Courtesy Course Technology/Cengage Learning
... – Indicate to which VLAN each port belongs – Additional specifications • Security parameters, filtering instructions, port performance requirements, network addressing and management options ...
... – Indicate to which VLAN each port belongs – Additional specifications • Security parameters, filtering instructions, port performance requirements, network addressing and management options ...
IP Forwarding
... We know that one router, the default router, is connected to the rest of the Internet. But there is some missing information. We do not know if network 130.4.8.0 is directly connected to router R2 or through a point-to-point network (WAN) and another router. We do not know if network140.6.12.64 is c ...
... We know that one router, the default router, is connected to the rest of the Internet. But there is some missing information. We do not know if network 130.4.8.0 is directly connected to router R2 or through a point-to-point network (WAN) and another router. We do not know if network140.6.12.64 is c ...
Wireless Mesh Networks Challenges and Opportunities
... Nodes can use a control channel to coordinate and the rest to exchange data. In some conditions can be very efficient. However the control channel can be: an unacceptable ...
... Nodes can use a control channel to coordinate and the rest to exchange data. In some conditions can be very efficient. However the control channel can be: an unacceptable ...
csci5211: Computer Networks and Data Communications
... According to [Saltzer84]: “…sometimes an incomplete version of the function provided by the communication system (lower levels) may be useful as a performance enhancement…” ...
... According to [Saltzer84]: “…sometimes an incomplete version of the function provided by the communication system (lower levels) may be useful as a performance enhancement…” ...
Networking Technology - Sandhills Community College
... and management of network infrastructure technologies and network operating systems. Emphasis is placed on the implementation and management of network software and the implementation and management of hardware such as switches and routers. Graduates may find employment in entry-level jobs as local ...
... and management of network infrastructure technologies and network operating systems. Emphasis is placed on the implementation and management of network software and the implementation and management of hardware such as switches and routers. Graduates may find employment in entry-level jobs as local ...
atm98-786
... UNITE can potentially help by setting up the connection quickly – provide a VPI/VCI to allow transmission of data quickly ...
... UNITE can potentially help by setting up the connection quickly – provide a VPI/VCI to allow transmission of data quickly ...
Routing Information Protocol 2 (RIP2)
... RIP-2 supports generic notion of authentication, but only “password” is defined so far. Still not very secure. RIP2 packet size increases as the number of networks increases hence it is not suitable for large networks. RIP2 generates more protocol traffic than OSPF, because it propagates routing inf ...
... RIP-2 supports generic notion of authentication, but only “password” is defined so far. Still not very secure. RIP2 packet size increases as the number of networks increases hence it is not suitable for large networks. RIP2 generates more protocol traffic than OSPF, because it propagates routing inf ...
ip address - St. Xavier`s College
... as 255.255.255.255) sometimes called an 'all ones broadcast' ...
... as 255.255.255.255) sometimes called an 'all ones broadcast' ...
IP_Suite - Virginia Tech
... •Use a number of private (internal) addresses (home users and small businesses) when assigned ONE (or a small set) externally NAT router replaces source address in outgoing packets with global NAT address NAT router replaces destination address in incoming packets with appropriate private address ...
... •Use a number of private (internal) addresses (home users and small businesses) when assigned ONE (or a small set) externally NAT router replaces source address in outgoing packets with global NAT address NAT router replaces destination address in incoming packets with appropriate private address ...
RIP V2
... The Next Hop address is used to identify a better next-hop address - if one exists - than the address of the sending router. If the field is set to all zeros (0.0.0.0), the address of the sending router is the best next-hop address. The purpose of the Next Hop field is to eliminate packets bei ...
... The Next Hop address is used to identify a better next-hop address - if one exists - than the address of the sending router. If the field is set to all zeros (0.0.0.0), the address of the sending router is the best next-hop address. The purpose of the Next Hop field is to eliminate packets bei ...
PPT
... • Number of wireless Internet-connected devices equals number of wireline Internet-connected devices – Laptops, Internet-enabled phones promise anytime untethered Internet access ...
... • Number of wireless Internet-connected devices equals number of wireline Internet-connected devices – Laptops, Internet-enabled phones promise anytime untethered Internet access ...
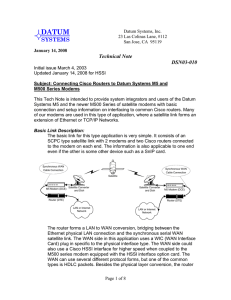
Tech Note - Datum Systems
... link was not correct, then the actual indication would be that the "Link" was down, while if the protocol was not correct then the indication would be that the Link is “Up” and the protocol is “Down”. The M500 series SnIP interface card running Linux can also be used on the other end of a link from ...
... link was not correct, then the actual indication would be that the "Link" was down, while if the protocol was not correct then the indication would be that the Link is “Up” and the protocol is “Down”. The M500 series SnIP interface card running Linux can also be used on the other end of a link from ...
Maestro2: A new challenge for high performance cluster network
... ters using off-the-shelf components especially for computation, there are also serious disadvantages especially when using conventional networking technology. Those conventional WAN or LAN-based network devices and protocols are not optimal for clusters, since they include overheads to guarantee rel ...
... ters using off-the-shelf components especially for computation, there are also serious disadvantages especially when using conventional networking technology. Those conventional WAN or LAN-based network devices and protocols are not optimal for clusters, since they include overheads to guarantee rel ...
TCP/IP Management
... system are communicating • Closed --- the connection has ended • Other states may be seen during a transition period • The ports( both remote and local) can use well-known names rather than a port number. These names are defined in the service table modified by the command WRKSRVTBLE ...
... system are communicating • Closed --- the connection has ended • Other states may be seen during a transition period • The ports( both remote and local) can use well-known names rather than a port number. These names are defined in the service table modified by the command WRKSRVTBLE ...
LESSON PLAN #67 Per. Name - Brooklyn Technical High School
... Assuming the following IP is not part of any subnet and is using classfull addressing, what is the network ID for the IP address 172.5.5.1? ...
... Assuming the following IP is not part of any subnet and is using classfull addressing, what is the network ID for the IP address 172.5.5.1? ...
Document
... Example 6.13 Figure 6.18 shows a simple example of searching in a routing table using the longest match algorithm. Although there are some more efficient algorithms today, the principle is the same. When the forwarding algorithm gets the destination address of the packet, it needs to delve into the ...
... Example 6.13 Figure 6.18 shows a simple example of searching in a routing table using the longest match algorithm. Although there are some more efficient algorithms today, the principle is the same. When the forwarding algorithm gets the destination address of the packet, it needs to delve into the ...
Networking
... Star Topology: The type of network topology in which each of the nodes of the network is connected to a central node with a point-to-point link in a 'hub' and 'spoke' fashion, the central node being the 'hub' and the nodes that are attached to the central node being the 'spokes' (e.g., a collection ...
... Star Topology: The type of network topology in which each of the nodes of the network is connected to a central node with a point-to-point link in a 'hub' and 'spoke' fashion, the central node being the 'hub' and the nodes that are attached to the central node being the 'spokes' (e.g., a collection ...
Multicasting in Mobile ad hoc networks
... Fast Handoff aims to reduce the handoff latency by using interaction between the radio and IP layers to detect the mobile movements. This can work only if the radio technology allows such interaction between layers.( its not solution for heterogenous wireless network) The packet loss during the hand ...
... Fast Handoff aims to reduce the handoff latency by using interaction between the radio and IP layers to detect the mobile movements. This can work only if the radio technology allows such interaction between layers.( its not solution for heterogenous wireless network) The packet loss during the hand ...
chapter4
... • The number of bits in the subnet mask determines the maximum number of hosts that can be on the subnet. • For example, a subnet mask of 24 bits means that the subnet can have at most 254 hosts (256 less 2 for reserved addresses). • This is because if we use 24 bits for the network address, that le ...
... • The number of bits in the subnet mask determines the maximum number of hosts that can be on the subnet. • For example, a subnet mask of 24 bits means that the subnet can have at most 254 hosts (256 less 2 for reserved addresses). • This is because if we use 24 bits for the network address, that le ...
CCNA Security
... • SNMP traps: Certain thresholds can be preconfigured. Events can be processed by the router and forwarded as SNMP traps to an external SNMP server. Requires the configuration and maintenance of an SNMP system. • Syslog: Configure routers to forward log messages to an external syslog service. This s ...
... • SNMP traps: Certain thresholds can be preconfigured. Events can be processed by the router and forwarded as SNMP traps to an external SNMP server. Requires the configuration and maintenance of an SNMP system. • Syslog: Configure routers to forward log messages to an external syslog service. This s ...
IP Forwarding (Ch 4) A Sample Network Examine IPv4 addresses:
... If I have > 256 hosts (no class C network) in a network and many networks like this, what do we do? Wasteful to have class B address for each S. Venkatesan Department of Computer Science 2010 ...
... If I have > 256 hosts (no class C network) in a network and many networks like this, what do we do? Wasteful to have class B address for each S. Venkatesan Department of Computer Science 2010 ...
Voip-tel - Smart Home Technology
... - Software release mangement For HiQ, HiE, HiG, IPUnity, TSM and AM - Interface between Siemens TAC2 and TAC3 service organizations ( TAC=Technical Assistance Centre level 2,3) - Development and execution of OA&M processes and procedures - Investigation of VoIP related network problems. - Incident e ...
... - Software release mangement For HiQ, HiE, HiG, IPUnity, TSM and AM - Interface between Siemens TAC2 and TAC3 service organizations ( TAC=Technical Assistance Centre level 2,3) - Development and execution of OA&M processes and procedures - Investigation of VoIP related network problems. - Incident e ...
Slide 1
... Efficient Hardware Integration and Isolation Complementary functionality (DMA, USART, etc) Selectable Power States (Off, Sleep, Standby) Operate at low voltages and low current Run to cut-off voltage of power source ...
... Efficient Hardware Integration and Isolation Complementary functionality (DMA, USART, etc) Selectable Power States (Off, Sleep, Standby) Operate at low voltages and low current Run to cut-off voltage of power source ...
Networking Designs
... center to a hub that contains the actual ring or bus. Linear-bus trunks connect the hubs in a star-bus, whereas the hubs in a star-ring are connected in a star pattern by the main hub. ...
... center to a hub that contains the actual ring or bus. Linear-bus trunks connect the hubs in a star-bus, whereas the hubs in a star-ring are connected in a star pattern by the main hub. ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.