An Overlay MAC Layer for 802.11 Networks Ananth Rao Ion Stoica UC Berkeley
... which do not experience similar problems. Asymmetric Carrier Sense: We conduct our first set of experiments using broadcast packets only. This allows us to better understand the interaction between senders, as broadcast communication abstracts away the ACKs and packet retransmissions at the MAC laye ...
... which do not experience similar problems. Asymmetric Carrier Sense: We conduct our first set of experiments using broadcast packets only. This allows us to better understand the interaction between senders, as broadcast communication abstracts away the ACKs and packet retransmissions at the MAC laye ...
Before You Begin: Assign Information Classification
... A physical topology defines the way in which computers, printers, and other ...
... A physical topology defines the way in which computers, printers, and other ...
CN 2015 1-2 - DSpace
... When connection is established, it is used for all the traffic. When connection is released, the virtual circuit is terminated. Every router has to maintain a table. ...
... When connection is established, it is used for all the traffic. When connection is released, the virtual circuit is terminated. Every router has to maintain a table. ...
Immediate ECN
... ...if the ECT codepoint is set in that packet's IP header ... then instead of dropping the packet, the router MAY instead set the CE codepoint in the IP header. An environment where all end nodes were ECN-Capable could allow new criteria to be developed for setting the CE codepoint, and new congesti ...
... ...if the ECT codepoint is set in that packet's IP header ... then instead of dropping the packet, the router MAY instead set the CE codepoint in the IP header. An environment where all end nodes were ECN-Capable could allow new criteria to be developed for setting the CE codepoint, and new congesti ...
CN26622627
... We can see that the more the attacker increases the Dst Seq, the lower the packet delivery rate is. Next, we investigate the packet delivery ratio from node 0 to node 1 when destination node 1 generates traffic to other nodes. We assume that destination node 1 generates traffic toward other nodes in ...
... We can see that the more the attacker increases the Dst Seq, the lower the packet delivery rate is. Next, we investigate the packet delivery ratio from node 0 to node 1 when destination node 1 generates traffic to other nodes. We assume that destination node 1 generates traffic toward other nodes in ...
BODi Multi-WAN BONDING
... The BODi product family uses a proprietary VPN Bonding Protocol to establish a peer to peer connection over multiple WAN interfaces. – VPN BONDING only works BODi to BODi – This can be configured with or without AES 256 Encryption. – The VPN BOND can have multiple end-points configured on both sides ...
... The BODi product family uses a proprietary VPN Bonding Protocol to establish a peer to peer connection over multiple WAN interfaces. – VPN BONDING only works BODi to BODi – This can be configured with or without AES 256 Encryption. – The VPN BOND can have multiple end-points configured on both sides ...
Towards an Accurate AS-level Traceroute Tool
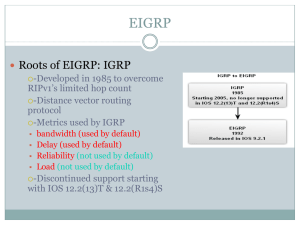
... Optimize routes taken between points within a network Internal Gateway Protocols (IGPs) ...
... Optimize routes taken between points within a network Internal Gateway Protocols (IGPs) ...
IPv6
... IPv6 Features • Header Format – very different from IPv4 • Extension Headers • IPv6 encodes information into separate headers • A datagram consists of the base IPv6 header followed by zero or more extension headers, followed by data ...
... IPv6 Features • Header Format – very different from IPv4 • Extension Headers • IPv6 encodes information into separate headers • A datagram consists of the base IPv6 header followed by zero or more extension headers, followed by data ...
9.4.2 CSMA/CD – The Process
... 9.4.3 Ethernet Timing Ethernet with throughput speeds of 10 Mbps and slower are asynchronous. An asynchronous communication in this context means that each receiving device will use the 8 bytes of timing information to synchronize the receive circuit to the incoming data and then discard the 8 by ...
... 9.4.3 Ethernet Timing Ethernet with throughput speeds of 10 Mbps and slower are asynchronous. An asynchronous communication in this context means that each receiving device will use the 8 bytes of timing information to synchronize the receive circuit to the incoming data and then discard the 8 by ...
Cooper Bussmann 945U-E Wireless Ethernet Modem & Device Server User Manual
... installed as recommended in the Installation Guide. 4. To avoid accidents during maintenance or adjustment of remotely controlled equipment, all equipment should be first disconnected from the 945U-E module during these adjustments. Equipment should carry clear markings to indicate remote or automa ...
... installed as recommended in the Installation Guide. 4. To avoid accidents during maintenance or adjustment of remotely controlled equipment, all equipment should be first disconnected from the 945U-E module during these adjustments. Equipment should carry clear markings to indicate remote or automa ...
Cisco Catalyst 6500/Cisco 7600 Series Supervisor Engine
... The Cisco Catalyst 6500/Cisco 7600 Series Supervisor Engine 720 is a family of Supervisor Engine(s) designed to deliver scalable performance and rich set of IP features in hardware. Its hardware-based feature set enables applications such as traditional IP forwarding, Layer 2 and Layer 3 Multiprotoc ...
... The Cisco Catalyst 6500/Cisco 7600 Series Supervisor Engine 720 is a family of Supervisor Engine(s) designed to deliver scalable performance and rich set of IP features in hardware. Its hardware-based feature set enables applications such as traditional IP forwarding, Layer 2 and Layer 3 Multiprotoc ...
Interphase 4515 / 4525 / 4575 Manual
... This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15, Subpart B of the FCC Rules. This equipment generates, uses, and can radiate radio frequency energy. If not installed and used in accordance with the instructions, it may cause interf ...
... This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15, Subpart B of the FCC Rules. This equipment generates, uses, and can radiate radio frequency energy. If not installed and used in accordance with the instructions, it may cause interf ...
MPLS
... With VPN, the traffic of a given enterprises or group passes transparently through the Internet in a way that effectively segregates that traffic from other packets on the Internet. MPLS provides an efficient mechanism for supporting VPNs proving performance guarantees and security. LSP - Label ...
... With VPN, the traffic of a given enterprises or group passes transparently through the Internet in a way that effectively segregates that traffic from other packets on the Internet. MPLS provides an efficient mechanism for supporting VPNs proving performance guarantees and security. LSP - Label ...
Host-to-host congestion control for TCP
... for shared network resources, the aggregate rate of all TCP senders sharing the same network can easily exceed (and in practice do exceed) the capacity of the network. It is commonly known in the flow-control world that if the offered load in an uncontrolled distributed sharing system (e.g., road tr ...
... for shared network resources, the aggregate rate of all TCP senders sharing the same network can easily exceed (and in practice do exceed) the capacity of the network. It is commonly known in the flow-control world that if the offered load in an uncontrolled distributed sharing system (e.g., road tr ...
Presentation - Constantia Fibre
... Speed of Deployment – The novel deployment methods enabled by the FOCUS™ technology reduces the need for civil construction methods and greatly accelerates the rate at which infrastructure can be deployed. FOCUS™ Backbone and last-mile networks are deployed five times faster than traditional trenchi ...
... Speed of Deployment – The novel deployment methods enabled by the FOCUS™ technology reduces the need for civil construction methods and greatly accelerates the rate at which infrastructure can be deployed. FOCUS™ Backbone and last-mile networks are deployed five times faster than traditional trenchi ...
MPLS QoS - Lyle School of Engineering
... carrying complete explicit route is prohibitive – MPLS allows explicit route to be carried only at the time the LSP is setup, and not with each packet – MPLS makes explicit routing practical ...
... carrying complete explicit route is prohibitive – MPLS allows explicit route to be carried only at the time the LSP is setup, and not with each packet – MPLS makes explicit routing practical ...
IPSec
... – Operates at the Network layer – Not supported by pre-Windows 2000 operating systems – Cannot be used with NAT – AH mode does not perform data encryption – ESP mode has ability to perform data encryption and authentication – Transport mode is used between two hosts – Tunnel mode is used between two ...
... – Operates at the Network layer – Not supported by pre-Windows 2000 operating systems – Cannot be used with NAT – AH mode does not perform data encryption – ESP mode has ability to perform data encryption and authentication – Transport mode is used between two hosts – Tunnel mode is used between two ...
the document - Support
... High planning, deployment, and optimization skill requirements on operation personnel because hardware devices may be provided by different vendors ...
... High planning, deployment, and optimization skill requirements on operation personnel because hardware devices may be provided by different vendors ...
Performance Evaluation and Comparison of Facsimile Transmission
... In a packet based network or IP network data is transmitted as packets. In real-time facsimile transmission the facsimile documents are send from one facsimile device to another in real-time over the IP network using the FoIP (Fax over IP) gateways [11]. The sending device segments the data into ind ...
... In a packet based network or IP network data is transmitted as packets. In real-time facsimile transmission the facsimile documents are send from one facsimile device to another in real-time over the IP network using the FoIP (Fax over IP) gateways [11]. The sending device segments the data into ind ...
Investigation on Material Dispersion as a Function of Pressure and
... (LED) or a laser at one end of the fiber. Optical networks are high-capacity telecommunications networks based on optical technologies and components that provide routing, grooming, and restoration at the wavelength level as well as wavelength based services. Most optical networks are used to carry ...
... (LED) or a laser at one end of the fiber. Optical networks are high-capacity telecommunications networks based on optical technologies and components that provide routing, grooming, and restoration at the wavelength level as well as wavelength based services. Most optical networks are used to carry ...