Application of Mininet
... Learn about the usage of network tool traceroute. Based on your readings, answer the following questions. 1. Explain the difference between hub, bridge/switch and router. 2. Which is more suitable for a network with a high traffic load, hub or switch? Why? A hub is less expensive, less intelligent, ...
... Learn about the usage of network tool traceroute. Based on your readings, answer the following questions. 1. Explain the difference between hub, bridge/switch and router. 2. Which is more suitable for a network with a high traffic load, hub or switch? Why? A hub is less expensive, less intelligent, ...
DeviceNet Overview
... 500 m @ 125Kb, 100 m @ 500Kb. 8 byte network length, fragmentation application. Linear trunk / drop line. Power & signal on same cable. 24Vdc @ 8A Peer to Peer or Master/Slave. Remove & replace under power. Hazardous area classification is Class 1 Div 2 Open standard administered by ODVA. ...
... 500 m @ 125Kb, 100 m @ 500Kb. 8 byte network length, fragmentation application. Linear trunk / drop line. Power & signal on same cable. 24Vdc @ 8A Peer to Peer or Master/Slave. Remove & replace under power. Hazardous area classification is Class 1 Div 2 Open standard administered by ODVA. ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... idea of the layering to speedily and efficiently explore for the available bandwidth. At the microscopic level, Layered TCP extends the present AIMD algorithm of TCP to find out the per acknowledgment performance. The primary purpose of the LTCP is to make the size of the congestion response functio ...
... idea of the layering to speedily and efficiently explore for the available bandwidth. At the microscopic level, Layered TCP extends the present AIMD algorithm of TCP to find out the per acknowledgment performance. The primary purpose of the LTCP is to make the size of the congestion response functio ...
The Transport Layer
... 4. Minimize copying. 5. You can buy more bandwidth but not lower delay. 6. Avoiding congestion is better than recovering from it. 7. Avoid timeouts. ...
... 4. Minimize copying. 5. You can buy more bandwidth but not lower delay. 6. Avoiding congestion is better than recovering from it. 7. Avoid timeouts. ...
Linux+ Guide to Linux Certification
... router has a route table used to determine how TCP/IP packets are forwarded • Network services are started by the Internet Super Daemon or by stand-alone daemons • There are many ways to remotely administer a Linux system, including the telnet, rsh, rcp, rlogin, and ssh commands, X Windows and ...
... router has a route table used to determine how TCP/IP packets are forwarded • Network services are started by the Internet Super Daemon or by stand-alone daemons • There are many ways to remotely administer a Linux system, including the telnet, rsh, rcp, rlogin, and ssh commands, X Windows and ...
The TCP/IP Protocol Suite
... In order to better understand the operation of the TCP/IP protocol suite, some important concepts and terms should be understood beforehand. Encapsulation In computer networking, encapsulation means including data from an upper layer protocol into a lower layer protocol. This is a method of abstract ...
... In order to better understand the operation of the TCP/IP protocol suite, some important concepts and terms should be understood beforehand. Encapsulation In computer networking, encapsulation means including data from an upper layer protocol into a lower layer protocol. This is a method of abstract ...
Virtual Private Network (VPN)
... Setting up a VPN Some of the factors that should be considered in designing a VPN are: Security Reliability Scalability Network management Policy management ...
... Setting up a VPN Some of the factors that should be considered in designing a VPN are: Security Reliability Scalability Network management Policy management ...
Chennai(config
... Sending updates every 30 seconds, next due in 13 seconds Invalid after 180 seconds, hold down 180, flushed after 240 Outgoing update filter list for all interfaces is not set Incoming update filter list for all interfaces is not set Redistributing: rip Default version control: send version 1, receiv ...
... Sending updates every 30 seconds, next due in 13 seconds Invalid after 180 seconds, hold down 180, flushed after 240 Outgoing update filter list for all interfaces is not set Incoming update filter list for all interfaces is not set Redistributing: rip Default version control: send version 1, receiv ...
Cisco Router Hardening
... Limit remote access Limit local access Display login banner Configure SNMP Configure logging and NTP Provide other protection mechanisms Provide anti-spoofing Mitigate Denial of Service attacks Verify the configuration ...
... Limit remote access Limit local access Display login banner Configure SNMP Configure logging and NTP Provide other protection mechanisms Provide anti-spoofing Mitigate Denial of Service attacks Verify the configuration ...
Cisco Router Hardening - Cisco Users Group
... Limit remote access Limit local access Display login banner Configure SNMP Configure logging and NTP Provide other protection mechanisms Provide anti-spoofing Mitigate Denial of Service attacks Verify the configuration ...
... Limit remote access Limit local access Display login banner Configure SNMP Configure logging and NTP Provide other protection mechanisms Provide anti-spoofing Mitigate Denial of Service attacks Verify the configuration ...
Guide to Network Defense and Countermeasures
... information for responsible parties – Physical security of APs – Approved hardware and software – Procedures for requesting, testing, installing, and configuring hardware and software – Assignment of responsibilities for installing, maintaining, and managing wireless devices – Guidelines and penalti ...
... information for responsible parties – Physical security of APs – Approved hardware and software – Procedures for requesting, testing, installing, and configuring hardware and software – Assignment of responsibilities for installing, maintaining, and managing wireless devices – Guidelines and penalti ...
Agenda
... This could be used to implement an OC-48 or OC-192 circuit between core routers in an IP backbone. It is worth pointing out that packet-over-SONET (POS) interfaces are used, so there is SONET framing in the architecture to provide management capabilities like inline monitoring, framing and synchroni ...
... This could be used to implement an OC-48 or OC-192 circuit between core routers in an IP backbone. It is worth pointing out that packet-over-SONET (POS) interfaces are used, so there is SONET framing in the architecture to provide management capabilities like inline monitoring, framing and synchroni ...
LevelOne WAP-6110 300Mbps Wireless PoE
... a. web-based program: a web browser such as Internet Explorer v4 or later, or Netscape v4 or later. Note that version 4 of each browser is the minimum version requirement – for optimum display quality, use Internet Explorer v5, or Netscape v6.1 b. EasySetup program: Graphical User Interface ...
... a. web-based program: a web browser such as Internet Explorer v4 or later, or Netscape v4 or later. Note that version 4 of each browser is the minimum version requirement – for optimum display quality, use Internet Explorer v5, or Netscape v6.1 b. EasySetup program: Graphical User Interface ...
September 2016 report
... updates. These updates are sent only when the path or the metric for a route changes; they contain information about only that changed link rather than the entire routing table. Propagation of these partial updates is automatically bounded so that only those routers that require the information are ...
... updates. These updates are sent only when the path or the metric for a route changes; they contain information about only that changed link rather than the entire routing table. Propagation of these partial updates is automatically bounded so that only those routers that require the information are ...
Developments in Cisco IOS Forensics
... Core dumps are enabled by configuration Configuration commands do not differ between IOS versions Configuration change has no effect on the router’s operation or performance ...
... Core dumps are enabled by configuration Configuration commands do not differ between IOS versions Configuration change has no effect on the router’s operation or performance ...
local area networks
... since they are used in office environments. They also have less stringent access time requirements. The user of a business work station can wait a few seconds for information without problem, but a machine being controlled by a PLC may require information within milliseconds to operate correctly. Pa ...
... since they are used in office environments. They also have less stringent access time requirements. The user of a business work station can wait a few seconds for information without problem, but a machine being controlled by a PLC may require information within milliseconds to operate correctly. Pa ...
Chapter 12 Supporting Network Address Translation (NAT) Lesson
... set of Internet services, such as World Wide Web access and e-mail, typically accessed the Internet services through application-layer gateways such as proxy servers and email servers. The result was that most organizations only required a small amount of public addresses for those nodes (such as pr ...
... set of Internet services, such as World Wide Web access and e-mail, typically accessed the Internet services through application-layer gateways such as proxy servers and email servers. The result was that most organizations only required a small amount of public addresses for those nodes (such as pr ...
1 - Education Queensland
... When the device is delivered it is pre-loaded with a ‘data only’ 3G SIM card. The device serial number and SIM card number is linked to the allocated student. Phone calls cannot be made using the SIM card. If the SIM cards are swapped between devices or inserted into mobile phones, it may permanentl ...
... When the device is delivered it is pre-loaded with a ‘data only’ 3G SIM card. The device serial number and SIM card number is linked to the allocated student. Phone calls cannot be made using the SIM card. If the SIM cards are swapped between devices or inserted into mobile phones, it may permanentl ...
September 2012
... geographically dispersed over time. Such M2M devices should, therefore, provide adequate security to detect and resist attacks. Devices may also need to support remote management including firmware updates to correct faults or recover from malicious attacks. Some M2M Equipment (M2Mes) are typically ...
... geographically dispersed over time. Such M2M devices should, therefore, provide adequate security to detect and resist attacks. Devices may also need to support remote management including firmware updates to correct faults or recover from malicious attacks. Some M2M Equipment (M2Mes) are typically ...
Guide to TCP/IP, Second Edition
... • Because they manage access to the networking medium, data link protocols also manage the transfer of datagrams across the network Normally, this means negotiating a connection between two communications partners and transferring data between them • Such transfers are called point-to-point because ...
... • Because they manage access to the networking medium, data link protocols also manage the transfer of datagrams across the network Normally, this means negotiating a connection between two communications partners and transferring data between them • Such transfers are called point-to-point because ...
ppt
... ‘physical addresses’ used in frame headers to identify source, dest • different from IP address! Error Detection: errors caused by signal attenuation, noise. receiver detects presence of errors: • signals sender for retransmission or drops frame ...
... ‘physical addresses’ used in frame headers to identify source, dest • different from IP address! Error Detection: errors caused by signal attenuation, noise. receiver detects presence of errors: • signals sender for retransmission or drops frame ...
무선 메쉬 네트워크 (Wireless Mesh Network)
... (134 bytes), once per second Nodes remember probes received over ...
... (134 bytes), once per second Nodes remember probes received over ...
module 3 Cyberpatriot Powerpoint
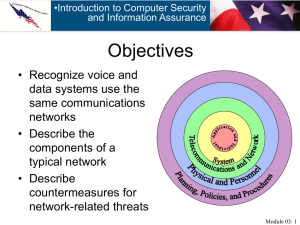
... • Recognize voice and data systems use the same communications networks • Describe the components of a typical network ...
... • Recognize voice and data systems use the same communications networks • Describe the components of a typical network ...
Chapter 1 - Introduction
... • Impersonation allows an adversary to launch various attacks • As an example, consider address spoofing in ARP: – an attacker broadcasts an ARP reply that binds an arbitrary IP address, A, to the attacker's MAC address – when any host on the network sends a packet to A, the packet will be forwarded ...
... • Impersonation allows an adversary to launch various attacks • As an example, consider address spoofing in ARP: – an attacker broadcasts an ARP reply that binds an arbitrary IP address, A, to the attacker's MAC address – when any host on the network sends a packet to A, the packet will be forwarded ...
Configuring the WT-4 for ftp (Infrastructure Mode)
... • Encryption: If you selected open system or shared key authentication, choose 64- or 128-bit WEP. If you selected WPA-PSK or WPA2-PSK authentication, choose TKIP or AES. The network in this example uses TKIP. • Encryption key: If you selected 64-bit WEP encryption, enter a 5-character ASCII or 10-d ...
... • Encryption: If you selected open system or shared key authentication, choose 64- or 128-bit WEP. If you selected WPA-PSK or WPA2-PSK authentication, choose TKIP or AES. The network in this example uses TKIP. • Encryption key: If you selected 64-bit WEP encryption, enter a 5-character ASCII or 10-d ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.