* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download IT 141: Information Systems I - Tonga Institute of Higher Education
Distributed firewall wikipedia , lookup
Computer security wikipedia , lookup
Net neutrality law wikipedia , lookup
Internet protocol suite wikipedia , lookup
Deep packet inspection wikipedia , lookup
Network tap wikipedia , lookup
Computer network wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Airborne Networking wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
UniPro protocol stack wikipedia , lookup
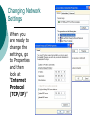
Tonga Institute of Higher Education IT 141: Information Systems Lecture 9: The Internet and Networking The network The network has enabled computers to enter a new realm of effectiveness and usability It evolves rapidly and new terms are always being introduced In this chapter we will learn about: Networking Basics Internet basics Internet access LANs – Local Area Networks Sending Data People realized early on how useful computers could be if they could send data to other computers. In 1948, Claude Shannon made a model of communications which we still use today Communications model In this model of communication: Data starts from its source It is encoded Transmitted over some sort of network Received by its recipient Decoded There may also be “noise” which means the data might be changed while being sent. It is important to make sure all the data sent is the right data. Most "protocols" (ways of sending data) have ways that check for errors. Encoding and Decoding The data has to be encoded before being sent. For computers, this means they must be encoded into binary. We have already seen one type of encoding, it is called ASCII. Characters are encoded into binary in ASCII How is data sent through a network When data is transmitted (sent) it is usually sent by electromagnetic signals This means the data will take different forms depending on the transmitter and receiver. For example, electronic voltages, radio waves, light waves or phone tones. To get the Internet in Tonga, think about all the different connections. Ethernet cables, satellites, underwater cables, phone lines Network Links A “communications channel” is the way data will travel through a network. Computers use many different types of methods (channels) to send data to the correct destination. Types of Links Twisted Pair cable – 4 copper wires twisted around each other. These are what are used for phone lines and Ethernet cables. They will end in a RJ-45 plug for Ethernet, or RJ-11 for a phone line Coax Cable – one wire that is surrounded by insulators to reduce data loss. Used for cable television and modems sometimes Fiber optic – A bundle of extremely small glass tubes. They do not use electric signals like the other cables, but use lasers instead. They are very fast and expensive Cable-less Types of Links Radio – Uses what is called RF signals (radio waves). Sent and received with a transceiver (a transmitter and receiver combined) Microwaves – These can carry a lot of data, but need a direct line of sight to work well Because radio and micro waves cannot bend to go around the curve of the earth, satellites are used in space to transmit signals around the globe Infrared light – uses light waves to transmit data. Only good for very short distances with clear line of sight Bandwidth Bandwidth the word describe how much data can be transmitted over a network link over a certain amount of time If the network is slow your "bandwidth" is small. To get a faster speed you may need to purchase a higher speed to obtain more bandwidth. If something has a lot of bandwidth it is called broadband (Ethernet networks, cable TV) If it has little bandwidth, it is called narrowband (phone lines, infrared) Network topology Network topology is how the computers connected together. 1) Star topology 2) Bus topology 3) Ring topology Ethernet networks use the Star Topology because there is a hub/switch that connects the devices together Ethernet vs. Token Ring Ethernet is the name for the way most networks are configured today. Packets are broadcasted over the whole network. If two packets run into each other, the Ethernet will allow them to resend them again Token Ring – older network configuration. It is slower. To prevent collisions of data, it uses a “token.” If a packet has the token, then it has priority to send itself. Then another packet uses that token to send data. Network Organization Workgroup (Peer-to-Peer) A workgroup is a group of computer connected by a LAN, but not sharing similar information, like usernames and passwords. This is commonly used in networks with less than five computers where each user has their own computer Domain (Client-Server) A domain allows all computers to be a part of a group that shares usernames, passwords and various settings. This allows a user to log into any computer on a network with the same password, as well as using the same settings Things in a network A node – A single device connected to a network is called a node Modem – uses phone lines to transmit data over a network Network Interface Card – a peripheral to connect to a local area network with Ethernet cable. Servers – a computer that provides services for other computers on a network Hub/Switch – a device that connects nodes on a network together (hub slow, switch fast) Router – connects two different networks together (like a local network and the internet) Repeater – amplifies signals on a network so that they don’t lose data to noise Routers Routers are similar to hubs in that they connect networks together, but routers are used to connect different networks together. Most of the time, you will use a router to connect your network to the Internet. It is a special device that determines where the data should go on your network. Either to the internet (or another network) or stay inside your LAN ROUTER HUB Network Addresses Every node on a network has at least one address so that other nodes know how to send data to it. A node may have other addresses depending on the protocols it uses. Address: Physical Address (network address, MAC address) Logical Address (IP address) Domain Name Physical Addresses A physical address is built into the hardware of a network interface card (NIC). This address may also be called the MAC address. Every NIC has a unique physical address. No other device will share the same address. The Logical Address - IP Addresses Besides the physical address, a computer needs a logical address that is used by the operating system and software in order to connect to other computers. IP addresses are the way that computers know where to send data. Every computer on a network has a different IP address The IP address is a series of numbers like 192.168.0.2 Each number can range from 0-255, which means each part is 8 bits (2^8 = 256). Since there are 4 parts, each IP address uses 32 bits. How many IP addresses can be used on the internet? Just over 4 billion. Dynamic and Static IPs If your IP address does not ever change, it is static. Usually servers and websites will have static IP addresses because other computers always need to know where to find them A dynamic IP address will change every time you connect to the internet. Usually, if you connect to the internet through a modem, you will have a dynamic IP If you have a dynamic IP, you can’t have a server on your computer Domain Names Computers may be able to remember and use IP addresses easily, but people have trouble remembering long numbers Domain names were invented so people have an easier time remembering the location of a server A domain name will “map” an IP address to a name Our domain name is tihe.org and our IP address is 209.58.72.33. Domain names will end in an extension that indicates something called the ‘toplevel’ domain. Example: .org, .to., .net Communications Protocol Protocol – a set of rules for communicating (talking). Commonly used to describe how computers send data over a network link Protocols for computers decide important things like Starting and ending transmissions Transmission errors The speed of data transmission How to format data TCP/IP and Network Protocols The most popular communications protocol is called TCP/IP (transmission control protocol / Internet protocol) It is used for transferring websites and email because it is able to safely send data without error. All computers that use TCP/IP know how to communicate with each other, even if they use different operating systems or are located in different countries. All modern networks use TCP/IP to transmit most data. Other protocols commonly used are UDP – for sending data quickly without checking for errors ICMP – for checking connections between computers Packets Most communication protocols will divide data into small pieces, called packets, when sending over a network link Packets contain the actual data, the destination address, and the address of the sender The receiver will wait until all the packets are received and then process the data Why packets? Why break up data into small parts? When people designed networks, they realized if data pieces were smaller it would be easier to manage. If one packet was lost it could be easily resent. If a big file was sent all at once and there was an error in the data, you’d have to send the whole big data file again With packets you just send small little pieces of data Internet Words The Internet – the global, public network that handles web sites, email and other data transmission LAN – Local area network – a small network in one location VPN (virtual private network) – allows access to a LAN from the internet with a password. WAN – wide area network – a network that covers a lot of space. The biggest WAN is the Internet Root Servers – a group of very powerful computers that know where to send all data on the Internet The Internet Started in 1969 as a U.S. government program to link computers together. At first, only a few people, mostly scientists and professors, had access to the internet. They knew the addresses of the computers that they wanted to connect to. There were no search engines and websites. The Internet only provided a way to connect to different computers separated by a great distance. By 1990, the Internet was becoming more userfriendly. Now there are at least 100 million computers on the Internet and there are popular protocols for sending email, accessing websites and transferring data ISPs – Internet Service Providers To connect to the internet, you need an ISP. Typically you can connect through a phone line, satellite, TV cable or a special direct line The ISP will have equipment like email servers, modems to connect users and a router to connect to the rest of the internet. NSPs ISPs then connect to Network Service Providers (NSPs). These are big telecommunications companies that provide access to the fast fiber optic cables that make up the "backbone" of the Internet. They might also connect through satellites, phone lines, TV cable lines, along with fiber optic lines How is data transferred Your computer connects to your ISP's LAN through a phone line. When that happens your computer is able to use their network resources This means you can use their router to connect to the NSP. The NSP will forward your data to the correct place and you will receive a reply Your data can be sent using one of many types of protocols for transferring data. One of the most popular is TCP/IP which breaks the data into packets and formats it in a certain way. TCP/IP is used whenever a connection must be established between two places. For example, to make sure email is correctly sent both computers must connect and talk to each other successively before the email can be transferred. Other Protocols TCP/IP is the foundation of most other protocols. It is responsible for breaking data and sending it over long distances. There are other protocols (see below) that work to help communication between different services. For example, a web browser and a web server use HTTP in order to discuss how to retrieve web pages. The information they use to communicate is then broken up according to the TCP/IP protocol and then sent Domain Name Servers The Internet would not be popular without easy to remember names. Every computer on the Internet needs an IP address, but numbers are hard to remember, so Domain Name Servers (DNS) provide a way for you to turn a name into an IP address or an IP address into a name. With this service, you can type in a name, your computer than asks a DNS server for the IP, gets an IP, then sends the data to that IP address Connecting to the Internet - Modems The most common way to get on the internet is through a modem A modem will dial an ISP over a regular phone line. The ISP will have a computer pick up the phone call. The ISP will then send your data through its network service provider Modem Speeds Modem speed is measured in “baud” rate, or the number of bits it can send per second over the phone line. There is a maximum baud rate of 56 Kbps, but the speed also relies on the quality of the phone lines and the connection Most of the time, you will not be able to go faster than 44Kbps for downloads Direct Connections (DSL,ISDN,T1,T3) Your internet session will last only until you disconnect with a modem. Newer technology lets your computer always be connected to the internet. ISDN – direct connection using special phone lines DSL – digital subscriber line – carries your data over existing phone lines, but much faster T1/T3 – Very expensive, very fast. You have to lease cable lines from the phone company for this connection. LAN Security If your network or computer is always connected to the internet, your computer might be vulnerable to hackers (someone who tries to take over control of your computer) One way to protect your network is with a "firewall" A firewall is a device (or computer) that examines all data coming into a network link and decides whether to allow it to pass through or deny it. Hackers need to send data to computers in order to take over. If it cannot send data, it cannot take over the computer Setting up a simple LAN Setting up a LAN is not difficult. First you must connect each computer with an Ethernet cable to a hub/switch. When you make a successful connection (and your cable is good) you will see a light appear on the hub. You must do this for the other computers as well After physically connecting, you must change the network configuration on each computer to the accurate information so each computer can connect Changing network properties After you log onto the Windows XP computer, go to Start -> Control Panel -> Network Connections This will allow you to view and change network configuration information Changing Network Settings With network connections open, you will see a picture that represents your Ethernet Card. It will give the name of your Ethernet Card and tell if it is connected properly or not. When you doubleclick on this you can change important settings Changing Network Settings You can view your network settings by looking at the support option. This will tell you things like IP address, gateway and netmask. If you look at “Details,” you can see even more information about your settings. Changing Network Settings When you are ready to change the settings, go to Properties and then look at “Internet Protocol (TCP/IP)” What numbers should I put in? Click on “Use the following IP address” This allows you to enter the IP address Because you will be making a private LAN, you should use the following form: “192.168.0.x” This is a set of numbers that is reserved just for LANs Usually the server on a network has the first number (192.168.0.1) and other computers come after. You are free to use any numbers between 1254. If you use 0 or 255, there could be problems For the first computer, use 192.168.0.1 and the second, 192.168.0.2 What numbers should I put in? For the netmask, you should use 255.255.255.0. You will almost always use this number for all networks. It is not necessary to have a gateway You only need a gateway if you will be connecting your LAN to the Internet. The gateway is another word for your router, and the gateway number is the IP address of your router. This router IP address is used when data will not travel to another computer on your LAN. Your computer will determine that the data must be sent to another network and it will then use the router The same goes for DNS. You can leave both blank unless you are using the Internet. If you are using the Internet you will get these IP numbers from your Internet provider (ISP). Static and Dynamic IP addresses Why is there a button that says, “Obtain IP address automatically” and “Use the following IP address” If you obtain an IP address automatically, it means that you are using a Dynamic IP address. This means that your IP address will change every time the computer starts Where does it get the IP from? A server will give computers IP address. This service is called “DHCP” and it means that when a computer starts, it will ask a server for an IP address Then the server will give it one. When you put the numbers in yourself, it means that you are using a Static IP address (because it will not change) Checking Networks After we enter the numbers and press “OK” how do we know if the network is working? The first thing to check is that the IP was set correctly and the computer accepts it. We can use a program from the command line called “ipconfig” to check the IP settings Checking Networks We also want to check to see if the network is working. How can we tell if computers are talking to each other? There is a program called “ping” that we use to check a network connection It sends a little piece of data to another computer. If the computer gets it, the computer will respond. This will show you if the network is correctly set up Summary Network physical structure and communications protocol How the internet works TCP/IP and domain names Connection devices LANs