Data Encryption Standard - gozips.uakron.edu
... The components of information security architecture are: Policies and procedures – documented procedures and company policies that elaborate on how security is to be carried out Security personnel and administrators – people who enforce and keep security in order Detection equipment – device ...
... The components of information security architecture are: Policies and procedures – documented procedures and company policies that elaborate on how security is to be carried out Security personnel and administrators – people who enforce and keep security in order Detection equipment – device ...
Attacks and vulnerabilities
... Backdoors (Vulnerabilities) Bypass normal means of authentication Hidden from casual inspection Installed separately or integrated into software ...
... Backdoors (Vulnerabilities) Bypass normal means of authentication Hidden from casual inspection Installed separately or integrated into software ...
Internet Vulnerabilities & Criminal Activity
... Malware Analysis Goal - provide insight into attackers Malware has two purposes Steal information from victim computers Commander victim computer’s resources for attacker’s use ...
... Malware Analysis Goal - provide insight into attackers Malware has two purposes Steal information from victim computers Commander victim computer’s resources for attacker’s use ...
Introduction
... intentional actions from occuring in a system. – These potential actions are threats. – Threats that are carried out are attacks. – Intentional attacks are carried out by an attacker. – Objects of attacks are assets. ...
... intentional actions from occuring in a system. – These potential actions are threats. – Threats that are carried out are attacks. – Intentional attacks are carried out by an attacker. – Objects of attacks are assets. ...
Chapter 2
... Many information security issues discussed here are caused by software elements of system Development of software and systems is often ...
... Many information security issues discussed here are caused by software elements of system Development of software and systems is often ...
Chapter 2
... Many information security issues discussed here are caused by software elements of system Development of software and systems is often ...
... Many information security issues discussed here are caused by software elements of system Development of software and systems is often ...
Exploration CCNA4 - Collin College Faculty Website Directory
... Over the years, threat tools and methods have evolved. – In 1985 an attacker had to have sophisticated computer knowledge to make tools and basic attacks. – As time progressed and attackers' tools improved, attackers no longer require the same level of knowledge. ...
... Over the years, threat tools and methods have evolved. – In 1985 an attacker had to have sophisticated computer knowledge to make tools and basic attacks. – As time progressed and attackers' tools improved, attackers no longer require the same level of knowledge. ...
ppt
... Can claim direct link to any other routers A bit harder to attack than DV BGP ASes can announce arbitrary prefix ASes can alter path ...
... Can claim direct link to any other routers A bit harder to attack than DV BGP ASes can announce arbitrary prefix ASes can alter path ...
lecture 1 - Philadelphia University
... – Detection ( in action)– to take measures to detect whether an asset has been damaged, how, and who has caused the damage. – Response ( post-action)– to take measures that allow recovery of assets or recovery from damage, and minimize losses. – Reflection – plans/processes that focus on security im ...
... – Detection ( in action)– to take measures to detect whether an asset has been damaged, how, and who has caused the damage. – Response ( post-action)– to take measures that allow recovery of assets or recovery from damage, and minimize losses. – Reflection – plans/processes that focus on security im ...
InterScan Messaging Security Solutions
... • Instead we apply predictive techniques--zero-day protection, heuristics, and behavior analysis - Antivirus = prevents virus attacks aimed at specific organizations (for example, ransom attacks) - Anti-spyware = stops the more targeted spyware attacks sent through email. - DHA and bounced mail prot ...
... • Instead we apply predictive techniques--zero-day protection, heuristics, and behavior analysis - Antivirus = prevents virus attacks aimed at specific organizations (for example, ransom attacks) - Anti-spyware = stops the more targeted spyware attacks sent through email. - DHA and bounced mail prot ...
Cutting Edge VoIP Security Issues Color
... Voice SPAM refers to bulk, automatically generated, unsolicited phone calls Similar to telemarketing, but occurring at the frequency of email SPAM Not an issue yet, but will become prevalent when: ...
... Voice SPAM refers to bulk, automatically generated, unsolicited phone calls Similar to telemarketing, but occurring at the frequency of email SPAM Not an issue yet, but will become prevalent when: ...
SCADA Security
... called information warfare, or cyber war as some people called it. It involved using computers and the Internet as weapons. Much of it was still theory, but we were told that before too long it might be possible for a hacker with a computer to disable critical infrastructure in a major city and disr ...
... called information warfare, or cyber war as some people called it. It involved using computers and the Internet as weapons. Much of it was still theory, but we were told that before too long it might be possible for a hacker with a computer to disable critical infrastructure in a major city and disr ...
SCADASummaryLsn
... called information warfare, or cyber war as some people called it. It involved using computers and the Internet as weapons. Much of it was still theory, but we were told that before too long it might be possible for a hacker with a computer to disable critical infrastructure in a major city and disr ...
... called information warfare, or cyber war as some people called it. It involved using computers and the Internet as weapons. Much of it was still theory, but we were told that before too long it might be possible for a hacker with a computer to disable critical infrastructure in a major city and disr ...
SOW
... The Contractor shall provide all personnel, equipment, tools, materials, supervision and other items necessary to perform the task defined in this Performance Work Statements (PWS), except as specified in Part 3, WMATAFurnished Resources. The Contractor shall provide timely, technically accurate and ...
... The Contractor shall provide all personnel, equipment, tools, materials, supervision and other items necessary to perform the task defined in this Performance Work Statements (PWS), except as specified in Part 3, WMATAFurnished Resources. The Contractor shall provide timely, technically accurate and ...
9781435420168_PPT_CH01
... Mail-bombing: another form of e-mail attack that is also a DoS, in which an attacker routes large quantities of e-mail to the target Sniffer: program and/or device that can monitor data traveling over a network; can be used for both legitimate network management and for stealing information from ...
... Mail-bombing: another form of e-mail attack that is also a DoS, in which an attacker routes large quantities of e-mail to the target Sniffer: program and/or device that can monitor data traveling over a network; can be used for both legitimate network management and for stealing information from ...
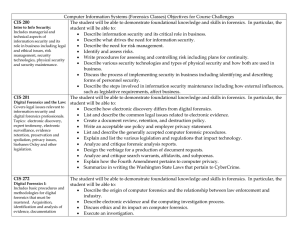
Computer Information Systems (Forensics Classes) Objectives for
... • Identify strengths and weaknesses associated with protocols designed to authenticate users. • Describe the technologies that exist at the different TCP/IP layers, infrastructure security concepts and the protocols used for dial-in security. • Discuss how digital signatures are used for secure tran ...
... • Identify strengths and weaknesses associated with protocols designed to authenticate users. • Describe the technologies that exist at the different TCP/IP layers, infrastructure security concepts and the protocols used for dial-in security. • Discuss how digital signatures are used for secure tran ...
Public Presentation - Academic Conferences
... – Joel Brenner, counterintelligence executive in CNN.com, October 19, 2007 ...
... – Joel Brenner, counterintelligence executive in CNN.com, October 19, 2007 ...
Top Five DNS Security Attack Risks and How to Avoid Them
... Global Program Director, Network Security ...
... Global Program Director, Network Security ...
Joshua White - Everis Inc.
... Joshua White Director of CyOON Research and Development “Cyber Operations for Optical Networks” [email protected] Everis Inc http://www.EverisInc.com ...
... Joshua White Director of CyOON Research and Development “Cyber Operations for Optical Networks” [email protected] Everis Inc http://www.EverisInc.com ...
Course Overview - Cyber Security Lab
... and remove vulnerabilities. More people are using computers without knowing well how to protect their computers. Even protocols used to manage your network can be a source of vulnerability themselves. All too often security weakness is exposed only after the system has been compromised, by which tim ...
... and remove vulnerabilities. More people are using computers without knowing well how to protect their computers. Even protocols used to manage your network can be a source of vulnerability themselves. All too often security weakness is exposed only after the system has been compromised, by which tim ...
Defending Office 365 Against Denial-of-Service Attacks
... Microsoft’s DoS Defense Strategy Microsoft’s strategy for defending against DoS is somewhat unique due to our scale and global footprint. This scale allows Microsoft to utilize strategies and techniques that few organizations (providers or customer organizations) can match. The cornerstone of our Do ...
... Microsoft’s DoS Defense Strategy Microsoft’s strategy for defending against DoS is somewhat unique due to our scale and global footprint. This scale allows Microsoft to utilize strategies and techniques that few organizations (providers or customer organizations) can match. The cornerstone of our Do ...
Blueprint For Security Chapter 6
... Fingerprinting: systematic survey of all of target organization’s Internet addresses collected during the footprinting phase Fingerprinting reveals useful information about internal structure and operational nature of target system or network for anticipated attack ...
... Fingerprinting: systematic survey of all of target organization’s Internet addresses collected during the footprinting phase Fingerprinting reveals useful information about internal structure and operational nature of target system or network for anticipated attack ...
Introduction to Information Security Chapter N
... Principles of Information Security - Chapter 2 ...
... Principles of Information Security - Chapter 2 ...
(FIPS) 140-2 - Aviat Networks
... protecting IT systems that carry sensitive but unclassified information • Validates both hardware and software • FIPS 140-2 Includes FIPS 197 • 4 Levels of increasing physical ...
... protecting IT systems that carry sensitive but unclassified information • Validates both hardware and software • FIPS 140-2 Includes FIPS 197 • 4 Levels of increasing physical ...