* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download NET331_lecture10
Multiprotocol Label Switching wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Internet protocol suite wikipedia , lookup
Computer network wikipedia , lookup
Airborne Networking wikipedia , lookup
Computer security wikipedia , lookup
Wireless security wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Network tap wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Deep packet inspection wikipedia , lookup
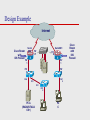
Firewalls What is a Firewall? A firewall is a set of related programs, located at a network gateway server, that protects the resources of a private network from users from other networks. System designed to prevent unauthorized access to or from a private network Will check messages entering and leaving and block those that do not meet the specified security criteria Considered the first line of defense in protecting private information Can be Hardware or Software Firewall Common Misconceptions of Firewalls A firewall is always a hardware A firewall can protect you from all possible threats A firewall protects all possible Information A firewall can protect you from a completely new threat If have a firewall you don’t need an anti-virus program Hardware Firewalls Can be a stand-alone product but typically found in broadband routers Use packet filtering ( next slides) Protects the system from the outside Pros: easy to set up, protect every machine on the local network Cons: treats any kind of traffic from the local network to the internet as safe Common Firewall Systems Cisco – Work with high end and large enterprise systems – Very expensive NetGear – Low end hardware security (not recommended) Hotbrick – Good firewall system for reasonable price – Home offices SonicWall – Good firewall – Medium to large scale company use Software Firewalls Installed on your computer Can block or allow a program’s ability to send and receive data Pros: knows what program is trying to access the internet and if it is malicious or not Cons: only protect the machine installed on Software firewall program • • • • IP Chains & IPTables IPCop SELinux ISA Firewall Techniques Packet Filtering – Accepts or rejects packets based on the rules defined by the user Application Gateway – Security to specific applications Circuit-level Gateway – Applies security mechanisms when a TCP connection is established Proxy Server – Intercepts messages entering and leaving the network Processing Mode Five – – – – – major categories Packet filtering Application gateway (proxy firewall) Circuit gateway MAC layer Hybrids » Most common use » Several of above Firewalls – Packet Filters Firewalls – Packet Filters Simplest of components Uses transport-layer information only – IP Source Address, Destination Address – Protocol/Next Header (TCP, UDP, ICMP, etc) – TCP or UDP source & destination ports – TCP Flags (SYN, ACK, FIN, RST, PSH, etc) – ICMP message type Examples – DNS uses port 53 » No incoming port 53 packets except known trusted servers Example Incoming packets from network 131.34.0.0 are blocked. ‘*’ means any. Incoming packets destined for any internal TELNET server (port 23) are blocked. Incoming packets destined to internal host 194.78.20.8 are blocked (this host for internal use) outgoing packets destined for an HTTP server (port 80) are blocked. (i.e. does not want employees to browser the Internet) Standard or Stateless Two main types packet filtering – Also known as first generation firewall – Operates at either the Network or Transport layer. – Most packet filters used the values of the following header field to determine what to pass or not » Protocol type, IP address, TCP/UDP port, Fragment number – they does not look at the actual payload. statefull known as dynamic packet filtering inspect every packet, compare the packet against the state table, and may examine the packet for any special protocol negotiations. Stateful firewalls operate mainly at the Transport (TCP and UDP) layer. Stateless vs.Stateful Stateless vs.Stateful Stateless Packet-Filtering Firewalls – ignores the state of the connection between the internal computer and the external computer. – A firewall that conducts stateless packet filtering simply blocks or allows a packet based on the information in the header. Stateful Packet-Filtering Firewalls – is an examination of the data contained in a packet as well as the state of the connection between internal and external computers. – This information, known as the state table, is kept in a memory location called the cache. – Stateful inspection is superior to stateless inspection because it uses the connection state to make decisions on whether to allow the traffic. Application Gateway Application gateway firewalls (AGFs), commonly called proxy firewalls Because AGFs process information at the application layer, most of the firewall control and filtering is done in software, – more control over traffic than packet-filtering or stateful firewalls. is frequently installed on a dedicated computer, separate from the filtering router, but is commonly used in conjunction with a filtering router. Sometimes AGFs support only a limited number of applications, or even just one application. – e-mail, web services, DNS, Telnet, FTP, Usenet news, LDAP, and finger. Circuit Gateways operates at the transport layer. Connections are authorized based on addresses. Like filtering firewalls, circuit gateway firewalls do not usually look at data traffic flowing between one network and another do prevent direct connections between one network and another by creating tunnels that connect specific processes or systems on each side of the firewall and then allowing only authorized traffic, such as a specific type of TCP connection for only authorized users, in these tunnels. OSI Model 7 Application 6 Presentation 5 Session Circuit Gateway 4 Transport 3 Network 2 Data 1 Physical MAC Layer Firewalls While not as well known or widely referenced as the firewall approaches above, MAC layer firewalls are designed to operate at the media access control layer of the OSI network model. This gives these firewalls the ability to consider the specific host computer’s identity in its filtering decisions. Using this approach, the MAC addresses of specific host computers are linked to ACL entries that identify the specific types of packets that can be sent to each host, and all other traffic is blocked. Hybrid Firewalls Combine elements of other types of firewalls; i.e., elements of packet filtering and proxy services, or of packet filtering and circuit gateways Alternately, may consist of two separate firewall devices; each a separate firewall system, but are connected to work in tandem Firewall Structure Firewall appliances are stand-alone, self-contained systems that frequently have many of the features of a general-purpose computer with the addition of firmware-based instructions that increase their reliability and performance and minimize the likelihood of their being compromised. A commercial-grade firewall system consists of firewall application software running on a general-purpose computer. Organizations can – install firewall software on an existing general-purpose computer system, – or they can purchase hardware that has been configured to the specifications that yield optimum performance for the firewall software. Firewall Structure Small Office/Home Office (SOHO) SOHO and residential-grade firewall devices, known as broadband gateways or DSL/cable modem routers, connect the user’s local area network or a specific computer system to the Internetworking device. The SOHO firewall serves first as a stateful firewall to enable inside-to-outside access, and it can be configured by use. Residential-grade firewall software is installed directly on the user’s system. Some of these applications combine firewall services with other protections such as antivirus or intrusion detection. There are limits to the level of configurability and protection that software firewalls can provide. Software vs. Hardware: the SOHO Firewall Debate Which firewall type should the residential user implement? Where would you rather defend against a hacker? With the software option, hacker is inside your computer With the hardware device, even if hacker manages to crash firewall system, computer and information are still safely behind the now disabled connection Firewall Architectures Sometimes the architecture is exclusive Configuration decision – Objectives of the network – The org’s ability to develop and implement architecture – Budget Firewall Architectures Packet filtering routers – Lacks auditing and strong authentication – Can degrade network performance Firewall Architectures Screened Host firewall – Combines packet filtering router with dedicated firewall – such as proxy server – Allows router to prescreen packets – Application proxy examines at application layer – Separate host – bastion or sacrificial host – Requires external attack to compromise 2 separate systems. Firewall Architectures Dual Homed Host – Two network interface cards » » » » » One connected to external network One connected to internal network Additional protection All traffic must go through firewall to get to networks Implementation of this architecture often makes use of NAT. NAT is a method of mapping assigned IP addresses to special ranges of nonroutable internal IP addresses, thereby creating yet another barrier to intrusion from external attackers. Disadvantage Host serves as a single point of entry to the organization Firewall Architectures Screened Subnet Firewalls (with DMZ) The dominant architecture used today provides a DMZ. The DMZ can be a dedicated port on the firewall device linking a single bastion host, or it can be connected to a screened subnet. Common arrangement – Connections from the outside or untrusted network are routed through an external filtering router. – Connections from the outside or untrusted network are routed into—and then out of—a routing firewall to the separate network segment known as the DMZ. – Connections into the trusted internal network are allowed only from the DMZ bastion host servers. Expensive to implement Complex to configure and manage DMZ Screened Subnet Firewall Design Simple Firewall Design Firewall designs can be as simple as having an inside network and outside network using two interfaces. – The inside network (or private network) is trusted. » The traffic from the inside is usually permitted to traverse the firewall to the outside with little or no restrictions. » Traffic returning from the outside that is associated with traffic originating from the inside is permitted to traverse from the untrusted interface to the trusted interface. – The outside network (or public network) is untrusted. » Traffic originating from the outside is generally blocked entirely or very selectively permitted. Modern Firewall Design Designs involve three or more interfaces on a firewall: – One inside network » Traffic to the outside is freely permitted. » Traffic to the DMZ is freely permitted. – One outside network » Traffic from the outside is generally blocked entirely unless it is associated with traffic originating from the inside or the DMZ. – One DMZ network » Traffic from the outside should be very specific such as email, DNS, HTTP, or HTTPS traffic. » Traffic to the outside is freely permitted. Modern Firewall Design Selecting the Right Firewall What firewall offers right balance between protection and cost for needs of organization? What features are included in base price and which are not? Ease of setup and configuration? How accessible are staff technicians who can configure the firewall? Can firewall adapt to organization’s growing network? Selecting the Right Firewall Most important factor – Extent to which the firewall design provides the required protection Second most important factor – Cost Configuring and Managing Firewalls Each firewall device must have own set of configuration rules regulating its actions Firewall policy configuration is usually complex and difficult Configuring firewall policies both an art and a science When security rules conflict with the performance of business, security often loses Firewall Best Practices Position firewalls at security boundaries. Firewalls are the primary security device. It is unwise to rely exclusively on a firewall for security. Deny all traffic by default. Permit only services that are needed. Ensure that physical access to the firewall is controlled. Regularly monitor firewall logs. Practice change management for firewall configuration changes. Remember that firewalls primarily protect from technical attacks originating from the outside. Design Example Internet R 2 Cisco Router with IOS Firewall Serial 0/0/0 F0/ 1 Serial0/0/1 F0/ 0 F0/ 0 R 1 R 3 F0/ 1 F0/ 5 F0/6 F0/ 5 S 1 S 3 F0/1 F0/1 S F0/1 2 8 PC A (RADIUS/TACA CS+) PC C F0/1 8 Cisco Router with IOS Firewall