Final bits of OS - Department of Computer Science
... • Can encrypt data with keys on one machine. • Data can then ONLY be decrypted on that machine. – Can even be sealed so that one a particular application can access it. ...
... • Can encrypt data with keys on one machine. • Data can then ONLY be decrypted on that machine. – Can even be sealed so that one a particular application can access it. ...
Protocol Overview
... • Kerberos is a network authentication protocol. It is designed to provide strong authentication for client/server applications by using secret-key cryptography. • Before a network connection is opened between two entities, Kerberos establishes a shared secret key through a Ticket Granting Server (T ...
... • Kerberos is a network authentication protocol. It is designed to provide strong authentication for client/server applications by using secret-key cryptography. • Before a network connection is opened between two entities, Kerberos establishes a shared secret key through a Ticket Granting Server (T ...
Chapter04
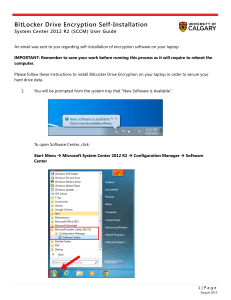
... on a new system then any hotfixes should be applied. The third common update is a patch, or a software update to fix or repair of a specific security flaw. Patches may be released on a regular or irregular basis, depending upon the vendor or support team. Patches for a local operating system can be ...
... on a new system then any hotfixes should be applied. The third common update is a patch, or a software update to fix or repair of a specific security flaw. Patches may be released on a regular or irregular basis, depending upon the vendor or support team. Patches for a local operating system can be ...
Operating System Security Chapter 9 Operating System Security
... • Security administrators should regularly assess the current status of a computer by locating and analyzing stored status data • Computer forensics is the process of searching for evidence of a specific activity by searching log files and file systems • System footprinting (baselining) is a “snapsh ...
... • Security administrators should regularly assess the current status of a computer by locating and analyzing stored status data • Computer forensics is the process of searching for evidence of a specific activity by searching log files and file systems • System footprinting (baselining) is a “snapsh ...
Ch10 - Protection Mechanism
... – Restriction of access to Web sites with non-business-related material, such as pornography, or restriction of spam e-mail ...
... – Restriction of access to Web sites with non-business-related material, such as pornography, or restriction of spam e-mail ...
Protocol Overview
... • Kerberos is a network authentication protocol. It is designed to provide strong authentication for client/server applications by using secret-key cryptography. • Before a network connection is opened between two entities, Kerberos establishes a shared secret key through a Ticket Granting Server (T ...
... • Kerberos is a network authentication protocol. It is designed to provide strong authentication for client/server applications by using secret-key cryptography. • Before a network connection is opened between two entities, Kerberos establishes a shared secret key through a Ticket Granting Server (T ...
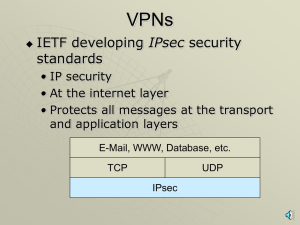
VPNs, PKIs, ISSs, SSLs with narration
... PKI Server Creates Public KeyPrivate Key Pairs • Distributes private keys to applicants securely ...
... PKI Server Creates Public KeyPrivate Key Pairs • Distributes private keys to applicants securely ...