Chapter 2
... the connection between an MS and the PDSN. In cdma2000, a PPP connection is equivalent to a packet data session, which is comparable to the UMTS PDP context. In the UMTS control plane, no PPP/IP connection is established between MS and SGSN. Signaling is carried over the RRC and ...
... the connection between an MS and the PDSN. In cdma2000, a PPP connection is equivalent to a packet data session, which is comparable to the UMTS PDP context. In the UMTS control plane, no PPP/IP connection is established between MS and SGSN. Signaling is carried over the RRC and ...
Software-Defined Internet Architecture
... requires that these are implemented in a way that is independent of how the interdomain task is implemented, but also that different domains can adopt different implementations of these intradomain tasks. To this end, we propose a “fabric-like” design as advocated in [5], which in turn was inspired ...
... requires that these are implemented in a way that is independent of how the interdomain task is implemented, but also that different domains can adopt different implementations of these intradomain tasks. To this end, we propose a “fabric-like” design as advocated in [5], which in turn was inspired ...
Chapter 4 slides
... Traffic Class: Similar idea to the type of service field in IPv4 Checksum: Does not exist in IPv6! It was removed entirely to reduce processing time at each hop Options: allowed, but outside of header, indicated by “Next Header” field ...
... Traffic Class: Similar idea to the type of service field in IPv4 Checksum: Does not exist in IPv6! It was removed entirely to reduce processing time at each hop Options: allowed, but outside of header, indicated by “Next Header” field ...
Chapter 4 Lecture Presentation
... Implement scheduler and test with other networks Create software tools to enable scientists and ISP/enterprise admins to visualize network topologies and request appropriate circuits/VCs High-BW, long-held: Therefore AAA is a must Path being pursued by DRAGON, USN, OSCARS, UCLP ...
... Implement scheduler and test with other networks Create software tools to enable scientists and ISP/enterprise admins to visualize network topologies and request appropriate circuits/VCs High-BW, long-held: Therefore AAA is a must Path being pursued by DRAGON, USN, OSCARS, UCLP ...
dizziness
... script tools to randomly generate large scale network config file import from and export to xml network config file Editing network nodes, ports, links export the xml config file for each node as to given xml schema ...
... script tools to randomly generate large scale network config file import from and export to xml network config file Editing network nodes, ports, links export the xml config file for each node as to given xml schema ...
Juniper Networks M-series : Product Overview
... that are designed to accelerate, extend, and optimize your highperformance networks. Our services allow you to maximize operational efficiency while reducing costs and minimizing risk, achieving a faster time to value for your network. Juniper Networks ensures operational excellence by optimizing th ...
... that are designed to accelerate, extend, and optimize your highperformance networks. Our services allow you to maximize operational efficiency while reducing costs and minimizing risk, achieving a faster time to value for your network. Juniper Networks ensures operational excellence by optimizing th ...
Chapter 21 PowerPoint Presentation
... Remote Authentication DialIn User Service (RADIUS) • RADIUS provides • Remote user authentication that is vendorindependent. • Scaleable authentication designs for performance. ...
... Remote Authentication DialIn User Service (RADIUS) • RADIUS provides • Remote user authentication that is vendorindependent. • Scaleable authentication designs for performance. ...
Next Generation Networks
... million lines will be deployed over the next 15-20 years There are more than 200 million wireless subscribers in the world today; an additional 700 million more will be added over the next 15-20 years There are more than 200 million Cable TV subscribers in the world today; an additional 300 mill ...
... million lines will be deployed over the next 15-20 years There are more than 200 million wireless subscribers in the world today; an additional 700 million more will be added over the next 15-20 years There are more than 200 million Cable TV subscribers in the world today; an additional 300 mill ...
MPLS networking at PSP Co Multi
... • Allow core routers/networking devices to switch packets based on some simplified header • Ultra fast forwarding • VPN ...
... • Allow core routers/networking devices to switch packets based on some simplified header • Ultra fast forwarding • VPN ...
Week #9
... In contrast, a hub connectivity diagram shows the hubs of your network, and how far they are from each other A more detailed version is the workstation connectivity diagram, which examines one segment (hub) and looks at the distances involved in its connections ...
... In contrast, a hub connectivity diagram shows the hubs of your network, and how far they are from each other A more detailed version is the workstation connectivity diagram, which examines one segment (hub) and looks at the distances involved in its connections ...
r02
... Approaches Towards Congestion Control • Two broad approaches towards congestion control: • End-end congestion control: • No explicit feedback from network • Congestion inferred from end-system observed loss, ...
... Approaches Towards Congestion Control • Two broad approaches towards congestion control: • End-end congestion control: • No explicit feedback from network • Congestion inferred from end-system observed loss, ...
Chapter 4 Routing Protocols
... that the depth of the device n is d and its address is A. This packet is for one of its descendants if the destination address Adest satisfies A < Adest < A+ Cskip(d − 1), and this packet will be relayed to the child router with address ...
... that the depth of the device n is d and its address is A. This packet is for one of its descendants if the destination address Adest satisfies A < Adest < A+ Cskip(d − 1), and this packet will be relayed to the child router with address ...
COS 420 day 17
... Cannot announce routes to networks from same interface you got route information from ...
... Cannot announce routes to networks from same interface you got route information from ...
Huawei AR3600 Series Agile Enterprise Gateway Datasheet
... The AR3600 series agile enterprise gateway provides strong openness and scalability, various applications, and centralized management. It can be deployed in schools. With the flexible and open X86 platform, the AR3600 can quickly integrate third-party application software, such as the teaching softwa ...
... The AR3600 series agile enterprise gateway provides strong openness and scalability, various applications, and centralized management. It can be deployed in schools. With the flexible and open X86 platform, the AR3600 can quickly integrate third-party application software, such as the teaching softwa ...
Fundamentals of Multimedia, Chapter 15
... • Packet Switching: used for almost all data networks in which data rates tend to be very much variable, and sometimes bursty. - Data is broken into small packets, usually of 1,000 bytes or less in length. The header of each packet will carry necessary control information such as destination address ...
... • Packet Switching: used for almost all data networks in which data rates tend to be very much variable, and sometimes bursty. - Data is broken into small packets, usually of 1,000 bytes or less in length. The header of each packet will carry necessary control information such as destination address ...
Running virtualized native drivers in User Mode Linux
... run multiple UML machines on different hosts. The simulation can therefore be distributed among multiple CPU’s. The TCP protocol has been chosen for its reliability. Indeed, it is not desirable to introduce uncertainty in the delivery of interrupt and data as one would like to control in a determini ...
... run multiple UML machines on different hosts. The simulation can therefore be distributed among multiple CPU’s. The TCP protocol has been chosen for its reliability. Indeed, it is not desirable to introduce uncertainty in the delivery of interrupt and data as one would like to control in a determini ...
Slides
... Networks are structured differently based (mostly) on distance between computers: Local area network (LAN) ▪ Small area: room or building ▪ Either wired (Cu or fiber) or wireless Wide area networks (WAN) ▪ Large area: more than 1 km ▪ Fiber-optic, copper transmission lines, μ-wave, satellite ...
... Networks are structured differently based (mostly) on distance between computers: Local area network (LAN) ▪ Small area: room or building ▪ Either wired (Cu or fiber) or wireless Wide area networks (WAN) ▪ Large area: more than 1 km ▪ Fiber-optic, copper transmission lines, μ-wave, satellite ...
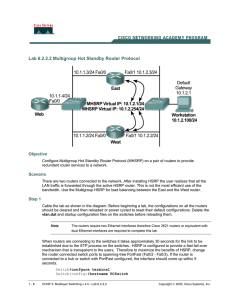
Lab 6.2.2.2 Multigroup Hot Standby Router Protocol
... If the ping does not work, go back and troubleshoot the configuration. Change the IP address of the workstation to another valid IP address (For example, 10.1.2.101) and then ping 10.1.1.4 again. Observe the lights on the routers and switch ports. Repeat this process several times using other valid ...
... If the ping does not work, go back and troubleshoot the configuration. Change the IP address of the workstation to another valid IP address (For example, 10.1.2.101) and then ping 10.1.1.4 again. Observe the lights on the routers and switch ports. Repeat this process several times using other valid ...
Computer Security and Penetration Testing Chapter 8 Session
... • Three ways of stopping a continuous ACK transfer: losing an ACK packet, ending the TCP connection, and resynchronizing the client and server • Packet blocking places the hacker in the actual flow of packets, solving the problem of the ACK transmission storm • TCP session hijacking with packet bloc ...
... • Three ways of stopping a continuous ACK transfer: losing an ACK packet, ending the TCP connection, and resynchronizing the client and server • Packet blocking places the hacker in the actual flow of packets, solving the problem of the ACK transmission storm • TCP session hijacking with packet bloc ...
Presentation
... individual end-to-end microflows to provide the QoS the service requires - connection setup Applications must specify the traffic characteristics of the microflow – token bucket model - rate and burst size specs. – flows are policed to ensure conformance ...
... individual end-to-end microflows to provide the QoS the service requires - connection setup Applications must specify the traffic characteristics of the microflow – token bucket model - rate and burst size specs. – flows are policed to ensure conformance ...
05. Reference Models and Example Networks
... • TCP/IP is based on five protocol layers instead of seven. The OSI model session and presentation layers can be considered empty in TCP/IP context. • TCP/IP stack with example protocols is shown below: ...
... • TCP/IP is based on five protocol layers instead of seven. The OSI model session and presentation layers can be considered empty in TCP/IP context. • TCP/IP stack with example protocols is shown below: ...
Data Security Standard (DSS) - PCI Security Standards Council
... units that can run with their own, distinct copy of the operating system and applications. Logical partitioning is typically used to allow the use of different operating systems and applications on a single device. The partitions may or may not be configured to communicate with each other or share s ...
... units that can run with their own, distinct copy of the operating system and applications. Logical partitioning is typically used to allow the use of different operating systems and applications on a single device. The partitions may or may not be configured to communicate with each other or share s ...
ppt - Suraj @ LUMS
... Packets are normally sent every 30sec If a route is not refreshed within 180 seconds, distance is set to infinity and later entry is removed ...
... Packets are normally sent every 30sec If a route is not refreshed within 180 seconds, distance is set to infinity and later entry is removed ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.