Maintenance ST - Common Criteria
... This Security Target (ST) defines the scope of the evaluation in terms of the assumptions made, the intended environment for the Alcatel-Lucent 7-Series Service Router Operating System (SROS) Software Family, hereafter referred to generically as SROS, the Information Technology (IT) security functio ...
... This Security Target (ST) defines the scope of the evaluation in terms of the assumptions made, the intended environment for the Alcatel-Lucent 7-Series Service Router Operating System (SROS) Software Family, hereafter referred to generically as SROS, the Information Technology (IT) security functio ...
Cost_Calculation
... example, existing WR can be part of GSR (high end router) ? How close it to BTS (Config-2, call it “star”) Meshed Wireless Routers (Config-3, one wireless router per BTS, full mesh within the central office region. Call this “WR”) Meshed Wireless Routers (WR) and each WR connected to multiple Gatewa ...
... example, existing WR can be part of GSR (high end router) ? How close it to BTS (Config-2, call it “star”) Meshed Wireless Routers (Config-3, one wireless router per BTS, full mesh within the central office region. Call this “WR”) Meshed Wireless Routers (WR) and each WR connected to multiple Gatewa ...
SMART WIRELESS GATEWAY HART MANUAL
... hours a day, will assist you with any needed information or materials. The center will ask for product model and serial numbers, and will provide a Return Material Authorization (RMA) number. The center will also ask for the process material to which the product was last exposed. ...
... hours a day, will assist you with any needed information or materials. The center will ask for product model and serial numbers, and will provide a Return Material Authorization (RMA) number. The center will also ask for the process material to which the product was last exposed. ...
North American Global IPv6 Summit June 24
... Networks have a mix of private and public IP addresses Firewalls prevent end to end connectivity ...
... Networks have a mix of private and public IP addresses Firewalls prevent end to end connectivity ...
- TUCAA: The Ultimate Computer Acronyms Archive
... An entry in an Access Control List (ACL). An ACE contains a set of access rights and a security identifier (SID) that identifies a trustee for whom the rights are allowed, denied, or audited (Operating systems) ...
... An entry in an Access Control List (ACL). An ACE contains a set of access rights and a security identifier (SID) that identifies a trustee for whom the rights are allowed, denied, or audited (Operating systems) ...
- TUCAA: The Ultimate Computer Acronyms Archive
... An entry in an Access Control List (ACL). An ACE contains a set of access rights and a security identifier (SID) that identifies a trustee for whom the rights are allowed, denied, or audited (Operating systems) ...
... An entry in an Access Control List (ACL). An ACE contains a set of access rights and a security identifier (SID) that identifies a trustee for whom the rights are allowed, denied, or audited (Operating systems) ...
The Ultimate Computer Acronyms Archive
... so on. But he's little out of date: The father asks, "So should I get one with a DSP?" "A what?" says the son. You just can't get far if you're not up on the lingo. You might squeak by in your company of technological nonexperts, but even some of them will surprise you. These days, technical acronym ...
... so on. But he's little out of date: The father asks, "So should I get one with a DSP?" "A what?" says the son. You just can't get far if you're not up on the lingo. You might squeak by in your company of technological nonexperts, but even some of them will surprise you. These days, technical acronym ...
Name Resolution
... Provides an easy way for network administrators to provide IP addressing information for network clients Reduces the work associated with moving clients between subnets DHCP server service can be used to create a pool of IP addresses known as scopes that can be dynamically assigned to clients ...
... Provides an easy way for network administrators to provide IP addressing information for network clients Reduces the work associated with moving clients between subnets DHCP server service can be used to create a pool of IP addresses known as scopes that can be dynamically assigned to clients ...
Reputation based Trust in Service-Oriented Network Environments by
... (user application) layer, that is, the application layer. On the lower levels (and more specifically on the network routing level) there is a shortage of protection mechanisms. Most protection mechanisms on the network routing level are based on encryption [20, 51, 86]. Thus, routing devices are vul ...
... (user application) layer, that is, the application layer. On the lower levels (and more specifically on the network routing level) there is a shortage of protection mechanisms. Most protection mechanisms on the network routing level are based on encryption [20, 51, 86]. Thus, routing devices are vul ...
TUCAA: The Ultimate Computer Acronyms Archive
... so on. But he's little out of date: The father asks, "So should I get one with a DSP?" "A what?" says the son. You just can't get far if you're not up on the lingo. You might squeak by in your company of technological nonexperts, but even some of them will surprise you. These days, technical acronym ...
... so on. But he's little out of date: The father asks, "So should I get one with a DSP?" "A what?" says the son. You just can't get far if you're not up on the lingo. You might squeak by in your company of technological nonexperts, but even some of them will surprise you. These days, technical acronym ...
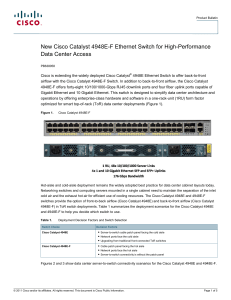
PDF
... Cisco IOS Software Cisco IOS Software is a proven network OS that offers best-in-class availability, manageability, and scalability. The Cisco Catalyst 4948E and 4948E-F support three levels of Cisco IOS Software. The basic level is LAN Base, developed for deployments that require data center-class ...
... Cisco IOS Software Cisco IOS Software is a proven network OS that offers best-in-class availability, manageability, and scalability. The Cisco Catalyst 4948E and 4948E-F support three levels of Cisco IOS Software. The basic level is LAN Base, developed for deployments that require data center-class ...
Magnum Network Software – DX
... This device complies with part 15 of the FCC Rules. Operation is subject to the following two conditions: (1) This device may not cause harmful interference, and (2) this device must accept any interference received, including interference that may cause undesired operation. Note: This equipment has ...
... This device complies with part 15 of the FCC Rules. Operation is subject to the following two conditions: (1) This device may not cause harmful interference, and (2) this device must accept any interference received, including interference that may cause undesired operation. Note: This equipment has ...
Intelligent WAN and WAN Design Summary (CVD) – October
... This guide provides a high level overview of several wide-area network (WAN) technologies, followed by a discussion of the usage of each technology at the WAN-aggregation site and remote sites. This guide should be used as a roadmap on how to use the companion Intelligent WAN (IWAN) and WAN deployme ...
... This guide provides a high level overview of several wide-area network (WAN) technologies, followed by a discussion of the usage of each technology at the WAN-aggregation site and remote sites. This guide should be used as a roadmap on how to use the companion Intelligent WAN (IWAN) and WAN deployme ...
20100810-OSG-NPW-Diagnostics
... perfSONAR-PS is an implementation of the perfSONAR measurement infrastructure and protocols written in the perl programming language All products are available as platform and architecture independent source code. All products are available as RPMs (e.g. RPM Package Manager). The perfSONAR-PS consor ...
... perfSONAR-PS is an implementation of the perfSONAR measurement infrastructure and protocols written in the perl programming language All products are available as platform and architecture independent source code. All products are available as RPMs (e.g. RPM Package Manager). The perfSONAR-PS consor ...
Lecture 5: Network Layer
... • Unless a network is well designed, it may experience a congestion collapse, in which performance plummets as the offered load increases beyond the capacity. • In a virtual-circuit net-work, new connections can be refused if they would cause the network to become congested. This is called admission ...
... • Unless a network is well designed, it may experience a congestion collapse, in which performance plummets as the offered load increases beyond the capacity. • In a virtual-circuit net-work, new connections can be refused if they would cause the network to become congested. This is called admission ...
Digi TransPort Release Notes 5.2.10.9
... 13. A problem with the DHCP server where Wi-Fi clients were not being issued IP addresses if the ‘Wi-Fi only’ configuration had been set. (SAROS-1399) 14. The ME909u-521 cellular (L1) module support has been updated to resolve a couple of issues related to the preferred system configuration. Firstly ...
... 13. A problem with the DHCP server where Wi-Fi clients were not being issued IP addresses if the ‘Wi-Fi only’ configuration had been set. (SAROS-1399) 14. The ME909u-521 cellular (L1) module support has been updated to resolve a couple of issues related to the preferred system configuration. Firstly ...
Module 1: Allocating IP Addressing by using Dynamic Host
... Relay agent forwards the DHCPDISCOVER message to the DHCP server Server sends a DHCPOFFER message to the DHCP relay agent Relay agent broadcasts the DHCPOFFER packet Client1 broadcasts a DHCPREQUEST packet ...
... Relay agent forwards the DHCPDISCOVER message to the DHCP server Server sends a DHCPOFFER message to the DHCP relay agent Relay agent broadcasts the DHCPOFFER packet Client1 broadcasts a DHCPREQUEST packet ...
Powerpoint Slides - Suraj @ LUMS
... uniformly distributed between 1 and 6 Call holding time is infinite 100 experiments with randomly selected ingress/egress pairs and traffic demands ...
... uniformly distributed between 1 and 6 Call holding time is infinite 100 experiments with randomly selected ingress/egress pairs and traffic demands ...
MA-ILT-Lesson-v4.2
... IP-EIGRP: Ext 172.69.43.0 255.255.255.0 metric 371200 - 256000 115200 IP-EIGRP: 192.135.246.0 255.255.255.0, - do advertise out Ethernet0/1 IP-EIGRP: Ext 192.135.246.0 255.255.255.0 metric 46310656 - 45714176 596480 IP-EIGRP: 172.69.40.0 255.255.255.0, - do advertise out Ethernet0/1 IP-EIGRP: Ext 17 ...
... IP-EIGRP: Ext 172.69.43.0 255.255.255.0 metric 371200 - 256000 115200 IP-EIGRP: 192.135.246.0 255.255.255.0, - do advertise out Ethernet0/1 IP-EIGRP: Ext 192.135.246.0 255.255.255.0 metric 46310656 - 45714176 596480 IP-EIGRP: 172.69.40.0 255.255.255.0, - do advertise out Ethernet0/1 IP-EIGRP: Ext 17 ...
TCP Fairness Issues
... – ECN must be supported by both TCP senders and receivers. – ECN-compliant TCP senders initiate their congestion avoidance algorithm after receiving marked ACK packets from the TCP receiver – A RED extension that marks packets to signal congestion ...
... – ECN must be supported by both TCP senders and receivers. – ECN-compliant TCP senders initiate their congestion avoidance algorithm after receiving marked ACK packets from the TCP receiver – A RED extension that marks packets to signal congestion ...
Route Optimization
... (Optional) Parameter used to specify the RIP seed metric for the redistributed route. When you are redistributing into RIP, this value is not specified and no value is specified using the defaultmetric router configuration command, then the default metric is 0, which is interpreted as infinity, and ...
... (Optional) Parameter used to specify the RIP seed metric for the redistributed route. When you are redistributing into RIP, this value is not specified and no value is specified using the defaultmetric router configuration command, then the default metric is 0, which is interpreted as infinity, and ...
D400 User Guide
... This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses and can radiate ...
... This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses and can radiate ...
User Manual Broadband Blaster DSL Ethernet/USB 8012U
... Software. Nor may you sub-license any of your rights under this Agreement. You may use the Software for your personal use only, and not for public performance or for the creation of publicly displayed videotapes. 10.Decompiling, Disassembling, or Reverse Engineering You acknowledge that the Software ...
... Software. Nor may you sub-license any of your rights under this Agreement. You may use the Software for your personal use only, and not for public performance or for the creation of publicly displayed videotapes. 10.Decompiling, Disassembling, or Reverse Engineering You acknowledge that the Software ...
Personal Area Networks: Bluetooth or IEEE 802.11? | SpringerLink
... Interconnecting all our electronic devices we carry around, such as cellular phones, PDAs, and laptops, with wireless links requires a cheap, low-power radio technology that still delivers good performance. In this context, the Bluetooth wireless technology was developed to meet the requirements int ...
... Interconnecting all our electronic devices we carry around, such as cellular phones, PDAs, and laptops, with wireless links requires a cheap, low-power radio technology that still delivers good performance. In this context, the Bluetooth wireless technology was developed to meet the requirements int ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.