485-CCU HUB - Tyco Safety Products ANZ
... the CCU/IO-485 to port A or B of the CCU/485-IO using the following connection diagram. Up to eight CCU/IO-485 boards can be chained off one channel of the CCU/485-IO, giving up to 16 CCU/IO-485 boards connected to one CCU/485-IO. Appendix A contains information on wiring for this configuration. Che ...
... the CCU/IO-485 to port A or B of the CCU/485-IO using the following connection diagram. Up to eight CCU/IO-485 boards can be chained off one channel of the CCU/485-IO, giving up to 16 CCU/IO-485 boards connected to one CCU/485-IO. Appendix A contains information on wiring for this configuration. Che ...
Routing - La Salle University
... • Bridges help reduce traffic because a bridge “learns” whether it filters or forwards a frame. • Unicast messages do not have to be forwarded to all segments but only to those connecting the source and destination. • This allows different segments to transmit different signals simultaneously (in pa ...
... • Bridges help reduce traffic because a bridge “learns” whether it filters or forwards a frame. • Unicast messages do not have to be forwarded to all segments but only to those connecting the source and destination. • This allows different segments to transmit different signals simultaneously (in pa ...
Routing - La Salle University
... (in the TTL time-to-live field). Each router reduces the number by one. When the TTL reaches 0, the ...
... (in the TTL time-to-live field). Each router reduces the number by one. When the TTL reaches 0, the ...
1 - Blonder Tongue Laboratories Inc.
... equipped with an Emergency Alert System (EAS) interface. A front-panel RF test point allows for monitoring/testing of the QAM output without service interruption. Comprehensive remote monitoring and control is accomplished using any standard Web browser via a front-panel 10/100BaseT Ethernet connect ...
... equipped with an Emergency Alert System (EAS) interface. A front-panel RF test point allows for monitoring/testing of the QAM output without service interruption. Comprehensive remote monitoring and control is accomplished using any standard Web browser via a front-panel 10/100BaseT Ethernet connect ...
Activity 6.4.1: Basic VLSM Calculation and
... Activity 6.4.1: Basic VLSM Calculation and Addressing Design Topology Diagram ...
... Activity 6.4.1: Basic VLSM Calculation and Addressing Design Topology Diagram ...
CHAPTER ONE
... the most likely choke points. A DSL modem is the most common small network example, with between 10 and 1000 Mbit/s of incoming bandwidth and at most 8 Mbit/s of outgoing bandwidth. The prevention of congestion collapse requires two major components: A mechanism in routers to reorder or drop packets ...
... the most likely choke points. A DSL modem is the most common small network example, with between 10 and 1000 Mbit/s of incoming bandwidth and at most 8 Mbit/s of outgoing bandwidth. The prevention of congestion collapse requires two major components: A mechanism in routers to reorder or drop packets ...
Tapestry: A Resilient Global-scale Overlay for Service Deployment
... hops available, and use runtime heuristics to assist. In contrast, Tapestry and Pastry construct locally optimal routing tables from initialization, and maintain them in order to reduce routing stretch. While some systems fix the number and location of object replicas by providing a distributed hash ...
... hops available, and use runtime heuristics to assist. In contrast, Tapestry and Pastry construct locally optimal routing tables from initialization, and maintain them in order to reduce routing stretch. While some systems fix the number and location of object replicas by providing a distributed hash ...
Cisco Inter-network Operating System (IOS) A short guide for the
... and provide Caching, Packet Buffering, and hold Routing Tables. The RAM is also where the Running Operating System lives when the Router is on. RAM loses all its data when reset or powered off. ...
... and provide Caching, Packet Buffering, and hold Routing Tables. The RAM is also where the Running Operating System lives when the Router is on. RAM loses all its data when reset or powered off. ...
MuON: Epidemic Based Mutual Anonymity
... frequently leave/join the network and most peers are connected to the overlay for a short period of time. Similarly ...
... frequently leave/join the network and most peers are connected to the overlay for a short period of time. Similarly ...
Basics of network lab - PolyU
... An IP address is a unique network layer numbering system that end systems use in order to identify and communicate with each other. It is a dotted decimal notation with four numbers ranging from 0 to 255 separated by periods. The numbers currently used in IP addresses range from 1.0.0.0 to 255. 255. ...
... An IP address is a unique network layer numbering system that end systems use in order to identify and communicate with each other. It is a dotted decimal notation with four numbers ranging from 0 to 255 separated by periods. The numbers currently used in IP addresses range from 1.0.0.0 to 255. 255. ...
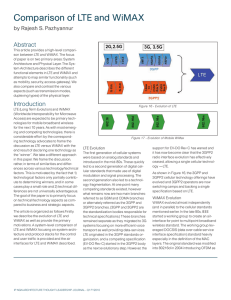
Comparison of LTE and WiMAX
... transport. The specific control messages transferred differ as well and are defined by corresponding specifications: S1 for LTE and R6 for WiMAX. A function unique to MME and S-GW is to interface with legacy 3G networks ...
... transport. The specific control messages transferred differ as well and are defined by corresponding specifications: S1 for LTE and R6 for WiMAX. A function unique to MME and S-GW is to interface with legacy 3G networks ...
245U-E (English)
... 4. The Equipment shall be powered using an external Listed Power Supply with LPS outputs, or a Class 2 Power Supply. 5. The Wireless Ethernet module must be properly grounded for surge protection before use. 6. If installed in a hazardous environment, coaxial cable shall be installed in a metalli ...
... 4. The Equipment shall be powered using an external Listed Power Supply with LPS outputs, or a Class 2 Power Supply. 5. The Wireless Ethernet module must be properly grounded for surge protection before use. 6. If installed in a hazardous environment, coaxial cable shall be installed in a metalli ...
Quality of Service in mobile ad hoc networks: a
... the routes between a source and a destination are often multihop. As there are no separate routers, nodes that are part of the network need to cooperate with each other for relaying packets of one another towards their ultimate destinations. The devices are often operated through batteries, the depl ...
... the routes between a source and a destination are often multihop. As there are no separate routers, nodes that are part of the network need to cooperate with each other for relaying packets of one another towards their ultimate destinations. The devices are often operated through batteries, the depl ...
Activity 6.4.1: Basic VLSM Calculation and Addressing Design
... Task 2: Design an IP Addressing Scheme Step 1: Determine the subnet information for the largest network segment or segments. In this case, the two HQ LANs are the largest subnets. 1. How many IP addresses are needed for each LAN? _______ 2. What is the smallest size subnet that can be used to meet t ...
... Task 2: Design an IP Addressing Scheme Step 1: Determine the subnet information for the largest network segment or segments. In this case, the two HQ LANs are the largest subnets. 1. How many IP addresses are needed for each LAN? _______ 2. What is the smallest size subnet that can be used to meet t ...
Wireless USB for HomeRF-Lite
... – keep a counter running so that it could predict which hop frequency the light would have reached or – use the inquiry procedure to find the light each time the switch was operated. Month Year ...
... – keep a counter running so that it could predict which hop frequency the light would have reached or – use the inquiry procedure to find the light each time the switch was operated. Month Year ...
BACnet Router FS-ROUTER-BAC
... Web Based configuration with no additional software needed for configuration NAT support with secondary BACnet/IP connection for routing between public and private IP networks Foreign Device Registration (FDR), exposing devices details on different subnets Ease of Installation MDIX to use an ...
... Web Based configuration with no additional software needed for configuration NAT support with secondary BACnet/IP connection for routing between public and private IP networks Foreign Device Registration (FDR), exposing devices details on different subnets Ease of Installation MDIX to use an ...
Raven and PinPoint GPRS User Guide
... of radio interference. In such areas, the AirLink Communications modem MUST BE POWERED OFF. The AirLink Communications modem can transmit signals that could interfere with this equipment. Do not operate the AirLink Communications modem in any aircraft, whether the aircraft is on the ground or in fli ...
... of radio interference. In such areas, the AirLink Communications modem MUST BE POWERED OFF. The AirLink Communications modem can transmit signals that could interfere with this equipment. Do not operate the AirLink Communications modem in any aircraft, whether the aircraft is on the ground or in fli ...
Chapter 4 Socket Programming Preliminary
... table is used to manage the sockets for this process. — Different processes use different SDTs. ...
... table is used to manage the sockets for this process. — Different processes use different SDTs. ...
CS610 Final term MAGA file.. all paperz are in 1 file..pages 1 to 42
... We want to TX the binary data unit 1100001 Adding together the number of 1’s gives us 3, an odd number Before TX, we pass the data unit through a parity generator, which counts the 1’s and appends the parity bit (1) to the end The total number of 1’s is now 4, an even number The system now transfers ...
... We want to TX the binary data unit 1100001 Adding together the number of 1’s gives us 3, an odd number Before TX, we pass the data unit through a parity generator, which counts the 1’s and appends the parity bit (1) to the end The total number of 1’s is now 4, an even number The system now transfers ...
Slide presentation with simulation results - OSPF
... RFC 5243 describes a new database exchange optimization that was originally part of OSPF-MDR, but applies to OSPF in general. – A router does not list an LSA in DD packets sent to a neighbor, if the same or a more recent instance of the LSA was listed in a DD packet already received from the neighbo ...
... RFC 5243 describes a new database exchange optimization that was originally part of OSPF-MDR, but applies to OSPF in general. – A router does not list an LSA in DD packets sent to a neighbor, if the same or a more recent instance of the LSA was listed in a DD packet already received from the neighbo ...
IP: Addresses and Forwarding
... Fully distributed approach: a consistency criterion or invariant across the states of adjacent nodes Signaled approach: the signaling protocol sets up local forwarding information along the path.Shivkumar Kalyanaraman ...
... Fully distributed approach: a consistency criterion or invariant across the states of adjacent nodes Signaled approach: the signaling protocol sets up local forwarding information along the path.Shivkumar Kalyanaraman ...