autoMAC: A Tool for Automating Network Moves, Adds, and Changes
... user can plug their host into any public ethernet jack attached to one of our user switches, and it will be automatically connected to the correct VLAN. This is accomplished using a RADIUS [6] server that ‘‘authenticates’’ the MAC address of the host attempting to connect to the network. A number of ...
... user can plug their host into any public ethernet jack attached to one of our user switches, and it will be automatically connected to the correct VLAN. This is accomplished using a RADIUS [6] server that ‘‘authenticates’’ the MAC address of the host attempting to connect to the network. A number of ...
Slide 1
... CSA Mechanism: Direct Exchange Direct Exchange: Use directly connected substrates to exchange address bindings Example: • B prefers non-broadcast Substrate 2, but does not have needed address • Use broadcast-enabled Substrate 1 to advertise address for Substrate 2 Substrate S1 (broadcast enabled) ...
... CSA Mechanism: Direct Exchange Direct Exchange: Use directly connected substrates to exchange address bindings Example: • B prefers non-broadcast Substrate 2, but does not have needed address • Use broadcast-enabled Substrate 1 to advertise address for Substrate 2 Substrate S1 (broadcast enabled) ...
Networking ALPHA signs on LANs using print servers
... the above two protocols is installed: In this example, the NetBEUI protocol is used. ...
... the above two protocols is installed: In this example, the NetBEUI protocol is used. ...
A+ Guide to Managing and Maintaining Your PC, 5e
... Installing Windows XP Components Needed to Share Resources ...
... Installing Windows XP Components Needed to Share Resources ...
- UNIMAS Institutional Repository
... There are lots of factors that can affect the performance of wireless network, such as the internal and external interference, user capacity and the application load itself. The focus of the project is to examine the effect of the various heavy applications running on Wireless LA ...
... There are lots of factors that can affect the performance of wireless network, such as the internal and external interference, user capacity and the application load itself. The focus of the project is to examine the effect of the various heavy applications running on Wireless LA ...
CompTIA Network+ N10-005 Authorized Exam Cram
... retrieval system, or transmitted by any means, electronic, mechanical, photocopying, recording, or otherwise, without written permission from the publisher. No patent liability is assumed with respect to the use of the information contained herein. Although every precaution has been taken in the pre ...
... retrieval system, or transmitted by any means, electronic, mechanical, photocopying, recording, or otherwise, without written permission from the publisher. No patent liability is assumed with respect to the use of the information contained herein. Although every precaution has been taken in the pre ...
Netware - The University of New Mexico
... – Developed by IBM shortly after the IBM personal computer was introduced. – Developed so that microcomputers could share access to files stored on central file servers. – NetWare is the most widely used network operating system because of its stability and speed. – Novell has continued to improve N ...
... – Developed by IBM shortly after the IBM personal computer was introduced. – Developed so that microcomputers could share access to files stored on central file servers. – NetWare is the most widely used network operating system because of its stability and speed. – Novell has continued to improve N ...
Internet Protocols - Chair for Network Architectures and Services
... Provides raw network protocol access. SOCK_SEQPACKET Provides a sequenced, reliable, two-way connection- based data transmission path for datagrams of fixed maximum length; a consumer is required to read an entire packet with each read system call. ...
... Provides raw network protocol access. SOCK_SEQPACKET Provides a sequenced, reliable, two-way connection- based data transmission path for datagrams of fixed maximum length; a consumer is required to read an entire packet with each read system call. ...
OSPF - Computing Sciences
... • An AS can be a collection of routers running a single IGP, or it can be a collection of routers running different protocols all belonging to one organization. • In either case, the outside world views the entire Autonomous System as a single entity. ...
... • An AS can be a collection of routers running a single IGP, or it can be a collection of routers running different protocols all belonging to one organization. • In either case, the outside world views the entire Autonomous System as a single entity. ...
OSPF - Computing Sciences
... • An AS can be a collection of routers running a single IGP, or it can be a collection of routers running different protocols all belonging to one organization. • In either case, the outside world views the entire Autonomous System as a single entity. ...
... • An AS can be a collection of routers running a single IGP, or it can be a collection of routers running different protocols all belonging to one organization. • In either case, the outside world views the entire Autonomous System as a single entity. ...
O`Brien MIS, 6th ed.
... The task of a router is significantly greater than that of repeaters, bridges, and switches because a router must convert between the idiosyncrasies of the two original networks For example, when transferring a message from a network using the token ring protocol to a network using CSMA/CD, ...
... The task of a router is significantly greater than that of repeaters, bridges, and switches because a router must convert between the idiosyncrasies of the two original networks For example, when transferring a message from a network using the token ring protocol to a network using CSMA/CD, ...
CCNA1 Complete Lecture Set Mod 1 to 11
... Network bandwidth is typically described as thousands of bits per second (kbps), millions of bits per second (Mbps), billions of bits per second (Gbps), and trillions of bits per second (Tbps). Bandwidth varies depending upon the type of media as well as the LAN and WAN technologies used. The physic ...
... Network bandwidth is typically described as thousands of bits per second (kbps), millions of bits per second (Mbps), billions of bits per second (Gbps), and trillions of bits per second (Tbps). Bandwidth varies depending upon the type of media as well as the LAN and WAN technologies used. The physic ...
Case Study - SolarWinds Supports High Levels of Patient Care in
... WAN path quality and LAN path quality. It has proved itself by showing which is a LAN issue and which is a WAN issue. Engineer’s Toolset – We purchased it because as far as we could find there wasn’t any other comparable product on the market at the time and have used it ever since. I use it mostly ...
... WAN path quality and LAN path quality. It has proved itself by showing which is a LAN issue and which is a WAN issue. Engineer’s Toolset – We purchased it because as far as we could find there wasn’t any other comparable product on the market at the time and have used it ever since. I use it mostly ...
Link Layer - dbmanagement.info
... compare transmitted, received signals difficult in wireless LANs: received signal strength ...
... compare transmitted, received signals difficult in wireless LANs: received signal strength ...
Routing in Packet Switching Networks Contd.
... This unit will develop student knowledge of the techniques and systems for network administration. On completion of this unit, the student should have acquired the knowledge needed to identify the tasks or roles required of network administrators, understand current developments and standards for ne ...
... This unit will develop student knowledge of the techniques and systems for network administration. On completion of this unit, the student should have acquired the knowledge needed to identify the tasks or roles required of network administrators, understand current developments and standards for ne ...
William Stallings Data and Computer Communications
... How many connections are required for the previous three stage switch compared to the crossbar matrix? How many calls can simultaneously be supported in each? ...
... How many connections are required for the previous three stage switch compared to the crossbar matrix? How many calls can simultaneously be supported in each? ...
Evolving Toward a Self-Managing Network Jennifer Rexford Princeton University
... – Complex decision logic and policies – Yet a simple protocol (and message format) – Use BGP messages to “program” the routers ...
... – Complex decision logic and policies – Yet a simple protocol (and message format) – Use BGP messages to “program” the routers ...
Internet Control Message Protocol
... due to some type of failure. A TCP or UDP packet directed at a port number with no receiver attached is also reported via ICMP. Announce network congestion: When a router begins buffering too many packets, due to an inability to transmit them as fast as they are being received, it will generate ICMP ...
... due to some type of failure. A TCP or UDP packet directed at a port number with no receiver attached is also reported via ICMP. Announce network congestion: When a router begins buffering too many packets, due to an inability to transmit them as fast as they are being received, it will generate ICMP ...
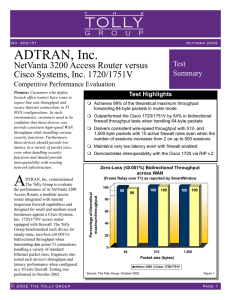
NetVanta 3200 Tolly Group Report
... User requirements for full linerate support are not limited to high-end connections on the LAN, but include WAN connections, as well. Remote connections via frame relay and Internet connectivity via PPP or frame relay continue to be in demand even with the growth of DSL and cable modem connections. ...
... User requirements for full linerate support are not limited to high-end connections on the LAN, but include WAN connections, as well. Remote connections via frame relay and Internet connectivity via PPP or frame relay continue to be in demand even with the growth of DSL and cable modem connections. ...
Different Hashing Algorithms
... Developed early 1980s and introduced in 1984: OSI Model Application Presentation Session Transport Network Data Link Physical ...
... Developed early 1980s and introduced in 1984: OSI Model Application Presentation Session Transport Network Data Link Physical ...
A+ Guide to Managing and Maintaining Your PC, 5e
... Installing Windows XP Components Needed to Share Resources ...
... Installing Windows XP Components Needed to Share Resources ...
Understanding Network Access Control
... There are a lot of niche-solutions on the market that try to replicate the process of detection and authentication via SNMP. Some organizations prefer using this method if no directory or RADIUS framework is available. The advantage is clearly the out-of-band management, compatible with all SNMP dev ...
... There are a lot of niche-solutions on the market that try to replicate the process of detection and authentication via SNMP. Some organizations prefer using this method if no directory or RADIUS framework is available. The advantage is clearly the out-of-band management, compatible with all SNMP dev ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.