Network+ Guide to Networks 6th Edition
... Figure 8-16 Home or small office WLAN arrangement Courtesy Course Technology/Cengage Learning Network+ Guide to Networks, 6th Edition ...
... Figure 8-16 Home or small office WLAN arrangement Courtesy Course Technology/Cengage Learning Network+ Guide to Networks, 6th Edition ...
VoIP (1)
... public networks Focus on scalability, network control, support for traditional phones, sophisticated gateway (GW) to the PSTN and its services Media GW interfaces voice stream to PSTN trunk or phone line Signaling GW allows signaling directly to SS7 network Softswitch controls Media GWs and ...
... public networks Focus on scalability, network control, support for traditional phones, sophisticated gateway (GW) to the PSTN and its services Media GW interfaces voice stream to PSTN trunk or phone line Signaling GW allows signaling directly to SS7 network Softswitch controls Media GWs and ...
Networking innovations for HPE ProLiant Gen9 servers
... traffic. This effectively eliminates the need for the CPU to segment and reassemble network data packets. Eliminating this work significantly increases the application performance of servers attached to Gigabit Ethernet networks. TOE is included on integrated Multifunction Gigabit Ethernet adapters ...
... traffic. This effectively eliminates the need for the CPU to segment and reassemble network data packets. Eliminating this work significantly increases the application performance of servers attached to Gigabit Ethernet networks. TOE is included on integrated Multifunction Gigabit Ethernet adapters ...
ex2-6 - wmmhicks.com
... You can “subnet the subnets” and have different sizes of subnet. Fit the addressing requirements better into the address space – less space needed. 25-May-17 ...
... You can “subnet the subnets” and have different sizes of subnet. Fit the addressing requirements better into the address space – less space needed. 25-May-17 ...
Routing Information Protocol (RIP)
... horizon and poison reverse where node B can still advertise the value of X, but if the source of information is A, it can replace the distance with infinity as a warning: “Don’t use this value; what I know about this route comes from you.” ...
... horizon and poison reverse where node B can still advertise the value of X, but if the source of information is A, it can replace the distance with infinity as a warning: “Don’t use this value; what I know about this route comes from you.” ...
Lecture-6 on 10/13/2009
... • r->ts: the timestamp from the incoming packet • arrival: the current time in the same units • s->transit: holds the relative transit time for the previous packet • s->jitter : holds the estimated jitter ...
... • r->ts: the timestamp from the incoming packet • arrival: the current time in the same units • s->transit: holds the relative transit time for the previous packet • s->jitter : holds the estimated jitter ...
Chen-WPC10-slide
... “IP multicast is a technique for one-to-many communication over an IP infrastructure in a network. It scales to a larger receiver population by not requiring prior knowledge of who or how many receivers there are. Multicast uses network infrastructure efficiently by requiring the source to send a pa ...
... “IP multicast is a technique for one-to-many communication over an IP infrastructure in a network. It scales to a larger receiver population by not requiring prior knowledge of who or how many receivers there are. Multicast uses network infrastructure efficiently by requiring the source to send a pa ...
Q1 on Ch08 Ethernet Switching
... transfers. Mary investigates the problem and notices that her co-worker John has been hosting an online video conference. What is the network probably experiencing? ...
... transfers. Mary investigates the problem and notices that her co-worker John has been hosting an online video conference. What is the network probably experiencing? ...
NFX250 Network Services Platform
... The NFX250 improves the overall cost efficiency of the CloudEnabled Branch and managed services with Cloud CPE. CapEx efficiency is enhanced where a single and scalable NFX250 replaces multiple on-premise devices. OpEx efficiency is achieved through automation, which simplifies operations and elimin ...
... The NFX250 improves the overall cost efficiency of the CloudEnabled Branch and managed services with Cloud CPE. CapEx efficiency is enhanced where a single and scalable NFX250 replaces multiple on-premise devices. OpEx efficiency is achieved through automation, which simplifies operations and elimin ...
ppt
... • Every network in a TCP/IP internet is assigned a unique network number. • Each host on a specific network is assigned a host address that is unique within that network. • Host’s IP address is the combination of the network number (prefix) and host address (suffix). • Assignment of network numbers ...
... • Every network in a TCP/IP internet is assigned a unique network number. • Each host on a specific network is assigned a host address that is unique within that network. • Host’s IP address is the combination of the network number (prefix) and host address (suffix). • Assignment of network numbers ...
Manual AV200-WME F-EU-ENG-May 31-07.indd
... In order to access the web-based configuration pages, it is necessary to know the adapter’s IP address and for your computer to be connected to the wall mount adapter (as described in section 2.5). Corinex adapters come with a default IP address 10.10.1.69. Open a web browser (Microsoft Internet Exp ...
... In order to access the web-based configuration pages, it is necessary to know the adapter’s IP address and for your computer to be connected to the wall mount adapter (as described in section 2.5). Corinex adapters come with a default IP address 10.10.1.69. Open a web browser (Microsoft Internet Exp ...
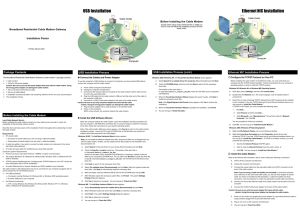
Ethernet NIC Installation USB Installation
... C. Connect the RF coaxial cable (not included) to the cable modem’s CATV cable connector and to the wall cable outlet. D. Plug the USB cable into the cable modem’s USB port and the other end of the cable to the computer’s USB port. E. Connect the 12VDC/1.25A power adapter to the back of the cable mo ...
... C. Connect the RF coaxial cable (not included) to the cable modem’s CATV cable connector and to the wall cable outlet. D. Plug the USB cable into the cable modem’s USB port and the other end of the cable to the computer’s USB port. E. Connect the 12VDC/1.25A power adapter to the back of the cable mo ...
product catalog 02-17 v1 - SM
... infrastructure, the activities to be carried out will depend on the network state, the products deployed, type of services running and new services to be introduced. The first step is to consolidate the existing infrstructure resulting in a solid transport network to base the future innovation on. M ...
... infrastructure, the activities to be carried out will depend on the network state, the products deployed, type of services running and new services to be introduced. The first step is to consolidate the existing infrstructure resulting in a solid transport network to base the future innovation on. M ...
All mesh networks are not created equal
... In contrast to AMI that is typically based on a multi-hop repeater network architecture, many metro-scale and enterprise infrastructure applications have requirements that can be better characterized as ubiquitous wireless broadband. Applications such as public safety and mobile workforce automation ...
... In contrast to AMI that is typically based on a multi-hop repeater network architecture, many metro-scale and enterprise infrastructure applications have requirements that can be better characterized as ubiquitous wireless broadband. Applications such as public safety and mobile workforce automation ...
Link Layer
... 7 bytes with pattern 10101010 followed by one byte with pattern 10101011 used to synchronize receiver, sender clock rates ...
... 7 bytes with pattern 10101010 followed by one byte with pattern 10101011 used to synchronize receiver, sender clock rates ...
Link Layer
... EDC= Error Detection and Correction bits (redundancy) D = Data protected by error checking, may include header fields • Error detection not 100% reliable! • protocol may miss some errors, but rarely • larger EDC field yields better detection and correction ...
... EDC= Error Detection and Correction bits (redundancy) D = Data protected by error checking, may include header fields • Error detection not 100% reliable! • protocol may miss some errors, but rarely • larger EDC field yields better detection and correction ...
Chapter 6 Configuring, Monitoring & Troubleshooting IPsec
... Windows supports 3 network types : Domain: selected when the computer is a domain member Private: networks trusted by the user (home or small office network) Public: default for newly detected networks, usually the most restrictive settings are assigned because of the security risks present on publi ...
... Windows supports 3 network types : Domain: selected when the computer is a domain member Private: networks trusted by the user (home or small office network) Public: default for newly detected networks, usually the most restrictive settings are assigned because of the security risks present on publi ...
CCIE Security Written Exam Study Guide
... quality and value. Each book is authored with attention to detail, undergoing strenuous development that involves input from a variety of technical experts. For technical support on this book, please visit: www.securityie.com Readers’ feedback is a natural part of this process. If you have any comme ...
... quality and value. Each book is authored with attention to detail, undergoing strenuous development that involves input from a variety of technical experts. For technical support on this book, please visit: www.securityie.com Readers’ feedback is a natural part of this process. If you have any comme ...
3G and 4G - Web Services Overview
... Predominantly voice- data as Converged data and VoIP add-on Wide area Cell based Hybrid – integration of Wireless Lan (WiFi), Blue ...
... Predominantly voice- data as Converged data and VoIP add-on Wide area Cell based Hybrid – integration of Wireless Lan (WiFi), Blue ...
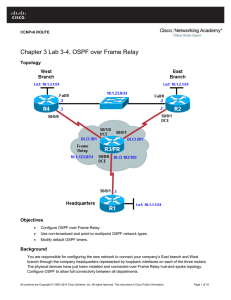
Chapter 3 Lab 3-4, OSPF over Frame Relay
... compatibility with other labs. If you are uncertain which side of the connection is the DCE, use the show controllers serial interface-number command: FRS# show controllers serial0/0/0 Interface Serial0/0/0 Hardware is GT96K DCE V.35, clock rate 64000 Note: In this lab, router R3 acts as the Frame R ...
... compatibility with other labs. If you are uncertain which side of the connection is the DCE, use the show controllers serial interface-number command: FRS# show controllers serial0/0/0 Interface Serial0/0/0 Hardware is GT96K DCE V.35, clock rate 64000 Note: In this lab, router R3 acts as the Frame R ...
CloudSync Network Drive
... four digits of the MAC address as seen on the bottom of your device (e.g. STORAGE-BB0B). 2.2.2 Nettool Application on a PC If typing STORAGE in the address field of your web browser does not work, use the Nettool application to locate the network drive instead. 1. The Nettool application requires th ...
... four digits of the MAC address as seen on the bottom of your device (e.g. STORAGE-BB0B). 2.2.2 Nettool Application on a PC If typing STORAGE in the address field of your web browser does not work, use the Nettool application to locate the network drive instead. 1. The Nettool application requires th ...
Arista Networks & VMware NSX-MH Integration INSIDE SOLUTION BRIEF
... layer-7 services like load balancers or firewalls. In addition, during migration to the SDDC, many existing storage and compute resources may need to be incorporated into the virtualized infrastructure. This physical and virtual resource integration is easily accomplished with network virtualizatio ...
... layer-7 services like load balancers or firewalls. In addition, during migration to the SDDC, many existing storage and compute resources may need to be incorporated into the virtualized infrastructure. This physical and virtual resource integration is easily accomplished with network virtualizatio ...
Virtual private networks
... based on Internet Protocol (IP) at the network layer. These VPNs can be implemented either by tunneling or by network layer encryption. A tunnel connects two points of a VPN across the shared network infrastructure. In the tunnel mode, the end-points of the tunnel are common nodes of the VPN and the ...
... based on Internet Protocol (IP) at the network layer. These VPNs can be implemented either by tunneling or by network layer encryption. A tunnel connects two points of a VPN across the shared network infrastructure. In the tunnel mode, the end-points of the tunnel are common nodes of the VPN and the ...
Chapter 4 slides
... They’re in powerpoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the ...
... They’re in powerpoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the ...
Flattened Butterfly Topology for On-Chip Networks
... found in the RAW processor [24], the TRIPS processor [12], the 80-node Intel’s Teraflops research chip [25], and the 64node chip multiprocessor from Tilera [2]. Although such low-radix networks provide a very simple network and lead to very short wires in the architecture, these networks have severa ...
... found in the RAW processor [24], the TRIPS processor [12], the 80-node Intel’s Teraflops research chip [25], and the 64node chip multiprocessor from Tilera [2]. Although such low-radix networks provide a very simple network and lead to very short wires in the architecture, these networks have severa ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.