Network Security - School of Computing and Engineering
... Profile of an Advanced Cyber Intrusion • Ongoing (since 1999) series of suspected intrusions on US commercial and military sites from PRC • Information presented in an unclassified document that details China’s capability to conduct cyber attacks • One element of that report is a detailed report of ...
... Profile of an Advanced Cyber Intrusion • Ongoing (since 1999) series of suspected intrusions on US commercial and military sites from PRC • Information presented in an unclassified document that details China’s capability to conduct cyber attacks • One element of that report is a detailed report of ...
Identify Security Risks and Threats
... Develop security remediation Test security remediation Capture security knowledge ...
... Develop security remediation Test security remediation Capture security knowledge ...
Introduction to Information Security Chapter N
... Identify and understand the threats posed to information security Identify and understand the more common attacks associated with those threats ...
... Identify and understand the threats posed to information security Identify and understand the more common attacks associated with those threats ...
Introduction to Information Security Chapter N
... Identify and understand the threats posed to information security Identify and understand the more common attacks associated with those threats ...
... Identify and understand the threats posed to information security Identify and understand the more common attacks associated with those threats ...
Network Security Network Attacks and Mitigation
... • A DoS attack damages or corrupts your computer system or denies you and others access to your networks, systems, or services. ...
... • A DoS attack damages or corrupts your computer system or denies you and others access to your networks, systems, or services. ...
Chapter 9
... To protect the contents of IP packets To provide defense against network attacks through packet filtering and the enforcement of trusted communication. Attacks that IPSec can prevent and reduce: Packet Sniffing Man in the Middle Data Modification Denial of Service Identity Spoofing ...
... To protect the contents of IP packets To provide defense against network attacks through packet filtering and the enforcement of trusted communication. Attacks that IPSec can prevent and reduce: Packet Sniffing Man in the Middle Data Modification Denial of Service Identity Spoofing ...
Introduction to IT Security - Virginia Alliance for Secure Computing
... Principle of Easiest Penetration: “An intruder must be expected to use any available means of penetration. This is not the most obvious means, nor is it the one against which the most solid defense has been installed.” (Pflegger) ...
... Principle of Easiest Penetration: “An intruder must be expected to use any available means of penetration. This is not the most obvious means, nor is it the one against which the most solid defense has been installed.” (Pflegger) ...
US SAFE WEB Act - Higher Education Compliance Alliance
... measures. The second principle, “scale down”, may not apply to the higher education industry as the FTC recommends only keeping information that is needed and many universities, especially public universities, are subject to statutes which require keeping records for a number of years, so scaling do ...
... measures. The second principle, “scale down”, may not apply to the higher education industry as the FTC recommends only keeping information that is needed and many universities, especially public universities, are subject to statutes which require keeping records for a number of years, so scaling do ...
Threats and Attacks
... § Incident: definitions vary § Any attack, all attacks using vulnerability X, etc. § Anything resulting in service degradation other than problem mgmt., service request fulfillment ...
... § Incident: definitions vary § Any attack, all attacks using vulnerability X, etc. § Anything resulting in service degradation other than problem mgmt., service request fulfillment ...
The AIG netAdvantage Suite® Coverage Highlights
... Identity Theft: Coverage for liability arising from the theft of personal information of the insured’s customers or clients arising from a breach of network security. PLUS, optional coverage for a 24/7 AIG Identity Theft Call Center for employees, customers or clients. ...
... Identity Theft: Coverage for liability arising from the theft of personal information of the insured’s customers or clients arising from a breach of network security. PLUS, optional coverage for a 24/7 AIG Identity Theft Call Center for employees, customers or clients. ...
The CyberFence Difference
... Precise processes in most critical-infrastructure networks rely on the undisturbed operation of industrial control systems (ICS). Failures within the ICS can cause critical services to fail, and may result in severe injury to people, property and the environment. In evaluating options for securing v ...
... Precise processes in most critical-infrastructure networks rely on the undisturbed operation of industrial control systems (ICS). Failures within the ICS can cause critical services to fail, and may result in severe injury to people, property and the environment. In evaluating options for securing v ...
FireWall-1 - Evolution Security Systems Ltd
... Continuous innovation means FireWall-1 delivers the highest level of security to your organization. FireWall-1, ...
... Continuous innovation means FireWall-1 delivers the highest level of security to your organization. FireWall-1, ...
Chapter 1 Study Outline
... B. A good security solution would involve implementation of the security products most suitable for the organizations needs, along with good security practices and ...
... B. A good security solution would involve implementation of the security products most suitable for the organizations needs, along with good security practices and ...
Cyber-Insurance--I Do Not Think That Word
... Sophisticated threats targeting specific computer systems and organizations big and small But strict sub-limits ...
... Sophisticated threats targeting specific computer systems and organizations big and small But strict sub-limits ...
Ch – 1 Introduction
... • A masquerade takes place when one entity pretends to be a different entity (Figure a) . A masquerade attack usually includes one of the other forms of active attack. • For example, authentication sequences can be captured and replayed after a valid authentication sequence has taken place, thus ena ...
... • A masquerade takes place when one entity pretends to be a different entity (Figure a) . A masquerade attack usually includes one of the other forms of active attack. • For example, authentication sequences can be captured and replayed after a valid authentication sequence has taken place, thus ena ...
Taking Control of Advanced Threats
... ▸Most NGFWs augment (not replace) existing firewalls ▸IPS component rated “most important” for securing data ...
... ▸Most NGFWs augment (not replace) existing firewalls ▸IPS component rated “most important” for securing data ...
security threats: a guide for small and medium
... the network operators and project managers as well as the security analysts. Therefore a disgruntled systems administrator will be a major security problem due to the amount of responsibility (and access rights) that he or she holds. With full access privileges, a systems administrator may plan a lo ...
... the network operators and project managers as well as the security analysts. Therefore a disgruntled systems administrator will be a major security problem due to the amount of responsibility (and access rights) that he or she holds. With full access privileges, a systems administrator may plan a lo ...
C.2. Vulnerabilities
... “In 2001, a reporter for The Wall Street Journal bought a used computer in Afghanistan. He found the hard drive contained what appeared to be files from a senior al Qaeda operative. Cullison reports that he turned the computer over to the FBI. In his story published in 2004 in The Atlantic, he caref ...
... “In 2001, a reporter for The Wall Street Journal bought a used computer in Afghanistan. He found the hard drive contained what appeared to be files from a senior al Qaeda operative. Cullison reports that he turned the computer over to the FBI. In his story published in 2004 in The Atlantic, he caref ...
Assessing Network Security for Northwind Traders What
... Port scanning countermeasures include: Implement defense-in-depth to use multiple layers of filtering Plan for misconfigurations or failures Implement an intrusion-detection system Run only the required services Expose services through a reverse proxy ...
... Port scanning countermeasures include: Implement defense-in-depth to use multiple layers of filtering Plan for misconfigurations or failures Implement an intrusion-detection system Run only the required services Expose services through a reverse proxy ...
Cisco 642-552
... exams using the Cisco 642-552 Practice Exam from ipass4sure.com. Once you start using our 642-552 exam questions you simply can't stop! You are guaranteed to pass your Cisco 642-552 test with ease and in your first attempt. Here's what you can expect from the ipass4sure Cisco 642-552 course: * Up-to ...
... exams using the Cisco 642-552 Practice Exam from ipass4sure.com. Once you start using our 642-552 exam questions you simply can't stop! You are guaranteed to pass your Cisco 642-552 test with ease and in your first attempt. Here's what you can expect from the ipass4sure Cisco 642-552 course: * Up-to ...
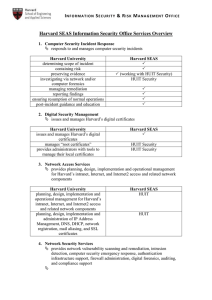
Harvard SEAS Information Security Office Services Overview
... monitors network traffic in real-time to detect anomalous behavior that may indicate computer attack, compromised machine, data breach, etc Harvard University monitors network traffic in real-time aggregates and correlates security data from network and system infrastructure ...
... monitors network traffic in real-time to detect anomalous behavior that may indicate computer attack, compromised machine, data breach, etc Harvard University monitors network traffic in real-time aggregates and correlates security data from network and system infrastructure ...
Global Information Assurance Certification (GIAC) develops and administers the premier
... with the candidates to help them to meet the required standards, which are achievable with hard work.” ...
... with the candidates to help them to meet the required standards, which are achievable with hard work.” ...