Activating an EVDO Wireless Card in a Cellular
... ❖ The MDN and MSID information will be displayed, meaning the activation was good. ❖ The system identification number (SID) and the network identification number (NID) might also be displayed. Note: After you configure the BANDIT device’s use of the wireless card, the BANDIT’s cellular statistics sh ...
... ❖ The MDN and MSID information will be displayed, meaning the activation was good. ❖ The system identification number (SID) and the network identification number (NID) might also be displayed. Note: After you configure the BANDIT device’s use of the wireless card, the BANDIT’s cellular statistics sh ...
N150 Wireless ADSL2+ Modem Router DGN1000 User
... The N150 Wireless ADSL2+ Modem Router DGN1000 provides you with an easy and secure way to set up a wireless home network with fast access to the Internet over a high-speed digital subscriber line (DSL). It has a built-in DSL modem, is compatible with all major DSL Internet service providers, lets yo ...
... The N150 Wireless ADSL2+ Modem Router DGN1000 provides you with an easy and secure way to set up a wireless home network with fast access to the Internet over a high-speed digital subscriber line (DSL). It has a built-in DSL modem, is compatible with all major DSL Internet service providers, lets yo ...
SwitchBlade® x908 [Rev ZJ]
... »» EPSRing (Ethernet Protection Switched Rings) with SuperLoop Protection (SLP) »» EPSR enhanced recovery for extra resiliency »» Loop protection: loop detection and thrash limiting ...
... »» EPSRing (Ethernet Protection Switched Rings) with SuperLoop Protection (SLP) »» EPSR enhanced recovery for extra resiliency »» Loop protection: loop detection and thrash limiting ...
Z2400 Series User`s Guide
... and walls. If the power cord is misused, a risk of fire or electrical shock results. Inspect the power cord regularly for signs of misuse. Remove the power cord from the electrical outlet before inspecting it. Refer service or repairs, other than those described in the user documentation, to a profe ...
... and walls. If the power cord is misused, a risk of fire or electrical shock results. Inspect the power cord regularly for signs of misuse. Remove the power cord from the electrical outlet before inspecting it. Refer service or repairs, other than those described in the user documentation, to a profe ...
N450 WiFi Cable Modem Router N450/CG2000Dv2 User Manual
... The modem router lets you access your network anywhere within the operating range of your wireless network. However, the operating distance or range of your wireless connection can vary significantly depending on the physical placement of your modem router. For example, the thickness and number of w ...
... The modem router lets you access your network anywhere within the operating range of your wireless network. However, the operating distance or range of your wireless connection can vary significantly depending on the physical placement of your modem router. For example, the thickness and number of w ...
Evaluating OpenFlow Controller Paradigms
... If the packet does not match any entry in the Flow Table, it will be sent to the Controller over a secure channel to ask for an action. Packets are matched against all flow entries based on some prioritization scheme. An entry with an exact match (no wildcards) has the highest priority. Optionally, ...
... If the packet does not match any entry in the Flow Table, it will be sent to the Controller over a secure channel to ask for an action. Packets are matched against all flow entries based on some prioritization scheme. An entry with an exact match (no wildcards) has the highest priority. Optionally, ...
ORAN: OpenFlow Routers for Academic Networks
... OpenFlow-enabled Gigabit Ethernet switch based on an ATCA industrial standard platform. Our work consists of an architectural design for introducing OpenFlow switch functionalities to the ATCA switching platform, design and development of an enhanced library for OpenFlow protocol stack, and porting ...
... OpenFlow-enabled Gigabit Ethernet switch based on an ATCA industrial standard platform. Our work consists of an architectural design for introducing OpenFlow switch functionalities to the ATCA switching platform, design and development of an enhanced library for OpenFlow protocol stack, and porting ...
User Guide Linksys E-Series Routers
... How to optimize your router for gaming and voice . . . . . . . . How to remotely change your router settings . . . . . . . . . . . How to enable Voice over IP on your network . . . . . . . . . . . How to configure UPnP . . . . . . . . . . . . . . . . . . ...
... How to optimize your router for gaming and voice . . . . . . . . How to remotely change your router settings . . . . . . . . . . . How to enable Voice over IP on your network . . . . . . . . . . . How to configure UPnP . . . . . . . . . . . . . . . . . . ...
Broadxent BritePort 8120 Manual
... this Agreement. You may use the Software for your personal use only, and not for public performance or for the creation of publicly displayed videotapes. 10.Decompiling, Disassembling, or Reverse Engineering You acknowledge that the Software contains trade secrets and other proprietary information o ...
... this Agreement. You may use the Software for your personal use only, and not for public performance or for the creation of publicly displayed videotapes. 10.Decompiling, Disassembling, or Reverse Engineering You acknowledge that the Software contains trade secrets and other proprietary information o ...
Exede WiFi Modem User Guide
... Although routers are great at allowing multiple devices to access the internet, please be aware that the devices are all still sharing a single internet connection. The more devices using the router at the same time, the less available bandwidth (speed) you’ll have. You’ll likely see data usage incr ...
... Although routers are great at allowing multiple devices to access the internet, please be aware that the devices are all still sharing a single internet connection. The more devices using the router at the same time, the less available bandwidth (speed) you’ll have. You’ll likely see data usage incr ...
Serial over Ethernet Device Server User`s Manual
... Serial over Ethernet Servers are designed to easily network your current serial devices. It provides a convenient and economical solution not only to protect your current hardware investment, but also to ensure future network expandability. With Serial over Ethernet Server, users can centralize seri ...
... Serial over Ethernet Servers are designed to easily network your current serial devices. It provides a convenient and economical solution not only to protect your current hardware investment, but also to ensure future network expandability. With Serial over Ethernet Server, users can centralize seri ...
PowerPoint - DePaul University
... But.. network solutions are *sigh* necessary TDC365 Spring 2001 ...
... But.. network solutions are *sigh* necessary TDC365 Spring 2001 ...
Aruba 2E Wired Access Point
... during all phases of installation and operation of the AP. Do not allow the Aruba 2E or optional power adapter (if used) to be connected to or make contact with metal or power outlets on a different electrical ground than the device to which it is connected. Also, never connect the AP to external st ...
... during all phases of installation and operation of the AP. Do not allow the Aruba 2E or optional power adapter (if used) to be connected to or make contact with metal or power outlets on a different electrical ground than the device to which it is connected. Also, never connect the AP to external st ...
Technical University Berlin Telecommunication Networks Group Optimization of Handover Performance
... the IP from the underlying technology and protocols may result in the development of a multitude of specific protocol stacks. This in turn will aggravate and hamper the application of heterogeneous all-IP wireless networks. An example for the usage of link-layer information are performance-enhancing ...
... the IP from the underlying technology and protocols may result in the development of a multitude of specific protocol stacks. This in turn will aggravate and hamper the application of heterogeneous all-IP wireless networks. An example for the usage of link-layer information are performance-enhancing ...
Product Description
... Clock/time source function ................................................................................. 73 Clock synchronization way for CES service ....................................................... 73 Security............................................................................... ...
... Clock/time source function ................................................................................. 73 Clock synchronization way for CES service ....................................................... 73 Security............................................................................... ...
Secure and Distributed Multicast Address Allocation on IPv6 Networks M. L. Slaviero
... Address allocation has been a limiting factor in the deployment of multicast solutions, and, as other multicast technologies advance, a general solution to this problem becomes more urgent. This study examines the current state of address allocation and finds impediments in many of the proposed solu ...
... Address allocation has been a limiting factor in the deployment of multicast solutions, and, as other multicast technologies advance, a general solution to this problem becomes more urgent. This study examines the current state of address allocation and finds impediments in many of the proposed solu ...
QFX10002 Fixed Ethernet Switches Product Description Data Sheet
... complete architectural flexibility. Additionally, the open architecture ensures that customers can innovate on top of Juniper Networks Junos® operating system to accelerate their pace of innovation. The QFX10000 switches also support Juniper Networks Junos Fusion architecture, a simple, easy-to-depl ...
... complete architectural flexibility. Additionally, the open architecture ensures that customers can innovate on top of Juniper Networks Junos® operating system to accelerate their pace of innovation. The QFX10000 switches also support Juniper Networks Junos Fusion architecture, a simple, easy-to-depl ...
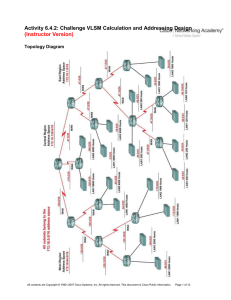
Ch05 ver 1.1
... private router to divide the network into four subnetworks. The rest of the Internet still sees only one network; internally the network is made of four subnetworks. Each subnetwork can now have almost 214 hosts. The network can belong to a university campus with four different schools (buildings). ...
... private router to divide the network into four subnetworks. The rest of the Internet still sees only one network; internally the network is made of four subnetworks. Each subnetwork can now have almost 214 hosts. The network can belong to a university campus with four different schools (buildings). ...
Forward-node-set-based broadcast in clustered mobile ad hoc
... protocols based on the nature of algorithms: probabilistic and deterministic. The locality of maintenance also plays an important role in evaluating the protocol. An important objective in designing a broadcast protocol is to reduce broadcast redundancy to save scarce resources such as energy and ba ...
... protocols based on the nature of algorithms: probabilistic and deterministic. The locality of maintenance also plays an important role in evaluating the protocol. An important objective in designing a broadcast protocol is to reduce broadcast redundancy to save scarce resources such as energy and ba ...
Chapter 6: The Transport Layer
... line is the normal path for a client. The heavy dashed line is the normal path for a server. The light lines are unusual events. Each transition is labeled by the event causing it and the action resulting from it, separated by a slash. ...
... line is the normal path for a client. The heavy dashed line is the normal path for a server. The light lines are unusual events. Each transition is labeled by the event causing it and the action resulting from it, separated by a slash. ...
Scap: Stream-Oriented Network Traffic Capture and
... discarding of uninteresting traffic, such as the tails of long-lived connections that belong to large file transfers, and (ii) it offers more control for tolerating packet loss under high load through stream priorities and best-effort reassembly. Scap also avoids the overhead of extra memory copies ...
... discarding of uninteresting traffic, such as the tails of long-lived connections that belong to large file transfers, and (ii) it offers more control for tolerating packet loss under high load through stream priorities and best-effort reassembly. Scap also avoids the overhead of extra memory copies ...
EMEA Technical Summit
... • Priority is relative and will be defined by who the user is and what business function they support • Allows the IT system to offer differing levels of information transport service based on differing business priorities ...
... • Priority is relative and will be defined by who the user is and what business function they support • Allows the IT system to offer differing levels of information transport service based on differing business priorities ...
Patch Management Integration November 11, 2014 (Revision 20)
... Package reporting is supported by RPM-based and Debian-based distributions that IBM TEM officially supports. This includes Red Hat derivatives such as RHEL, CentOS, Scientific Linux, and Oracle Linux, as well as Debian and Ubuntu. Other distributions may also work, but unless officially supported by ...
... Package reporting is supported by RPM-based and Debian-based distributions that IBM TEM officially supports. This includes Red Hat derivatives such as RHEL, CentOS, Scientific Linux, and Oracle Linux, as well as Debian and Ubuntu. Other distributions may also work, but unless officially supported by ...
Underlying Technologies
... 3-1 WIRED LOCAL AREA NETWORKS A local area network (LAN) is a computer network that is designed for a limited geographic area such as a building or a campus. Although a LAN can be used as an isolated network to connect computers in an organization for the sole purpose of sharing resources, most LAN ...
... 3-1 WIRED LOCAL AREA NETWORKS A local area network (LAN) is a computer network that is designed for a limited geographic area such as a building or a campus. Although a LAN can be used as an isolated network to connect computers in an organization for the sole purpose of sharing resources, most LAN ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.

![SwitchBlade® x908 [Rev ZJ]](http://s1.studyres.com/store/data/008053519_1-53b0e3770fa5647be537fdbf48703248-300x300.png)