Chapter 1 - Introduction
... • RIP was among the first IGP used in the Internet • RIP has the following characteristics: • Routing within an AS – RIP is designed as an IGP to be used among routers within an AS ...
... • RIP was among the first IGP used in the Internet • RIP has the following characteristics: • Routing within an AS – RIP is designed as an IGP to be used among routers within an AS ...
Toward an IPv6 world in mobile networks – mechanisms
... Based on their experiences, office and home users can already rely entirely on an IPv6-only network. In terms of web browsers and e-mail clients, the volunteers observed no difference when comparing the IPv6-only experience with that offered by a dual-stack network. Software updates, operating syste ...
... Based on their experiences, office and home users can already rely entirely on an IPv6-only network. In terms of web browsers and e-mail clients, the volunteers observed no difference when comparing the IPv6-only experience with that offered by a dual-stack network. Software updates, operating syste ...
Objectives
... OSPFv3 protocol instances per link. In order to have two instances talk to each other, they need to have the same instance ID. By default it is 0, and for any additional instance it is increased. ...
... OSPFv3 protocol instances per link. In order to have two instances talk to each other, they need to have the same instance ID. By default it is 0, and for any additional instance it is increased. ...
Chapter 27 PPT
... • RIP was among the first IGP used in the Internet • RIP has the following characteristics: • Routing within an AS – RIP is designed as an IGP to be used among routers within an AS ...
... • RIP was among the first IGP used in the Internet • RIP has the following characteristics: • Routing within an AS – RIP is designed as an IGP to be used among routers within an AS ...
EQ-BGP: an efficient inter-domain QoS routing protocol
... The EQ-BGP is the extension of BGP-4 inter-domain routing protocol that fixes routing paths taking into account the QoS capabilities of particular domains. For that purpose, the border routers running EQ-BGP protocol, called EQ-BGP routers, advertise to their neighbours the information about reachab ...
... The EQ-BGP is the extension of BGP-4 inter-domain routing protocol that fixes routing paths taking into account the QoS capabilities of particular domains. For that purpose, the border routers running EQ-BGP protocol, called EQ-BGP routers, advertise to their neighbours the information about reachab ...
OneWireless R240.1 Release Notes
... OneWireless R240 Migration User's Guide – OWDOC-X258-en-240A The OneWireless R220 Migration User's Guide provides information about migrating from OneWireless R120.1 to R240.1 (i.e. proprietary to ISA100.11a compliant) and OneWireless R202.1 to R240.1 (i.e. previous to latest release). OneWireless E ...
... OneWireless R240 Migration User's Guide – OWDOC-X258-en-240A The OneWireless R220 Migration User's Guide provides information about migrating from OneWireless R120.1 to R240.1 (i.e. proprietary to ISA100.11a compliant) and OneWireless R202.1 to R240.1 (i.e. previous to latest release). OneWireless E ...
Network Load Balancing - Security Audit Systems
... Network Load Balancing is automatically installed and can be optionally enabled on the Advanced Server and Datacenter Server versions of the Windows 2000 operating system. It operates as an optional service for local area network (LAN) connections and can be enabled for one LAN connection in the sys ...
... Network Load Balancing is automatically installed and can be optionally enabled on the Advanced Server and Datacenter Server versions of the Windows 2000 operating system. It operates as an optional service for local area network (LAN) connections and can be enabled for one LAN connection in the sys ...
ch4
... • each “spoke” runs a (separate) Ethernet protocol (nodes do not collide with each other) ...
... • each “spoke” runs a (separate) Ethernet protocol (nodes do not collide with each other) ...
Presentation Local Area Network Technologies
... Local Area Network (LAN) Technologies To successfully troubleshoot Transmission Control Protocol/Internet Protocol (TCP/IP) problemson a local area network (LAN), it is important to understand how IP datagrams and Address Resolution Protocol (ARP) messages are encapsulated when sent by a computer r ...
... Local Area Network (LAN) Technologies To successfully troubleshoot Transmission Control Protocol/Internet Protocol (TCP/IP) problemson a local area network (LAN), it is important to understand how IP datagrams and Address Resolution Protocol (ARP) messages are encapsulated when sent by a computer r ...
PDF
... secure UMA and GAN traffic, where the subscriber has a UMA-capable mobile handset that communicates using a Wi-Fi access point over an untrusted network and back to the mobile operator’s data center. In addition, this gateway can be deployed to secure 3G and 4G base stations that are connected to th ...
... secure UMA and GAN traffic, where the subscriber has a UMA-capable mobile handset that communicates using a Wi-Fi access point over an untrusted network and back to the mobile operator’s data center. In addition, this gateway can be deployed to secure 3G and 4G base stations that are connected to th ...
An Experimenter`s Guide to OpenFlow
... • Useful for development, testing • Starting point for other implementations • Available under the OpenFlow License (BSD Style) at http://www.openflowswitch.org ...
... • Useful for development, testing • Starting point for other implementations • Available under the OpenFlow License (BSD Style) at http://www.openflowswitch.org ...
EdgeMarc 5300 Network Services Gateway
... VoIP call admission control Passive call quality monitoring (MOS, jitter, latency and more) DHCP server NAT/PAT Management: HTTP, HTTPS, SSH, Telnet, SNMPv1 and V3 ...
... VoIP call admission control Passive call quality monitoring (MOS, jitter, latency and more) DHCP server NAT/PAT Management: HTTP, HTTPS, SSH, Telnet, SNMPv1 and V3 ...
International Technical Support Organization High
... When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. Copyright International Business Machines Corporation 1992 1993 1995. All rights reserved. Note to U.S. Government ...
... When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. Copyright International Business Machines Corporation 1992 1993 1995. All rights reserved. Note to U.S. Government ...
Machine-to-Machine (M2M) Gateway: Trusted and Connected
... and I2C controllers allow direct connection to ZigBee®, Wi-Fi® and 2.5G/3G modem chipset ports or to local wired and wireless sensor networks. • Security: Trusted boot platform and integrated security engine have single pass encryption/ message authentication for common security protocols (e.g., IP ...
... and I2C controllers allow direct connection to ZigBee®, Wi-Fi® and 2.5G/3G modem chipset ports or to local wired and wireless sensor networks. • Security: Trusted boot platform and integrated security engine have single pass encryption/ message authentication for common security protocols (e.g., IP ...
COmpUter ANd iNFOrmAtiON SYStemS Natural and Appled Sciences Division Jamie Alonzo, Division Dean
... http://www.cabrillo.edu/programs ...
... http://www.cabrillo.edu/programs ...
Dell ™ PowerConnect ™ 28xx Systems
... same egress port resources. HOL blocking queues packets, and the packets at the head of the queue are forwarded before packets at the end of the queue. By default, the device is configured so that the HOL blocking prevention mechanism is active at all times, except when QoS (Quality of Service), Flo ...
... same egress port resources. HOL blocking queues packets, and the packets at the head of the queue are forwarded before packets at the end of the queue. By default, the device is configured so that the HOL blocking prevention mechanism is active at all times, except when QoS (Quality of Service), Flo ...
Ch03
... 3-1 WIRED LOCAL AREA NETWORKS A local area network (LAN) is a computer network that is designed for a limited geographic area such as a building or a campus. Although a LAN can be used as an isolated network to connect computers in an organization for the sole purpose of sharing resources, most LAN ...
... 3-1 WIRED LOCAL AREA NETWORKS A local area network (LAN) is a computer network that is designed for a limited geographic area such as a building or a campus. Although a LAN can be used as an isolated network to connect computers in an organization for the sole purpose of sharing resources, most LAN ...
How Ethernet becomes industrial
... office nor for the plant ! One standard solution for determinism and QoS issues (not yet ?) One standard solution for connecting in industrial environment (not yet ?) ...
... office nor for the plant ! One standard solution for determinism and QoS issues (not yet ?) One standard solution for connecting in industrial environment (not yet ?) ...
D_UCY_WP4_41_c2, Specification on E2E UMTS simulator
... One of SEACORN’s main objectives is to develop a high performance simulator for dynamic system level simulation and characterisation of Enhanced UMTS access and core networks. This simulator will enable the evaluation of capacity gain, Radio Resource Management (RRM) mechanisms, Quality of Service ( ...
... One of SEACORN’s main objectives is to develop a high performance simulator for dynamic system level simulation and characterisation of Enhanced UMTS access and core networks. This simulator will enable the evaluation of capacity gain, Radio Resource Management (RRM) mechanisms, Quality of Service ( ...
download
... EIGRP Concepts • Every EIGRP router maintains a topology table for each configured network protocol. • All learned routes to a destination are maintained in the topology table. ...
... EIGRP Concepts • Every EIGRP router maintains a topology table for each configured network protocol. • All learned routes to a destination are maintained in the topology table. ...
Tema 1: Tecnologías de red. - GRC
... Proposed Standard (PS) = kind of works Draft Standard (DS) = solid, interoperability tested (2 interoperable implementations for each feature), but not necessarily widely used Standard (S) = well tested, widely deployed ...
... Proposed Standard (PS) = kind of works Draft Standard (DS) = solid, interoperability tested (2 interoperable implementations for each feature), but not necessarily widely used Standard (S) = well tested, widely deployed ...
Web Page Configuration
... Try to avoid configuring modules using both config software and web pages unless absolutly necessary as some parameters of the configuration can become out of sync. It is recomened that if using Web page configuration it is for minor infield changes only. ...
... Try to avoid configuring modules using both config software and web pages unless absolutly necessary as some parameters of the configuration can become out of sync. It is recomened that if using Web page configuration it is for minor infield changes only. ...
here - FTP Directory Listing
... Networking protocol used on most computer networks to automate the management of IP address allocation Also provides other information about the network to ...
... Networking protocol used on most computer networks to automate the management of IP address allocation Also provides other information about the network to ...
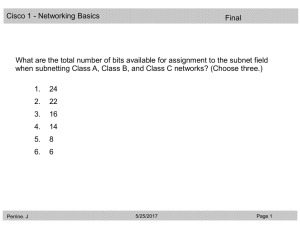
Q1 on FINAL
... The upper layer protocols will reconstruct the data from the damaged frame since most of the frame was transmitted before the collision and only the padding was damaged. ...
... The upper layer protocols will reconstruct the data from the damaged frame since most of the frame was transmitted before the collision and only the padding was damaged. ...
Multicast - Virginia Tech
... filtering (When interface told to receive frames destined to one specific Ethernet multicast address, it can receive frames destined to other Ethernet multicast addresses) Ethernet interface cards apply a hash function to group address, calculating a value between 0 and 511. This information turns ...
... filtering (When interface told to receive frames destined to one specific Ethernet multicast address, it can receive frames destined to other Ethernet multicast addresses) Ethernet interface cards apply a hash function to group address, calculating a value between 0 and 511. This information turns ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.