HTTP ● HTML ...
... ● File Transfer Protocol (FTP) ● World Wide Web ● HTTP ● HTML ...
VLAN History
... as to which incoming data link layer addresses are assigned to which VLAN segment. Easier to manage than Port-based. ...
... as to which incoming data link layer addresses are assigned to which VLAN segment. Easier to manage than Port-based. ...
Practical use of Ethernet OAM Joerg Ammon, Brocade
... • A variety of Operations, Administration, and Management (OAM) protocols and tools were developed in recent years for MPLS, IP, and Ethernet networks. • These tools provide unparalleled power for an operator to proactively manage networks and customer Service Level Agreements (SLAs). • This session ...
... • A variety of Operations, Administration, and Management (OAM) protocols and tools were developed in recent years for MPLS, IP, and Ethernet networks. • These tools provide unparalleled power for an operator to proactively manage networks and customer Service Level Agreements (SLAs). • This session ...
A Survey on Network Attacks
... on a desktop, server, or in products like Check Point used as a central firewall for all inbound and outbound network traffic. Firewalls are generally configured to allow certain traffic in and out, and everything else is dropped and preferably logged for later review. ...
... on a desktop, server, or in products like Check Point used as a central firewall for all inbound and outbound network traffic. Firewalls are generally configured to allow certain traffic in and out, and everything else is dropped and preferably logged for later review. ...
Multimedia Communications
... chunk arrives after t+q: data arrives too late for playout, data “lost” Tradeoff for q: large q: less packet loss ...
... chunk arrives after t+q: data arrives too late for playout, data “lost” Tradeoff for q: large q: less packet loss ...
IntServ, DiffServ, RSVP
... • Typically slower links at edges • E.g., mail sorting in post office ...
... • Typically slower links at edges • E.g., mail sorting in post office ...
Smoke and Mirrors: Reflecting Files at a Geographically Remote Location Without Loss of Performance.
... destination machine to which data is being sent. Accordingly, our model assumes wide-area networks with high data rates (10 to 40 Gbits) but sporadic packet loss, potentially bursty. The packet loss model used in our experiments is based on actual observations of TeraGrid, a scientific data network ...
... destination machine to which data is being sent. Accordingly, our model assumes wide-area networks with high data rates (10 to 40 Gbits) but sporadic packet loss, potentially bursty. The packet loss model used in our experiments is based on actual observations of TeraGrid, a scientific data network ...
Security in Computer Networks
... A note on the use of these ppt slides: We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. I ...
... A note on the use of these ppt slides: We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. I ...
Computer Networking : Principles, Protocols and Practice Release
... To enable the two hosts to exchange information, they need to be linked together by some kind of physical media. Computer networks have used various types of physical media to exchange information, notably : • electrical cable. Information can be transmitted over different types of electrical cables ...
... To enable the two hosts to exchange information, they need to be linked together by some kind of physical media. Computer networks have used various types of physical media to exchange information, notably : • electrical cable. Information can be transmitted over different types of electrical cables ...
common lower-layer protocols
... networks and indirectly connected devices. The use of physical addresses facilitates communication on a single network segment for devices that are directly connected to each other with a switch. In most cases, these two types of addressing must work together in order for communication to occur. Con ...
... networks and indirectly connected devices. The use of physical addresses facilitates communication on a single network segment for devices that are directly connected to each other with a switch. In most cases, these two types of addressing must work together in order for communication to occur. Con ...
paced invocations - Google Project Hosting
... Integrating SCTP as a pluggable protocol into middleware allows effortless and seamless integration for DRE applications SCTP is available when using ACE, TAO, CIAO and AVStreaming Continue to use other network QoS mechanisms such as DiffServ and IntServ with SCTP Both OpenSS7 and (specially) LKSCTP ...
... Integrating SCTP as a pluggable protocol into middleware allows effortless and seamless integration for DRE applications SCTP is available when using ACE, TAO, CIAO and AVStreaming Continue to use other network QoS mechanisms such as DiffServ and IntServ with SCTP Both OpenSS7 and (specially) LKSCTP ...
Chapter_1_V6.1 - Rose
... 1.5 protocol layers, service models 1.6 networks under attack: security 1.7 history ...
... 1.5 protocol layers, service models 1.6 networks under attack: security 1.7 history ...
WIRELESS SENSOR NETWORKS: SECURITY ISSUES AND
... dollars already invested down the drain if future expansion is needed. Therefore, in order to choose the right wireless technology and determine what is best for future expansion, this introduction will consider both proprietary as well as open standard wireless technologies and will point out why o ...
... dollars already invested down the drain if future expansion is needed. Therefore, in order to choose the right wireless technology and determine what is best for future expansion, this introduction will consider both proprietary as well as open standard wireless technologies and will point out why o ...
dccn-ARP - WordPress.com
... If the IP address of the destination host in the ARP query is infact one of the hosts connected to the router, then, the router itself replies the sender with the physical address of the router itself in a unicast ARP response message. When a packet arrives with the destination host’s IP address and ...
... If the IP address of the destination host in the ARP query is infact one of the hosts connected to the router, then, the router itself replies the sender with the physical address of the router itself in a unicast ARP response message. When a packet arrives with the destination host’s IP address and ...
The Pulse Protocol - Department of Computer Science
... Changes to the metric are only reported locally Routes are continuously adjusted as the metrics change High speed accurate route tracking is essentially an on-demand decompression of the topology ...
... Changes to the metric are only reported locally Routes are continuously adjusted as the metrics change High speed accurate route tracking is essentially an on-demand decompression of the topology ...
Proceedings of the 7th Annual ISC Graduate Research Symposium ISC-GRS 2013
... This scheme was adopted in the overlay structure because it helps us to realize the basic goals for an efficient protocol ...
... This scheme was adopted in the overlay structure because it helps us to realize the basic goals for an efficient protocol ...
P10
... • Bandwidth Requirements: • The flooding of link-state packets can adversely affect the available bandwidth on a network. • This should only occur during initial startup of routers, but it can also be an issue on unstable networks. CCNA2-40 ...
... • Bandwidth Requirements: • The flooding of link-state packets can adversely affect the available bandwidth on a network. • This should only occur during initial startup of routers, but it can also be an issue on unstable networks. CCNA2-40 ...
Internet protocol suite

The Internet protocol suite is the computer networking model and set of communications protocols used on the Internet and similar computer networks. It is commonly known as TCP/IP, because among many protocols, the Transmission Control Protocol (TCP) and the Internet Protocol (IP) is the accepted and most widely used protocol in Internet. Often also called the Internet model, it was originally also known as the DoD model, because the development of the networking model was funded by DARPA, an agency of the United States Department of Defense.TCP/IP provides end-to-end connectivity specifying how data should be packetized, addressed, transmitted, routed and received at the destination. This functionality is organized into four abstraction layers which are used to sort all related protocols according to the scope of networking involved. From lowest to highest, the layers are the link layer, containing communication technologies for a single network segment (link); the internet layer, connecting hosts across independent networks, thus establishing internetworking; the transport layer handling host-to-host communication; and the application layer, which provides process-to-process application data exchange.The TCP/IP model and related protocol models are maintained by the Internet Engineering Task Force (IETF).