Virtual Private Networks (VPNs)
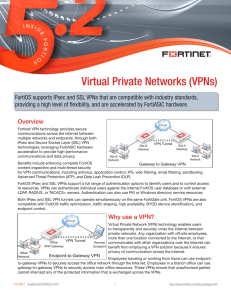
... protocol required for many applications and is almost never blocked. SSL VPN is the best solution for endpoint-to-gateway VPNs. Remote users can securely log into the SSL VPN web portal from any endpoint running a web browser that supports HTTPS, which could include PCs, tablets, and mobile devices. ...
... protocol required for many applications and is almost never blocked. SSL VPN is the best solution for endpoint-to-gateway VPNs. Remote users can securely log into the SSL VPN web portal from any endpoint running a web browser that supports HTTPS, which could include PCs, tablets, and mobile devices. ...
IPsec - Allied Telesis
... trying to go into the tunnel is accepted and encrypted. This means it may be necessary to create multiple SAs within the tunnel, so that different streams of traffic within the tunnel are encrypted by different SAs. The latter case is necessitated by connections with some legacy devices that may not ...
... trying to go into the tunnel is accepted and encrypted. This means it may be necessary to create multiple SAs within the tunnel, so that different streams of traffic within the tunnel are encrypted by different SAs. The latter case is necessitated by connections with some legacy devices that may not ...
Command Line Interface Guide
... This guide is intended to help you configure and manage the router using the Command Line Interface. The guide assumes that you have read the information about the router and installed the hardware using the Internet Quick Start Guide. The guide is divided into eight parts: Introduction. Describes t ...
... This guide is intended to help you configure and manage the router using the Command Line Interface. The guide assumes that you have read the information about the router and installed the hardware using the Internet Quick Start Guide. The guide is divided into eight parts: Introduction. Describes t ...
Vipersat CDM-570/570L
... notification of such revision. Comtech periodically revises and improves its products and, therefore, the information in this document is subject to change without prior notice. Comtech makes no warranty of any kind with regard to this material, including but not limited to the implied warranties of ...
... notification of such revision. Comtech periodically revises and improves its products and, therefore, the information in this document is subject to change without prior notice. Comtech makes no warranty of any kind with regard to this material, including but not limited to the implied warranties of ...
CN 2015 1-2 - DSpace
... Hybrid networks use a combination of any two or more topologies in such a way that the resulting network does not exhibit one of the standard topologies ...
... Hybrid networks use a combination of any two or more topologies in such a way that the resulting network does not exhibit one of the standard topologies ...
TRANSITION FROM IPv4 TO IPv6 LAHTI UNIVERSITY OF APPLIED
... be affected is internet service providers (ISPs), large enterprises, companies, etc. The reason is that they hold the most number of IPv4 for operation and management and before the IPv4 runs out, they will need an appropriate act to handle the exhaustion, and otherwise, the collapse of the worldwid ...
... be affected is internet service providers (ISPs), large enterprises, companies, etc. The reason is that they hold the most number of IPv4 for operation and management and before the IPv4 runs out, they will need an appropriate act to handle the exhaustion, and otherwise, the collapse of the worldwid ...
2. Principles governing the use of TCP/IP on the GTS
... less a series of bilateral links. Such a strategy could be pursued but the emergence of the Internet and TCP/IP networking offers an alternative that appears much more attractive, particularly for non MSS requirements. The evolution of the GTS to adopt TCP/IP is now appropriate because: it has bec ...
... less a series of bilateral links. Such a strategy could be pursued but the emergence of the Internet and TCP/IP networking offers an alternative that appears much more attractive, particularly for non MSS requirements. The evolution of the GTS to adopt TCP/IP is now appropriate because: it has bec ...
Universal WiFi Range Extender WN3000RP
... 1. The Extender connects to a wireless network that is up and running. When the Extender connects wirelessly to a network, it acts as a network client. This is similar to how a computer connects to a network. 2. The Extender acts as an access point for computers. The Extender has its own wireless ne ...
... 1. The Extender connects to a wireless network that is up and running. When the Extender connects wirelessly to a network, it acts as a network client. This is similar to how a computer connects to a network. 2. The Extender acts as an access point for computers. The Extender has its own wireless ne ...
Using Switches with a PS Series Group
... A PS Series storage array automatically supports standard Ethernet frames and Jumbo Frames up to 9000 bytes (9018 including the TCP header itself). (This is sometimes referred to as the “Alteon standard.”) PS Series storage arrays also support path MTU, which is the ability to automatically detect t ...
... A PS Series storage array automatically supports standard Ethernet frames and Jumbo Frames up to 9000 bytes (9018 including the TCP header itself). (This is sometimes referred to as the “Alteon standard.”) PS Series storage arrays also support path MTU, which is the ability to automatically detect t ...
Unix System Administration
... • Source and stateful routing and failover functions Route traffic more efficiant and faster than regular IP routers. ...
... • Source and stateful routing and failover functions Route traffic more efficiant and faster than regular IP routers. ...
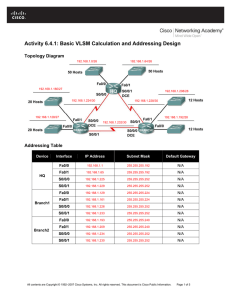
Activity 6.4.1: Basic VLSM Calculation and Addressing Design
... 4. What is the maximum number of host IP addresses that are needed for a single subnet? _______ 5. What is the least number of host IP addresses that are needed for a single subnet? _______ 6. How many IP addresses are needed for the East portion of the network? Be sure to include the WAN links betw ...
... 4. What is the maximum number of host IP addresses that are needed for a single subnet? _______ 5. What is the least number of host IP addresses that are needed for a single subnet? _______ 6. How many IP addresses are needed for the East portion of the network? Be sure to include the WAN links betw ...
Cisco RV180/RV180W Administration Guide
... WAN LED—The WAN (Internet) LED lights up green when the device is connected to your cable or DSL modem. The LED flashes green when the device is sending or receiving data over the WAN port. WIRELESS—The Wireless LED lights up green when the wireless module is enabled by the Device Manager. The LED i ...
... WAN LED—The WAN (Internet) LED lights up green when the device is connected to your cable or DSL modem. The LED flashes green when the device is sending or receiving data over the WAN port. WIRELESS—The Wireless LED lights up green when the wireless module is enabled by the Device Manager. The LED i ...
Ch 11-OSPF
... –Purpose is to encrypt & authenticate routing information –This is an interface specific configuration –Routers will only accept routing information from other routers that have been configured with the same password or authentication information ...
... –Purpose is to encrypt & authenticate routing information –This is an interface specific configuration –Routers will only accept routing information from other routers that have been configured with the same password or authentication information ...
bgp2
... – In comparing two or more different routes, given that all other attributes are identical, a shorter path is always preferred. – In case of a tie in AS_PATH length, other attributes are used to make the decision. (later) Private AS numbers cannot be leaked to the Internet because they are not uniqu ...
... – In comparing two or more different routes, given that all other attributes are identical, a shorter path is always preferred. – In case of a tie in AS_PATH length, other attributes are used to make the decision. (later) Private AS numbers cannot be leaked to the Internet because they are not uniqu ...
Wireless Security
... do not specify an SSID in their configurations, you can set up a guest SSID. • The access point includes the guest SSID in its beacon. • By default, the access point's default SSID, tsunami, is set to guest mode. • However, to keep your network secure, you should disable the guest mode SSID on most ...
... do not specify an SSID in their configurations, you can set up a guest SSID. • The access point includes the guest SSID in its beacon. • By default, the access point's default SSID, tsunami, is set to guest mode. • However, to keep your network secure, you should disable the guest mode SSID on most ...
1769-SG001 - Literature Library
... The CompactLogix 5380 controllers are the first Logix controllers to offer configurable EtherNet/IP modes, that is, Dual-IP mode or Linear/DLR mode. With CompactLogix 5380 controller firmware revision 29.011 or later, you can configure the embedded Ethernet ports to connect to separate networks, an ...
... The CompactLogix 5380 controllers are the first Logix controllers to offer configurable EtherNet/IP modes, that is, Dual-IP mode or Linear/DLR mode. With CompactLogix 5380 controller firmware revision 29.011 or later, you can configure the embedded Ethernet ports to connect to separate networks, an ...
Steps for Configuring the IPv6 Test Lab - TechNet Gallery
... utility the size of today’s Internet. However, on today’s Internet, IPv4 has the following disadvantages: ...
... utility the size of today’s Internet. However, on today’s Internet, IPv4 has the following disadvantages: ...
Wireless sensor network monitoring using the Simple Network
... The research done offers a glimpse into the possibilities that an SNMP enabled 6LoWPAN WSN hold. It does so without having to do modifications to the 6LoWPAN stack used and also without the need for a translation gateway. The SNMPv1 software agent using blip in TinyOS is also one of the first such i ...
... The research done offers a glimpse into the possibilities that an SNMP enabled 6LoWPAN WSN hold. It does so without having to do modifications to the 6LoWPAN stack used and also without the need for a translation gateway. The SNMPv1 software agent using blip in TinyOS is also one of the first such i ...
... for end users and devices spread over a single floor or building. A campus network is created by interconnecting a group of LANs that are spread over a small geographic area. Campus network design concepts are inclusive small networks that use a single LAN switch up to very large networks with thous ...
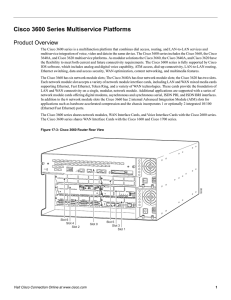
Cisco 3600 Series Multiservice Platforms
... The Cisco 3600 series is a multifunction platform that combines dial access, routing, and LAN-to-LAN services and multiservice integration of voice, video and data in the same device. The Cisco 3600 series includes the Cisco 3660, the Cisco 3640A, and Cisco 3620 multiservice platforms. As modular so ...
... The Cisco 3600 series is a multifunction platform that combines dial access, routing, and LAN-to-LAN services and multiservice integration of voice, video and data in the same device. The Cisco 3600 series includes the Cisco 3660, the Cisco 3640A, and Cisco 3620 multiservice platforms. As modular so ...
Cisco IP SLA`s
... • VoIP may be difficult to deploy when the network behavior is not well understood Cisco IOS IP SLAs will verify network readiness and QoS Measure critical performance for VoIP deployment Real time warning of network performance degradation IP SLA is universally available across Cisco IOS Software ...
... • VoIP may be difficult to deploy when the network behavior is not well understood Cisco IOS IP SLAs will verify network readiness and QoS Measure critical performance for VoIP deployment Real time warning of network performance degradation IP SLA is universally available across Cisco IOS Software ...
Cost_Calculation
... example, existing WR can be part of GSR (high end router) ? How close it to BTS (Config-2, call it “star”) Meshed Wireless Routers (Config-3, one wireless router per BTS, full mesh within the central office region. Call this “WR”) Meshed Wireless Routers (WR) and each WR connected to multiple Gatewa ...
... example, existing WR can be part of GSR (high end router) ? How close it to BTS (Config-2, call it “star”) Meshed Wireless Routers (Config-3, one wireless router per BTS, full mesh within the central office region. Call this “WR”) Meshed Wireless Routers (WR) and each WR connected to multiple Gatewa ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.