Document
... WASHINGTON, Feb 7, 2011 -- Cyberspies have penetrated the U.S. electrical grid and left behind software programs that could be used to disrupt the system, according to current and former national-security officials. The spies came from China, Russia and other countries, these officials said, and wer ...
... WASHINGTON, Feb 7, 2011 -- Cyberspies have penetrated the U.S. electrical grid and left behind software programs that could be used to disrupt the system, according to current and former national-security officials. The spies came from China, Russia and other countries, these officials said, and wer ...
Information Security in the New Millennium
... •Demonstrated security experience can be a key discriminator in any IT career ...
... •Demonstrated security experience can be a key discriminator in any IT career ...
About EICTA - Baltic IT&T Review
... Associated Press reports.(Feb’06) The entire source code for a much-anticipated computer game, Half-Life 2, has been leaked to the Internet,… source code was stolen by hackers who systematically compromised the company´s computer systems. Security vulnerabilities at CardSystems (credit card payment ...
... Associated Press reports.(Feb’06) The entire source code for a much-anticipated computer game, Half-Life 2, has been leaked to the Internet,… source code was stolen by hackers who systematically compromised the company´s computer systems. Security vulnerabilities at CardSystems (credit card payment ...
Cobrador – Channeler brochure
... information. Networking technologies are perpetually evolving: only a live adaptive ...
... information. Networking technologies are perpetually evolving: only a live adaptive ...
DDoS Attacks: What You Can`t See Can Hurt You Dave Larson
... DDoS Analytics & Data Interpretation - Highlights • Real-time and historical DDoS attack data interpretation Single screen operation with summary, top charts, drill-down searches ...
... DDoS Analytics & Data Interpretation - Highlights • Real-time and historical DDoS attack data interpretation Single screen operation with summary, top charts, drill-down searches ...
Survey of online attacks on E-Commerce sites
... Web based attacks are considered to be the greatest threat to the online business as it is related to confidentiality, availability, and integrity. The motive behind e-commerce attack is significantly different then other attacks; Web based attacks focus on an application itself and functions on lay ...
... Web based attacks are considered to be the greatest threat to the online business as it is related to confidentiality, availability, and integrity. The motive behind e-commerce attack is significantly different then other attacks; Web based attacks focus on an application itself and functions on lay ...
Information System Security
... • using this model requires us to: • design a suitable algorithm for the security transformation • generate the secret information (keys) used by the algorithm • develop methods to distribute and share the secret information • specify a protocol enabling the principals to use the transformation and ...
... • using this model requires us to: • design a suitable algorithm for the security transformation • generate the secret information (keys) used by the algorithm • develop methods to distribute and share the secret information • specify a protocol enabling the principals to use the transformation and ...
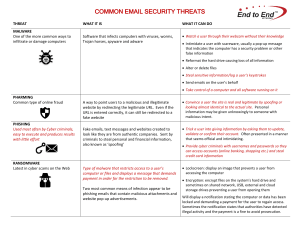
COMMON EMAIL SECURITY THREATS
... Is the email from someone outside of you organization and asking you to something outside of your typical role? Is the sender a stranger? Does the email include a link or attachment? ...
... Is the email from someone outside of you organization and asking you to something outside of your typical role? Is the sender a stranger? Does the email include a link or attachment? ...
BILL ANALYSIS
... basis. As computer needs arise, agencies with resources to fill these needs often find solutions, while agencies with limited resources are often forced to choose between accessibility and security. This fragmented network security approach can lead to overlapping and redundant state assets on one h ...
... basis. As computer needs arise, agencies with resources to fill these needs often find solutions, while agencies with limited resources are often forced to choose between accessibility and security. This fragmented network security approach can lead to overlapping and redundant state assets on one h ...
Notification
... configured to allow anonymous access, potentially exposing sensitive data stored on the servers, The anonymous extension of FTP allows a user to authenticate to the FTP server with a common username such as "anonymous" or "ftp" without submitting a password or by submitting a generic password ore-ma ...
... configured to allow anonymous access, potentially exposing sensitive data stored on the servers, The anonymous extension of FTP allows a user to authenticate to the FTP server with a common username such as "anonymous" or "ftp" without submitting a password or by submitting a generic password ore-ma ...
Network Security
... algorithms and protocols underlying network security applications, including encryption, hash functions, digital signatures, and key exchange. • Part Two : Examines the use of cryptographic algorithms and security protocols to provide security over networks and the Internet. Topics covered include u ...
... algorithms and protocols underlying network security applications, including encryption, hash functions, digital signatures, and key exchange. • Part Two : Examines the use of cryptographic algorithms and security protocols to provide security over networks and the Internet. Topics covered include u ...
Network Security Overview
... Unstructured threats consist of mostly inexperienced individuals using easily available hacking tools from the Internet. Some of the people in this category are motivated by malicious intent, but most are motivated by the intellectual challenge and are commonly called script kiddies. They are not th ...
... Unstructured threats consist of mostly inexperienced individuals using easily available hacking tools from the Internet. Some of the people in this category are motivated by malicious intent, but most are motivated by the intellectual challenge and are commonly called script kiddies. They are not th ...
Slide 1
... Trusted Network Interpretation of the Trusted Computer System Evaluation Criteria (1987) ...
... Trusted Network Interpretation of the Trusted Computer System Evaluation Criteria (1987) ...
426_Fall10_lect01 - Purdue Computer Science
... Security is Secondary • What protection/security mechanisms one has in the physical world? • Why the need for security mechanisms arises? • Security is secondary to the interactions that make security necessary. ...
... Security is Secondary • What protection/security mechanisms one has in the physical world? • Why the need for security mechanisms arises? • Security is secondary to the interactions that make security necessary. ...
E-Commerce and Bank Security
... Prevent unauthorized access while allowing authorized user to connect ...
... Prevent unauthorized access while allowing authorized user to connect ...
Cyber-Multi-Attribute Task Battery (C-MATB)
... analysts work collaboratively with computer systems to identify and respond to cyber threats – Intrusion detection: “the process of monitoring the events occurring in a computer system or network and analyzing them for signs of possible incidents, which are violations or imminent threats of violatio ...
... analysts work collaboratively with computer systems to identify and respond to cyber threats – Intrusion detection: “the process of monitoring the events occurring in a computer system or network and analyzing them for signs of possible incidents, which are violations or imminent threats of violatio ...
18_DataCenter_Security_Overview
... •Eavesdropping - is the unauthorized interception of information that travels on the network, this information might contain confidential data such as username and password. Another example is packet capturing. •Viruses & Worms – both cases of malicious code, hidden in the system until the damage is ...
... •Eavesdropping - is the unauthorized interception of information that travels on the network, this information might contain confidential data such as username and password. Another example is packet capturing. •Viruses & Worms – both cases of malicious code, hidden in the system until the damage is ...
18_DataCenter_Security_Overview
... •Eavesdropping - is the unauthorized interception of information that travels on the network, this information might contain confidential data such as username and password. Another example is packet capturing. •Viruses & Worms – both cases of malicious code, hidden in the system until the damage is ...
... •Eavesdropping - is the unauthorized interception of information that travels on the network, this information might contain confidential data such as username and password. Another example is packet capturing. •Viruses & Worms – both cases of malicious code, hidden in the system until the damage is ...
Network Security
... algorithms and protocols underlying network security applications, including encryption, hash functions, digital signatures, and key exchange. • Part Two : Examines the use of cryptographic algorithms and security protocols to provide security over networks and the Internet. Topics covered include u ...
... algorithms and protocols underlying network security applications, including encryption, hash functions, digital signatures, and key exchange. • Part Two : Examines the use of cryptographic algorithms and security protocols to provide security over networks and the Internet. Topics covered include u ...
Presentation Prepared By: Raghda Zahran
... Information Technology Security Assessment Prepared By: Raghda Zahran Supervised By: Dr. Lo’ai Tawalbeh New York Institute of Technology (NYIT)Jordan’s campus-2006 ...
... Information Technology Security Assessment Prepared By: Raghda Zahran Supervised By: Dr. Lo’ai Tawalbeh New York Institute of Technology (NYIT)Jordan’s campus-2006 ...
Countering Evolving Threats in Distributed Applications
... • Each cluster forms a general story about the emails contained within it from which the basis of the attack can be deduced – For example, for cluster 4, the attack is trying to get the user to update information for their banking account. ...
... • Each cluster forms a general story about the emails contained within it from which the basis of the attack can be deduced – For example, for cluster 4, the attack is trying to get the user to update information for their banking account. ...