Towards Automated Dynamic Analysis for Linux
... position that many of these devices occupy. For example, a wireless router is frequently the first and only line of defense between a user’s computing equipment (e.g., laptops, mobile phones, and tablets) and the Internet. An attacker that succeeds in compromising such a networking device is able to ...
... position that many of these devices occupy. For example, a wireless router is frequently the first and only line of defense between a user’s computing equipment (e.g., laptops, mobile phones, and tablets) and the Internet. An attacker that succeeds in compromising such a networking device is able to ...
Linux+ Guide to Linux Certification
... • Products being shipped must first be located then transferred to correct location and truck – Mistakes in inventory or inability to locate items can be devastating ...
... • Products being shipped must first be located then transferred to correct location and truck – Mistakes in inventory or inability to locate items can be devastating ...
PDF
... security guidelines, and also recommended aliases and general Cisco documents, see the monthly What’s New in Cisco Product Documentation, which also lists all new and revised Cisco technical documentation, at: http://www.cisco.com/en/US/docs/general/whatsnew/whatsnew.html CCDE, CCENT, Cisco Eos, Cis ...
... security guidelines, and also recommended aliases and general Cisco documents, see the monthly What’s New in Cisco Product Documentation, which also lists all new and revised Cisco technical documentation, at: http://www.cisco.com/en/US/docs/general/whatsnew/whatsnew.html CCDE, CCENT, Cisco Eos, Cis ...
Annex B – Routing Area Reorganization in IETF (as of Nov
... considered as part of the OTNT standardization work plan. The focus will be the transport and networking of digital client payloads over fibre optic cables. Though established optical transport mechanisms in transport plane (such as Synchronous Digital Hierarchy (SDH), Optical Transport Network (OTN ...
... considered as part of the OTNT standardization work plan. The focus will be the transport and networking of digital client payloads over fibre optic cables. Though established optical transport mechanisms in transport plane (such as Synchronous Digital Hierarchy (SDH), Optical Transport Network (OTN ...
6LoWPAN: The Wireless Embedded Internet
... For details of our global editorial offices, for customer services and for information about how to apply for permission to reuse the copyright material in this book please see our website at www.wiley.com. The right of the author to be identified as the author of this work has been asserted in acco ...
... For details of our global editorial offices, for customer services and for information about how to apply for permission to reuse the copyright material in this book please see our website at www.wiley.com. The right of the author to be identified as the author of this work has been asserted in acco ...
Manual - D-Link
... network or from the Internet. Support for WPA/WPA2 standards ensure that you’ll be able to use the best possible encryption method, regardless of your client devices. In addition, this router utilizes dual active firewalls (SPI and NAT) to prevent potential attacks from across the Internet. * Maximu ...
... network or from the Internet. Support for WPA/WPA2 standards ensure that you’ll be able to use the best possible encryption method, regardless of your client devices. In addition, this router utilizes dual active firewalls (SPI and NAT) to prevent potential attacks from across the Internet. * Maximu ...
Description
... The authentication feature is used in subscriber identification, authentication, and synchronization of the encryption key. This feature checks the validity of a subscriber's service requests to ensure that only legal subscribers can use network services. The authentication procedure is performed in ...
... The authentication feature is used in subscriber identification, authentication, and synchronization of the encryption key. This feature checks the validity of a subscriber's service requests to ensure that only legal subscribers can use network services. The authentication procedure is performed in ...
Design and Implementation of a Routing Control Platform Matthew Caesar Donald Caldwell
... all routers in the AS and provides this information to the RCS. The IGP Viewer must discover only the path costs between any two routers in the AS, but it need not discover the weights of each IGP edge. The RCS then uses these path costs to determine, from any router in the AS, what the closest egre ...
... all routers in the AS and provides this information to the RCS. The IGP Viewer must discover only the path costs between any two routers in the AS, but it need not discover the weights of each IGP edge. The RCS then uses these path costs to determine, from any router in the AS, what the closest egre ...
Extending AODV to enforce participation in a Mobile Ad
... We also make assumptions about the kind of selfish behavior a node can exhibit. One of the ways in which a selfish node can drop non-local data packets is by using a packet filtering personal firewall. Moreover, the selfish node can still send and receive its own data while exhibiting this selfish b ...
... We also make assumptions about the kind of selfish behavior a node can exhibit. One of the ways in which a selfish node can drop non-local data packets is by using a packet filtering personal firewall. Moreover, the selfish node can still send and receive its own data while exhibiting this selfish b ...
ITE PC v4.0 Chapter 1 - Chakarov - Ivailo Chakarov
... Unique local • Similar to private addresses for IPv4 • Used for local addressing within a site or between a limited number of sites • In the range of FC00::/7 to FDFF::/7 ...
... Unique local • Similar to private addresses for IPv4 • Used for local addressing within a site or between a limited number of sites • In the range of FC00::/7 to FDFF::/7 ...
Design and Implementation of a Routing Control Platform Matthew Caesar Donald Caldwell
... all routers in the AS and provides this information to the RCS. The IGP Viewer must discover only the path costs between any two routers in the AS, but it need not discover the weights of each IGP edge. The RCS then uses these path costs to determine, from any router in the AS, what the closest egre ...
... all routers in the AS and provides this information to the RCS. The IGP Viewer must discover only the path costs between any two routers in the AS, but it need not discover the weights of each IGP edge. The RCS then uses these path costs to determine, from any router in the AS, what the closest egre ...
Multicast_I
... •host informs its attached router that an application running on the host wants to join or leave a specific multicast group •another protocol is required to coordinate multicast routers throughout the Internet network layer multicast routing algorithms •Network layer multicast IGMP and multicast ...
... •host informs its attached router that an application running on the host wants to join or leave a specific multicast group •another protocol is required to coordinate multicast routers throughout the Internet network layer multicast routing algorithms •Network layer multicast IGMP and multicast ...
http://www.gratisexam.com/
... C. You should select a router to connect the two groups. When computers are in different subnets, as these two groups are, you will require a device that can make decisions based on IP addresses. Routers operate at layer 3 of the Open Systems Interconnect (OSI) model and make data-forwarding decisio ...
... C. You should select a router to connect the two groups. When computers are in different subnets, as these two groups are, you will require a device that can make decisions based on IP addresses. Routers operate at layer 3 of the Open Systems Interconnect (OSI) model and make data-forwarding decisio ...
HMC 840 Connectivity Security White Paper
... default route. When using this type of configuration on the Power HMC, the client can optionally use a second network card to physically separate the local system network from the Internet enabled network. For the DS8000, a second network card in the HMC is not supported. The preferred configuration ...
... default route. When using this type of configuration on the Power HMC, the client can optionally use a second network card to physically separate the local system network from the Internet enabled network. For the DS8000, a second network card in the HMC is not supported. The preferred configuration ...
System Architecture Definition and Specifications
... classification commands The actions are forwarded to DiffServ/MPLS Marking interface of the IMM, which applies them into the ingress router (i.e. LER 1) of the transport network, where the packet marking and traffic classification is performed ...
... classification commands The actions are forwarded to DiffServ/MPLS Marking interface of the IMM, which applies them into the ingress router (i.e. LER 1) of the transport network, where the packet marking and traffic classification is performed ...
User Guide Verizon FiOS®Router Model 9100EM
... home. Built around a state of the art, dual-core network processor, this versatile product helps ensure that data and services reach your connected home devices without interruption or delay. The Router allows you to transfer data over your existing in-home coax cables and simultaneously supports bo ...
... home. Built around a state of the art, dual-core network processor, this versatile product helps ensure that data and services reach your connected home devices without interruption or delay. The Router allows you to transfer data over your existing in-home coax cables and simultaneously supports bo ...
powerpoint - ARQoS - North Carolina State University
... Tracing Approach Classification • Host-based: – tracing based on information collected from each host ...
... Tracing Approach Classification • Host-based: – tracing based on information collected from each host ...
NPort 5600-8-DT/DTL Series User’s Manual Seventh Edition, February 2014 www.moxa.com/product
... The software described in this manual is furnished under a license agreement and may be used only in accordance with the terms of that agreement. ...
... The software described in this manual is furnished under a license agreement and may be used only in accordance with the terms of that agreement. ...
The Internet and Education
... “One to One” • An address destined for a single interface. • A packet sent to a unicast address is delivered to the interface identified by that address. “One to Many” • An address for a set of interfaces (typically belonging to different nodes). • A packet sent to a multicast address will be delive ...
... “One to One” • An address destined for a single interface. • A packet sent to a unicast address is delivered to the interface identified by that address. “One to Many” • An address for a set of interfaces (typically belonging to different nodes). • A packet sent to a multicast address will be delive ...
RoamAbout 802.11 Wireless Networking Guide
... Before calling Cabletron Systems, please have the following information ready: ...
... Before calling Cabletron Systems, please have the following information ready: ...
scratch
... Textbook describes Internet Port Addresses in terms of OSI’s “TSAP” concept • Your Instructor believes that this is confusing for those not familiar with OSI, even though these OSI concepts are helpful for a formal orientation. • This instructor-inserted slide seeks to summarize pgs 509-512 and 554 ...
... Textbook describes Internet Port Addresses in terms of OSI’s “TSAP” concept • Your Instructor believes that this is confusing for those not familiar with OSI, even though these OSI concepts are helpful for a formal orientation. • This instructor-inserted slide seeks to summarize pgs 509-512 and 554 ...
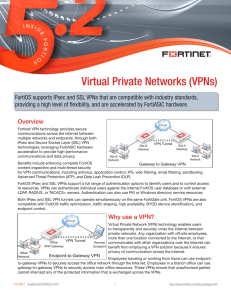
Virtual Private Networks (VPNs)
... protocol required for many applications and is almost never blocked. SSL VPN is the best solution for endpoint-to-gateway VPNs. Remote users can securely log into the SSL VPN web portal from any endpoint running a web browser that supports HTTPS, which could include PCs, tablets, and mobile devices. ...
... protocol required for many applications and is almost never blocked. SSL VPN is the best solution for endpoint-to-gateway VPNs. Remote users can securely log into the SSL VPN web portal from any endpoint running a web browser that supports HTTPS, which could include PCs, tablets, and mobile devices. ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.