Virtual Cyber Security Lab - Celtic-Plus
... Virtual Cyber Security Lab Uğur Çağal, Hakan Kılınç [email protected] ...
... Virtual Cyber Security Lab Uğur Çağal, Hakan Kılınç [email protected] ...
Open resource
... secure, assess, and mitigate cyber risk; and prepare for, prevent, and respond to cyber incidents. CS&C leads efforts to protect the federal “.gov” domain of civilian government networks and to collaborate with the private sector—the “.com” domain—to increase the security of critical networks. B ...
... secure, assess, and mitigate cyber risk; and prepare for, prevent, and respond to cyber incidents. CS&C leads efforts to protect the federal “.gov” domain of civilian government networks and to collaborate with the private sector—the “.com” domain—to increase the security of critical networks. B ...
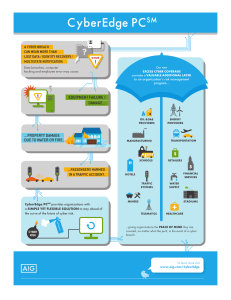
PDF Product Profile CyberEdge PC Overview
... American International Group, Inc. (AIG) is a leading international insurance organization serving customers in more than 130 countries. AIG companies serve commercial, institutional, and individual customers through one of the most extensive worldwide property-casualty networks of any insurer. In a ...
... American International Group, Inc. (AIG) is a leading international insurance organization serving customers in more than 130 countries. AIG companies serve commercial, institutional, and individual customers through one of the most extensive worldwide property-casualty networks of any insurer. In a ...
Junior Enlisted - Cyber Security
... skills with detection, prevention and response to threats against customer’s enterprise. Monitored multiple security technologies utilizing Security Information and Event management. Department of Defense Security Clearance Honorable Discharge United States Marine Corps ...
... skills with detection, prevention and response to threats against customer’s enterprise. Monitored multiple security technologies utilizing Security Information and Event management. Department of Defense Security Clearance Honorable Discharge United States Marine Corps ...
Attivo Networks Deception Platform Integrates with the Check Point
... have consistently led to breaches in companies of every size across many different industries. In addition to the security weaknesses, many security devices do not communicate with each other – meaning alerts raised by one device may not be passed to others in time to stop the same threat at a diffe ...
... have consistently led to breaches in companies of every size across many different industries. In addition to the security weaknesses, many security devices do not communicate with each other – meaning alerts raised by one device may not be passed to others in time to stop the same threat at a diffe ...
Symbolic Honeynets for Gathering Cyber
... ● uses SHODAN to detect how many ICS systems are connected to internet EACH DAY: ● 2000-8000 NEW ICS on internet PER DAY ...
... ● uses SHODAN to detect how many ICS systems are connected to internet EACH DAY: ● 2000-8000 NEW ICS on internet PER DAY ...
NetDay Cyber Security Kit for Schools
... community directors and finance managers, as well as school-level administrators, such as principals, guidance counselors and libraries. Safeguarding computers in the schools is not just for technology professionals: it is every administrator’s responsibility. While most school districts have securi ...
... community directors and finance managers, as well as school-level administrators, such as principals, guidance counselors and libraries. Safeguarding computers in the schools is not just for technology professionals: it is every administrator’s responsibility. While most school districts have securi ...
Document
... improving process for defending IT assets • The CND approach in this Chapter includes: – Lightweight process for CND – Set of open source scripts for network monitoring and Advanced Log Analysis (ALA) on Backtrack – Agile strategy for escalating defenses – Cyber investigations process – Scenario for ...
... improving process for defending IT assets • The CND approach in this Chapter includes: – Lightweight process for CND – Set of open source scripts for network monitoring and Advanced Log Analysis (ALA) on Backtrack – Agile strategy for escalating defenses – Cyber investigations process – Scenario for ...
Cyber Risks of Manufacturers Limiting the Risk Factors of
... employees to break up any routine tasks during the workday by taking a walk or doing a few quick stretches. Each employee should also ensure that his or her workstation is suited for his or her individual needs. For more information on MSDs and preventing workplace injuries, contact Atlantic Pacific ...
... employees to break up any routine tasks during the workday by taking a walk or doing a few quick stretches. Each employee should also ensure that his or her workstation is suited for his or her individual needs. For more information on MSDs and preventing workplace injuries, contact Atlantic Pacific ...
file - ScholarSphere
... Mart, etc. Threats of break-ins are already affecting computer security executives. A report issued in January by the Center for Strategic and International Studies and the computer security company McAfee, which surveyed 600 computer security professionals in 14 countries, found that half of the re ...
... Mart, etc. Threats of break-ins are already affecting computer security executives. A report issued in January by the Center for Strategic and International Studies and the computer security company McAfee, which surveyed 600 computer security professionals in 14 countries, found that half of the re ...
Cyber Challenges
... Providing the design, engineering, acquisition and provisioning of ground and space segment communications services; operate network operations center (NOC) ...
... Providing the design, engineering, acquisition and provisioning of ground and space segment communications services; operate network operations center (NOC) ...
Cybersecurity - Queen`s Wiki
... That could never happen to me! Think again. • Microsoft reports the ransomware attack rate in Canada is 4x higher than any other country • A recent Anti-Phishing Working Group study states there are more phishing attacks “than at any other time in history” with incidents rising by a massive 250% in ...
... That could never happen to me! Think again. • Microsoft reports the ransomware attack rate in Canada is 4x higher than any other country • A recent Anti-Phishing Working Group study states there are more phishing attacks “than at any other time in history” with incidents rising by a massive 250% in ...
Cyber insurance market set to reach $7.5 billion in annual
... report says, there is a real risk that a disruptor will move in and corner the market with aggressive pricing and more favourable terms. “Many insurers and reinsurers are looking to take advantage of what they see as a rare opportunity to secure high margins in an otherwise soft market,” Mr Britten ...
... report says, there is a real risk that a disruptor will move in and corner the market with aggressive pricing and more favourable terms. “Many insurers and reinsurers are looking to take advantage of what they see as a rare opportunity to secure high margins in an otherwise soft market,” Mr Britten ...
Data Mining BS/MS Project
... • K. Ingham. “Comparing Anomaly Detection Techniques for HTTP”. Proc. 10th International Symposium on Recent Advances in Intrusion Detection. 2006. • S. Stolfo. “Anomaly Detection in Computer Security and an Application to File System Accesses”. Lecture Notes in Computer Science, Vol. 3488, pp. 14-2 ...
... • K. Ingham. “Comparing Anomaly Detection Techniques for HTTP”. Proc. 10th International Symposium on Recent Advances in Intrusion Detection. 2006. • S. Stolfo. “Anomaly Detection in Computer Security and an Application to File System Accesses”. Lecture Notes in Computer Science, Vol. 3488, pp. 14-2 ...
Glenbriar TakeStock! - Glenbriar Technologies Inc.
... Local data storage will invite opportunities from industries that utilize highly sensitive data (finance, healthcare, mining, etc.) ...
... Local data storage will invite opportunities from industries that utilize highly sensitive data (finance, healthcare, mining, etc.) ...
Beyond Data Breach Cyber Trends and Exposures â Mr. Jason Kelly
... CyberEdge® Mobile App The CyberEdge Mobile App for iPads combines the latest cyber news, opinion and risk analysis with real-time updates on country-wide data breaches, to put the cyber information users want at their fingertips. The app is available for free on the App Store. ...
... CyberEdge® Mobile App The CyberEdge Mobile App for iPads combines the latest cyber news, opinion and risk analysis with real-time updates on country-wide data breaches, to put the cyber information users want at their fingertips. The app is available for free on the App Store. ...
Power Point Slides - Organization of American States
... •Important aspect of dealing with these disasters: crisis communication •Partner closely with other orgs like PAHO, the Caribbean Disaster Management Agency (CDEMA) and private sector entities ...
... •Important aspect of dealing with these disasters: crisis communication •Partner closely with other orgs like PAHO, the Caribbean Disaster Management Agency (CDEMA) and private sector entities ...
Enter Title in Docm Properties
... Your initial responsibilities will be the development of modules for the Tofino Security Appliance. This includes system design, code development, documentation, unit-tests, code-reviews, and bug-fixes. Depending on your skill level, this will evolve into leading a team to develop new product module ...
... Your initial responsibilities will be the development of modules for the Tofino Security Appliance. This includes system design, code development, documentation, unit-tests, code-reviews, and bug-fixes. Depending on your skill level, this will evolve into leading a team to develop new product module ...
BIO-ELECTRO-INFO TECHNOLOGIES TO COMBAT TERRORISM
... who would authorize it, what constitutes legitimate targets, and what kinds of attacks -- Denial of Service, hacking, worms -- could be used. ...
... who would authorize it, what constitutes legitimate targets, and what kinds of attacks -- Denial of Service, hacking, worms -- could be used. ...
Marine Center for Advanced Operational Culture Training
... Advanced Operational Culture Training (CAOCL) Allen Corporation of America has won, as a subcontractor to Corps Solutions, a base plus four-year contract to support the Center for Advanced Operational Culture Learning (CAOCL). CAOCL is a directorate within the United States Marine Corps Training and ...
... Advanced Operational Culture Training (CAOCL) Allen Corporation of America has won, as a subcontractor to Corps Solutions, a base plus four-year contract to support the Center for Advanced Operational Culture Learning (CAOCL). CAOCL is a directorate within the United States Marine Corps Training and ...
Neal Ziring Very Short Bio
... Mr. Neal Ziring is the Technical Director for the National Security Agency’s Capabilities Directorate, serving as a technical advisor to the Capabilities Director, Deputy Director, and other senior leadership. Mr. Ziring is responsible for setting the technical direction across many parts of the cap ...
... Mr. Neal Ziring is the Technical Director for the National Security Agency’s Capabilities Directorate, serving as a technical advisor to the Capabilities Director, Deputy Director, and other senior leadership. Mr. Ziring is responsible for setting the technical direction across many parts of the cap ...
ICBA Encourages Consumers to Protect their Data during Cyber
... financial institutions. Increasingly, cybercriminals compromise the networks that support these devices. This often results in identity theft, which can also yield financial losses and safety for consumers. In fact, a recent report from the Center for Strategic and International Studies (CSIS) found ...
... financial institutions. Increasingly, cybercriminals compromise the networks that support these devices. This often results in identity theft, which can also yield financial losses and safety for consumers. In fact, a recent report from the Center for Strategic and International Studies (CSIS) found ...
Internet Techniques
... IMS. Cyber threats and cyber defence. Internet based social networking (e.g. Twitter, Youtube). Military networks, cyber warfare. Semantic Web and Web 2.0. SOA. IoS. P2P. Cloud computing. Laboratories exercises are relevant to the issues raised at the lecture. Students learn the practical use of too ...
... IMS. Cyber threats and cyber defence. Internet based social networking (e.g. Twitter, Youtube). Military networks, cyber warfare. Semantic Web and Web 2.0. SOA. IoS. P2P. Cloud computing. Laboratories exercises are relevant to the issues raised at the lecture. Students learn the practical use of too ...