* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download VLANs
Point-to-Point Protocol over Ethernet wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
Wireless security wikipedia , lookup
Internet protocol suite wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Distributed firewall wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Computer network wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Deep packet inspection wikipedia , lookup
Telephone exchange wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Airborne Networking wikipedia , lookup
Wake-on-LAN wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Network tap wikipedia , lookup
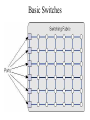
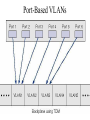
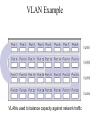
Virtual LAN Design • Switches also have enabled the creation of Virtual LANs (VLANs). VLANs provide greater opportunities to manage the flow of traffic on the LAN and reduce broadcast traffic between segments. • VLANs are groups of computers in an intelligent switched network. • Before getting into VLANs let’s revisit switches... Basic Switches Intelligent Switches • Intelligent switches support larger networks than the basic switch’s 8- or 16- port LANs. • As well as being able to support far more computers or network connections, the key advantage is in the modularity of intelligent switches (might add an ATM, Fiber module). • These switches often can support several hundred ports spread over a dozen or more different modules. Intelligent Switches • For most switches there is not enough capacity in the switching fabric / backplane to support all ports if they become active so the switch forms groups of connections and assigns capacity using time division multiplexing. • This means that the switch no longer guarantees simultaneous transmission on all ports, but will accept simultaneous input and will switch incoming data to outgoing ports as fast as possible. • The groups are called VLANs VLANS • VLANs can be seen as analogous to a group of endstations, perhaps on multiple physical LAN segments, that are not constrained by their physical location and can communicate as if they were on a common LAN • Big wins – Broadcast traffic is limited to the VLAN • Consider a big network across an entire campus on 1 switch, there would be too much broadcast traffic! – VLANs can be assigned and managed dynamically without physical limitations – VLAN can be used to balance bandwidth allotment per group VLAN introduction VLANs logically segment switched networks based on the functions, project teams, or applications of the organization regardless of the physical location or connections to the network. All workstations and servers used by a particular workgroup share the same VLAN, regardless of the physical connection or location. VLAN introduction VLANs function by logically segmenting the network into different broadcast domains so that packets are only switched between ports that are designated for the same VLAN. Routers in VLAN topologies provide broadcast filtering, security, and traffic flow management. Port-Based VLANs (Layer-1 VLANs) • Port-based VLANs use the physical port address to form the groups for the VLAN. • It is logical to connect computers that are physically close together on the LAN into ports that are physically close together on the switch, and to assign ports that are physically close together into the same VLAN. • This is the approach used in traditional LAN design: physical location determines the LAN, but is not always the most effective approach. Port-Based VLANs VLAN Example VLANs used to balance capacity against network traffic MAC-Based VLANs Layer-2 VLANs • MAC-based VLANs use the same data link layer addresses to form the VLAN groups. • The advantage is that they are simpler to manage when computers are moved. IP-Based VLANs Layer-3 VLANs • IP-based VLANs use the network layer address (i.e. TCP/IP address) to form the VLAN groups. Layer-3 VLANs reduce the time spent reconfiguring the network when a computer is moved as well. • Some layer-3 VLANs can also use the network layer protocol to create VLAN groups. This flexibility enables manager even greater precision in the allocation of network capacity. Application-Based VLANs Layer-4 VLANs • Application-based VLANs use the application layer protocol in combination with the data link layer and network layer addresses to form the VLAN groups. • The advantage is a very precise allocation of network capacity. Some requirements of LANs • Need to split up broadcast domains to make good use of bandwidth • People in the same department may need to be grouped together for access to servers • Security: restrict access by certain users to some areas of the LAN • Provide a way for different areas of the LAN to communicate with each other Solution using routers • Divide the LAN into subnets • Use routers to link the subnets Solution using routers BUT • Routers are expensive • Routers are slower than switches • Subnets are restricted to limited physical areas • Subnets are inflexible Types of VLAN • • • • • Data or user VLAN Voice VLAN Management VLAN Native VLAN Default VLAN Data VLAN • Carry files, e-mails, shared application traffic, most user traffic. • Separate VLAN for each group of users. Voice VLAN • • • • Use with IP phone. Phone acts as a switch too. Voice traffic is tagged, given priority. Data not tagged, no priority. Management VLAN • Has the switch IP address. • Used for telnet/SSH or web access for management purposes. • Better not to use VLAN 1 for security reasons. Native VLAN • • • • • For backward compatibility with older systems. Relevant to trunk ports. Trunk ports carry traffic from multiple VLANs. VLAN is identified by a “tag” in the frame. Native VLAN does not have a tag. Default VLAN • VLAN 1 on Cisco switches. • Carries CDP and STP (spanning tree protocol) traffic. • Initially all ports are in this VLAN. • Do not use it for data, voice or management traffic for security reasons. Static VLAN • The normal type. Port configured to be on a VLAN. Connected device is on this VLAN. • VLAN can be created using CLI command, given number and name. • VLAN can be learned from another switch. • If a port is put on a VLAN and the VLAN does not exist, then the VLAN is created. Static VLAN (Port-centric) • If VLAN 20 did not exist before – then it does now. Dynamic VLAN • Not widely used. • Use a VLAN Membership Policy Server (VMPS). • Assign a device to a VLAN based on its MAC address. • Connect device, server assigns VLAN. • Useful if you want to move devices around. Traffic between VLANs • Layer 2 switch keeps VLANs separate. • Router can route between VLANs. It needs to provide a default gateway for each VLAN as VLANs are separate subnets. • Layer 3 switch has a switch virtual interface (SVI) configured for each VLAN. These act like router interfaces to route between VLANs. • A trunk is a point-to-point link between one or more Ethernet switch interfaces and another networking device, such as a router or a switch. • Ethernet trunks carry the traffic of multiple VLANs over a single link. • A VLAN trunk allows you to extend the VLANs across an entire network.






























![[2016-NEW!] 200-120 New Questions and Answers -](http://s1.studyres.com/store/data/000108812_1-bba6a7d69201d6f7aa4d0f7684ac7604-150x150.png)