ANALYSIS OF RED PACKET LOSS PERFORMANCE IN A SIMULATED IP WAN
... Simulation results show the effects of the RED algorithm on network traffic and equipment performance. It is shown that random packet discarding improves source transmission rate stabilization, as well as node utilization. If the packet dropping probability is set high, the TCP source transmission r ...
... Simulation results show the effects of the RED algorithm on network traffic and equipment performance. It is shown that random packet discarding improves source transmission rate stabilization, as well as node utilization. If the packet dropping probability is set high, the TCP source transmission r ...
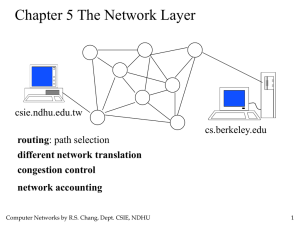
Network Layer
... reason not to put the complexity in the hosts. 2. The subnet is a major international investment that will last for decades, so it should not be cluttered up with features that may become obsolete quickly. 3. Some applications, such as digitized voice and real-time data collection may regard speedy ...
... reason not to put the complexity in the hosts. 2. The subnet is a major international investment that will last for decades, so it should not be cluttered up with features that may become obsolete quickly. 3. Some applications, such as digitized voice and real-time data collection may regard speedy ...
Panasonic Ethernet
... wide-spread IEC 60870-5 telecontrol standard is possible. Thus remote process stations can easily be linked to supervisory control systems or telecontrol main systems. The IEC60870 Communicator supports both IEC 60870-5-101 communication via RS232C or modem and IEC 60870-5-104 communication via Ethe ...
... wide-spread IEC 60870-5 telecontrol standard is possible. Thus remote process stations can easily be linked to supervisory control systems or telecontrol main systems. The IEC60870 Communicator supports both IEC 60870-5-101 communication via RS232C or modem and IEC 60870-5-104 communication via Ethe ...
A DoS-limiting Network Architecture
... Security based on inability of attacker to gain capabilities for routers along path to destination. Hashing scheme uses a sufficiently small key that changes every 128 sec. Breaking the key is practically impossible. Attacker may observe pre-capabilities in requests by routers. Stolen capabi ...
... Security based on inability of attacker to gain capabilities for routers along path to destination. Hashing scheme uses a sufficiently small key that changes every 128 sec. Breaking the key is practically impossible. Attacker may observe pre-capabilities in requests by routers. Stolen capabi ...
ISIS Introduction - Workshops
... ISIS supports a large number of routers in a single area When network is so large requiring the use of areas, employ summary-addresses >400 routers in the backbone is quite doable … according to Philip Smith :-) ...
... ISIS supports a large number of routers in a single area When network is so large requiring the use of areas, employ summary-addresses >400 routers in the backbone is quite doable … according to Philip Smith :-) ...
Introduction
... Case 2 : No Physical Multicast Support Most WANs do not support physical multicast addressing . To send a multicast packet through these networks, a process called tunneling is used. In tunneling , the multicast packet is encapsulated in a unicast packet and sent through the network, where it emer ...
... Case 2 : No Physical Multicast Support Most WANs do not support physical multicast addressing . To send a multicast packet through these networks, a process called tunneling is used. In tunneling , the multicast packet is encapsulated in a unicast packet and sent through the network, where it emer ...
SEMESTER 1 Chapter 5
... Establishment of adjacencies with neighboring routers using the EIGRP hello protocol. Support for VLSM and manual route summarization. These allow EIGRP to create hierarchically structured large networks. Although routes are propagated in a distance vector manner, the metric is based on minimum band ...
... Establishment of adjacencies with neighboring routers using the EIGRP hello protocol. Support for VLSM and manual route summarization. These allow EIGRP to create hierarchically structured large networks. Although routes are propagated in a distance vector manner, the metric is based on minimum band ...
Internet QoS
... – scalability: SLA based on the local QoS capabilities – Single-domain QoS – Multidomain QoS – The whole Internet – Q-BGP (= QoS-Enhanced Border Gateway Protocol) – Application-layer QoS routing – Performance-based routing: best routes selected by monitoring the ...
... – scalability: SLA based on the local QoS capabilities – Single-domain QoS – Multidomain QoS – The whole Internet – Q-BGP (= QoS-Enhanced Border Gateway Protocol) – Application-layer QoS routing – Performance-based routing: best routes selected by monitoring the ...
MidoNet Troubleshooting Guide
... MidoNet is a network virtualization software for Infrastructure-as-a-Service (IaaS) clouds. It decouples your IaaS cloud from your network hardware, creating an intelligent software abstraction layer between your end hosts and your physical network. This document contains useful information on troub ...
... MidoNet is a network virtualization software for Infrastructure-as-a-Service (IaaS) clouds. It decouples your IaaS cloud from your network hardware, creating an intelligent software abstraction layer between your end hosts and your physical network. This document contains useful information on troub ...
Mobile networking in the Internet
... Besides minimal weight and size, there are other hardware implications when designing for mobile computing. Clearly, battery powered operation is highly desirable, and improvements in battery life continue to extend the feasibility of tetherless computing. On the other hand, the proliferation of mob ...
... Besides minimal weight and size, there are other hardware implications when designing for mobile computing. Clearly, battery powered operation is highly desirable, and improvements in battery life continue to extend the feasibility of tetherless computing. On the other hand, the proliferation of mob ...
11-BGP
... • Sent periodically (but before hold timer expires) to peers to ensure connectivity. • Sent in place of an UPDATE message ...
... • Sent periodically (but before hold timer expires) to peers to ensure connectivity. • Sent in place of an UPDATE message ...
Explicit Congestion Notification (ECN) RFC 3168
... receiver MUST keep sending ECE ACKs until it gets a TCP-PDU with CWR set Any more IP-PDUs with CE set are treated as new instances of congestion in the network In delayed ACKs, ECE in ACK is set if CE is set for any of the IP-PDUs being acknowledged What does the receipt of CWR guarantee? ...
... receiver MUST keep sending ECE ACKs until it gets a TCP-PDU with CWR set Any more IP-PDUs with CE set are treated as new instances of congestion in the network In delayed ACKs, ECE in ACK is set if CE is set for any of the IP-PDUs being acknowledged What does the receipt of CWR guarantee? ...
Link-State Routing Protocols
... • Each router builds its own Link State Packet (LSP) which includes information about neighbors such as neighbor ID, link type, & bandwidth • After the LSP is created the router floods it to all immediate neighbors who then store the information, and then forward it until all routers have the same i ...
... • Each router builds its own Link State Packet (LSP) which includes information about neighbors such as neighbor ID, link type, & bandwidth • After the LSP is created the router floods it to all immediate neighbors who then store the information, and then forward it until all routers have the same i ...
ppt
... Have a window of packets ready for transmission Can send only those packets that are in the window up to the end of the window Every time an acknowledgement is received, window slides (and its size may be increased). Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher ...
... Have a window of packets ready for transmission Can send only those packets that are in the window up to the end of the window Every time an acknowledgement is received, window slides (and its size may be increased). Copyright Jorg Liebeherr 98, Modified with permission, Abdelzaher ...
CB23474480
... TCP/IP network can be further divided, or subnetted, by a system administrator. A system administrator who is allocated a block of IP addresses may be administering networks that are not organized in a way that easily fits these addresses. For example, you have a wide area network with 150 hosts on ...
... TCP/IP network can be further divided, or subnetted, by a system administrator. A system administrator who is allocated a block of IP addresses may be administering networks that are not organized in a way that easily fits these addresses. For example, you have a wide area network with 150 hosts on ...
Routing
... Designed to overcome the drawbacks of distancevector routing When a router is initialized, it determines the link cost on each of its network interfaces The router then advertises this set of link costs to all other routers in the internet topology, not just neighboring routers From then on, the rou ...
... Designed to overcome the drawbacks of distancevector routing When a router is initialized, it determines the link cost on each of its network interfaces The router then advertises this set of link costs to all other routers in the internet topology, not just neighboring routers From then on, the rou ...
Chap 11 Routing
... Network and host addressing Path selection and packet switching Routed versus routing protocol Network-layer protocol operations Multiprotocol routing ...
... Network and host addressing Path selection and packet switching Routed versus routing protocol Network-layer protocol operations Multiprotocol routing ...
Broadband Open Access: Lessons from Municipal Network Case
... FTTx Architectures and Why it Matters for the Open Access Debate Marvin A. Sirbu Department of Engineering and Public Policy Carnegie Mellon University [email protected] http://www.andrew.cmu.edu/user/sirbu/ ...
... FTTx Architectures and Why it Matters for the Open Access Debate Marvin A. Sirbu Department of Engineering and Public Policy Carnegie Mellon University [email protected] http://www.andrew.cmu.edu/user/sirbu/ ...
IPNetworkingUNIT7 - Rhema Impact Ministries
... VLSM • VLSM occurs when an internetwork uses more than one mask in different subnets of a single Class A, B, or C network. • VLSM allows engineers to reduce the number of wasted IP addresses in each subnet, allowing more subnets and avoiding having to obtain another registered IP network number fro ...
... VLSM • VLSM occurs when an internetwork uses more than one mask in different subnets of a single Class A, B, or C network. • VLSM allows engineers to reduce the number of wasted IP addresses in each subnet, allowing more subnets and avoiding having to obtain another registered IP network number fro ...
Document
... Design issues: services Interface o Important: = interface between carrier and customer o Designed with following goals in mind: • Services should be independent of the subnet technology • Transport layer should be shielded from the number, type, topology of the subnets • Network addresses should ...
... Design issues: services Interface o Important: = interface between carrier and customer o Designed with following goals in mind: • Services should be independent of the subnet technology • Transport layer should be shielded from the number, type, topology of the subnets • Network addresses should ...
Internet protocol suite

The Internet protocol suite is the computer networking model and set of communications protocols used on the Internet and similar computer networks. It is commonly known as TCP/IP, because among many protocols, the Transmission Control Protocol (TCP) and the Internet Protocol (IP) is the accepted and most widely used protocol in Internet. Often also called the Internet model, it was originally also known as the DoD model, because the development of the networking model was funded by DARPA, an agency of the United States Department of Defense.TCP/IP provides end-to-end connectivity specifying how data should be packetized, addressed, transmitted, routed and received at the destination. This functionality is organized into four abstraction layers which are used to sort all related protocols according to the scope of networking involved. From lowest to highest, the layers are the link layer, containing communication technologies for a single network segment (link); the internet layer, connecting hosts across independent networks, thus establishing internetworking; the transport layer handling host-to-host communication; and the application layer, which provides process-to-process application data exchange.The TCP/IP model and related protocol models are maintained by the Internet Engineering Task Force (IETF).