* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Network review
Piggybacking (Internet access) wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Serial digital interface wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
Computer network wikipedia , lookup
Network tap wikipedia , lookup
Airborne Networking wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Deep packet inspection wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Routing in delay-tolerant networking wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Internet protocol suite wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
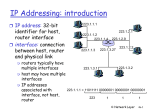
Cosc 4765 Networking overview Bandwidth Review • Bit (b) = a unit of information, 0 or 1 – 10 bits can represent 1024 different messages – 20 bits represent > 1 million – 30 bits > 1 billion messages • The bandwidth of a communication channel = number of bits per second it transmits • All channels have limited bandwidth • One byte (B) = 8 bits (an octet) • Transmitting 1 MB at 56K bps takes 143 sec. • 1 GB = gigabyte takes 40 hours – at 7Mbps 19 minutes; at 1 Gbps takes 8 seconds • Latency = delay from first bit transmitted to first received Progress of Technology • Have more disk storage IMPROVEMENT: 8000 x – 1971: 10 MB – 2001: 80,000 MB (soon 1 terabyte = 1000GB) • Higher communication speeds – – – – – – 1971-2001 IMPROVEMENT: 3 BILLION x Human speech: 30 bits/sec 1971 Modem 300 bits/sec 2001 Modem: 56,000 bits/sec T1 line: 1,544,000 bits/sec Internet 2: 1,000,000,000 bits/sec Nortel: 1,000,000,000,000 bits/sec in 1 fiber (entire U.S. telephone traffic) BANDWIDTH APPLICATION TECHNOLOGY Experimental 1 terabit All U.S. telephone conversations simultaneously Gigabit Ethernet 1 gigabit Full-motion HDTV OC12 = 622 Mb FDDI OC3 = 155 Mb Virtual Reality, Medical Imaging T3/E3 T3 = 44.7 Mb Video Conferencing, Multimedia DSL ~ 7 Mb Streaming Video + Voice T1 = 1.544 Mb ADSL T1/E1 ISDN 128K Fiber Copper Browsing, Audio New Modem 56K E-mail, FTP In Kbps 19.2 Old Modem Telnet 4.8 Wireless WAN Paging Human speech = 30 bps BANDWIDTH LIST Some humor first http://www.the5thwave.com/images/cartoons_computer/large/training/631lg.gif IEEE Standards for networking There are 7 layers in the OSI network model • Layer 7: Application – mechanisms to support end-user applications such as mail, ftp, etc. • Layer 6: Presentation – mechanisms for dealing with data representation • Layer 5: Session – mechanisms for establishing reliable communications between cooperating applications IEEE Standards for networking (2) • Layer 4: Transport layer – provides reliable end-to-end error recovery mechanisms and flow control in the higher networking software – Firewall work here (an up to layer 7) • Layer 3: Network (hardware) – Establishes communication from station to station – Most high level Network protocols are in this layer – Routers work at this layer IEEE Standards for networking (3) • Layer 2: Data link (hardware) – transmits and receives frames, MAC protocol belongs to this layer – Switches and bridges work at this layer. • layer 1: Physical (hardware) – standardizes the electrical, mechanical, and functional control of data circuits that connect to the transmission media – Hubs and repeaters work at this layer. • Layer 0: transmission media – cables between two network stations (includes wireless transmissions) How OSI layer works. – A program, which "functions" at layer 7, (application layer) passes the message down to the next OSI levels. Each layer changes and adds information as needed. – the message goes out onto the network. – then back up the OSI levels (stripping off information needed only at that layer and changing the message as needed) until it reaches the application layer of the receiving program, which then reads the message based on the protocol used. • We are going to look at each layer, starting at layer 7 and working our way down to layer 0 • But remember, each layer is dependent on the one above it and below it. • An important concept in OSI is data encapsulation. Layer 7 data is encapsulated by Layer 4, then layer 3 encapsulates layer 4 data (which is encapsulated layer 7 data with more information), continuing this process down to layer 2. – Each layer also uses different terms as well. Ethernet • Uses the OSI network model, but with different names. – Also compresses layer 5, 6, 7 into the same layer. Most network applications are written to the Ethernet standards (including O/Ss), • Because of the different names, which confuses people, the layer number is normally used as the name. Layer 7: Application • Application protocol defines: – types of messages to be exchanged • requests and response messages – The syntax of the messages, fields and how they are delineated. – semantics of the fields (ie what they mean) – rules for when and how a program sends messages and replies to messages. • Such as the HTTP protocol. Layer 6: Presentation layer • Deals with data representation – since UNIX, windows, Mac, the Internet, etc do not agree on what the data should look like, this layer deals with the multiple data representation standards. – These include whether the O/S uses ASCII standards or another character standard, big/little Endian byte ordering standards, etc. Layer 5: Session layer • when a program asks for a network connection, it is this layer than establishes and maintains the connection – Sockets are created on this layer • These layer makes a request to Layer 4 for protocol. Layer 5 is a virtual layer in most respects. It's standard interface into layer 4. – A socket is created on this layer, but how all the communication is done is left up layer 4 and below. Layer 4: Transport • Provides logical communication between application processes on different hosts. – Not a physical connection, but applications think so. – Applications don’t need to worry about physical infrastructure. • Two protocols provided and developer must choose one. – UDP (User Datagram Protocol) – TCP (Transmission control Protocol) • Other non-common transport protocols exist here UDP in detail • [RFC 768] – multiplex/demultiplexing and error checking. – No connection establishment – No connection state – small packet header overhead • UDP adds 8B of header, while TCP adds 20B – Unregulated send rate UDP segment • Contains – – – – – Source Port # Destination Port # Length of entire segment (including header) Checksum Application data or message. • No IP number, contained in the network layer header information. IP are layer 3 information. TCP: Overview RFCs: 793, 1122, 1323, 2018, 2581 • point-to-point: • full duplex data: – one sender, one receiver – bi-directional data flow in same connection – MSS: maximum segment size • reliable, in-order byte steam: – no “message boundaries” • pipelined: • connection-oriented: – handshaking (exchange of control msgs) init’s sender, receiver state before data exchange – TCP congestion and flow control set window size • send & receive buffers socket door application writes data application reads data TCP send buffer TCP receive buffer segment • flow controlled: socket door – sender will not overwhelm receiver TCP segment structure 32 bits URG: urgent data (generally not used) ACK: ACK # valid PSH: push data now (generally not used) RST, SYN, FIN: connection estab (setup, teardown commands) Internet checksum (as in UDP) source port # dest port # sequence number acknowledgement number head not UA P R S F len used checksum rcvr window size ptr urgent data Options (variable length) application data (variable length) counting by bytes of data (not segments!) # bytes rcvr willing to accept Data Reliability • Why does TCP provide reliable data transfer and UDP does not? – In the Network layer (Layer 3), Best-effect delivery service is provided – Meaning the best attempt to deliver is made, but no guarantees, no orderly deliver, and no guarantee on the integrity of the data. Layer 3: Network layer Host, router network layer functions: Transport layer: TCP, UDP Network layer IP protocol •addressing conventions •datagram format •packet handling conventions Routing protocols •path selection •RIP, OSPF, BGP routing table ICMP protocol •error reporting •router “signaling” Link layer physical layer Network layer functions • transport packet from sending to receiving hosts • network layer protocols in every host, router application transport network data link physical network data link physical network data link physical three important functions: • path determination: route taken by packets from source to dest. Routing algorithms • switching: move packets from router’s input to appropriate router output • call setup: some network architectures require router call setup along path before data flows network data link physical network data link physical network data link physical network data link physical network data link physical network data link physical application transport network data link physical Network service model Q: What service model for “channel” transporting packets from sender to receiver? • guaranteed bandwidth? • preservation of interpacket timing (no jitter)? • loss-free delivery? • in-order delivery? • congestion feedback to sender? The most important abstraction provided by network layer: ? ? ? virtual circuit or datagram? Virtual circuits “source-to-dest path behaves much like telephone circuit” – performance-wise – network actions along source-to-dest path • call setup, teardown for each call before data can flow • each packet carries VC identifier • every router on source-dest path s maintain “state” for each passing connection – transport-layer connection only involved two end systems • link, router resources (bandwidth, buffers) may be allocated to VC – to get circuit-like performance. Virtual circuits: signaling protocols • used to setup, maintain teardown VC • used in ATM, frame-relay, X.25 • not used in today’s Internet application transport 5. Data flow begins network 4. Call connected data link 1. Initiate call physical 6. Receive data application 3. Accept call transport 2. incoming call network data link physical Datagram networks: the Internet model • no call setup at network layer • routers: no state about end-to-end connections – no network-level concept of “connection” • packets typically routed using destination host ID – packets between same source-dest pair may take different paths application transport network data link 1. Send data physical application transport 2. Receive data network data link physical Datagram or VC network: why? Internet • data exchange among computers ATM (asynchronous transfer mode) • evolved from telephony • human conversation: – “elastic” service, no strict – strict timing, timing req. reliability • “smart” end systems requirements (computers) – need for guaranteed – can adapt, perform control, service error recovery – simple inside network, • “dumb” end systems complexity at “edge” – telephones • many link types – complexity inside – different characteristics network – uniform service difficult Routing Routing protocol 5 Goal: determine “good” path (sequence of routers) thru network from source to dest. Graph abstraction for routing algorithms: • graph nodes are routers • graph edges are physical links – link cost: delay, $ cost, or congestion level 2 A B 2 1 D 3 C F 1 3 1 5 E 2 • “good” path: – typically means minimum cost path – other def’s possible IP Addressing: introduction • IP address: 32-bit identifier for host, router interface • interface: connection between host, router and physical link – router’s typically have multiple interfaces – host may have multiple interfaces – IP addresses associated with interface, not host, router 223.1.1.1 223.1.2.1 223.1.1.2 223.1.1.4 223.1.1.3 223.1.2.9 223.1.3.27 223.1.2.2 223.1.3.2 223.1.3.1 223.1.1.1 = 11011111 00000001 00000001 00000001 223 1 1 1 IP datagram format IP protocol version number header length (bytes) “type” of data max number remaining hops (decremented at each router) upper layer protocol to deliver payload to 32 bits type of ver head. len service length fragment 16-bit identifier flgs offset time to upper Internet layer live checksum total datagram length (bytes) for fragmentation/ reassembly 32 bit source IP address 32 bit destination IP address Options (if any) data (variable length, typically a TCP or UDP segment) E.g. timestamp, record route taken, specify list of routers to visit. Getting a datagram from source to dest. routing table in A Dest. Net. next router Nhops 223.1.1 223.1.2 223.1.3 IP datagram: misc source dest fields IP addr IP addr data • datagram remains unchanged, as it travels source to destination • addr fields of interest here A 223.1.1.4 223.1.1.4 1 2 2 223.1.1.1 223.1.2.1 B 223.1.1.2 223.1.1.4 223.1.1.3 223.1.3.1 223.1.2.9 223.1.3.27 223.1.2.2 223.1.3.2 E Getting a datagram from source to dest. misc data fields 223.1.1.1 223.1.1.3 Starting at A, given IP datagram addressed to B: • look up net. address of B • find B is on same net. as A • link layer will send datagram directly to B inside link-layer frame – B and A are directly connected Dest. Net. next router Nhops 223.1.1 223.1.2 223.1.3 A 223.1.1.4 223.1.1.4 1 2 2 223.1.1.1 223.1.2.1 B 223.1.1.2 223.1.1.4 223.1.1.3 223.1.3.1 223.1.2.9 223.1.3.27 223.1.2.2 223.1.3.2 E Getting a datagram from source to dest. misc data fields 223.1.1.1 223.1.2.3 Dest. Net. next router Nhops 223.1.1 223.1.2 223.1.3 Starting at A, dest. E: • look up network address of E • E on different network A 223.1.1.4 223.1.1.4 223.1.1.1 – A, E not directly attached • routing table: next hop router to E is 223.1.1.4 • link layer sends datagram to router 223.1.1.4 inside linklayer frame • datagram arrives at 223.1.1.4 • continued….. 1 2 2 223.1.2.1 B 223.1.1.2 223.1.1.4 223.1.1.3 223.1.3.1 223.1.2.9 223.1.3.27 223.1.2.2 223.1.3.2 E Getting a datagram from source to dest. misc data fields 223.1.1.1 223.1.2.3 • Arriving at 223.1.4, destined for 223.1.2.2 • look up network address of E • E on same network as router’s interface 223.1.2.9 Dest. next network router Nhops interface 223.1.1 223.1.2 223.1.3 A 1 1 1 223.1.1.4 223.1.2.9 223.1.3.27 223.1.1.1 223.1.2.1 – router, E directly attached • link layer sends datagram to 223.1.2.2 inside link-layer frame via interface 223.1.2.9 • datagram arrives at 223.1.2.2!!! (hooray!) - B 223.1.1.2 223.1.1.4 223.1.1.3 223.1.3.1 223.1.2.9 223.1.3.27 223.1.2.2 223.1.3.2 E IP Fragmentation & Reassembly • network links have MTU (max.transfer size) - largest possible link-level frame. – different link types, different MTUs • large IP datagram divided (“fragmented”) within net – one datagram becomes several datagrams – “reassembled” only at final destination – IP header bits used to identify, order related fragments fragmentation: in: one large datagram out: 3 smaller datagrams reassembly IP Fragmentation and Reassembly length ID fragflag offset =4000 =x =0 =0 One large datagram becomes several smaller datagrams length ID fragflag offset =1500 =x =1 =0 length ID fragflag offset =1500 =x =1 =1480 length ID fragflag offset =1040 =x =0 =2960 MTU is min. of 576 bytes, so if MSS is 536b, fragmentation can eliminated RIP ( Routing Information Protocol) • Distance vector algorithm • Included in BSD-UNIX Distribution in 1982 • Distance metric: # of hops (max = 15 hops) – Can you guess why? • Distance vectors: exchanged every 30 sec via Response Message (also called advertisement) • Each advertisement: route to up to 25 destination nets RIP: Link Failure and Recovery If no advertisement heard after 180 sec --> neighbor/link declared dead – routes via neighbor invalidated – new advertisements sent to neighbors – neighbors in turn send out new advertisements (if tables changed) – link failure info quickly propagates to entire net – poison reverse used to prevent ping-pong loops (infinite distance = 16 hops) RIP Table processing • RIP routing tables managed by applicationlevel process called route-d (daemon) • advertisements sent in UDP packets, periodically repeated RIP Table example (continued) Router: giroflee.eurocom.fr Destination -------------------127.0.0.1 192.168.2. 193.55.114. 192.168.3. 224.0.0.0 default Gateway Flags Ref Use Interface -------------------- ----- ----- ------ --------127.0.0.1 UH 0 26492 lo0 192.168.2.5 U 2 13 fa0 193.55.114.6 U 3 58503 le0 192.168.3.5 U 2 25 qaa0 193.55.114.6 U 3 0 le0 193.55.114.129 UG 0 143454 • Three attached class C networks (LANs) • Router only knows routes to attached LANs • Default router used to “go up” • Route multicast address: 224.0.0.0 • Loopback interface (for debugging) • ASUWLINK: netstat –rn will show the route table ICMP: Internet Control Message Protocol • used by hosts, routers, gateways to communication network-level information – error reporting: unreachable host, network, port, protocol – echo request/reply (used by ping) • network-layer “above” IP: – ICMP msgs carried in IP datagrams • ICMP message: type, code plus first 8 bytes of IP datagram causing error ICMP • Reason for ICMP: – provides a mechanism for IP devices to use when they need to exchange information about network problems that are preventing delivery • Normally semi-permanent and/or non-transient errors. • problems that prevent all datagrams through to their destination. ICMP (2) • IP datagram failed to be delivered because – next-hop router is unavailable – non-existent destination IP address or Port • ICMP error message are returned if is a semi-permanent or non-transient error – transient errors are ignored and left to the application or TCP to deal with. • why? the next packet should not have the same problem. ICMP (3) • non-transient and semi-permanent errors – a fundamental problem with the network itself – a problem in the way that the sender is trying to use the network – destination becomes unreachable – IP Time-to-Live value reaching zero • Time-to-Live value based on hops, not actual time. ICMP (4) • Also used for – exchanging general information about the network • Essentially ICMP is a collection of predefined messages – system chooses a message from a dictionary, places the code for the message into an ICMP-specific datagram and then sends it. ICMP Message Formats Ping and ICMP • Uses ICMP messages to test basic connectivity between two devices • The message created is for ICMP itself, so no other protocols are involved – ICMP is not a transport protocol and as such can not be used to deliver application data. • ICMP receives the message, which is an "echo request", then generates a response "echo reply" and sends it. UNIX ping • example (ping k2 from meru) seker>ping k2 PING k2.cs.uwyo.edu (129.72.216.12): 56 data bytes 64 bytes from 129.72.216.12: icmp_seq=0 ttl=64 time=2.773 ms 64 bytes from 129.72.216.12: icmp_seq=1 ttl=64 time=1.720 ms ----k2.cs.uwyo.edu PING Statistics---2 packets transmitted, 2 packets received, 0.0% packet loss round-trip min/avg/max = 1.720/2.246/2.773 ms • MEANS: • icmp_seq is the sequence number from the icmp packet • ttl is time-to-live, time is the round trip time for the packet, so 2.773 milliseconds for the first line • And summary information ICMP message types • Three main message types: – ICMP error message • There a problem to report – ICMP query message • Asking for information – ICMP query reply message • response to query • It is really a ICMP query message, it is easier to think about separately. When not to send ICMP Messages • An ICMP error message in response to another ICMP error message. – would create a message loop and case a network/broadcast storm. • ICMP Error messages to broadcast or multicast address – It could generate thousands of messages. • ICMP query response messages may be sent. • Optional in the RFC 1122 Common Message Types Type 0 3 4 5 8 9 10 11 12 13 14 17 18 Code 0 0-15 0 0-3 0 0 0 0-1 0-2 0 0 0 0 description echo reply (ping) dest. network unreachable source quench Redirect echo request (ping) route advertisement router Solicition Time-To-Live expired bad IP header Timestamp Request Timestamp reply Address Mask request Address Mask Reply Message Family Query (reply) Error Error Error Query (request) Query (reply) Query (request) Error Error Query (request) Query (reply) Query (request) (obsolete) Query (reply) (obsolete) traceroute • allows you to identify the route that datagrams are taking to a remote device. • How it works: – sends a set of packets with incrementally larger Timeto-Live (hops) values, checking ICMP time exceeded error messages as packets expire getting to their distintation – first packet ttl =1, router sets it to zero, and returns an ICMP error, traceroute notes the router and time – second packet ttl=2, so the second router sets it to zero, and returns an ICMP error, traceroute notes the routers and time, – etc, until it reaches it destination. Traceroute Example 1 >traceroute k2 traceroute to k2 (129.72.216.12), 30 hops max, 60 byte packets 1 k2.cs.uwyo.edu (129.72.216.12) 3 ms 2 ms 2 ms • Only 1 hop, because there is no router in between • this version sends 3 messages to get a better idea of time. >traceroute arthur.uwyo.edu traceroute to arthur.uwyo.edu (129.72.10.203), 30 hops max, 60 byte packets 1 129.72.216.1 11 ms 7 ms 9 ms 2 quark.uwyo.edu (129.72.62.70) 1 ms 5 ms 2 ms 3 arthur.uwyo.edu (129.72.10.203) 2 ms 2 ms 2 ms • the 216 "gateway", internal uwyo router, then arthur. traceroute Example 2 >traceroute www.netscape.com traceroute to www.netscape.com (64.12.151.215), 30 hops max, 60 byte packets 1 129.72.216.1 5 ms 8 ms 8 ms 2 uwyo-router-subnet-062.uwyo.edu (129.72.62.1) 2 ms 1780 ms 1781 ms 3 frgp-gw-1.uwyo.edu (129.72.253.6) 12 ms 9 ms 6 ms 4 ucar.edu.ip.att.net (12.124.158.13) 24 ms 18 ms 16 ms 5 gbr1-p60.dvmco.ip.att.net (12.123.36.138) 27 ms 20 ms 25 ms 6 gbr4-p70.dvmco.ip.att.net (12.122.5.21) 19 ms 1697 ms 1781 ms 7 gbr4-p80.dlstx.ip.att.net (12.122.2.101) 29 ms 1703 ms 1781 ms 8 gbr6-p70.dlstx.ip.att.net (12.122.5.85) 31 ms 1708 ms 1781 ms 9 *** 10 tbr2-p013401.attga.ip.att.net (12.122.10.74) 52 ms 2764 ms 46 ms 11 tbr1-p012501.attga.ip.att.net (12.122.9.157) 47 ms 2763 ms 46 ms 12 tbr2-p013801.wswdc.ip.att.net (12.122.10.69) 56 ms 2775 ms 62 ms 13 ggr2-p390.wswdc.ip.att.net (12.123.9.85) 60 ms 1706 ms 1781 ms • NOTE: * * * indicates the request timed out, since it is not receiving any response from either the destination system or intermediary, but continues with the next ttl increment. • It may be a firewall, instead of a network failure. Multicast • Normally, an IP number refers to 1 host, but it can refer to many hosts on 1 or more networks. – Known as a multicast address • Multicasting: Sending a packet from 1 host to members of a multicast group Multicast Examples • Multimedia – Users "tune in" a video or audio transmission from a single source, but the source does not send to each individual. • Teleconferencing • Database – replicated database are updated at the same time • Distributed computation – intermediate results are sent to all participants. The sender need no even know who they are • Real-time workgroup – work is exchanged among active members in real time. Broadcast (briefly) • Broadcast sends data from one device to every other device on a local network – uses a broadcast specific address to a network topology – Devices MUST monitor and read any frame that is marked for the broadcast address – typically, 255 as the last octet. • 10.216.218.255 is the broadcast address for cosc. • 129.72.255.255 is the broadcast address for all of uwyo.edu. (very bad to use!) Vs Broadcast and Unicast • Broadcast sends the message to everyone on the network • Unicast sends to an individual • So if we have 5 members on 2 different networks – unicast must create and send 5 packets (1 for each member) for each packet sent. – broadcast must broadcast each packet to 2 networks. – Multicast sends 1 packet and each member gets the packet. Vs Broadcast and Unicast (2) • Unicast – more work for the source host, must create and send a packet for each member • Broadcast – Many (hundreds!) get "junk" packets. • Multicast – Source host sends only 1 packet to the group. The work is done on the routers (if there is more than 1 network/LAN involved). Multicast addresses • Multicast address are known as a Class D addresses – All IP address from 224.0.0.0 to 239.255.255.255 – there are ranges inside that are associated with a specific application service • All number 224.0.0.0 to 224.0.0.255 are predefined and reserved addresses for routing protocols and infrastructure services. – http://www.isi.edu/in-notes/iana/assignments/mulitcastaddresses Multicast addresses examples • 224.0.0.1 all local multicast hosts (including routers) and is never forwarded • 224.0.0.2 all local multicast routers and is never forwarded • 224.0.1.1 Network Time Protocol • 224.0.1.24 Microsoft's Windows Internet Name Server locator services (WINS) Layer 2: Data Link Layer • link layer services – error detection, correction – multiple access protocols and LANs – link layer addressing, ARP Link Layer: setting the context • two physically connected devices: – host-router, router-router, host-host • unit of data: frame M Ht M Hn Ht M Hl Hn Ht M application transport network link physical data link protocol phys. link adapter card network link physical Hl Hn Ht M frame CSMA: Carrier Sense Multiple Access CSMA: listen before transmit: • If channel sensed idle: transmit entire packet • If channel sensed busy, defer transmission – Persistent CSMA: retry immediately with probability p when channel becomes idle (may cause instability) – Non-persistent CSMA: retry after random interval • human analogy: don’t interrupt others! CSMA/CD (Collision Detection) CSMA/CD: carrier sensing, deferral as in CSMA – collisions detected within short time – colliding transmissions aborted, reducing channel wastage – persistent or non-persistent retransmission • collision detection: – easy in wired LANs: measure signal strengths, compare transmitted, received signals – difficult in wireless LANs: receiver shut off while transmitting • human analogy: the polite conversationalist LAN Addresses and ARP 32-bit IP address: • network-layer address • used to get datagram to destination network (recall IP network definition) LAN (or MAC or physical) address: • used to get the frame from one interface to another physically-connected interface (same network) • 48 bit MAC address (for most LANs) burned in the adapter ROM LAN Addresses and ARP Each adapter on LAN has unique LAN address LAN Address (more) • MAC address allocation administered by IEEE • manufacturer buys portion of MAC address space (to assure uniqueness) • Analogy: (a) MAC address: like Social Security Number (b) IP address: like postal address • MAC flat address => portability – can move LAN card from one LAN to another • IP hierarchical address NOT portable – depends on network to which one attaches Recall earlier routing discussion Starting at A, given IP datagram addressed to B: A • look up net. address of B, find B on same net. as A • link layer send datagram to B inside link-layer frame B frame source, dest address B’s MAC A’s MAC addr addr 223.1.1.1 223.1.2.1 223.1.1.2 223.1.1.4 223.1.2.9 223.1.1.3 223.1.3.1 223.1.3.27 223.1.2.2 223.1.3.2 datagram source, dest address A’s IP addr B’s IP addr datagram frame IP payload E ARP: Address Resolution Protocol Question: how to determine MAC address of B given B’s IP address? • Each IP node (Host, Router) on LAN has ARP module, table • ARP Table: IP/MAC address mappings for some LAN nodes < IP address; MAC address; TTL> < ………………………….. > – TTL (Time To Live): time after which address mapping will be forgotten (typically 20 min) ARP protocol • A knows B's IP address, wants to learn physical address of B • A broadcasts ARP query packet, containing B's IP address – all machines on LAN receive ARP query • B receives ARP packet, replies to A with its (B's) physical layer address • A caches (saves) IP-to-physical address pairs until information becomes old (times out) – soft state: information that times out (goes away) unless refreshed Routing to another LAN walkthrough: routing from A to B via R A R B • In routing table at source Host, find router 111.111.111.110 • In ARP table at source, find MAC address E6E9-00-17-BB-4B, etc • A creates IP packet with source A, destination B • A uses ARP to get R’s physical layer address for 111.111.111.110 • A creates Ethernet frame with R's physical address as dest, Ethernet frame contains A-to-B IP datagram • A’s data link layer sends Ethernet frame • R’s data link layer receives Ethernet frame • R removes IP datagram from Ethernet frame, sees its destined to B • R uses ARP to get B’s physical layer address • R creates frame containing A-to-B IP datagram sends to B A R B Layer 1 and 0 • For our discussions we don’t have to worry to much about layer 1 which is hardware NICs. Also hubs and repeaters. – Packet sniffing is done “mostly” at layer 2 and above. • Layer 0 is transmission media such as wiring for wired LANs. – This would be physical security issue and less a network issue. – Wireless Technology will be covered separately. References • Computer Networking, A Top-Down Approach featuring the Internet, Kurose and Ross, Addison Wesley, 2001 • Ethernet, The definitive Guide, Charles Spurgeon, O’Reilly, 2000. • Internet Core Protocols, The Definitive Guide, Hall, O'Reilly, 2000. • Cisco LAN Switch Configuration Guide, 1997 • Computer Networks, 3rd Edition, Andrew Tanenbaum, Prentice Hall, 1996 • Networking Essentials, 2nd Edition, Microsoft Press • Computer Networking with Internet Protocols and Technology, Stallings, Prentice Hall, 2003 • Computer Networks and Internets, 4th, Prentice Hall, 2003 • Internet Architectures, Minoli and Schmidt, Wiley, 1999 • Managing IP networks with Cisco Routers, Ballew, O'Reilly, 1997 • The Switch Book, The complete Guide to LAN Switching Technology, Seifert, Wiley, 2000 • Numerous websites Q&A