Thesis Report
... v). Security: The radio environment is especially vulnerable to impersonation attacks so to ensure the wanted behavior of the routing protocol we need some sort of security measures. Authentication and encryption is the way to go and problem here lies within distributing the keys among the nodes in ...
... v). Security: The radio environment is especially vulnerable to impersonation attacks so to ensure the wanted behavior of the routing protocol we need some sort of security measures. Authentication and encryption is the way to go and problem here lies within distributing the keys among the nodes in ...
Random Early Detection Gateways for Congestion Avoidance
... drop probability. This is discussed as a rough initial implementation. Hashem [11] stresses that in future imple- Early descriptions of IP Source Quench messages sugmentations the drop level and the drop probability should gest that gateways could send Source Quench messages be adjusted dynamically, ...
... drop probability. This is discussed as a rough initial implementation. Hashem [11] stresses that in future imple- Early descriptions of IP Source Quench messages sugmentations the drop level and the drop probability should gest that gateways could send Source Quench messages be adjusted dynamically, ...
Prestige 645M
... This equipment has been tested and found to comply with the limits for a CLASS B digital device pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a commercial environment. This equipment generates, uses, and can radiate r ...
... This equipment has been tested and found to comply with the limits for a CLASS B digital device pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a commercial environment. This equipment generates, uses, and can radiate r ...
Wiley Publishing - CCNA For Dummies [2000].
... Segmenting a Network for Fun and Profit............................................................................................46 Reaping the benefits of segmentation............................................................................................47 Bridging the difference............ ...
... Segmenting a Network for Fun and Profit............................................................................................46 Reaping the benefits of segmentation............................................................................................47 Bridging the difference............ ...
PPT
... enough to tolerate additional delays due to link level retransmits. CMPE 257 Spring 2005 ...
... enough to tolerate additional delays due to link level retransmits. CMPE 257 Spring 2005 ...
Employing a secure Virtual Private Network (VPN)
... GHOSTNet is a secure and anonymous Virtual Private Network (VPN) service. Coupling Ethernet tunneling and proxy services to provide users safe and anonymous Internet access, GHOSTNet utilizes TLS (SSL) protocol with AES-256 encryption to secure the network along with PKI certificates and HMAC protec ...
... GHOSTNet is a secure and anonymous Virtual Private Network (VPN) service. Coupling Ethernet tunneling and proxy services to provide users safe and anonymous Internet access, GHOSTNet utilizes TLS (SSL) protocol with AES-256 encryption to secure the network along with PKI certificates and HMAC protec ...
Extensive Featured Switch for Small Businesses
... The ZyXEL GS1200-5HP and GS1200-8HP deliver PoE capabilities of IEEE 802.3at (30 watts/per port with total PoE power budget 60 watts) to supply power to PoE-capable network devices such as wireless and Bluetooth APs, IP cameras and IP phones. Web GUI management enables you to monitor power status of ...
... The ZyXEL GS1200-5HP and GS1200-8HP deliver PoE capabilities of IEEE 802.3at (30 watts/per port with total PoE power budget 60 watts) to supply power to PoE-capable network devices such as wireless and Bluetooth APs, IP cameras and IP phones. Web GUI management enables you to monitor power status of ...
Powerpoint
... – what the application layer “plugs into” – programmer cares about Application Programming Interface (API) End ...
... – what the application layer “plugs into” – programmer cares about Application Programming Interface (API) End ...
Exploration CCNA4 - Information Systems Technology
... provides status information about Frame Relay connections between the router (DTE) and the Frame Relay switch (DCE). –Every 10 seconds or so, the end device polls the network, either requesting a channel status information. –The figure shows the show frame-relay lmi command. ...
... provides status information about Frame Relay connections between the router (DTE) and the Frame Relay switch (DCE). –Every 10 seconds or so, the end device polls the network, either requesting a channel status information. –The figure shows the show frame-relay lmi command. ...
computer networks
... Each router must do the following: 1. Discover its neighbors, learn their network address. 2. Measure the delay or cost to each of its neighbors. 3. Construct a packet telling all it has just learned. 4. Send this packet to all other routers. 5. Compute the shortest path to every other router. ...
... Each router must do the following: 1. Discover its neighbors, learn their network address. 2. Measure the delay or cost to each of its neighbors. 3. Construct a packet telling all it has just learned. 4. Send this packet to all other routers. 5. Compute the shortest path to every other router. ...
coe041-451 LAN/MAN Performance
... rate S packets/slot or λ packet /s where S=λ* •Total arrivals of the process (new and retransmitted) have Poisson distribution with G packets/slot. •Stations have always one packet ready for transmission (new and retransmitted). •Bus end to end propagation delay is τ seconds. •A station knows about ...
... rate S packets/slot or λ packet /s where S=λ* •Total arrivals of the process (new and retransmitted) have Poisson distribution with G packets/slot. •Stations have always one packet ready for transmission (new and retransmitted). •Bus end to end propagation delay is τ seconds. •A station knows about ...
SanDevices E682 Pixel Controller with Version 4 Firmware Operating Manual
... The E682 is a single PC board, approximately 4” x 7”, the mounting hole pattern is compatible with the “new style” industry-standard Keptel or equivalent CG-1500 enclosure. DMX data input via the SACN protocol, also known as E1.31, or DMX over Ethernet, using a 100mb Ethernet connection. The E682 pr ...
... The E682 is a single PC board, approximately 4” x 7”, the mounting hole pattern is compatible with the “new style” industry-standard Keptel or equivalent CG-1500 enclosure. DMX data input via the SACN protocol, also known as E1.31, or DMX over Ethernet, using a 100mb Ethernet connection. The E682 pr ...
www.yorktech.com
... Less expensive than leased-line installations Can be used to connect to more than one location ...
... Less expensive than leased-line installations Can be used to connect to more than one location ...
snmpintro
... sent by agent to manager most important type is linkDown - interface crashed (e.g., router interface) common to have linkDown caught by some manager as part of trap/event analysis – HPOV can do this, or net-snmp trapd can be setup to do this – send page to network manager (human being) Jim Binkl ...
... sent by agent to manager most important type is linkDown - interface crashed (e.g., router interface) common to have linkDown caught by some manager as part of trap/event analysis – HPOV can do this, or net-snmp trapd can be setup to do this – send page to network manager (human being) Jim Binkl ...
DESIGN AND IMPLEMENTATION OF CONTENT SWITCH ON
... Testing local OpenSSL implementation on IXP ssldump ...
... Testing local OpenSSL implementation on IXP ssldump ...
Technical Report DSL Forum TR-059
... o Variable precedence arrangements – allowing some application’s traffic to take precedence over others. o Specific support for IP applications (e.g. IP-QoS and multicasting), o Support for new business models that can include more types of service providers, and o Support for these new service para ...
... o Variable precedence arrangements – allowing some application’s traffic to take precedence over others. o Specific support for IP applications (e.g. IP-QoS and multicasting), o Support for new business models that can include more types of service providers, and o Support for these new service para ...
Protection And Restoration In MPLS Networks
... determined by the initial label value. Such a path is called a Label Switched Path (LSP). MPLS may also be applied to data switching technologies that are not packet based. The path followed by data through the network is still defined by the transition of switching labels and so is still legitimate ...
... determined by the initial label value. Such a path is called a Label Switched Path (LSP). MPLS may also be applied to data switching technologies that are not packet based. The path followed by data through the network is still defined by the transition of switching labels and so is still legitimate ...
IPv6 Here and Now
... – Configures interface to receive addresses FF02::1, the all hosts group – Sends ICMP Solicitation Message (type 133) to FF02::2, the all routers group – the link layer address is embedded in the message – A router, if it exists, sends back an ICMP Router Advertisement message (type 134) ...
... – Configures interface to receive addresses FF02::1, the all hosts group – Sends ICMP Solicitation Message (type 133) to FF02::2, the all routers group – the link layer address is embedded in the message – A router, if it exists, sends back an ICMP Router Advertisement message (type 134) ...
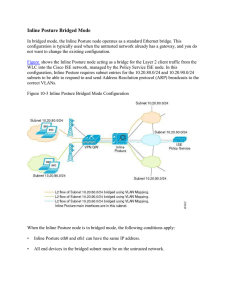
15360608-Inline Posture Bridged Mode
... Consider the following when configuring filters: • As typically implemented, Inline Posture enforces authentication requirements on endpoints that attempt to access the network. Device and subnet filters are used to validate or deny WLC and VPN devices. • For certain devices, you may want to bypass ...
... Consider the following when configuring filters: • As typically implemented, Inline Posture enforces authentication requirements on endpoints that attempt to access the network. Device and subnet filters are used to validate or deny WLC and VPN devices. • For certain devices, you may want to bypass ...
acba0bdb38899c8
... max. hop count value to avoid counting to infinity) and send its routing table to B after the periodic interval. - Before B sends its periodic update to C , router C sent its routing table to B containing a path to 10.0.0.0 with a better metric so B think that 10.0.0.0 can be reached by C while C de ...
... max. hop count value to avoid counting to infinity) and send its routing table to B after the periodic interval. - Before B sends its periodic update to C , router C sent its routing table to B containing a path to 10.0.0.0 with a better metric so B think that 10.0.0.0 can be reached by C while C de ...
Elektronischer Hšrsaal
... – TCP dominant, but does not satisfy Max-Min-fairness criterion! – Ack-clocked - flows with shorter RTT react sooner (slow start, ..) and achieve better results – Therefore, Internet definition of fairness: TCP-friendliness "A flow is TCP-compatible (TCP-friendly) if, in steady state, it uses no mor ...
... – TCP dominant, but does not satisfy Max-Min-fairness criterion! – Ack-clocked - flows with shorter RTT react sooner (slow start, ..) and achieve better results – Therefore, Internet definition of fairness: TCP-friendliness "A flow is TCP-compatible (TCP-friendly) if, in steady state, it uses no mor ...
Business Data Communications and Networking
... multicast is an old concept by Internet standards—compare with WWW & HTTP Jan 1992—the MBone, did not exist—in 1995, it made up 20% of all the Internet data bytes at one research lab—40% at another and more than 50% at yet another---but traffic overshadowed by Web soon after. ...
... multicast is an old concept by Internet standards—compare with WWW & HTTP Jan 1992—the MBone, did not exist—in 1995, it made up 20% of all the Internet data bytes at one research lab—40% at another and more than 50% at yet another---but traffic overshadowed by Web soon after. ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.


![Wiley Publishing - CCNA For Dummies [2000].](http://s1.studyres.com/store/data/008049680_1-a9b72081a3d6e4abe69a6bd824c30e5a-300x300.png)