Document
... • ABwE is a light weight available bandwidth measurement tool based on the packet pair dispersion technique. • It uses fixed size packets with specific delay between each packet pair. • The observed packet pair delay is converted into available bandwidth calculations. • The tool can be used in conti ...
... • ABwE is a light weight available bandwidth measurement tool based on the packet pair dispersion technique. • It uses fixed size packets with specific delay between each packet pair. • The observed packet pair delay is converted into available bandwidth calculations. • The tool can be used in conti ...
Final exam
... 2. We transfer a 6 M byte message through a network with the bandwidth of 400 Kbps, using the Go-back-N ARQ protocol. The sender window size is 4, and the receiver sends ACK for each data frame. Each data frame carries 2,000 bits of data. Assume that the distance between the sender and the receiver ...
... 2. We transfer a 6 M byte message through a network with the bandwidth of 400 Kbps, using the Go-back-N ARQ protocol. The sender window size is 4, and the receiver sends ACK for each data frame. Each data frame carries 2,000 bits of data. Assume that the distance between the sender and the receiver ...
Network Setup and Configuration
... When two or more people want to share their resources through their own PCs, a network has to be setup. A very common network that most offices and schools are using is the Ethernet Network. In order to build the network, network cables, network interface card or hubs/routers will be used. ...
... When two or more people want to share their resources through their own PCs, a network has to be setup. A very common network that most offices and schools are using is the Ethernet Network. In order to build the network, network cables, network interface card or hubs/routers will be used. ...
Part I: Introduction
... carry network layer data of any network layer protocol (not just IP) at same time ability to demultiplex upwards bit transparency: must carry any bit pattern in the data field error detection (no correction) connection livenes: detect, signal link failure to network layer network layer address n ...
... carry network layer data of any network layer protocol (not just IP) at same time ability to demultiplex upwards bit transparency: must carry any bit pattern in the data field error detection (no correction) connection livenes: detect, signal link failure to network layer network layer address n ...
lecture9 - Academic Csuohio
... Datagram Networks • No call setup at network layer • Routers: no state about end-to-end connections – no network-level concept of “connection” ...
... Datagram Networks • No call setup at network layer • Routers: no state about end-to-end connections – no network-level concept of “connection” ...
Set 1 File
... sharing; and many, many more. In addition, your programs can define their own application layer protocols as necessary. ...
... sharing; and many, many more. In addition, your programs can define their own application layer protocols as necessary. ...
2. (a) What universal set of communication services is provided by
... (b) How is independence from underlying network technologies achieved? Solution: The two basic communications services provided by TCP and UDP are built on the connectionless packet transfer service provided by the Internet Protocol (IP). Many network interfaces are defined to support IP. The salien ...
... (b) How is independence from underlying network technologies achieved? Solution: The two basic communications services provided by TCP and UDP are built on the connectionless packet transfer service provided by the Internet Protocol (IP). Many network interfaces are defined to support IP. The salien ...
MIS 430 Part III Chapter 6
... 10Base-T = 10 Mbps twisted pair 100Base-T= 100 Mbps UTP 1000Base-T = 1 Gbps Ethernet 40GbE = 40 Gbps fiber Some use 10/100 which switches to match speed ...
... 10Base-T = 10 Mbps twisted pair 100Base-T= 100 Mbps UTP 1000Base-T = 1 Gbps Ethernet 40GbE = 40 Gbps fiber Some use 10/100 which switches to match speed ...
Adventures in Computer Security - Applied Crypto Group at Stanford
... Client to Daemon to Victim • TCP, SYN and UDP floods • Fixed payload size ...
... Client to Daemon to Victim • TCP, SYN and UDP floods • Fixed payload size ...
NAME: Computer Science 461 Midterm Exam March 14, 2014
... 1. Which are true about network switches and routers? a. Ethernet switches will always send received frames out all interfaces (except the one on which the packet was received). b. Both IP routers and Ethernet hubs drop packets when there is congestion. c. Ethernet switches learn the location of hos ...
... 1. Which are true about network switches and routers? a. Ethernet switches will always send received frames out all interfaces (except the one on which the packet was received). b. Both IP routers and Ethernet hubs drop packets when there is congestion. c. Ethernet switches learn the location of hos ...
Chapter 2 - William Stallings, Data and Computer
... used by the global Internet protocol suite comprises a large collection of standardized protocols ...
... used by the global Internet protocol suite comprises a large collection of standardized protocols ...
Event Based Routing In Delay Tolerant Networks
... (hosts that can be reached within a few hops). This information would enable each router to estimate the number of matching subscribers that are expected to be reached (directly or through other routers) in the next Tx time Units, given an event E. These statistics are used for several important pur ...
... (hosts that can be reached within a few hops). This information would enable each router to estimate the number of matching subscribers that are expected to be reached (directly or through other routers) in the next Tx time Units, given an event E. These statistics are used for several important pur ...
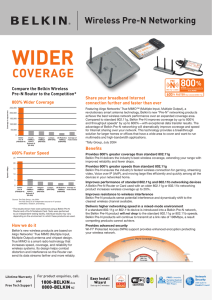
coverage
... achieve the best wireless network performance over an expanded coverage area. Compared to standard 802.11g, Belkin Pre-N improves coverage by up to 800% and throughput speeds* by up to 600%—with exceptional data transfer results. The advantage of Belkin Pre-N networking will dramatically improve cov ...
... achieve the best wireless network performance over an expanded coverage area. Compared to standard 802.11g, Belkin Pre-N improves coverage by up to 800% and throughput speeds* by up to 600%—with exceptional data transfer results. The advantage of Belkin Pre-N networking will dramatically improve cov ...
15-744: Computer Networking
... • Mark packets with a small number of bits; each bit encoding represents a class or subclass ...
... • Mark packets with a small number of bits; each bit encoding represents a class or subclass ...
BDC5eChapter19
... • Each "player" in the network management system maintains local database of network management information (MIB) • Standard defines information structure and allowable data types (SMI) • At least one system must be responsible for network management; others act as agents • Information exchanged usi ...
... • Each "player" in the network management system maintains local database of network management information (MIB) • Standard defines information structure and allowable data types (SMI) • At least one system must be responsible for network management; others act as agents • Information exchanged usi ...
Ad-Hoc Wireless Networks
... (WLAN) are defined in IEEE 802.11 standard • It defines two different topologies: ad-hoc network and infrastructure network ...
... (WLAN) are defined in IEEE 802.11 standard • It defines two different topologies: ad-hoc network and infrastructure network ...
pptx - Brown Computer Science
... • Cut-through routing can greatly decrease latency • Disadvantage – Can waste transmission (classic optimistic approach) • CRC may be bad • If Ethernet collision, may have to send runt packet on output link ...
... • Cut-through routing can greatly decrease latency • Disadvantage – Can waste transmission (classic optimistic approach) • CRC may be bad • If Ethernet collision, may have to send runt packet on output link ...
Introduction - Suraj @ LUMS
... 1. To arrange or place (troops, for example) in line for a parade, maneuver, or review. 2. To arrange, place, or set in methodical order. 3. To enlist and organize. 4. To guide ceremoniously; conduct or usher. ...
... 1. To arrange or place (troops, for example) in line for a parade, maneuver, or review. 2. To arrange, place, or set in methodical order. 3. To enlist and organize. 4. To guide ceremoniously; conduct or usher. ...
Adventures in Computer Security
... • If attacker knows initial seq # and amount of traffic sent, can estimate likely current values • Send a flood of packets with likely seq numbers • Attacker can inject packets into existing connection ...
... • If attacker knows initial seq # and amount of traffic sent, can estimate likely current values • Send a flood of packets with likely seq numbers • Attacker can inject packets into existing connection ...
IT 141: Information Systems I - Tonga Institute of Higher Education
... Why is there a button that says, “Obtain IP address automatically” and “Use the following IP address” If you obtain an IP address automatically, it means that you are using a Dynamic IP address. This means that your IP address will change every time the computer starts Where does it get the IP from? ...
... Why is there a button that says, “Obtain IP address automatically” and “Use the following IP address” If you obtain an IP address automatically, it means that you are using a Dynamic IP address. This means that your IP address will change every time the computer starts Where does it get the IP from? ...
N0254_LL-Status_WG7_meeting_2009-01
... This document focuses on the identification and characterization of the transport services required by the upper layers of the ISO/IEEE 11073 family of standards that are to be provided by the lower layers of the ISO/IEEE 11073 family of standards. The transport services and characteristics may cove ...
... This document focuses on the identification and characterization of the transport services required by the upper layers of the ISO/IEEE 11073 family of standards that are to be provided by the lower layers of the ISO/IEEE 11073 family of standards. The transport services and characteristics may cove ...
Network review
... (computers) – need for guaranteed – can adapt, perform control, service error recovery – simple inside network, • “dumb” end systems complexity at “edge” – telephones • many link types – complexity inside – different characteristics network – uniform service difficult ...
... (computers) – need for guaranteed – can adapt, perform control, service error recovery – simple inside network, • “dumb” end systems complexity at “edge” – telephones • many link types – complexity inside – different characteristics network – uniform service difficult ...