Intro to Internet-services from Security Standpoint
... – Challenge: setting the right policy for the right kind of communication. – The concept of layer independence complicates things => security associations to transport level port numbers. – Disadvantages: requires replacement of the TCP/IP stack. • On UNIX/Linux this requires kernel recompilation. • ...
... – Challenge: setting the right policy for the right kind of communication. – The concept of layer independence complicates things => security associations to transport level port numbers. – Disadvantages: requires replacement of the TCP/IP stack. • On UNIX/Linux this requires kernel recompilation. • ...
The Polycom SoundPoint IP 400
... costs and in addition, companies utilizing IP trunking can reduce long distance and toll call communication costs. • Integrating voice and data into one network means investment in one technology and one support organization, reducing infrastructure costs. • System configurations do not have to be c ...
... costs and in addition, companies utilizing IP trunking can reduce long distance and toll call communication costs. • Integrating voice and data into one network means investment in one technology and one support organization, reducing infrastructure costs. • System configurations do not have to be c ...
Topics discussed in this section
... A protocol is a set of rules that govern data communications. A protocol defines what is communicated, how it is communicated, and when it is communicated. The key elements of a protocol are syntax, semantics, and timing. Syntax refers to the structure or format of the data, meaning the order in whi ...
... A protocol is a set of rules that govern data communications. A protocol defines what is communicated, how it is communicated, and when it is communicated. The key elements of a protocol are syntax, semantics, and timing. Syntax refers to the structure or format of the data, meaning the order in whi ...
Computer Networks BITS ZC481
... packets (Packet Switching) from one node to other towards destination host can be routers or switches. ...
... packets (Packet Switching) from one node to other towards destination host can be routers or switches. ...
PPP - Chakarov
... The network layer routing •The switch will allow routing in the local LAN •A packet of information will be forwarded out of a particular interface based on the MAC address of the device attached to it •Routers forward based on the IP address (Network layer) information ...
... The network layer routing •The switch will allow routing in the local LAN •A packet of information will be forwarded out of a particular interface based on the MAC address of the device attached to it •Routers forward based on the IP address (Network layer) information ...
An introduction to Network Analyzers
... computer communication Based on shared medium and broadcasting Ethernet address is called MAC address 48 bit HW address coded in the RON of the NIC card The first 12 bits represent the vender The second 12 bits represent the serial number Use: arp –a Remember: IP address is logical address ...
... computer communication Based on shared medium and broadcasting Ethernet address is called MAC address 48 bit HW address coded in the RON of the NIC card The first 12 bits represent the vender The second 12 bits represent the serial number Use: arp –a Remember: IP address is logical address ...
Network Layer
... computer into its network layer (IP) address. Find the application layer address of the computer in the To box in the Network Map, and write its IP address in the Final Destination box. 2. Route the message by finding the next computer to which the message should be sent in the Network Map, and writ ...
... computer into its network layer (IP) address. Find the application layer address of the computer in the To box in the Network Map, and write its IP address in the Final Destination box. 2. Route the message by finding the next computer to which the message should be sent in the Network Map, and writ ...
Slide 1
... The USSR launches the first satellite, Sputnik. To compete against the USSR's success at launching the first satellite, the United States Department of Defense creates the Advanced Research Projects Agency (ARPA). ARPA is responsible for the development of new technology for use by the military. ...
... The USSR launches the first satellite, Sputnik. To compete against the USSR's success at launching the first satellite, the United States Department of Defense creates the Advanced Research Projects Agency (ARPA). ARPA is responsible for the development of new technology for use by the military. ...
CSCI6268L19
... responses to security compromises • Identify trends in intruder activity • Work with other security experts to identify solutions to security problems • Disseminate information to the broad community ...
... responses to security compromises • Identify trends in intruder activity • Work with other security experts to identify solutions to security problems • Disseminate information to the broad community ...
Overview
... • Router role identification [Rocketfuel] – Backbone vs. access routers – Use DNS and topological ordering ...
... • Router role identification [Rocketfuel] – Backbone vs. access routers – Use DNS and topological ordering ...
Networking
... Star Topology: The type of network topology in which each of the nodes of the network is connected to a central node with a point-to-point link in a 'hub' and 'spoke' fashion, the central node being the 'hub' and the nodes that are attached to the central node being the 'spokes' (e.g., a collection ...
... Star Topology: The type of network topology in which each of the nodes of the network is connected to a central node with a point-to-point link in a 'hub' and 'spoke' fashion, the central node being the 'hub' and the nodes that are attached to the central node being the 'spokes' (e.g., a collection ...
CAN1102-2009-10-S1-exampaper
... The IEEE 802 series of standards describe both the Physical and Data Link layers of their respective technologies. Two important standards are 802.3 and 802.5, respectively known as CSMA/CD (Ethernet) and Token Ring. i. Explain how CSMA/CD operates and describe how Ethernet deals with ...
... The IEEE 802 series of standards describe both the Physical and Data Link layers of their respective technologies. Two important standards are 802.3 and 802.5, respectively known as CSMA/CD (Ethernet) and Token Ring. i. Explain how CSMA/CD operates and describe how Ethernet deals with ...
Network Interface Card Specifications
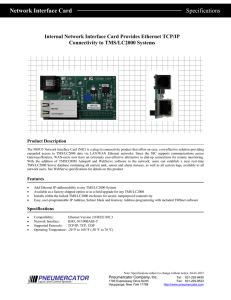
... expanded access to TMS/LC2000 data via LAN/WAN Ethernet networks. Since the NIC supports communications across Gateways/Routers, WAN-users now have an extremely cost-effective alternative to dial-up connections for remote monitoring. With the addition of TMSCOMM Autopoll and WebServe software to the ...
... expanded access to TMS/LC2000 data via LAN/WAN Ethernet networks. Since the NIC supports communications across Gateways/Routers, WAN-users now have an extremely cost-effective alternative to dial-up connections for remote monitoring. With the addition of TMSCOMM Autopoll and WebServe software to the ...
TCP/IP architecture
... TCP/IP architecture—application layer • Provide services that can be used by other applications • Incorporate the functions of top 3 OSI layers • E.g., HTTP protocol, format in request, dialogue between client and server – http request/response contains format information, so ...
... TCP/IP architecture—application layer • Provide services that can be used by other applications • Incorporate the functions of top 3 OSI layers • E.g., HTTP protocol, format in request, dialogue between client and server – http request/response contains format information, so ...
TCP/IP model
... – Assigned to vendors by a central authority – The broadcast address is all 1’s. ...
... – Assigned to vendors by a central authority – The broadcast address is all 1’s. ...
Introduction to Network Computing - Computer Science
... networks so that they act as if they are one network usually connects like networks: Ethernet to Ethernet, etc. “smart” repeater: monitors and limits “traffic” ...
... networks so that they act as if they are one network usually connects like networks: Ethernet to Ethernet, etc. “smart” repeater: monitors and limits “traffic” ...
Lecture 3: Introduction to net
... Each network should be able to work on its own, developing its own applications without restraint and requiring no modification to participate in the Internet Within each network there would be a 'gateway', which would link it to the 'outside world' ...
... Each network should be able to work on its own, developing its own applications without restraint and requiring no modification to participate in the Internet Within each network there would be a 'gateway', which would link it to the 'outside world' ...
Wireless TCP(September 20)
... Comparison of Mechanisms for Improving TCP Performance over Wireless Links , " IEEE/ACM Transactions on Networking, December 1997. ...
... Comparison of Mechanisms for Improving TCP Performance over Wireless Links , " IEEE/ACM Transactions on Networking, December 1997. ...
Closure - The University of Sydney
... Provides access to local network Supplies local address Transports traffic over one hop only Many different technologies with different characteristics • Wired and wireless ...
... Provides access to local network Supplies local address Transports traffic over one hop only Many different technologies with different characteristics • Wired and wireless ...
cut-through
... What will a bridge do if it receives a frame with a MAC address that is not within the table? • send frame to all ports except ...
... What will a bridge do if it receives a frame with a MAC address that is not within the table? • send frame to all ports except ...
Hybrid Networks - MIT Haystack Observatory
... Over the last decade, the most widely used technology for establishing connections within the Internet has been Multi-Protocol Label Switching (MPLS) ...
... Over the last decade, the most widely used technology for establishing connections within the Internet has been Multi-Protocol Label Switching (MPLS) ...
Internet protocol suite

The Internet protocol suite is the computer networking model and set of communications protocols used on the Internet and similar computer networks. It is commonly known as TCP/IP, because among many protocols, the Transmission Control Protocol (TCP) and the Internet Protocol (IP) is the accepted and most widely used protocol in Internet. Often also called the Internet model, it was originally also known as the DoD model, because the development of the networking model was funded by DARPA, an agency of the United States Department of Defense.TCP/IP provides end-to-end connectivity specifying how data should be packetized, addressed, transmitted, routed and received at the destination. This functionality is organized into four abstraction layers which are used to sort all related protocols according to the scope of networking involved. From lowest to highest, the layers are the link layer, containing communication technologies for a single network segment (link); the internet layer, connecting hosts across independent networks, thus establishing internetworking; the transport layer handling host-to-host communication; and the application layer, which provides process-to-process application data exchange.The TCP/IP model and related protocol models are maintained by the Internet Engineering Task Force (IETF).