“The Tenet Architecture for Tiered Sensor Networks.”
... sensor data fusion. In contrast to a mote-application-specific view of sensor networking, the principle constrains the processing of data received from multiple sensors to be placed at the master tier, regardless of whether that processing is specific to an application or can be expressed as a gener ...
... sensor data fusion. In contrast to a mote-application-specific view of sensor networking, the principle constrains the processing of data received from multiple sensors to be placed at the master tier, regardless of whether that processing is specific to an application or can be expressed as a gener ...
Network Performance Definitions & Analysis
... Via satellite with a distance of 30 km between the base and the satellite ...
... Via satellite with a distance of 30 km between the base and the satellite ...
FAS Systems System-Level Diagnostics Guide
... To run system-level diagnostics, you must already be running Data ONTAP because you need to reach the Maintenance mode boot option in Data ONTAP. There are several approaches to get to this option, but this is the recommended approach taken in the procedures documented in this guide. Some hardware c ...
... To run system-level diagnostics, you must already be running Data ONTAP because you need to reach the Maintenance mode boot option in Data ONTAP. There are several approaches to get to this option, but this is the recommended approach taken in the procedures documented in this guide. Some hardware c ...
Detecting and Preventing Rogue Devices on the Network
... could be instances like someone spoofing MAC address of CPEʼs or APʼs. On the other hand someone can create noise intentionally like applying broadcast de- ...
... could be instances like someone spoofing MAC address of CPEʼs or APʼs. On the other hand someone can create noise intentionally like applying broadcast de- ...
Alcatel-Lucent OmniAccess 5510
... purpose-built platform for simultaneous, secure, wire-speed delivery of voice and data services to small offices. It has been specifically designed to meet the needs of carrier managed services applications for Small & Medium Businesses (SMBs) and Enterprise small branch offices. The OmniAccess 5510 ...
... purpose-built platform for simultaneous, secure, wire-speed delivery of voice and data services to small offices. It has been specifically designed to meet the needs of carrier managed services applications for Small & Medium Businesses (SMBs) and Enterprise small branch offices. The OmniAccess 5510 ...
Attacks to the IDS
... – Check process listing, local log files, system calls. – It is difficult for NIDS to associate packets to specific users (except when content switch-based NIDS is used!) and to determine if the commands in the packets violate specific user’s access privilege. ...
... – Check process listing, local log files, system calls. – It is difficult for NIDS to associate packets to specific users (except when content switch-based NIDS is used!) and to determine if the commands in the packets violate specific user’s access privilege. ...
(QoS)?
... Cant get QoS with a “free-for-all” Need to use new scheduling disciplines which provide “isolation” of performance from arrival rates of background traffic ...
... Cant get QoS with a “free-for-all” Need to use new scheduling disciplines which provide “isolation” of performance from arrival rates of background traffic ...
Networking 101 An Introduction to Networking
... As material is covered in the book, exam questions are inserted to show what the student should be learning. These exam questions appear throughout the book, together with acceptable answers. At the back of the book, Appendix A (page 310) is a Test Bank. It repeats these same questions that appeared ...
... As material is covered in the book, exam questions are inserted to show what the student should be learning. These exam questions appear throughout the book, together with acceptable answers. At the back of the book, Appendix A (page 310) is a Test Bank. It repeats these same questions that appeared ...
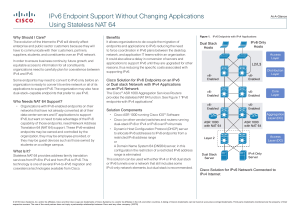
IPv6 Endpoint Support Without Changing Applications Using Stateless NAT 64
... site or campus can still provide access to and from the IPv4 Internet. One important restriction of this solution is that it requires each host in the IPv6 network that needs to communicate with the IPv4 Internet to have a routable IPv4 address at the Cisco ASR 1000, so it does not currently solve t ...
... site or campus can still provide access to and from the IPv4 Internet. One important restriction of this solution is that it requires each host in the IPv6 network that needs to communicate with the IPv4 Internet to have a routable IPv4 address at the Cisco ASR 1000, so it does not currently solve t ...
Administrator`s Handbook for the Motorola 3347
... DHCP Server functionality enables the Gateway to assign to your LAN computer(s) a “private” IP address and other parameters that allow network communication. The default DHCP Server configuration of the Gateway supports up to 253 LAN IP addresses. This feature simplifies network administration becau ...
... DHCP Server functionality enables the Gateway to assign to your LAN computer(s) a “private” IP address and other parameters that allow network communication. The default DHCP Server configuration of the Gateway supports up to 253 LAN IP addresses. This feature simplifies network administration becau ...
CS610 Final term MAGA file.. all paperz are in 1 file..pages 1 to 42
... We want to TX the binary data unit 1100001 Adding together the number of 1’s gives us 3, an odd number Before TX, we pass the data unit through a parity generator, which counts the 1’s and appends the parity bit (1) to the end The total number of 1’s is now 4, an even number The system now transfers ...
... We want to TX the binary data unit 1100001 Adding together the number of 1’s gives us 3, an odd number Before TX, we pass the data unit through a parity generator, which counts the 1’s and appends the parity bit (1) to the end The total number of 1’s is now 4, an even number The system now transfers ...
CISSP Guide to Security Essentials, Ch4
... – Even when there are intermediate devices such as routers and a variety of physical media between the nodes ...
... – Even when there are intermediate devices such as routers and a variety of physical media between the nodes ...
FRITZ!WLAN USB Stick AC 860
... Connecting Computers Directly (Ad Hoc Network) In a direct connection (also called an ad hoc network), computers are connected with each other without any wireless access point like the FRITZ!Box involved. If you set up an ad hoc network on a computer with the FRITZ!WLAN USB stick, other computers c ...
... Connecting Computers Directly (Ad Hoc Network) In a direct connection (also called an ad hoc network), computers are connected with each other without any wireless access point like the FRITZ!Box involved. If you set up an ad hoc network on a computer with the FRITZ!WLAN USB stick, other computers c ...
The Tenet Architecture for Tiered Sensor Networks
... sensor data fusion. In contrast to a mote-application-specific view of sensor networking, the principle constrains the processing of data received from multiple sensors to be placed at the master tier, regardless of whether that processing is specific to an application or can be expressed as a gener ...
... sensor data fusion. In contrast to a mote-application-specific view of sensor networking, the principle constrains the processing of data received from multiple sensors to be placed at the master tier, regardless of whether that processing is specific to an application or can be expressed as a gener ...
3346 Software User Guide V6.3
... Storage temperature: . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Relative storage humidity: . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Software and protocols . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Software media: . . . . . . . . . . . ...
... Storage temperature: . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Relative storage humidity: . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Software and protocols . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Software media: . . . . . . . . . . . ...
3. issues on ip multicast-based push - EECG Toronto
... Push technology stems from a very simple idea: rather than requiring users to explicitly request the information that they need, data can be sent to users without having them specifically ask for it. The advantages of push technology over the conventional pull technology are straightforward. The tra ...
... Push technology stems from a very simple idea: rather than requiring users to explicitly request the information that they need, data can be sent to users without having them specifically ask for it. The advantages of push technology over the conventional pull technology are straightforward. The tra ...
An Internet Architecture for the 21st Century – The SCION Internet
... computed faster than performing DRAM memory lookups, the packet-carried state design can enable higher packet processing speeds and simpler router architectures compared to today’s IP routers. Avoiding state on routers additionally prevents state-exhaustion attacks [27] and state inconsistencies. Ou ...
... computed faster than performing DRAM memory lookups, the packet-carried state design can enable higher packet processing speeds and simpler router architectures compared to today’s IP routers. Avoiding state on routers additionally prevents state-exhaustion attacks [27] and state inconsistencies. Ou ...
The Design and Performance of RIO -- a Real
... bound to any connection and are inactive until needed. Each kthread in RIO’s pool is associated with a queue. The queue links the various protocol modules in a STREAM. Each thread is assigned a particular rate, based on computations from TAO’s static scheduling service [1]. This rate corresponds to ...
... bound to any connection and are inactive until needed. Each kthread in RIO’s pool is associated with a queue. The queue links the various protocol modules in a STREAM. Each thread is assigned a particular rate, based on computations from TAO’s static scheduling service [1]. This rate corresponds to ...
Performance Enhancement of TFRC in Wireless Networks
... Gigabit Ethernet History In February 1997 the Gigabit Ethernet Alliance announced that IEEE802.3z Task Force met to review the first draft of the Gigabit Ethernet Standard. According to IDC by the end of 1997 85% of all network connections used Ethernet. Higher capacity Ethernet was appealing b ...
... Gigabit Ethernet History In February 1997 the Gigabit Ethernet Alliance announced that IEEE802.3z Task Force met to review the first draft of the Gigabit Ethernet Standard. According to IDC by the end of 1997 85% of all network connections used Ethernet. Higher capacity Ethernet was appealing b ...
Routing in IPv6 over Low-Power Wireless Personal Area Networks
... device enriched ability, operating system misbehavior, hardware problem, and power consumption by source. The link failure condition occurs in harsh environments, but in few condition, user desires the feedback after carrying out actions, routing protocols must cover within 2 seconds if the destinat ...
... device enriched ability, operating system misbehavior, hardware problem, and power consumption by source. The link failure condition occurs in harsh environments, but in few condition, user desires the feedback after carrying out actions, routing protocols must cover within 2 seconds if the destinat ...
ABLELink SW5002 Wireless Serial Server
... SW5002) transforms whatever data received from RS-232/RS-485 to TCP/UDP port then connects devices to the IP network via a single application program or multiple application programs. Many control devices provide the ability to communicate with hosts through RS-232/RS-485 however RS-232/RS-485 seria ...
... SW5002) transforms whatever data received from RS-232/RS-485 to TCP/UDP port then connects devices to the IP network via a single application program or multiple application programs. Many control devices provide the ability to communicate with hosts through RS-232/RS-485 however RS-232/RS-485 seria ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.