Wireless N 150Mbps - Atlantis-Land
... security, it increases the level of data protection and access control for Wireless LAN. Reverse-SMA 5 dBi Antenna provides extended coverage. The WDS (up to 4 AP) feature makes the WebShare 242 WN an ideal solution for quickly creating and extending a wireless local area network (WLAN) in offices o ...
... security, it increases the level of data protection and access control for Wireless LAN. Reverse-SMA 5 dBi Antenna provides extended coverage. The WDS (up to 4 AP) feature makes the WebShare 242 WN an ideal solution for quickly creating and extending a wireless local area network (WLAN) in offices o ...
Semester 3 Chapter 4 - Institute of Technology Sligo
... devices. Therefore, they also share the same collision domain. To determine the bandwidth per host, simply divide the port’s bandwidth by the number of hosts (see graphic). In a pure switched LAN environment where each host has its own port, the size of the collision domain is 2. If running full-dup ...
... devices. Therefore, they also share the same collision domain. To determine the bandwidth per host, simply divide the port’s bandwidth by the number of hosts (see graphic). In a pure switched LAN environment where each host has its own port, the size of the collision domain is 2. If running full-dup ...
Research Rugby
... – Use a four-way handshake: RTS-CTS-DATA-ACK where the RTS and CTS packets are significantly smaller than the average data packet. – The maximum number of RTS retransmissions is set to 7. ...
... – Use a four-way handshake: RTS-CTS-DATA-ACK where the RTS and CTS packets are significantly smaller than the average data packet. – The maximum number of RTS retransmissions is set to 7. ...
CSE3213 Computer Network I
... Datagram networks • no call setup at network layer • routers: no state about end-to-end connections – no network-level concept of “connection” ...
... Datagram networks • no call setup at network layer • routers: no state about end-to-end connections – no network-level concept of “connection” ...
IJAER-International Journal of Advances in Engineering Research
... Though it won't be winning any router beauty contests any time soon with its homely design, theAirlink101 AR504 soundly beats the competition in this roundup, both in terms of performance and feature set. With nearly double the benchmarked speeds of its nearest competitor, along with a full set of f ...
... Though it won't be winning any router beauty contests any time soon with its homely design, theAirlink101 AR504 soundly beats the competition in this roundup, both in terms of performance and feature set. With nearly double the benchmarked speeds of its nearest competitor, along with a full set of f ...
OTTAWA POLICE SERVICE JOB DESCRIPTION
... Attends classes, seminars, conferences and reviews professional literature to enhance knowledge of trends and developments related to wide and local area network systems. Maintain current knowledge of industrial standards and best practices of major developments and trends in information technology, ...
... Attends classes, seminars, conferences and reviews professional literature to enhance knowledge of trends and developments related to wide and local area network systems. Maintain current knowledge of industrial standards and best practices of major developments and trends in information technology, ...
Security Management System - Remote Client
... internal network of an enterprise. Hence it is not accessible from the client applications running on computers outside this internal enterprise network. This is common practice followed for security of computers on the internal network. However in some case, it may be needed to grant access to a fe ...
... internal network of an enterprise. Hence it is not accessible from the client applications running on computers outside this internal enterprise network. This is common practice followed for security of computers on the internal network. However in some case, it may be needed to grant access to a fe ...
Network Fundamentals
... a packet should be forwarded toward its destination. • Allow different networks to communicate with each other • A router creates and maintain a table of the available routes and their conditions and uses this information along with distance and cost algorithms to determine the best route for a give ...
... a packet should be forwarded toward its destination. • Allow different networks to communicate with each other • A router creates and maintain a table of the available routes and their conditions and uses this information along with distance and cost algorithms to determine the best route for a give ...
File - Itassignments
... ARP reply is cached (kept in cache memory for a while) because a system normally sends several packets to the same destination. A system that receives an ARP reply stores the mapping in the cache memory and keeps it for 20 to 30 minutes unless the space in the cache is exhausted. Before sending an A ...
... ARP reply is cached (kept in cache memory for a while) because a system normally sends several packets to the same destination. A system that receives an ARP reply stores the mapping in the cache memory and keeps it for 20 to 30 minutes unless the space in the cache is exhausted. Before sending an A ...
Slide 1
... expansion slot inside the computer. Some computers, such as Mac Classics, use external boxes which are attached to a serial port or a SCSI port. Laptop computers generally use external LAN adapters connected to the parallel port or network cards that slip into a PCMCIA slot. • Network interface card ...
... expansion slot inside the computer. Some computers, such as Mac Classics, use external boxes which are attached to a serial port or a SCSI port. Laptop computers generally use external LAN adapters connected to the parallel port or network cards that slip into a PCMCIA slot. • Network interface card ...
EIE Building - Department of LD
... and know computer Internetworking including Architecture, Inter-networking issues such as: network layer structure, Router and gateway, Internet protocol standards, Internet IP, routing protocols, Addressing, Domain Name System, Connectionless datagram delivery, Internet protocol suite, Internet app ...
... and know computer Internetworking including Architecture, Inter-networking issues such as: network layer structure, Router and gateway, Internet protocol standards, Internet IP, routing protocols, Addressing, Domain Name System, Connectionless datagram delivery, Internet protocol suite, Internet app ...
Document
... Frames are similar to data packets but are blocks of data specific to a single type of hardware architecture. Frames have checksums to detect errors in transmission. Corrupted frames are discarded so that they will not be passed to higher layers. ...
... Frames are similar to data packets but are blocks of data specific to a single type of hardware architecture. Frames have checksums to detect errors in transmission. Corrupted frames are discarded so that they will not be passed to higher layers. ...
Chapter 1
... transmission of IP packets over serial lines. The point-topoint link provides a single, pre-established communications path from the ending element through a carrier network, such as a telephone company, to a remote network. These links can carry datagram or data-stream transmissions. – xDirect Serv ...
... transmission of IP packets over serial lines. The point-topoint link provides a single, pre-established communications path from the ending element through a carrier network, such as a telephone company, to a remote network. These links can carry datagram or data-stream transmissions. – xDirect Serv ...
Northeastern Illinois University Department of Computer
... Instructions: The answer to the questions should ALL be written down in space provided. Poorly written answers will be poorly graded. Question 1: Multiple choice (2 points for each correct answer), please select your answer by placing a circle over the letter and justifying when asked. There is only ...
... Instructions: The answer to the questions should ALL be written down in space provided. Poorly written answers will be poorly graded. Question 1: Multiple choice (2 points for each correct answer), please select your answer by placing a circle over the letter and justifying when asked. There is only ...
инструкция
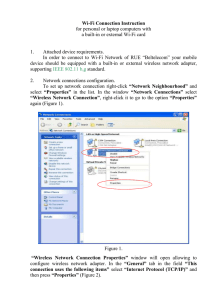
... PLEASE NOTE: Should you choose connection to the wireless network “byfly WIFI” and the message “No or limited connectivity” is displayed in the window containing the list of available wireless network connections, or the authorization page fails to download when entering the necessary address in th ...
... PLEASE NOTE: Should you choose connection to the wireless network “byfly WIFI” and the message “No or limited connectivity” is displayed in the window containing the list of available wireless network connections, or the authorization page fails to download when entering the necessary address in th ...
ppt - Courses
... 2008 ISP Infrastructure Security Report (Arbor, 2008) - Largest DDoS attack peak traffic volume of 40Gbps ...
... 2008 ISP Infrastructure Security Report (Arbor, 2008) - Largest DDoS attack peak traffic volume of 40Gbps ...
Port Forwarding with Linksys Router
... If your service provider does not offer static IP addresses it is possible to use a dynamic address in conjunction with a DDNS service (i.e. www.tzo.com or www.dyndns.org). ...
... If your service provider does not offer static IP addresses it is possible to use a dynamic address in conjunction with a DDNS service (i.e. www.tzo.com or www.dyndns.org). ...
ITS CSS Desktop Support
... IP is used for communicating data across a packet-switched network. Nodes within a network are assigned an IP address. IP acts as a transport layer for other network protocols (ICMP, TCP, UDP) ...
... IP is used for communicating data across a packet-switched network. Nodes within a network are assigned an IP address. IP acts as a transport layer for other network protocols (ICMP, TCP, UDP) ...
Sniffing/Spoofing - Dr. Stephen C. Hayne
... computer is dead to network Attacker launches a connection with victim using trusted computer’s IP address The victim returns an SYN-ACK to trusted computer, but no reply is sent because it was hit with a DoS attack Using the sequence numbers gathered from step 1 the attacker sends ACK packets to th ...
... computer is dead to network Attacker launches a connection with victim using trusted computer’s IP address The victim returns an SYN-ACK to trusted computer, but no reply is sent because it was hit with a DoS attack Using the sequence numbers gathered from step 1 the attacker sends ACK packets to th ...
FAQ novoconnect - EDCO Education
... Yes, you can. As a matter of fact, you can connect NovoConnect to any display equipment with an HDMI port or a VGA port (via an adaptor). ...
... Yes, you can. As a matter of fact, you can connect NovoConnect to any display equipment with an HDMI port or a VGA port (via an adaptor). ...
Document
... To understand the flow of information on the Internet To understand the levels of activity in network traffic flow To understand the basis for vulnerabilities To understand the basis for security tools and how they work ...
... To understand the flow of information on the Internet To understand the levels of activity in network traffic flow To understand the basis for vulnerabilities To understand the basis for security tools and how they work ...
Chapter 15 Local Area Network Overview
... Routers + and + arbitrary topologies can be supported, cycling is limited by TTL counters (and good routing protocols) + provide protection against broadcast storms - require IP address configuration (not plug and play) - require higher packet processing ...
... Routers + and + arbitrary topologies can be supported, cycling is limited by TTL counters (and good routing protocols) + provide protection against broadcast storms - require IP address configuration (not plug and play) - require higher packet processing ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.