NetAdmin
... • Whatever value is specified with the bandwidth command, EIGRP always takes 50% of it (by default). • Remember: The bandwidth command is only used by routing protocols—it has no effect on user traffic when the protocol is EIGRP. The router does not use this command for any other purpose. • For exam ...
... • Whatever value is specified with the bandwidth command, EIGRP always takes 50% of it (by default). • Remember: The bandwidth command is only used by routing protocols—it has no effect on user traffic when the protocol is EIGRP. The router does not use this command for any other purpose. • For exam ...
Abstract: The Internet Engineering Task force began an effort to
... restricted to traditional IPv4 operation and hosts equipped with IPv6 capability. To allow seamless interoperation, all hosts running IPng must still be able to communicate with the older technology. On the application level software designed for IPv4 uses the older API while new IPng applications u ...
... restricted to traditional IPv4 operation and hosts equipped with IPv6 capability. To allow seamless interoperation, all hosts running IPng must still be able to communicate with the older technology. On the application level software designed for IPv4 uses the older API while new IPng applications u ...
Wireless Application Development Issues
... In the very recent past, major technology changes have been introduced which are transforming the way we live and work. Foremost among these are the technologies used to move information along the Internet, the “information super-highway”. Individuals and companies are in the early stages of underst ...
... In the very recent past, major technology changes have been introduced which are transforming the way we live and work. Foremost among these are the technologies used to move information along the Internet, the “information super-highway”. Individuals and companies are in the early stages of underst ...
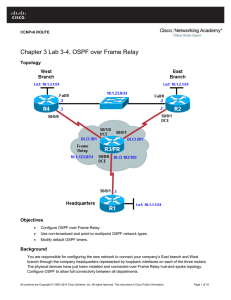
Chapter 3 Lab 3-4, OSPF over Frame Relay
... a. Configure the routers to send five hellos a second. __________________________________________________________________________________ __________________________________________________________________________________ ...
... a. Configure the routers to send five hellos a second. __________________________________________________________________________________ __________________________________________________________________________________ ...
CT-500S ADSL Router User`s Manual
... An RS232 straight-through cable to connect to the Console PortAn RS232, DB9-to-DB9 straight-through cable is required to connect the terminal to the device. An AC power adapter cord to connect to the Power jackA suitable AC-to-AC power adapter cord is shipped with the device. It is used to provide t ...
... An RS232 straight-through cable to connect to the Console PortAn RS232, DB9-to-DB9 straight-through cable is required to connect the terminal to the device. An AC power adapter cord to connect to the Power jackA suitable AC-to-AC power adapter cord is shipped with the device. It is used to provide t ...
Manual: Emerson Smart Wireless Gateway 1410
... networks with host systems and data applications. Modbus® communications over RS-485 or Ethernet provide universal integration and system interoperability. The optional OPC or EtherNet/IP functionality from the Gateway offers a means to connect to newer systems and applications while providing a ric ...
... networks with host systems and data applications. Modbus® communications over RS-485 or Ethernet provide universal integration and system interoperability. The optional OPC or EtherNet/IP functionality from the Gateway offers a means to connect to newer systems and applications while providing a ric ...
Chapter
... • The Internet was initially based on a besteffort packet delivery service • Today's Internet carries many more different applications than 20 years ago • Some applications have special bandwidth and/or delay requirements • The Integrated Services model (RFC1633) was introduced to guarantee a predic ...
... • The Internet was initially based on a besteffort packet delivery service • Today's Internet carries many more different applications than 20 years ago • Some applications have special bandwidth and/or delay requirements • The Integrated Services model (RFC1633) was introduced to guarantee a predic ...
Tracetree: A Scalable Mechanism to Discover Multicast Tree Topologies in the Internet
... NOC personnel within a domain. However, it is not accessible by ordinary end users in the domain and it is also not effective in the interdomain. As a result, mmon (or any other SNMP-based topology discovery tool) is effective at discovering multicast (sub)tree topologies within a domain only. MHeal ...
... NOC personnel within a domain. However, it is not accessible by ordinary end users in the domain and it is also not effective in the interdomain. As a result, mmon (or any other SNMP-based topology discovery tool) is effective at discovering multicast (sub)tree topologies within a domain only. MHeal ...
uBR 10000 Series High-End Broadband Router
... hardware for almost 2 years • Many features of DOCSIS 1.1 already in shipping software • Full DOCSIS 1.1 was supported in production code, March 2001 ...
... hardware for almost 2 years • Many features of DOCSIS 1.1 already in shipping software • Full DOCSIS 1.1 was supported in production code, March 2001 ...
1. Use Cases
... and Motorola predefined). 2. Parse the configuration file and finish the construction of the MIBTree according to the parsed information in the configuration file. 3. Pass the MIBTree to the Agent module. 4. Register Traps (TrapInfo objects) to the Monitor module using/scanning the MIBTree. 2a. If t ...
... and Motorola predefined). 2. Parse the configuration file and finish the construction of the MIBTree according to the parsed information in the configuration file. 3. Pass the MIBTree to the Agent module. 4. Register Traps (TrapInfo objects) to the Monitor module using/scanning the MIBTree. 2a. If t ...
Multicast Over Wireless Networks
... • After finishing transmission, prepare to transmit next packet and go to step A (no waiting for feedback). • The next step is executed only when multicast transmission occurs in step C. ...
... • After finishing transmission, prepare to transmit next packet and go to step A (no waiting for feedback). • The next step is executed only when multicast transmission occurs in step C. ...
Energy-Aware Adaptive Routing Solutions in IP-over-WDM Networks Filip Idzikowski
... saving and the Quality of Service (QoS) guarantees. EWA is compared with the Least Flow Algorithm (LFA) and the Genetic Algorithm (GA) taking power and energy consumption, reconfigured traffic, and overload ratio as evaluation metrics. The evaluation is performed on unique network scenarios. Differe ...
... saving and the Quality of Service (QoS) guarantees. EWA is compared with the Least Flow Algorithm (LFA) and the Genetic Algorithm (GA) taking power and energy consumption, reconfigured traffic, and overload ratio as evaluation metrics. The evaluation is performed on unique network scenarios. Differe ...
IEEE Report Jul 99 - IEEE Communications Society
... • New 802 Project approved by IEEE Standards Board Dec. 2000 as IEEE 802.17 Resilient Packet Ring WG • Packet Ring Access Protocol for use in Local, Metropolitan and Wide Area Networks • Transfer of packets at rates scalable to many gigabits per ...
... • New 802 Project approved by IEEE Standards Board Dec. 2000 as IEEE 802.17 Resilient Packet Ring WG • Packet Ring Access Protocol for use in Local, Metropolitan and Wide Area Networks • Transfer of packets at rates scalable to many gigabits per ...
Chapter 1 - Introduction
... – RIP measures distance in network hops • where each network between the source and destination counts as a single hop ...
... – RIP measures distance in network hops • where each network between the source and destination counts as a single hop ...
EWS Core Question Bank
... through the fibre is known as ………… a) absorption b) refraction c) attenuation The correct answer is c) attenuation 132. Safety loss, added by system designers is of the value …… dB. a) 1 dB b) .5 dB c) 2 dB The correct answer is b ) .5 dB 133. The ITUT standard for non dispersion shifted, Single Mod ...
... through the fibre is known as ………… a) absorption b) refraction c) attenuation The correct answer is c) attenuation 132. Safety loss, added by system designers is of the value …… dB. a) 1 dB b) .5 dB c) 2 dB The correct answer is b ) .5 dB 133. The ITUT standard for non dispersion shifted, Single Mod ...
EPL-Router sorgt für Transparenz und Durchgängigkeit
... throughout the world thousands of end users have more than 210000 nodes installed in more than 28000 machines. More than 200 mechanical engineers bank on Ethernet Powerlink. Soon Ethernet Powerlink will be part of the standards IEC 61748-2 and IEC 61158. The original physical level is 100Base-X Fast ...
... throughout the world thousands of end users have more than 210000 nodes installed in more than 28000 machines. More than 200 mechanical engineers bank on Ethernet Powerlink. Soon Ethernet Powerlink will be part of the standards IEC 61748-2 and IEC 61158. The original physical level is 100Base-X Fast ...
PPT
... playback can lag tens of seconds after transmission still have timing constraint Interactivity fast forward impossible rewind, pause possible! CPSC 441: Multimedia Networking ...
... playback can lag tens of seconds after transmission still have timing constraint Interactivity fast forward impossible rewind, pause possible! CPSC 441: Multimedia Networking ...
Chapter 27 PPT
... – RIP measures distance in network hops • where each network between the source and destination counts as a single hop ...
... – RIP measures distance in network hops • where each network between the source and destination counts as a single hop ...